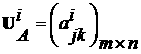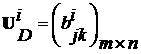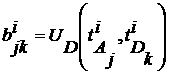Network safety optimum attacking and defending decision method for attacking and defending game
A network security, offensive and defensive game technology, applied in data exchange networks, digital transmission systems, electrical components, etc., can solve problems such as unreasonable defense, and achieve the effect of maximizing, realizing revenue, and simplifying calculation.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0030] The present invention will be further described below in conjunction with the drawings and embodiments.
[0031] Such as figure 1 As shown, a network security optimal offensive and defensive decision-making method based on offensive and defensive games, the specific method steps are as follows:
[0032] The first step is to construct a reachable matrix based on the connectivity of all host nodes in the network topology.
[0033] The second step is to use the vulnerability scanning tools Nessus, ISS and SARA to scan each host node in the network to obtain the vulnerability set of each host node.
[0034] The third step is to construct a state attack and defense graph based on the vulnerability set of each host node and the utilization rules of each vulnerability. The state attack and defense diagram is a state transition system diagram ;among them, It is the state node set in the figure, which represents the network security state; It is the edge set in the graph, which repre...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com