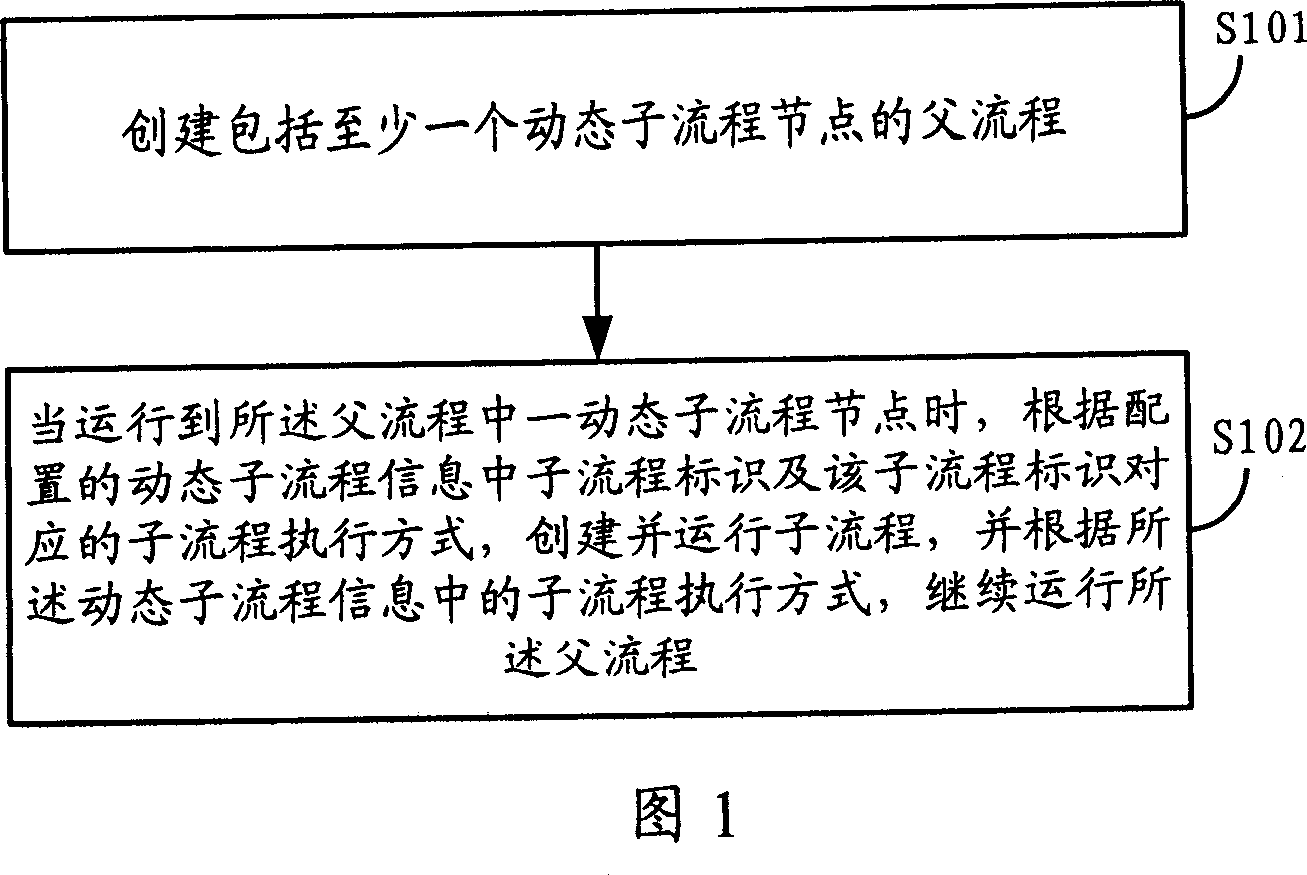
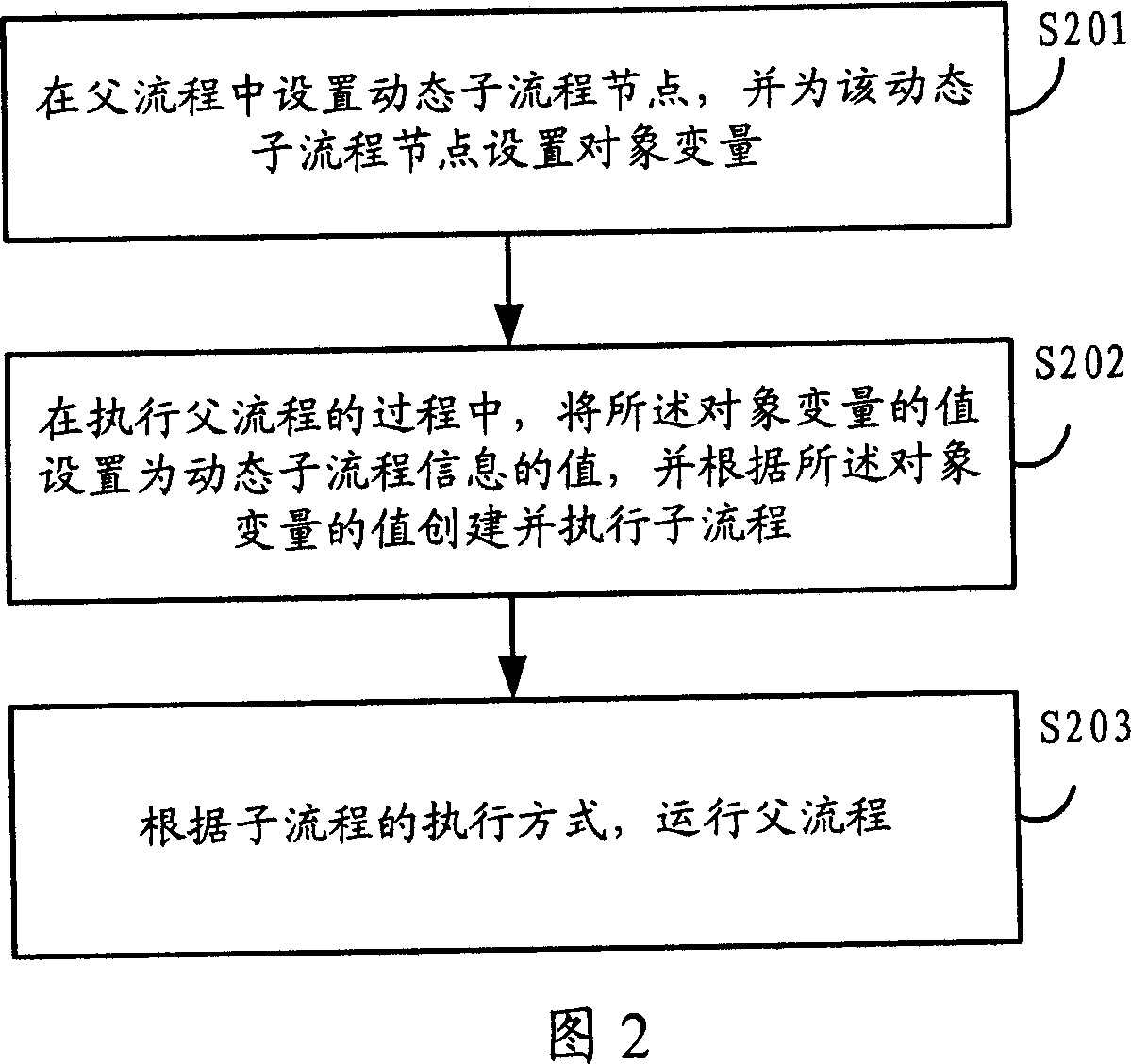
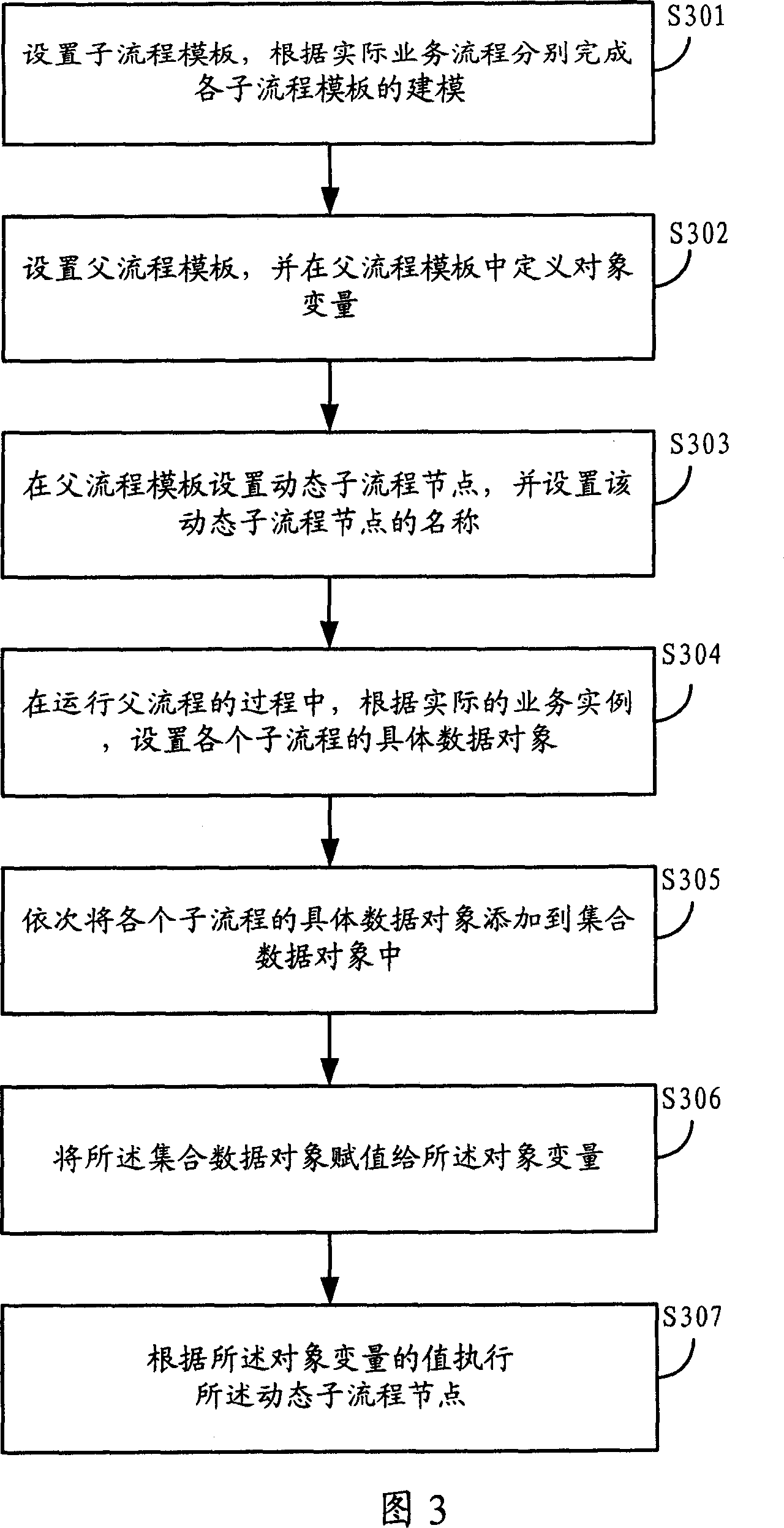
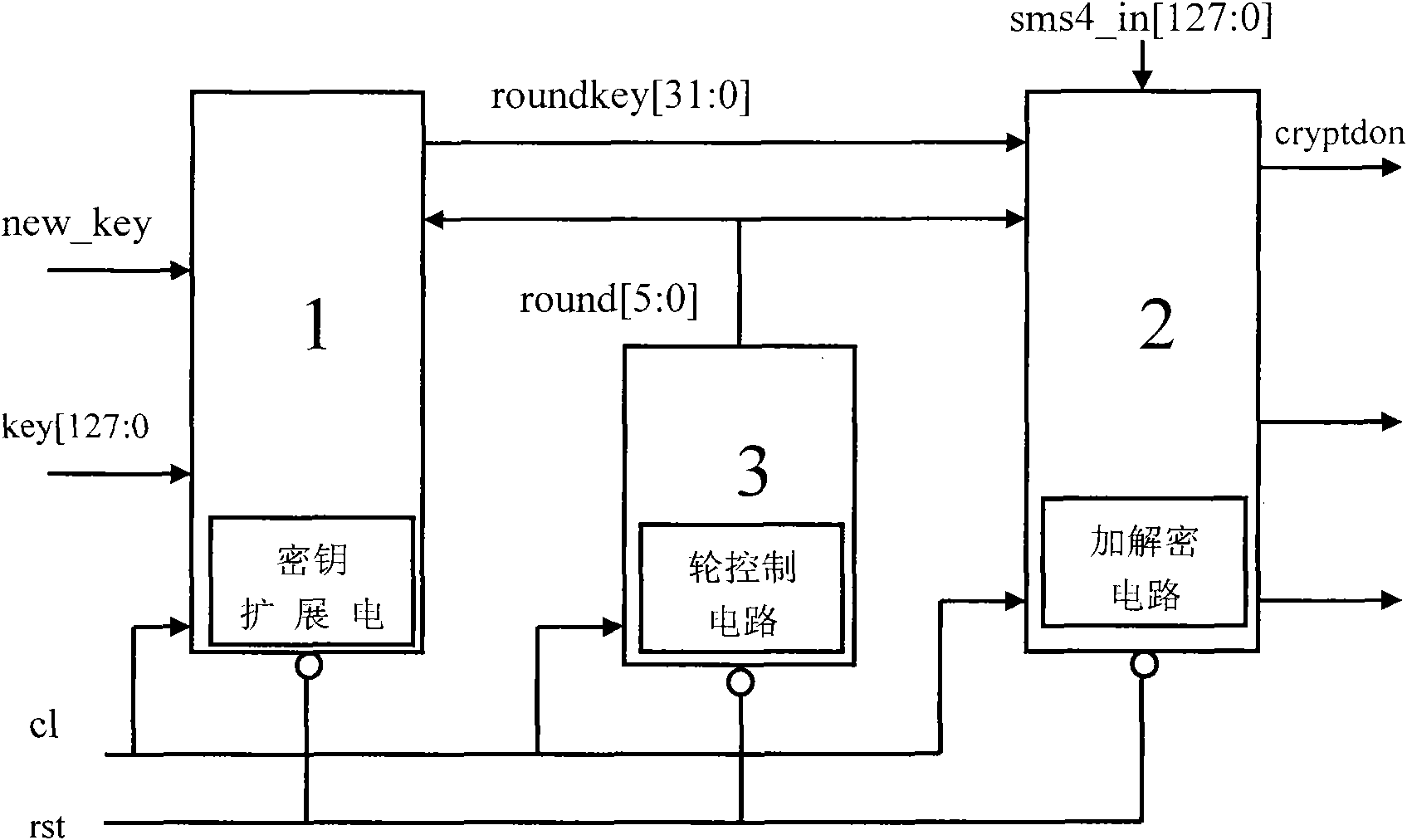
Patents
Literature
40results about How to "Achieve flexibility and convenience" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
