Keyword cipher text retrieval method for cloud storage
A keyword and cloud storage technology, applied in digital data processing, instruments, calculations, etc., can solve the problems of not being absolutely accurate and poor expansion performance, and achieve improved security, low performance requirements, and low retrieval costs Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0022] A cloud storage-oriented keyword ciphertext retrieval method of the present invention will be described in detail below in conjunction with the accompanying drawings.
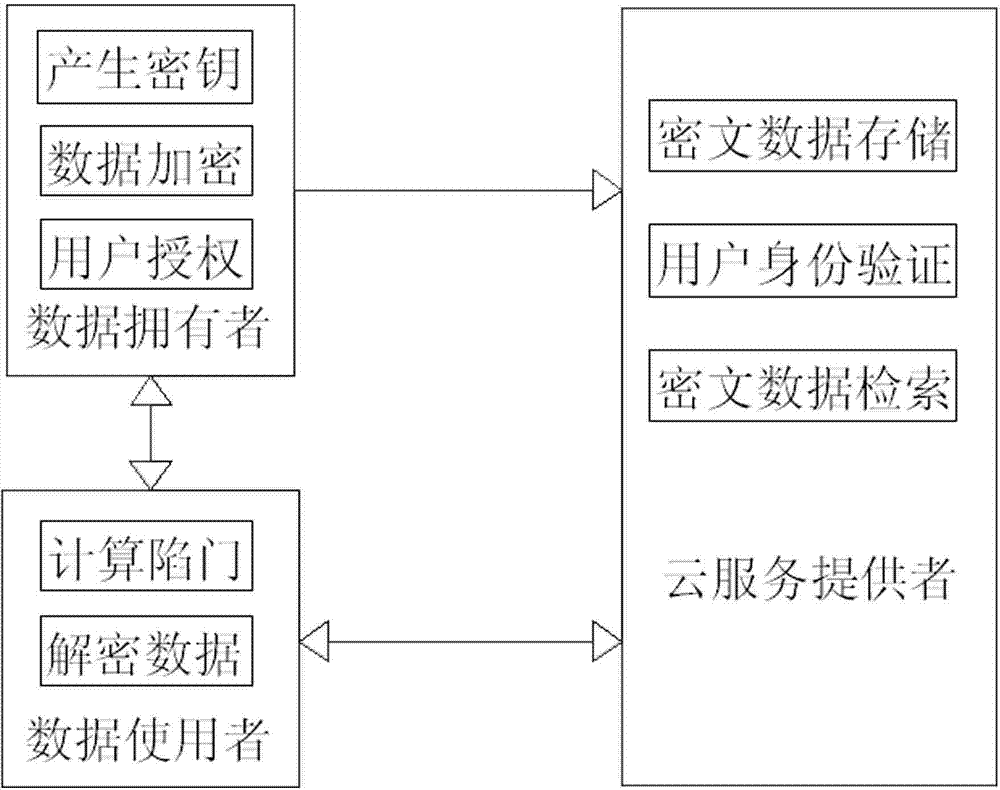
[0023] For the cloud storage environment, this method proposes a new keyword ciphertext retrieval method, which uses the AES symmetric encryption algorithm to encrypt the documents stored in the cloud server, and uses the NTRU public key algorithm to realize the ciphertext retrieval. Keyword search in the text. as attached figure 1 As shown, a cloud storage-oriented keyword ciphertext retrieval method is now provided. The method is based on the cloud storage system. The structure includes the data owner DO (Data Owner), data user DU (Data Users), cloud service provider or CS (Cloud Server) three roles.
[0024] Data owner DO: The services provided include basic parameters such as selecting an encryption algorithm and generating keys; sending encrypted documents and encrypted keywords to CS; authorizing...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com