Method and processor for encryption and decryption
An encryption and decryption, processor technology, applied in the field of methods and processors, can solve problems such as occupying more FPGA area
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0024] Specific embodiments of the present invention will be described in detail below in conjunction with the accompanying drawings. In the following description, for purposes of explanation and not limitation, specific details are set forth in order to provide a thorough understanding of the invention. It will be apparent, however, to one skilled in the art that the present invention may be practiced in other embodiments that depart from these specific details.
[0025] It should be noted here that, in order to avoid obscuring the present invention due to unnecessary details, only the device structure and / or processing steps closely related to the solution according to the present invention are shown in the drawings, and the steps related to the present invention are omitted. Invent other details that don't really matter.
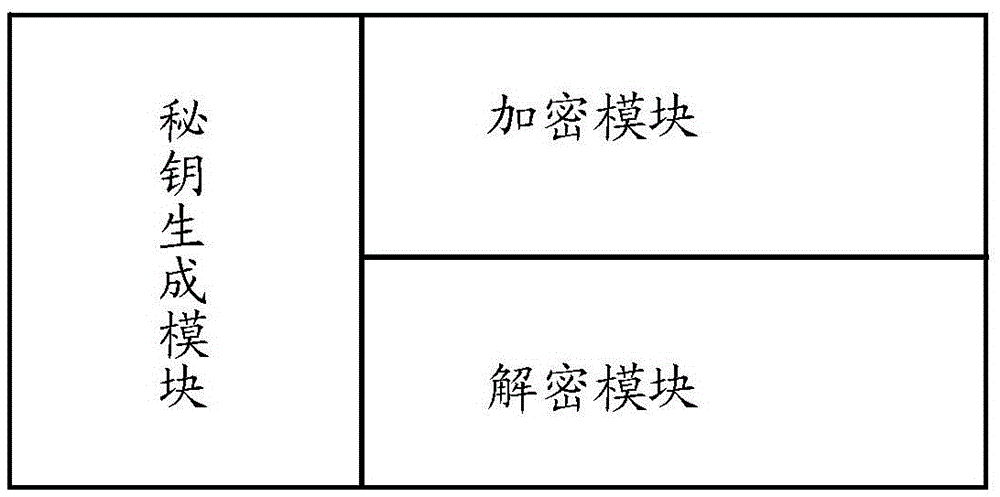
[0026] An embodiment of the present invention provides a processor for encryption and decryption, such as figure 1 As shown, it includes: a secret key ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com