Table-driven signature error detection algorithm
A technology of error detection and detection algorithm, applied in the direction of error detection/correction, calculation, software testing/debugging, etc., can solve problems such as illegal branches, and achieve the effect of improving coverage
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0030] The present invention will be described in detail below in conjunction with the accompanying drawings.
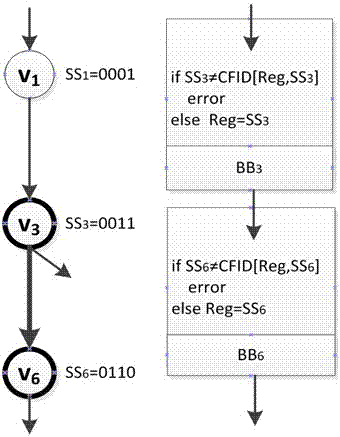
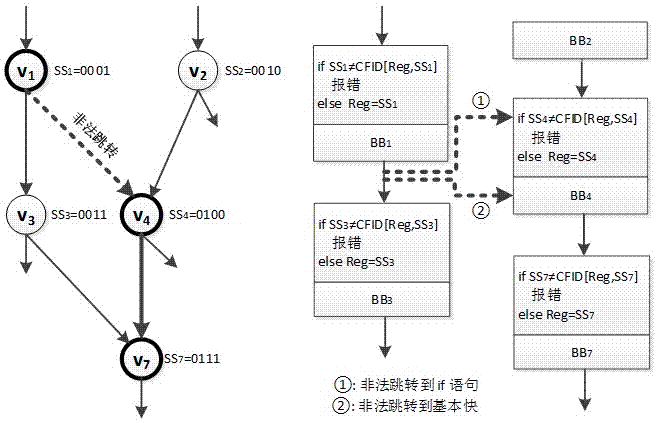
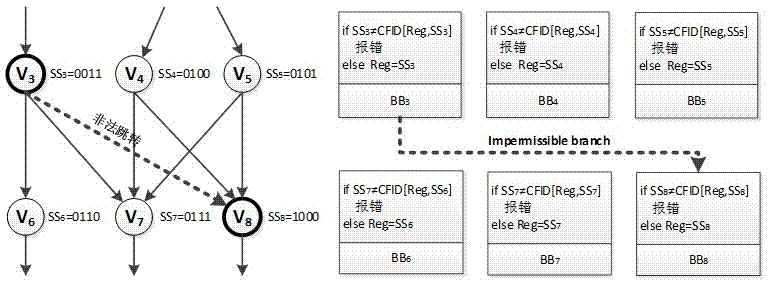
[0031] attached figure 1 is the detection of allowed execution branches without shared fan-in nodes, and all basic blocks in the figure have been identified and numbered. as attached figure 1 As shown on the left, each basic block is assigned a different value equal to its own position identifier. attached figure 1 The right side shows how the check instruction performs error detection. When the program executes to v3, the comparison of SS3 with CFID[Reg, SS3] shall be performed first before proceeding to execute the instructions in v3. Reg is a global variable used to store dynamic signatures, which are stored in allocated registers. If the equality relationship between SS3 and CFID[Reg, SS3] is established, that is, if brReg,3 is a legal branch, Reg will be updated to SS3, and the original instructions in the basic block will continue to be executed until the ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com