Algorithm hardware realizing method for improving network safety
A hardware implementation and security technology, applied in network topology, security devices, electrical components, etc., can solve problems such as large circuit implementation area and power consumption, unsatisfactory calculation speed, and restrictions on encryption and decryption methods, so as to reduce the implementation area , easy to implement, and conducive to verification
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
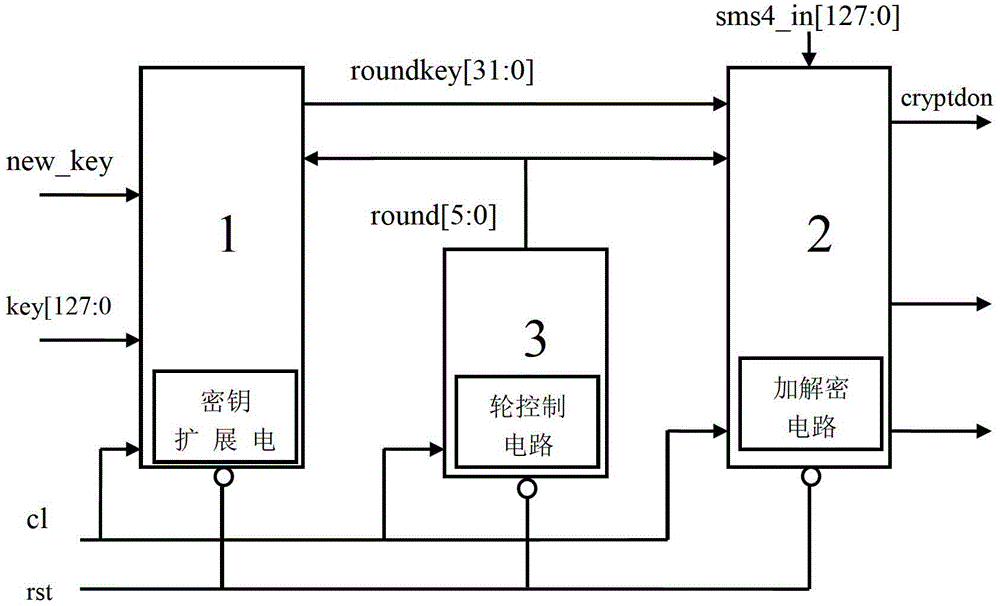
[0033] Embodiment: a kind of algorithm hardware implementation method for improving network security comprises the following steps:
[0034] Encryption process:
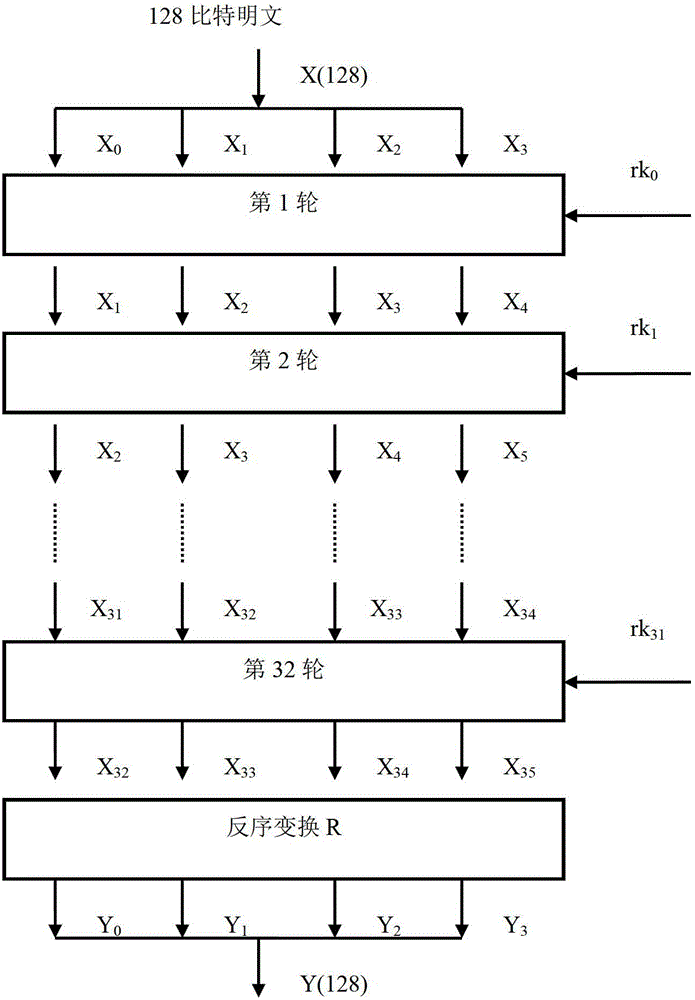
[0035] Step 1: Divide the plaintext code into 4 code words in units of words, and divide the master key code into 4 key words in units of words.
