Enterprise information security management system and method
A technology for enterprise information and security management, applied in transmission systems, digital transmission systems, electrical components, etc., can solve problems such as high requirements for network administrators, complex implementation, and inconvenience for network administrators, and achieve simple network security management and reduced costs and complexity, the effect of reducing complexity
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
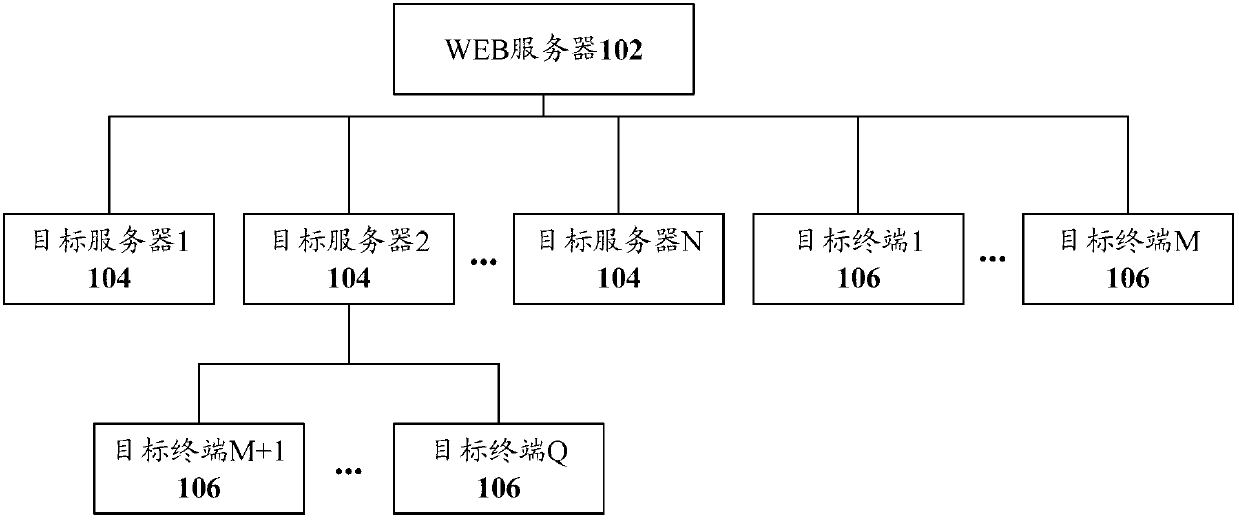
[0032] refer to figure 1 , shows a structural block diagram of an enterprise information security management system according to Embodiment 1 of the present invention.
[0033] The enterprise information security management system of this embodiment is set in the enterprise intranet, and the system includes: a WEB server 102 of the enterprise intranet, a target server 104 of the enterprise intranet, and a target terminal 106 of the enterprise intranet. Generally speaking, the enterprise information security management system includes both the target server 104 and the target terminal 106 , but is not limited thereto. In some cases, it may only include the target server 104 or only the target terminal 106 .
[0034] in,
[0035] The WEB server 102 is used to receive the enterprise information security management instruction input by the user through the WEB page, and determine the target server and / or target terminal of the enterprise information security management instructio...
Embodiment 2
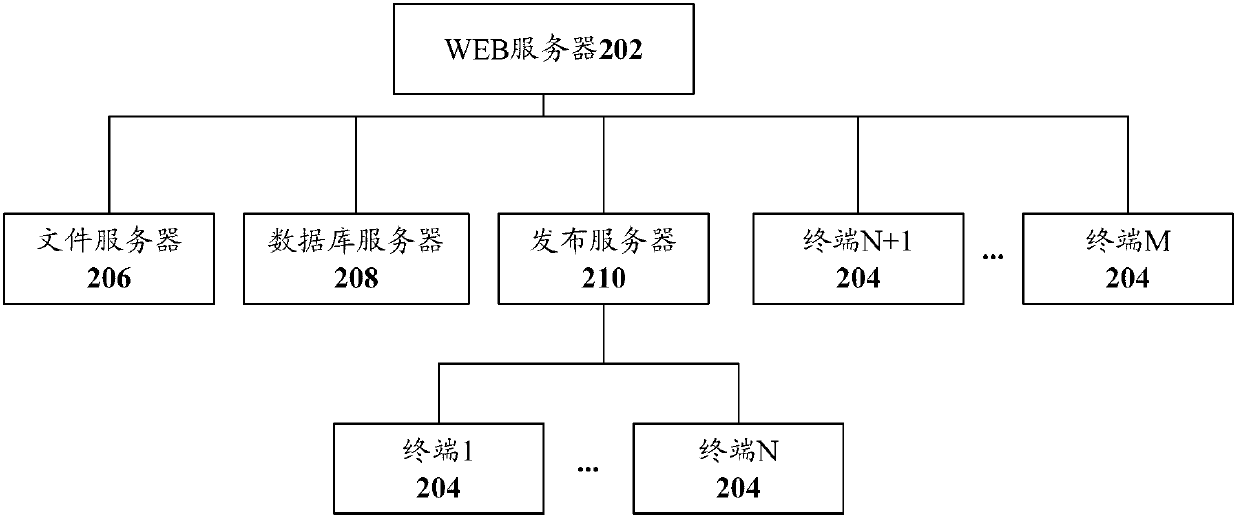
[0041] refer to figure 2 , shows a structural block diagram of an enterprise information security management system according to Embodiment 2 of the present invention.
