Automation positioning method for binary system program vulnerabilities
A technology of binary program and positioning method, which is applied in the field of binary program vulnerability automatic positioning and vulnerability positioning, which can solve the problems of being unable to find the real cause of the vulnerability, uncontrollable execution flow differences, and difficulty in finding the execution flow, so as to prevent malicious use and reduce The number of instructions and the effect of improving analysis efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
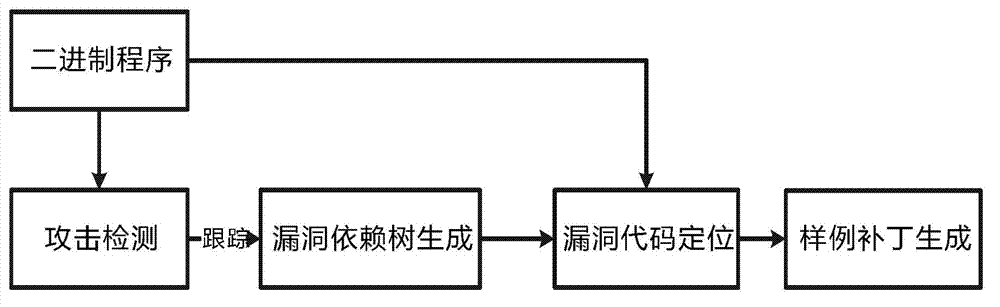
Image
Examples
Embodiment Construction
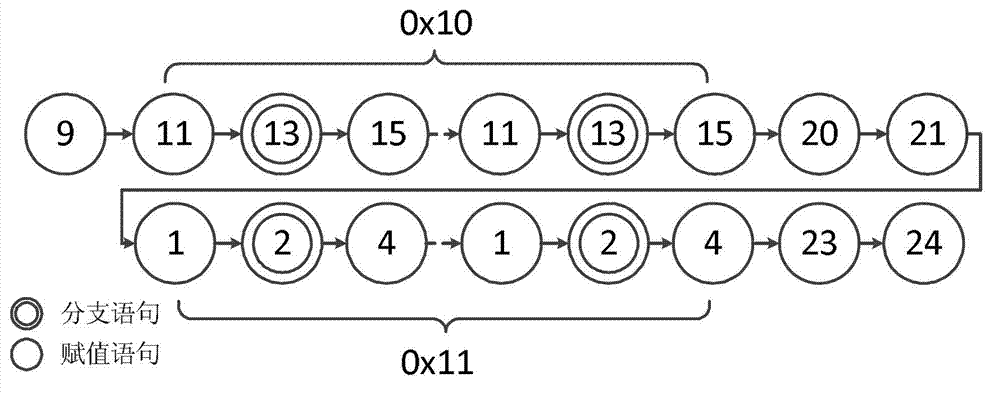
[0031] 1) Record the execution path of the error operation in the operation of the binary program to be detected, that is, record all instructions from the beginning of the program to the error process (it is known that a certain input will cause the program error, such as a crash phenomenon, and then start recording from the beginning). In order to avoid analyzing the program again, the recording process includes recording each branch instruction and selected branch. In the actual analysis, because the location of the vulnerability is close to the instruction, and considering the limitations of the program and hard disk space, we set a threshold for instruction tracking and recording. Currently, 100,000 instructions are selected. If this threshold is exceeded, the newly recorded instruction will overwrite the latest instruction. The command recorded first will be recorded in a loop. If the vulnerable code cannot be found in the recorded instructions, we will reset the thresho...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com