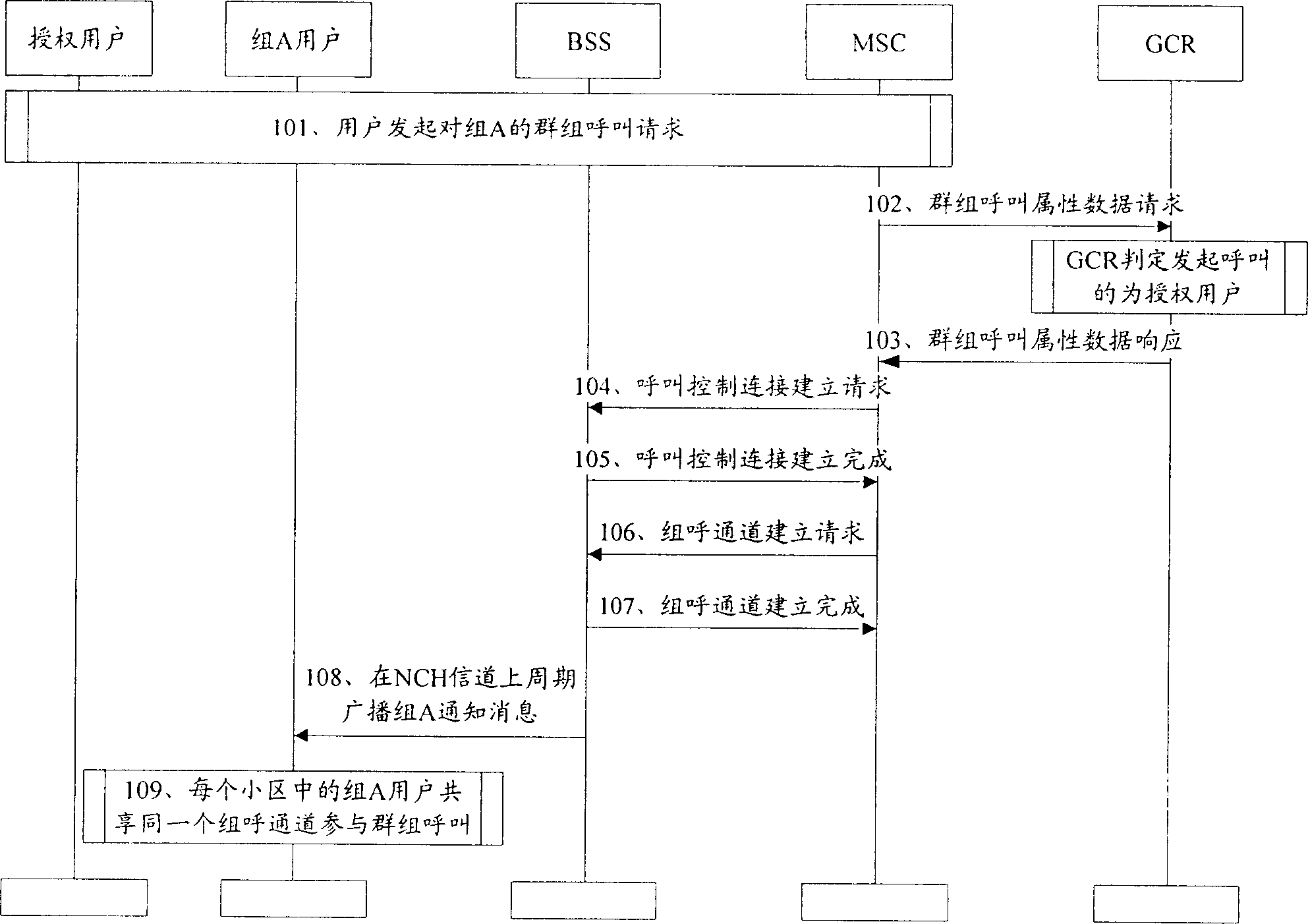
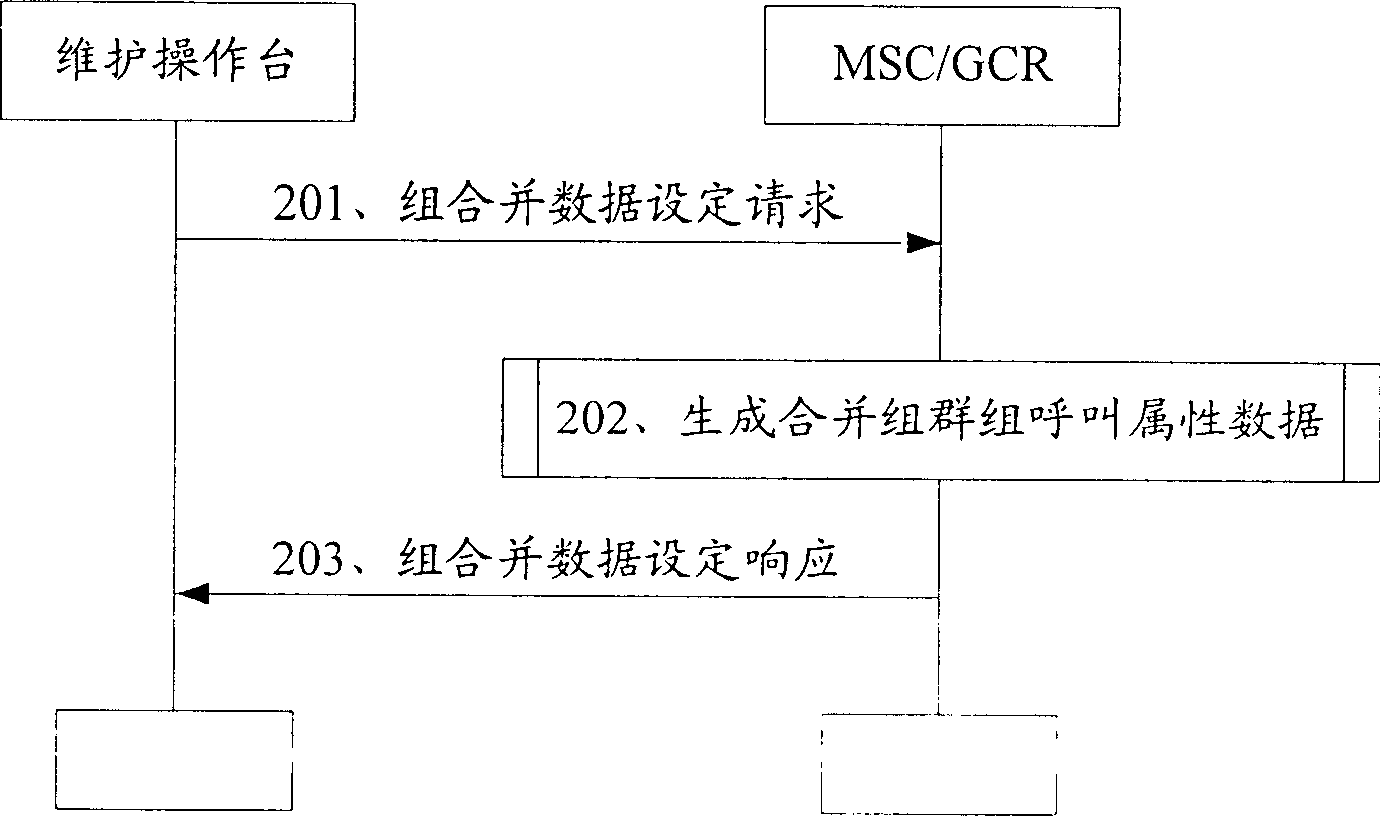
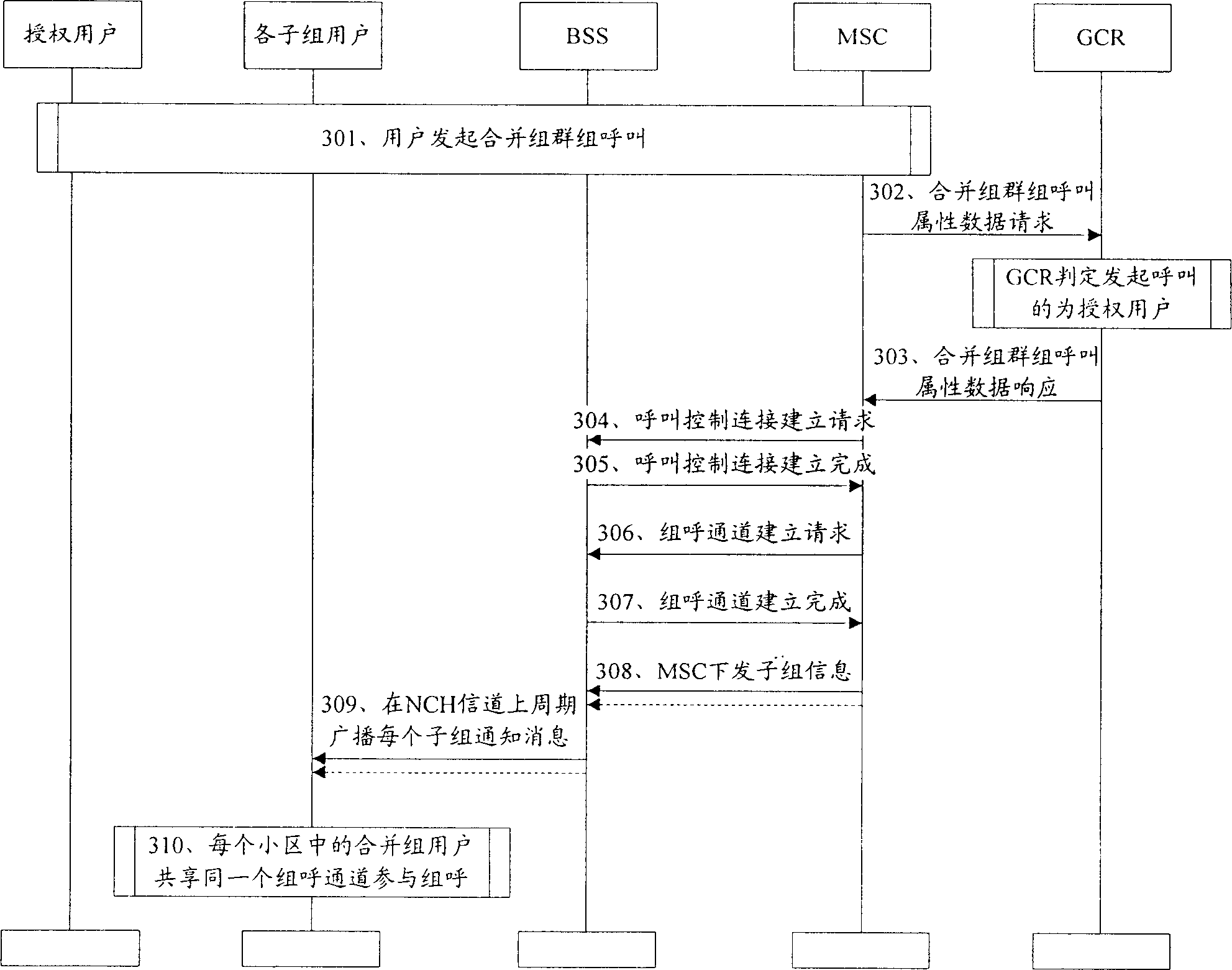
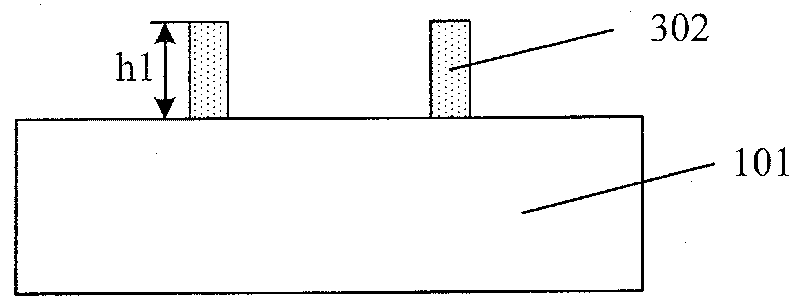
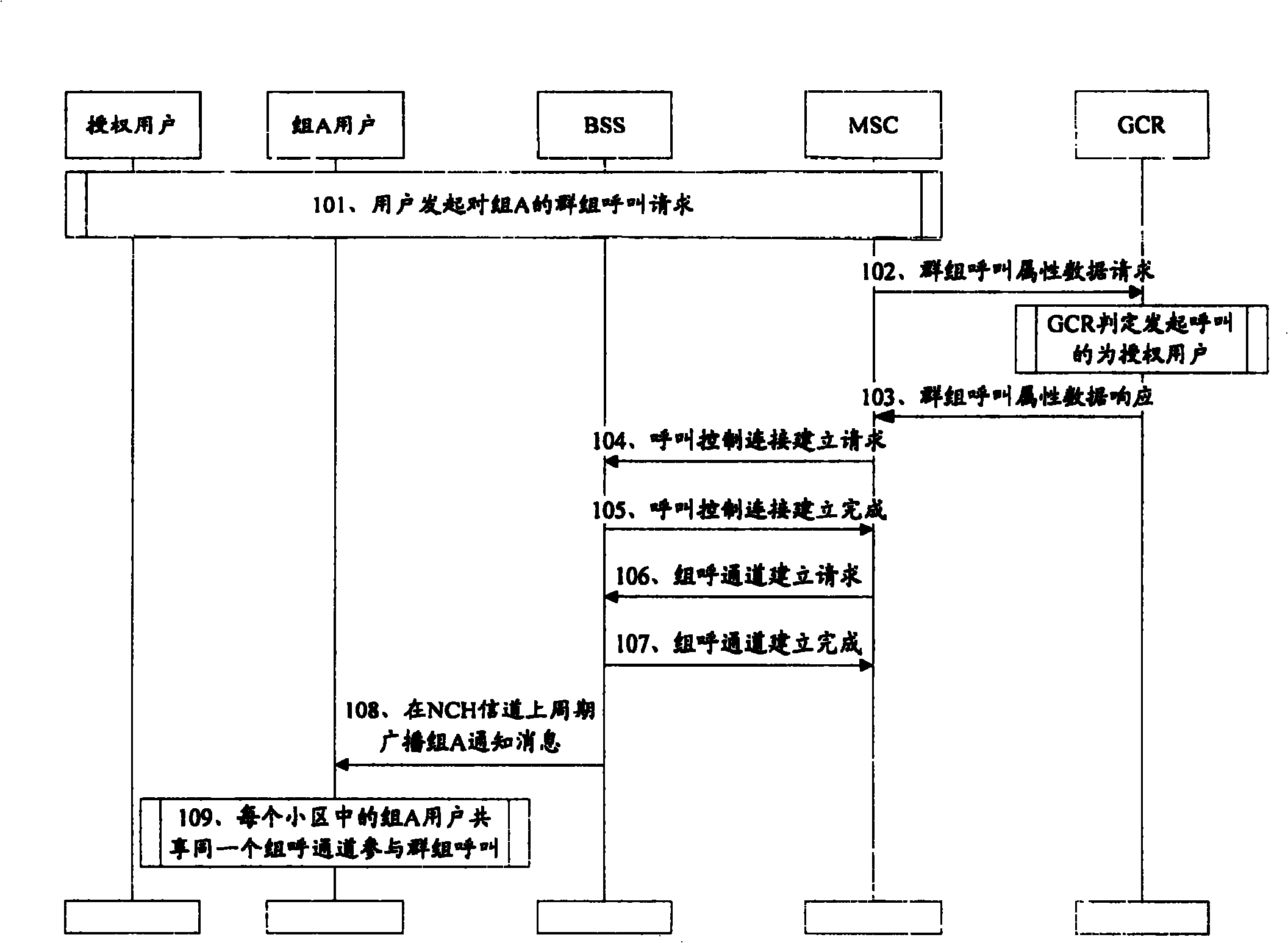
Method for realizing cluster call merging
InactiveCN1859637AEasy to implementMeeting Joint Communications NeedsRadio/inductive link selection arrangementsTelecommunicationsSpeech sound
The present invention discloses realizing groups calling merged method. It contains network side pre-establishing mergence group containing at least one subgroup, saving mergence group and subgroup message, user terminal sending mergence group groups calling request carrying mergence group information to network side, network side according to mergence group message obtaining said mergence subgroup message from stored message; network side sending relevant subgroup information carried groups calling notification message in cell, any subgroup user terminal according to said groups calling notification message accessing groups call channel, to participate groups calling. Said invented method make having different group ID user capable of making speech communication in same mergence groups calling.
