Privacy-removing processing method and device using the same
A technology of de-privacy and processing methods, which is applied in the field of data warehouse privacy data protection and de-privacy processing, which can solve the problems of poor privacy data de-privacy processing and achieve the effect of ensuring uniformity and security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0049]According to an embodiment of the present invention, a de-privacy processing method is provided. Embodiment 1 of this method includes:
[0050] Step S102, data acquisition: after the data acquisition layer extracts data (Extract) from systems such as CRM (customer relationship management), BOSS (business operation support system), VGOP (value-added business integrated operation platform), these source data contain a lot of customer privacy data. Before the source data enters the data warehouse, it is necessary to determine whether the data to be imported contains the customer's private information. If so, the private information needs to be de-privatized. Otherwise, skip the privacy processing step and continue to follow the original process. deal with;
[0051] Step S104, de-privacy processing: In the data conversion processing stage (Translate), continue to perform various inspections and normalization processing on the data. For customer data that contains privacy, ...
Embodiment 2
[0060] Embodiment 2 of this method includes:
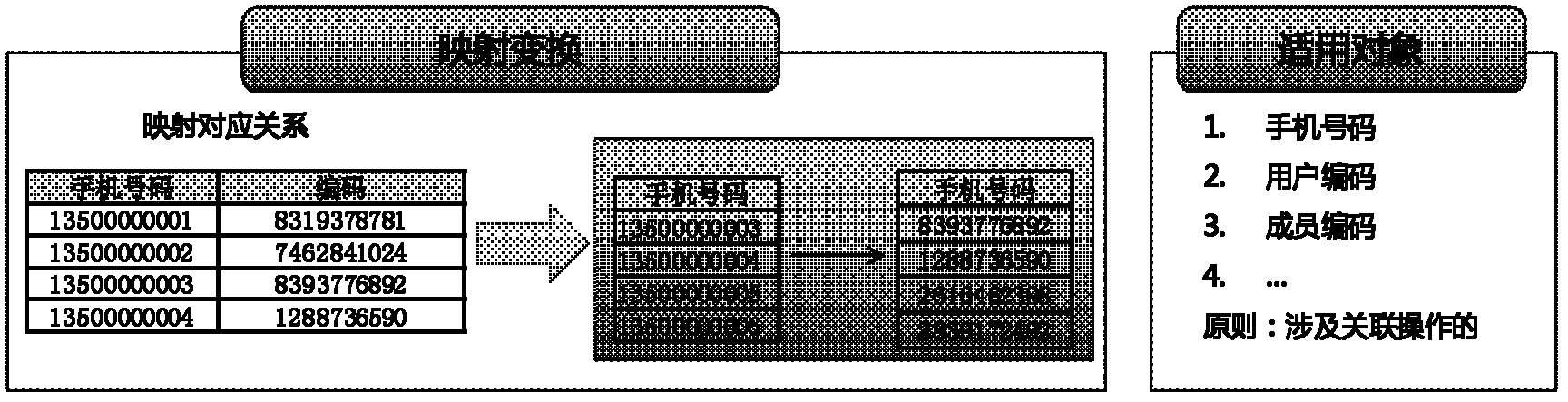
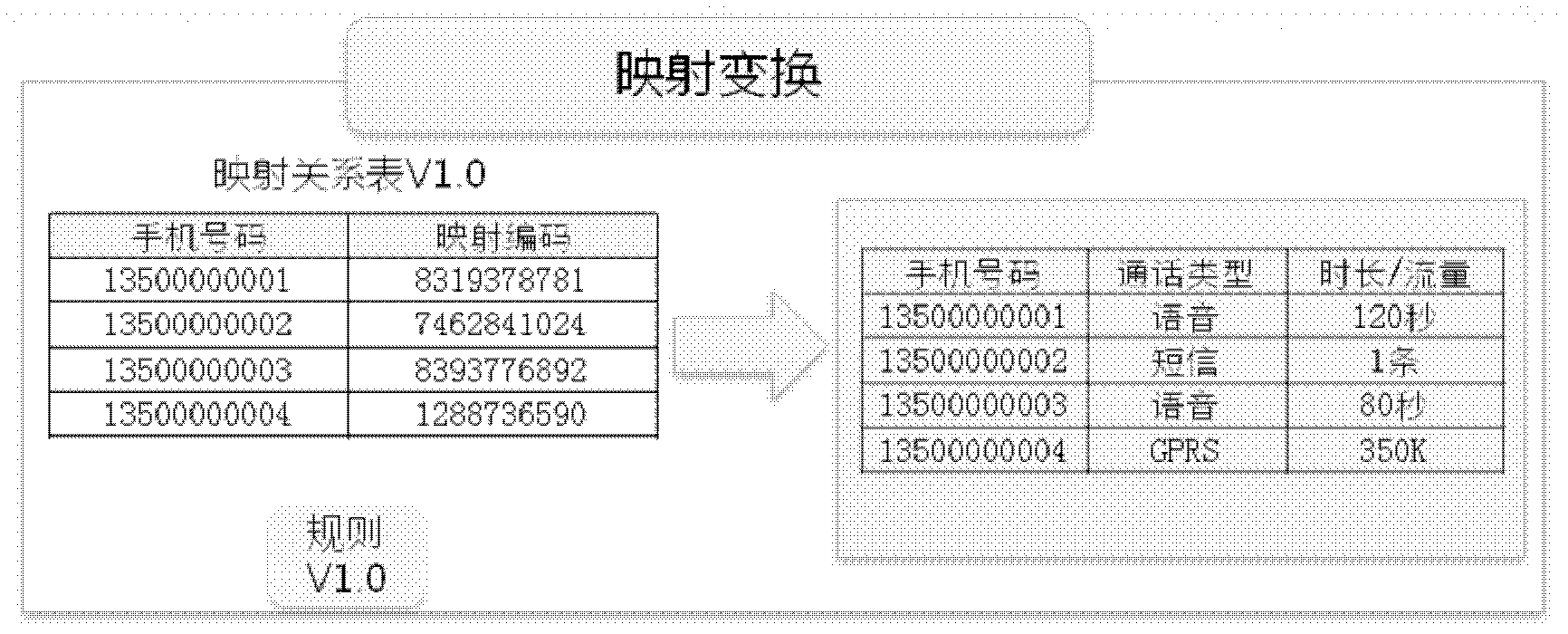
[0061] Step S202: the data warehouse obtains a new data file ( figure 2 table on the right), found that the mobile phone number in the data file is customer privacy data, and needs to use the set mapping relationship table V1.0 ( figure 2 Table on the left) to perform mapping transformation processing;
