Method and system for achieving communication security protection
A technology of communication security and implementation method, applied in transmission systems and key distribution, can solve the problems of lack of end-to-end security protection, lack of visibility of IP data flow, etc., and achieve the effect of ensuring confidentiality
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
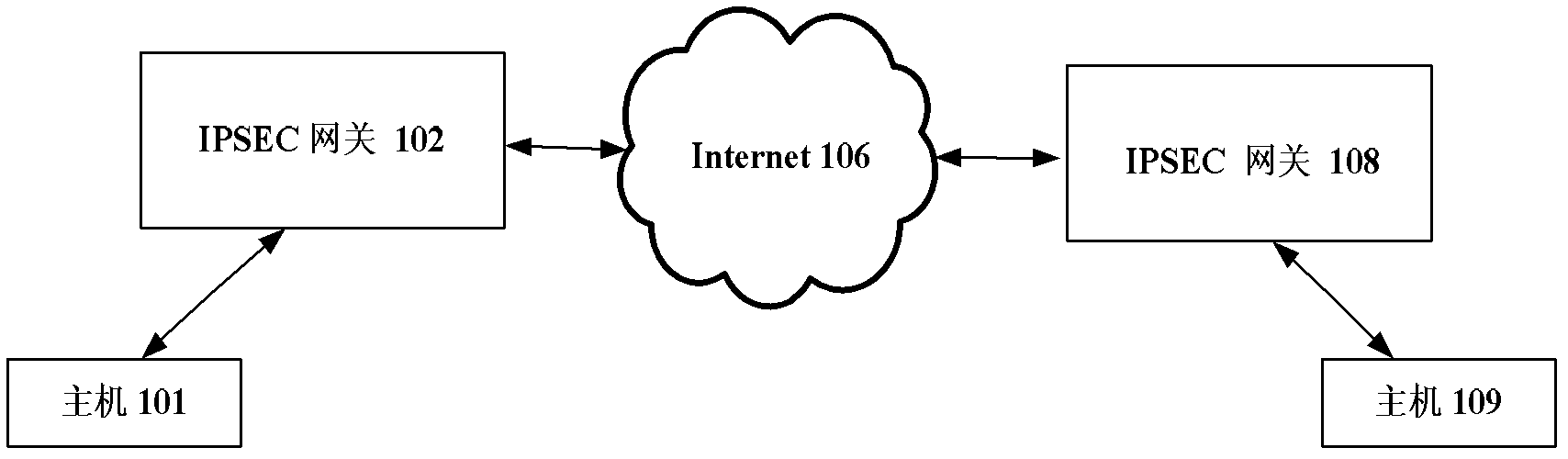
[0095] Figure 4 The process of establishing an IKE SA between the initiator host 101 and the gateway 102 is shown. The process of establishing IKE SA between initiator host 101 and gateway 102 is as follows: Figure 4 As shown, the specific description of the process is as follows:
[0096] Step 11 , the initiator host 101 sends an IKE_SA_INIT request to the gateway 102 .
[0097] In step 12, the gateway 102 sends an IKE_SA_INIT response to the initiator host 101.
[0098] Step 13, the initiator host 101 sends an IKE_SA_AUTH request to the gateway 102, including end-to-end security protection and visibility support payload and security association payload. The end-to-end security protection is used to indicate that the own party has end-to-end security protection and visibility support capabilities, and the security association payload is used to indicate to the gateway the set of security protocols and cryptographic algorithms supported by the own party.
[0099] In step...
