Identity authentication method and system and data transmission method and device based on same
A technology of a data transmission method and a data transmission device, which is applied in the field of devices, data transmission methods, identity authentication methods, and systems, can solve problems such as unfavorable secure communication between a client and a server, and achieve the effect of ensuring security and the security of an identity authentication method
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
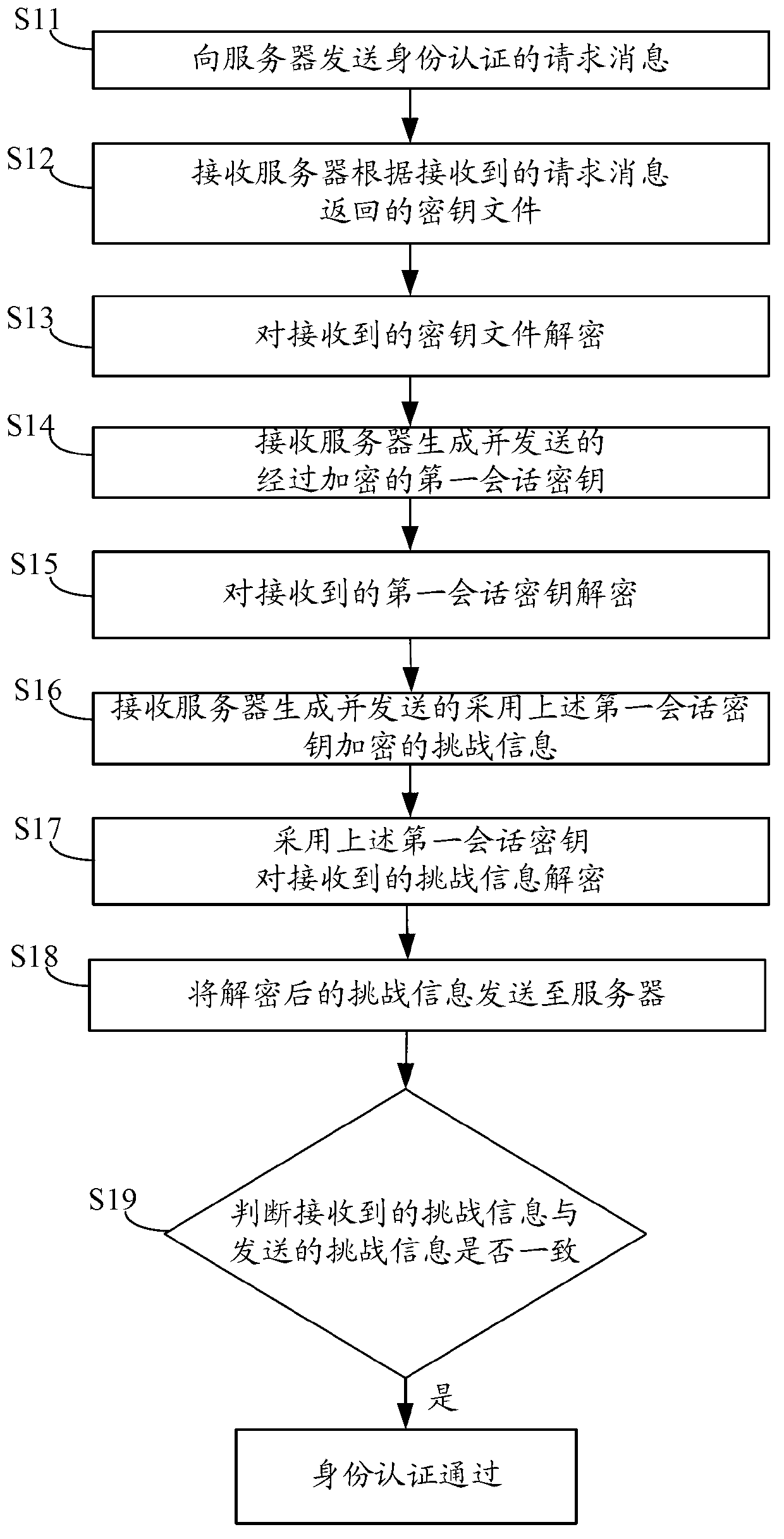
Examples
Embodiment 1
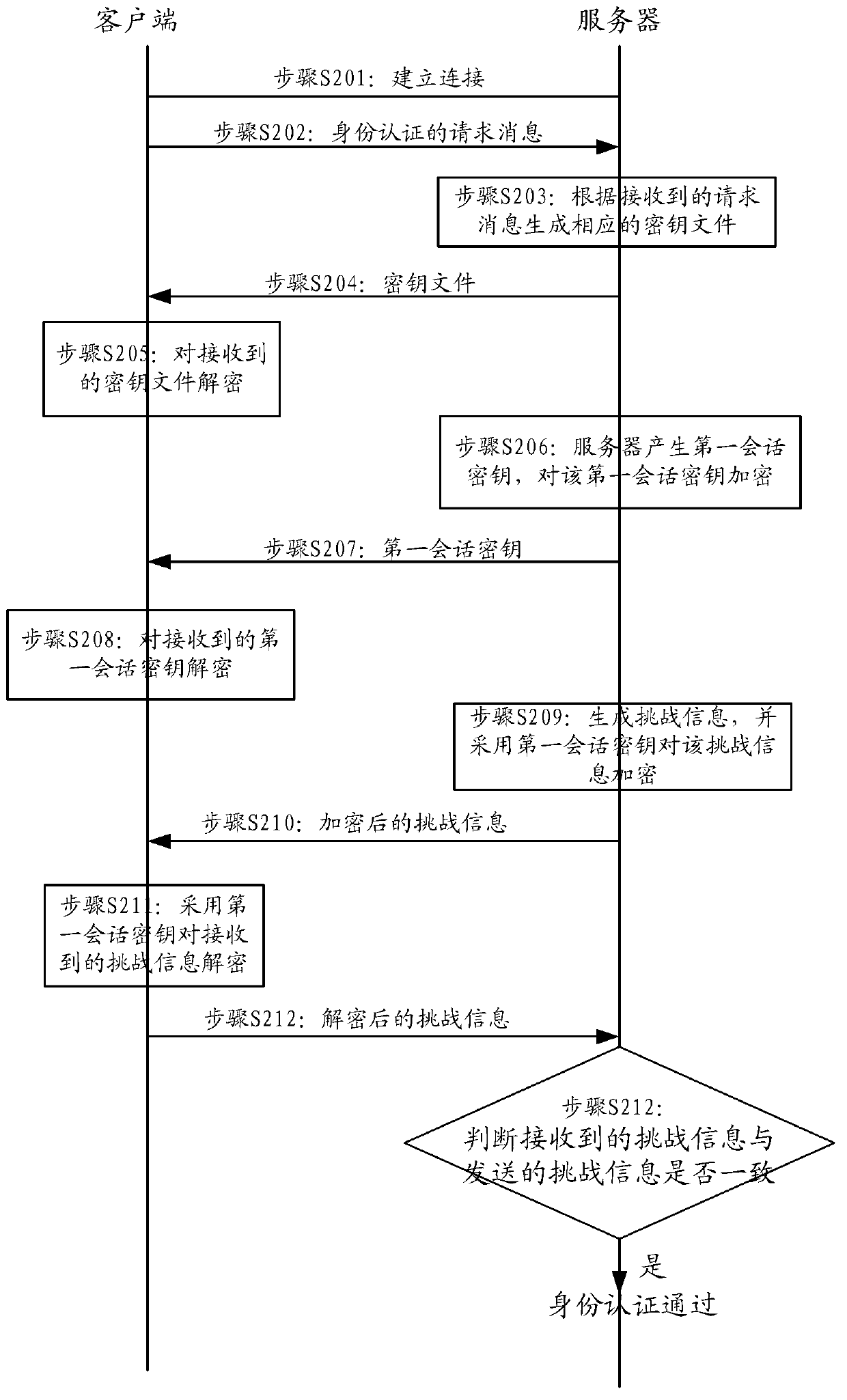
[0082] figure 2 It shows a schematic flowchart of an identity authentication method in Embodiment 1 of the present invention, and the method includes the following steps:
[0083] Step S201: the client establishes a connection with the server.
[0084] In the embodiment of the present invention, the client may be a VNC client, and the server may be a VNC server. Specifically, the client can establish an HTTP (Hypertext transport protocol, hypertext transfer protocol) connection or a Socket (socket) connection with the server, where the connection between the client and the server is only the client and the server can send messages to each other The state is not the state where the client and the server send data and communicate with each other.
[0085] Step S202: the client sends an identity authentication request message to the server.
[0086] Step S203: The server generates a corresponding key file according to the received request message.
[0087] After the server r...