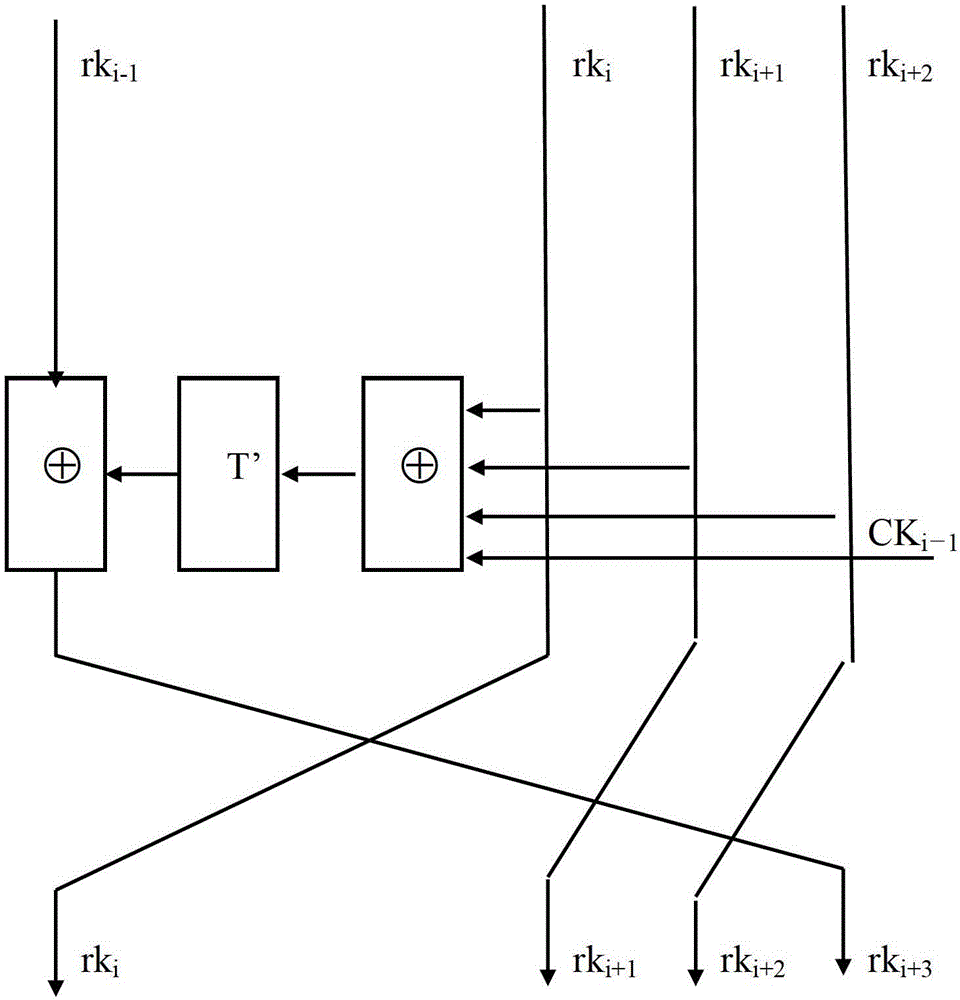
[0036] Step 2. XOR the 1st to 3rd key word in the master key with a constant, then perform reversible transformation, and then XOR with the 0th key word to generate a word-length For the first round of keys, move the 1st to 3rd key word forward to the position of the 0th to 2nd key word, and move the first round key to the 3rd position The location of the key word.
[0037] Step 3: XOR the first-round key with the plaintext code from the 1st to 3rd coded word, perform reversible transformation, and then XOR with the 0th coded word to generate a word-length The first round of cipher text, then move the first to the third code word to the position of the 0th to the second...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com