Association rule mining method for privacy protection under distributed environment
A technology for distributed environment and privacy protection, which is applied in the mining field of association rules for privacy protection in a distributed environment. It can solve the problems of decreased mining accuracy, high algorithm complexity, and damaged attribute correlation, etc., to reduce the amount of calculation and communication. , Improve the excavation efficiency, improve the effect of recovery accuracy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
specific Embodiment approach
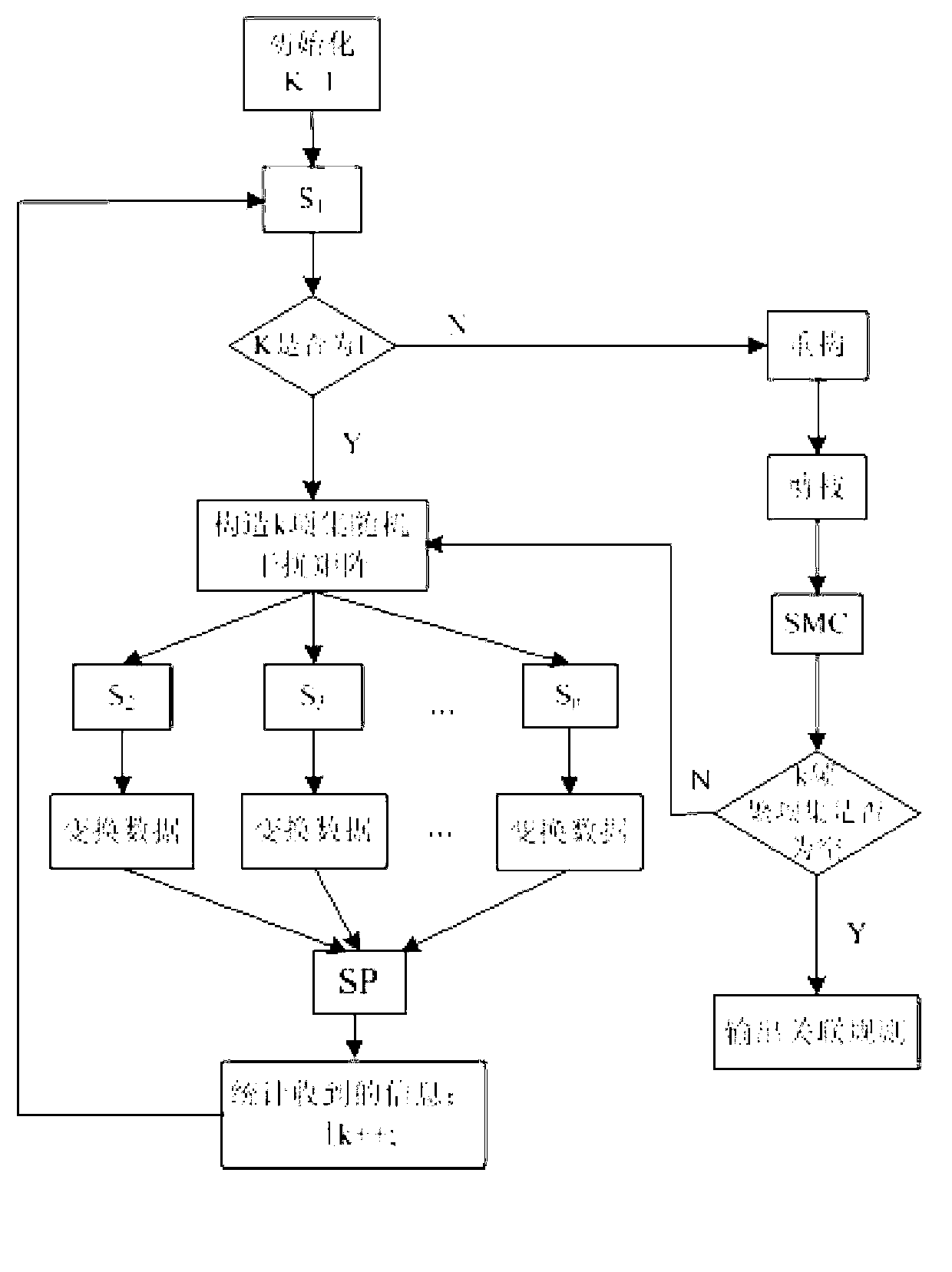
[0048] BEGIN (start)
[0049] k=1; / / 1-itemset
[0050] Repeat
[0051] {
[0052] 1) S 1 According to the candidate k-itemset, construct the itemset random interference matrix P L sent to other local sites.