Embodiment 2
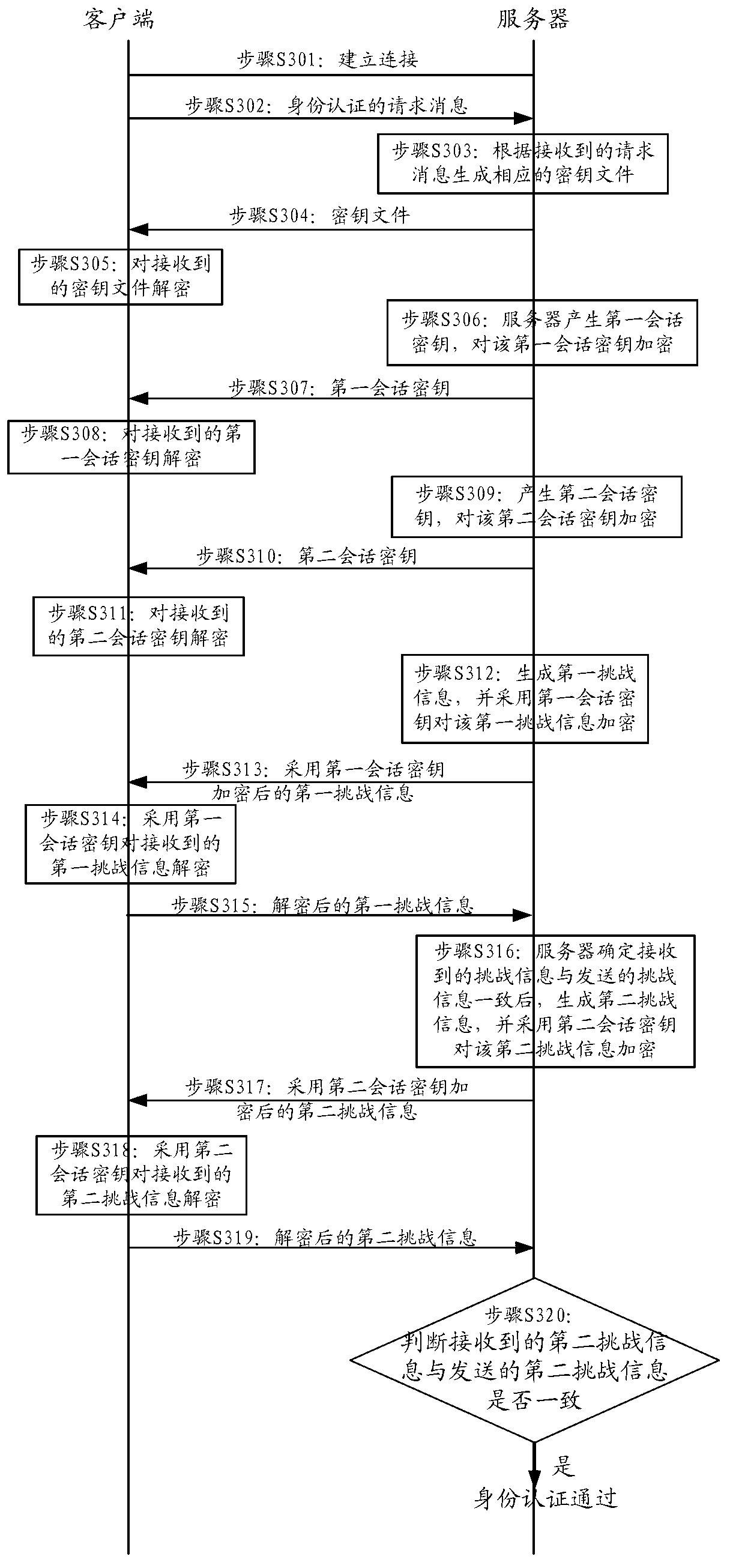
[0108] image 3 It shows a schematic flowchart of the method for identity authentication in Embodiment 2 of the present invention, and the method includes the following steps:
[0109] It should be noted that steps S301 to S308 in the second embodiment are the same as steps S201 to S208 in the first embodiment, and will not be repeated here. For related content, please refer to the description in the first embodiment.
[0110] Step S309: the server generates a second session key, and encrypts the second session key.
[0111] After sending the first session key to the client, the server can generate a second session key through a random function, and encrypt the second session key with a public key (such as an RSA public key).
[0112] Further, the server can also obtain the length z of the second session key, and the function defining the length of the second session key can be N(z), wherein the function N(z) can be a linear function, preferably the function N(z ) can be a n...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com