Owner:HUAWEI TECH CO LTD
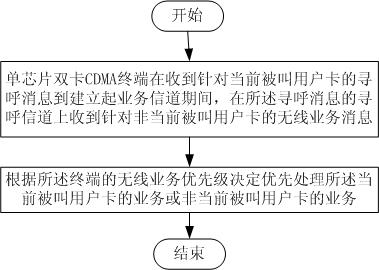
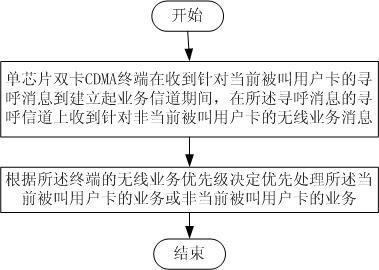
Management method for wireless service of single-chip dual-card CDMA terminal and CDMA terminal
InactiveCN102026374AImprove performanceEnsure reasonable schedulingWireless communicationProtocol for Carrying Authentication for Network AccessSingle chip
The invention discloses a management method for the wireless service of a single-chip dual-card CDMA terminal and a CDMA terminal, wherein the method comprises the following steps of: during a period from receiving a paging message corresponding to the current called subscriber card to establishing a service channel by the single-chip dual-card CDMA terminal, determining to process the service of the current called subscriber car or a service of a non-current called subscriber card according to wireless service priority of the terminal when the single-chip dual-card CDMA terminal receives a wireless service message corresponding to the non-current called subscriber card on the paging channel of the paging message. In the management method for the single-chip dual-card CDMA terminal wireless service and the CDMA terminal, by setting the wireless service priority of the terminal and using the single-mode dual-card and dual-standby called service priority management implemented by the prior protocol rules, rational scheduling of the single-chip dual-card CDMA terminal to a dual subscriber card service is ensured, regular operation of the called functions of the terminal in steady and efficient state is guaranteed, and performance of the terminal is improved.
Owner:ZTE CORP
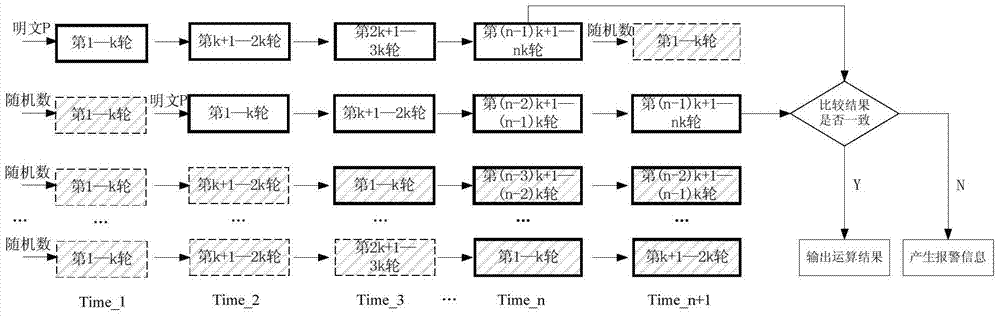
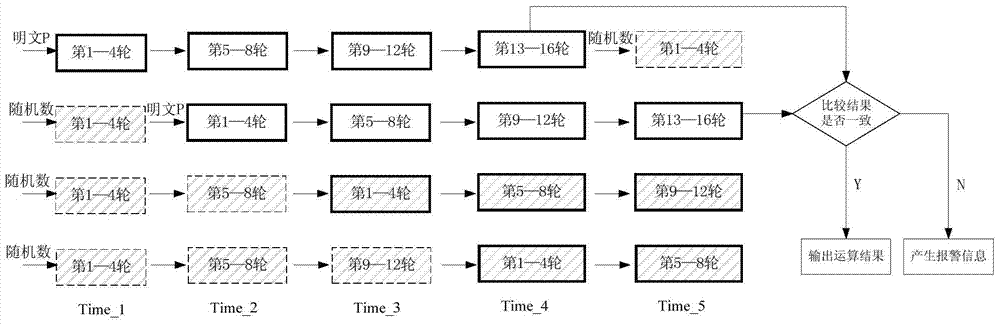
Protection method for side channel attack and fault attack