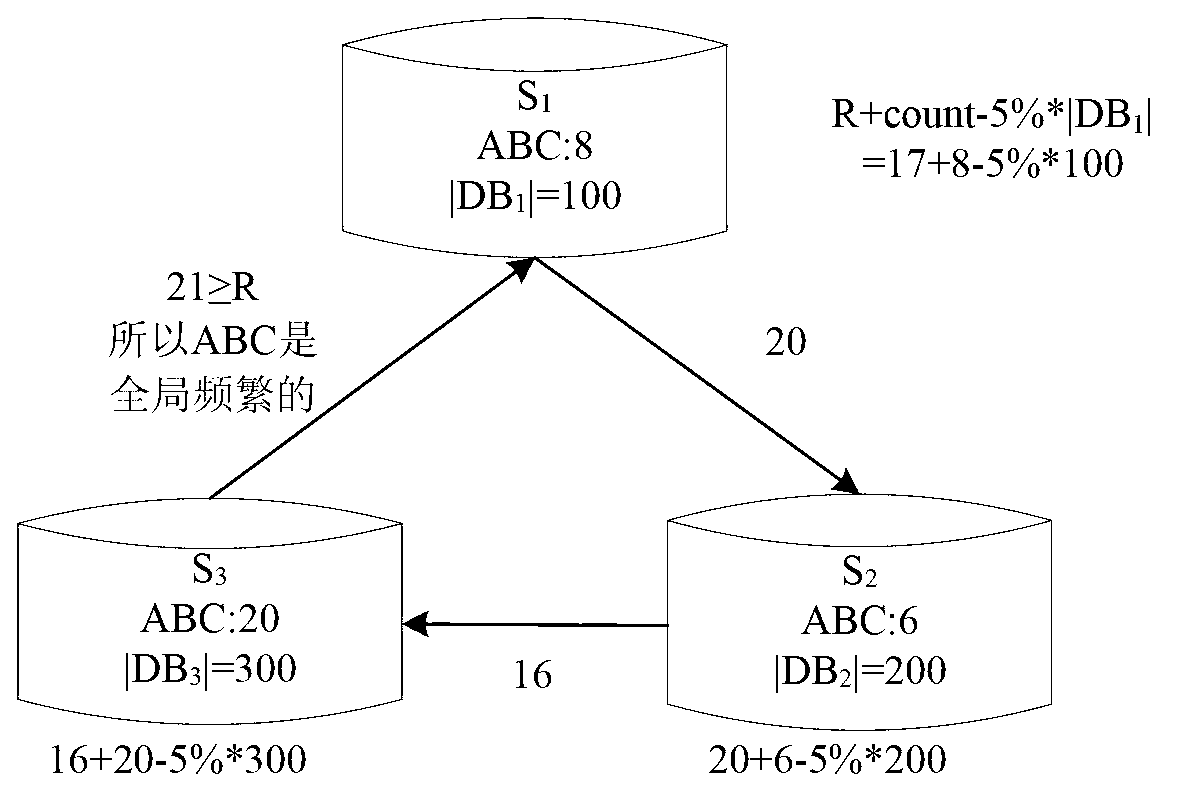
[0053] 2) Each local site according to P L Disturb all its records, and then count the support numbers of the k-itemsets in the disturbed database, and send them to the semi-trusted third-party site SP to form a matrix of support numbers.
[0054] 3) The semi-integrity third-party site SP sums all the item set support matrixes sent by each local site, obtains the summed support matrix MS', and sends it to S 1 .
[0055] 4) S 1 Use P L -1 (P L The inverse matrix) restores the support count MS of the item set in MS' in the original data, and finds out the value greater than or equal to the threshold (MST-w) (the parameter w is set here, mainly to obtain more approximate frequent items after estimation set, so that more itemsets will have the opportunity to determ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com