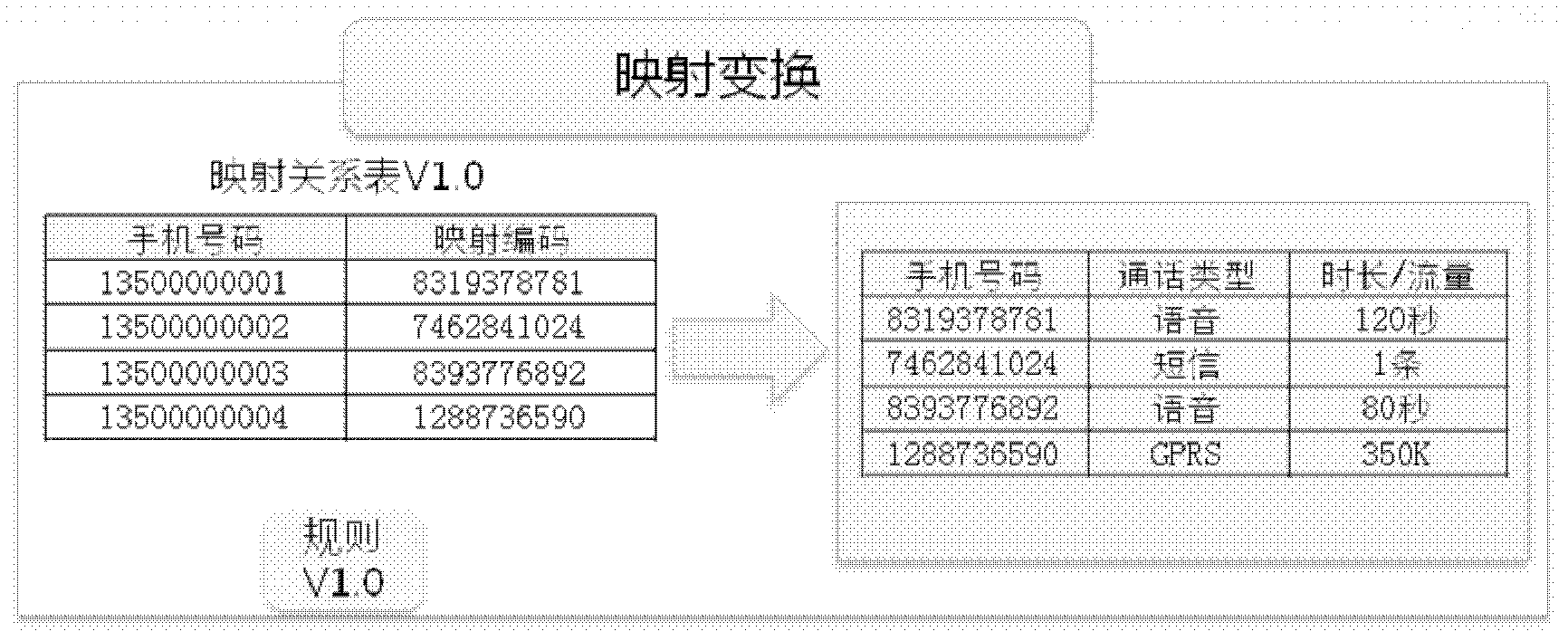
[0062] Step S204: According to the mapping conversion method called from the de-privacy method library, according to the mapping rule V1.0, the mobile phone number in the data file is converted into the mapping code in the mapping relationship table V1.0, and the customer in the data file is completed. De-privacy processing of private data, such as image 3 shown.
[0063] In the de-privacy processing method of this embodiment, the customer privacy data in the source data is de-privacy processing in the ETL conversion stage, so that the data saved in the data warehouse no longer contains customer privacy data, even if data le...
Embodiment 3
[0065] Embodiment three of this method includes:
[0066] Step S302: For the data file ( Figure 4 The mobile phone number in the table on the right), if in the mapping relationship table ( Figure 4 The corresponding mapping rule cannot be found in the table on the left), and the exception handling process needs to be started. First, add the mapping rule in the mapping relationship table V1.0, and then perform mapping transformation processing according to the new mapping rule, such as Figure 4 shown;
[0067] Step S304: According to the mapping rule maintenance plan, add a new mapping rule to the mapping relationship table V1.0 for the mobile phone number 13500000005, such as Figure 5 shown;
[0068] Step S306: According to the mapping rule V1.0, the mobile phone number in the data file is transformed into the mapping code in the new mapping relationship table V1.0, and the abnormal processing of de-privacy of the customer privacy data in the data file is completed, suc...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com