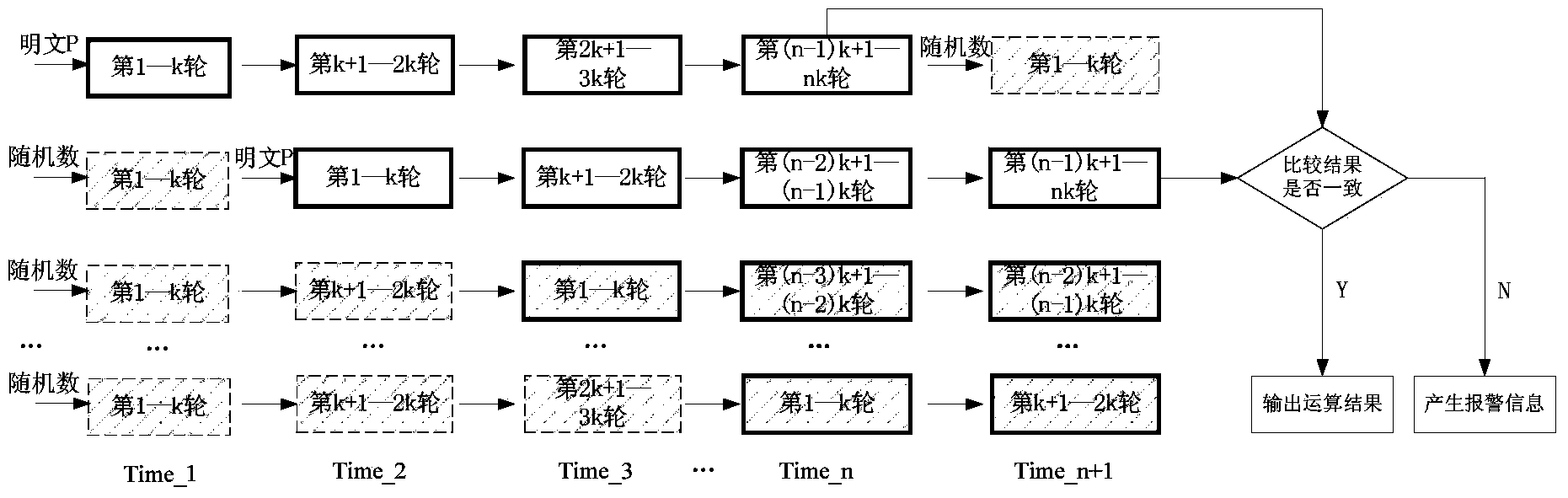
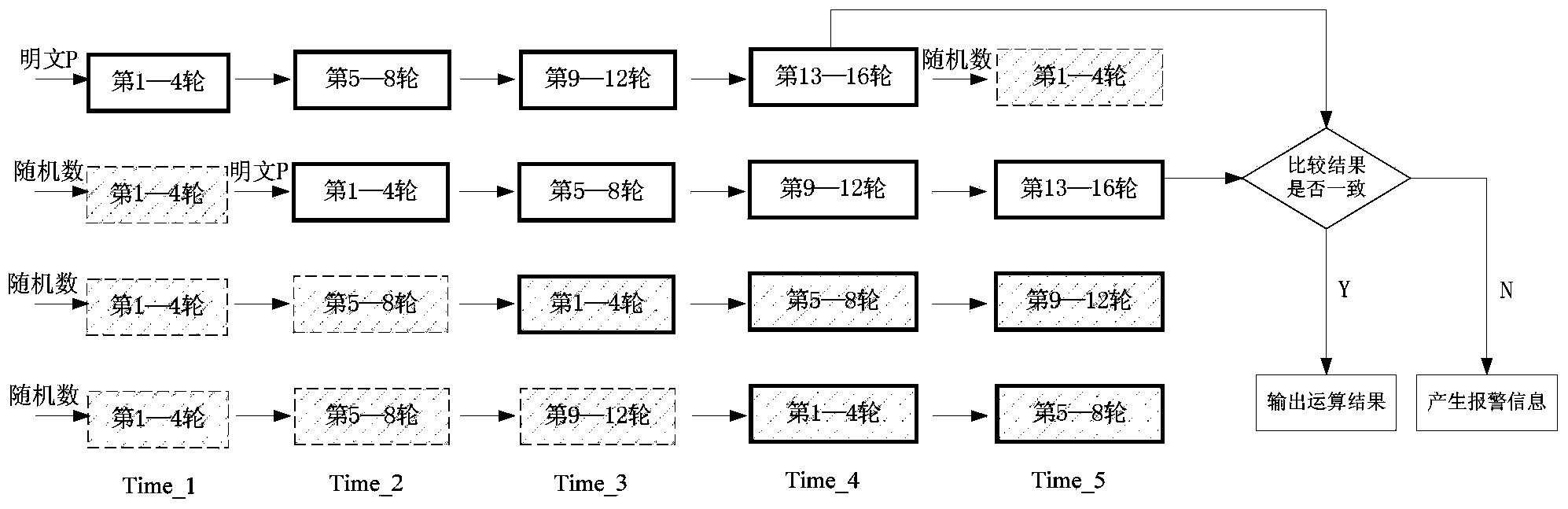
ActiveCN103634102AStrong securityImprove execution efficiencyEncryption apparatus with shift registers/memoriesSide channel attackPlaintext
The invention provides a protection method for side channel attack and fault attack. The protection method comprises the following steps of I. dividing operation of block cipher algorithm into a plurality of stages of pipelines; II. inputting real plaintext into two stages of pipelines selected at random, and inputting random number into other stages of pipelines; III. carrying out operation, and then comparing whether the operation results of the two real data are consistent after the operation is finished. The protection method can resist both side channel attack and fault attack, and has strong safety and high execution efficiency.
Owner:STATE GRID CORP OF CHINA +4
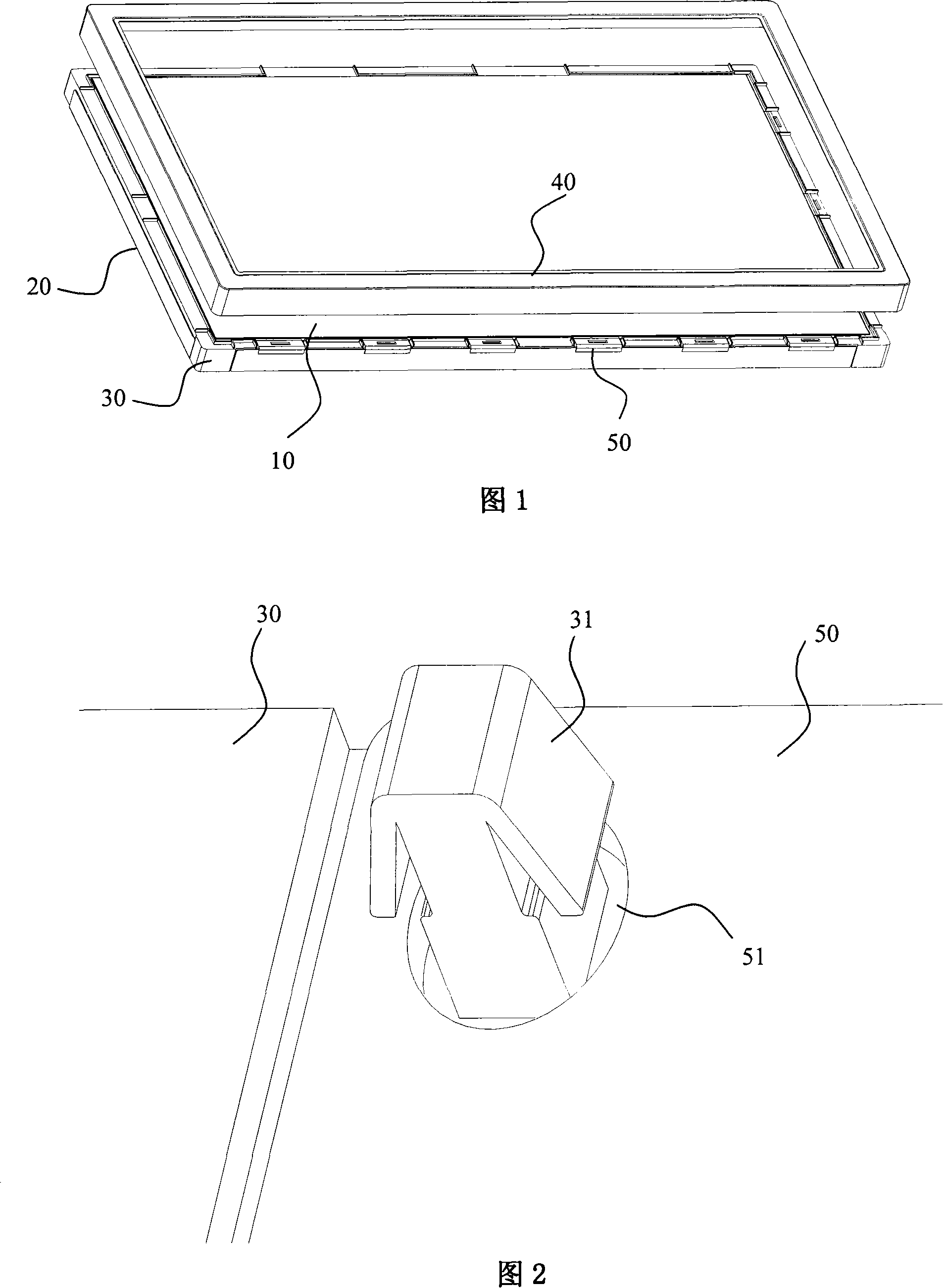
LCD display module
InactiveCN101149495ASolve assembly problemsEasy to assemblePrinted circuit detailsStatic indicating devicesLiquid-crystal displayEngineering
This invention discloses a sort of liquid crystal display die set. It consists of a backboard, a first framing which is laid in this backboard, a second framing which is covered in the first framing, a liquid crystal display panel which is laid in the first framing, a PCB plate which is fixed in the first framing. This first framing has the grab, and this PCB plate has the clip core which corresponds to the grab. This invention adopts the grab orientation configuration to fix the PCB plate, it solves the assemblage problem and the resolving problem of the PCB plate effectively, it predigests the assemblage, and it saves the production time and the manpower cost.
