Computer malicious software detection novel method based on software control flow features
A software control and malicious software technology, applied in computing, special data processing applications, instruments, etc., can solve problems such as insufficient accuracy, unstable local features, and reduced detection effects, achieving good stability, maintaining stability, and good The effect of test results
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
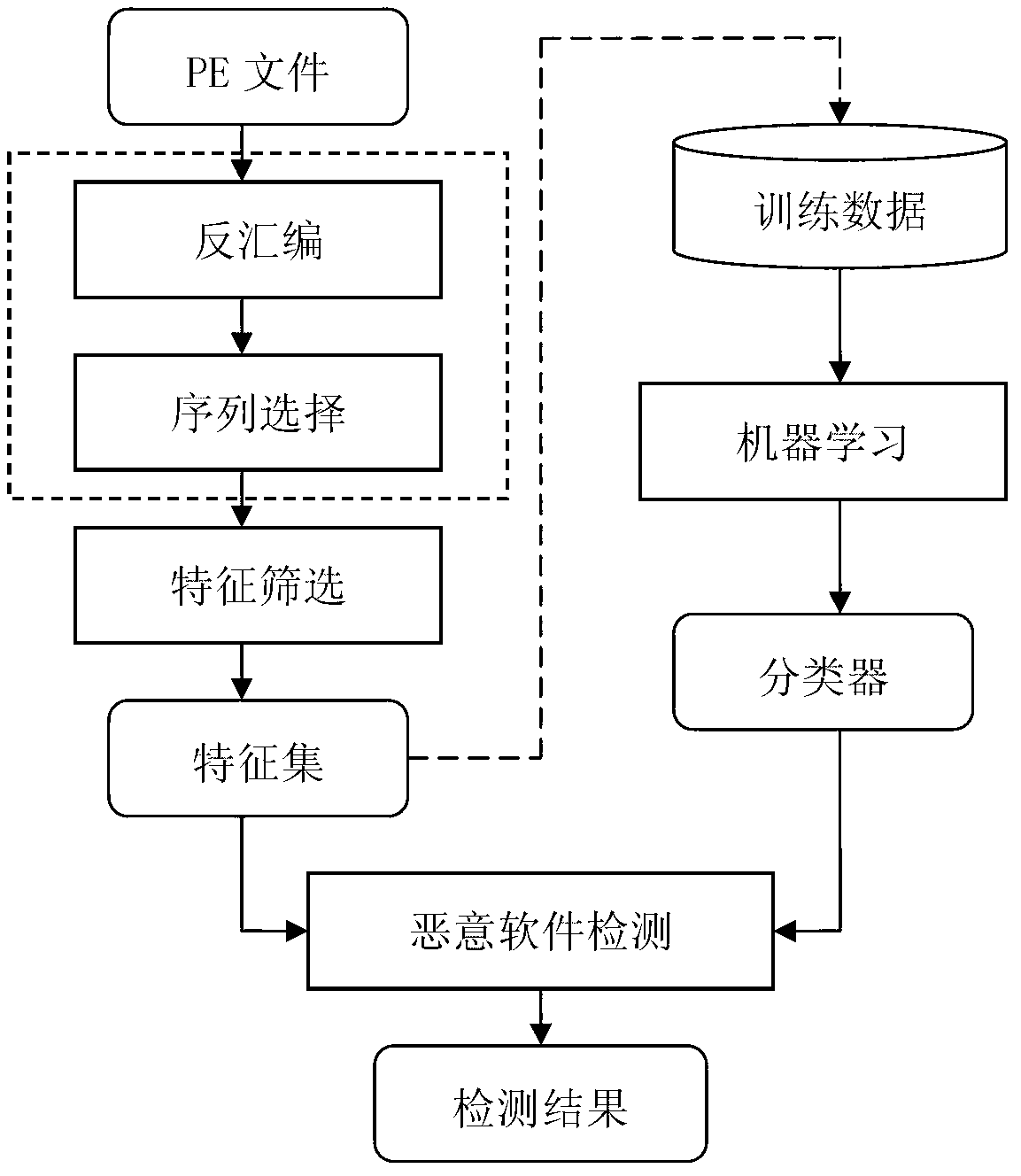
[0029] see figure 1 , the present invention comprises following 4 steps: 1, carry out disassembly to PE format file; 2, select code basic block according to control flow; 3, software feature representation and screening; 4, judge malicious software and normal software by classification algorithm; Proceed as follows:
[0030] 1) Disassemble the PE format file:
[0031] The objects we deal with are files in PE format, and the main data are the codes obtained after these files are disassembled. Therefore, the quality of disassembly is related to the accuracy of the data. In this model, the recursive descent algorithm is used to process the files. The advantage is that it can effectively distinguish instructions from data and improve reliable results. Due to differences in function call instructions generated by different compilers, we use the x86 assembly instruction set to create instruction sequences.
[0032] 2) Select the basic block of code
[0033] The performance of so...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com