[0042] The enterprise information security management system of this embodiment is set in the enterprise intranet, and the system includes a file server 206, a database server 208, and a publishing server 210 in addition to a WEB server 202 and a plurality of terminals 204. It should be noted that, in this embodiment, the file server 206, the database server 208, and the publishing server 210 exist at the same time, but in practical applications, one or some of them can be selected as needed, and of course, more can also be set as needed. server, and can implement corresponding enterprise information security management functions with reference to this embodiment. Each of the foregoing servers in this embodiment may include one or more.
[0043] In the enterprise information security management system of th...
Embodiment 3
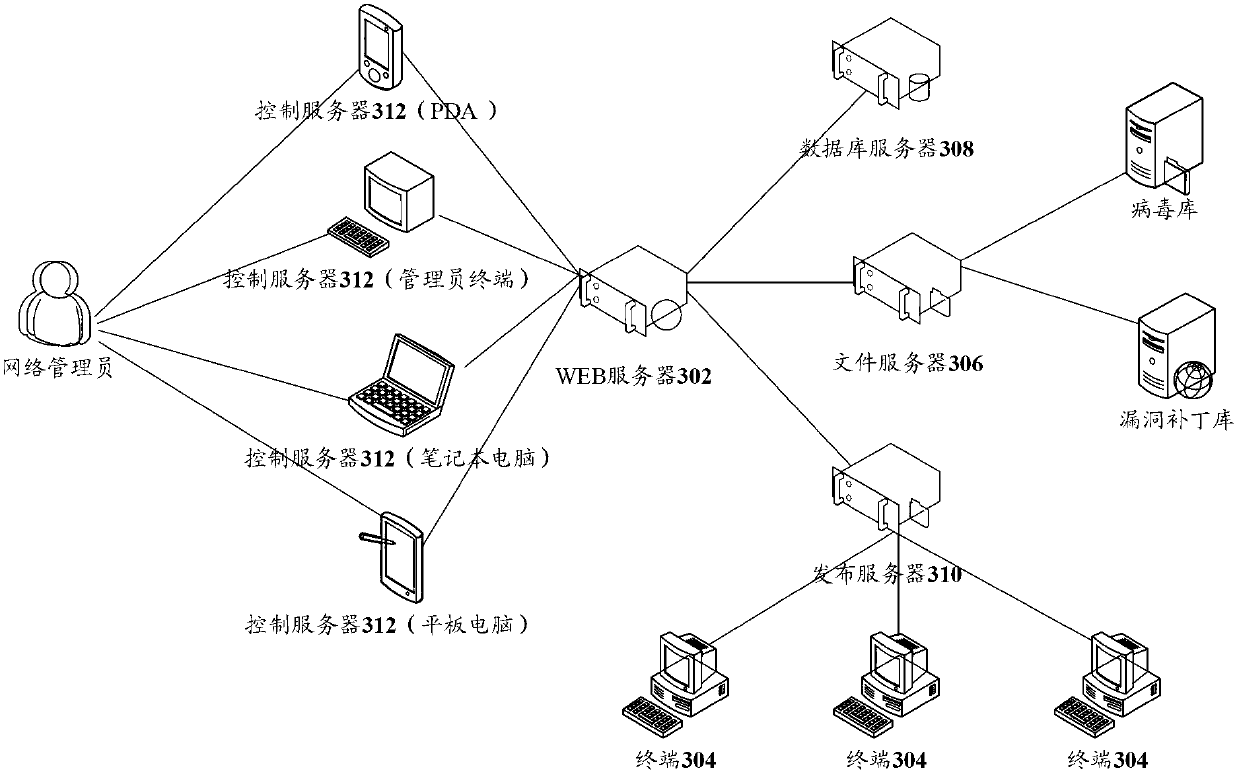
[0057] refer to image 3 , shows a schematic structural diagram of an enterprise information security management system according to Embodiment 3 of the present invention.
[0058] The enterprise information security management in this embodiment is set in the enterprise intranet, and the system includes: WEB server 302 , multiple terminals 304 , file server 306 , database server 308 , publishing server 310 , and control server 312 .
[0059] Such as image 3 As shown, the file server 306 , the database server 308 , the distribution server 310 , and the control server 312 are all connected to the WEB server 302 , and a plurality of terminals 304 are connected to the distribution server 310 .
[0060] In this embodiment, the control server 312 accesses the WEB server 302, presents the enterprise information security management page to the user, for the user (the network administrator in this embodiment) to input the enterprise information security management instruction, and t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com