Embodiment 2
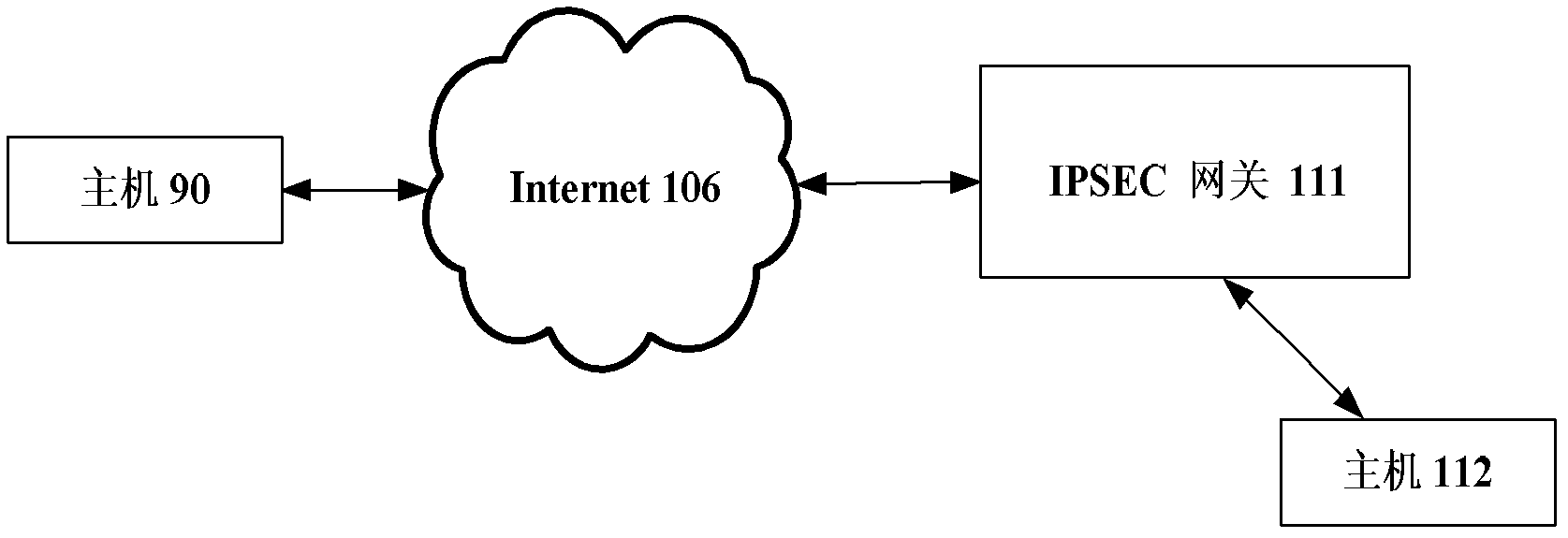
[0101] If the peer gateway in the host-gateway-gateway-host mode establishes an IPsec SA for the peer host, but the IKE SA with the peer host has not been established, it needs to establish the IKE SA first. Figure 5 Describes the process of establishing IKE SA between the peer gateway and the peer host, such as Figure 5 As shown, the specific description of the process is as follows:
[0102] In steps 21 and 22, both parties send IKE_SA_INIT request and response messages.
[0103] In step 23, the peer gateway 108 sends an IKE_SA_AUTH request to the peer host 109, and adds an end-to-end security protection and visibility support payload to the message, indicating that its own side has end-to-end security protection and visibility support capabilities.
[0104] Step 24, the peer host 109 sends an IKE SA AUTH response to the peer gateway 108, including end-to-end security protection and visibility support payload and security association payload.
[0105] In the remote host-...
Embodiment 3
[0107] This embodiment provides a process of establishing, updating and deleting an IPsec SA in a host-gateway-gateway-mode. In this embodiment, it is assumed that the IKE SA between the host 101 and the gateway 102, between the gateway 102 and the peer gateway 108, and between the peer gateway 108 and the peer host 109 has been established, such as Figure 6 As shown, the specific description of the process is as follows:
[0108] Step 201, the initiator host 101 sends an IPsec SA establishment request
[0109] Step 202, the gateway 102 sends a CREATE_CHILD_SA request to the peer gateway 108
[0110] In step 203 and step 204, the peer gateway 108 performs a survivability check on the peer host 109 . If no IKE SA is established between the peer gateway 108 and the peer host 109, use Figure 5 Steps 21-24 in replace steps 203 and 204.
[0111] Step 205, peer gateway 108 sends a CREATE_CHILD_SA response to gateway 102
[0112] In step 206 and step 206A, the gateway 102 and ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com