Owner:上海广电光电子有限公司
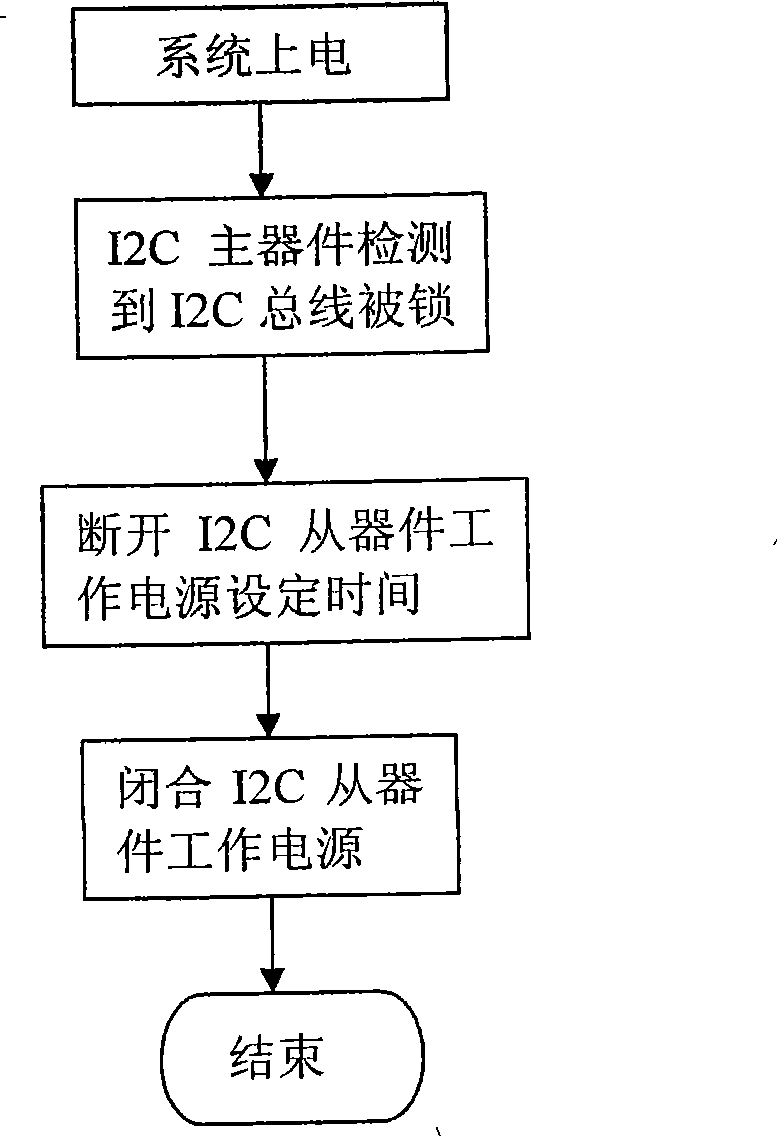
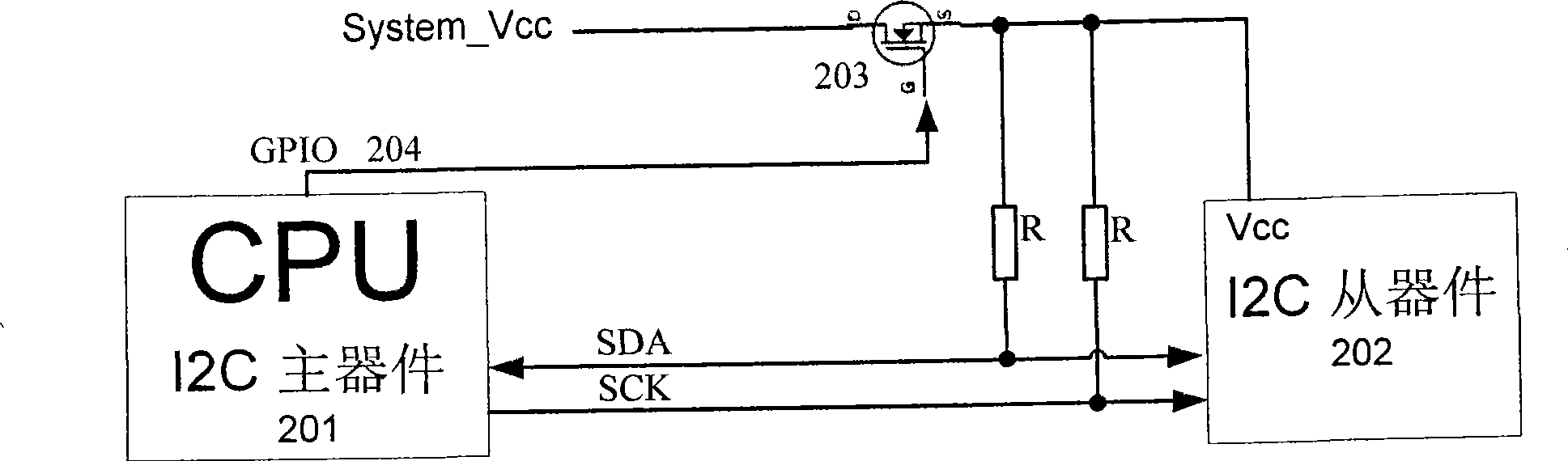
Method and apparatus for recovering I2C bus locked by slave device
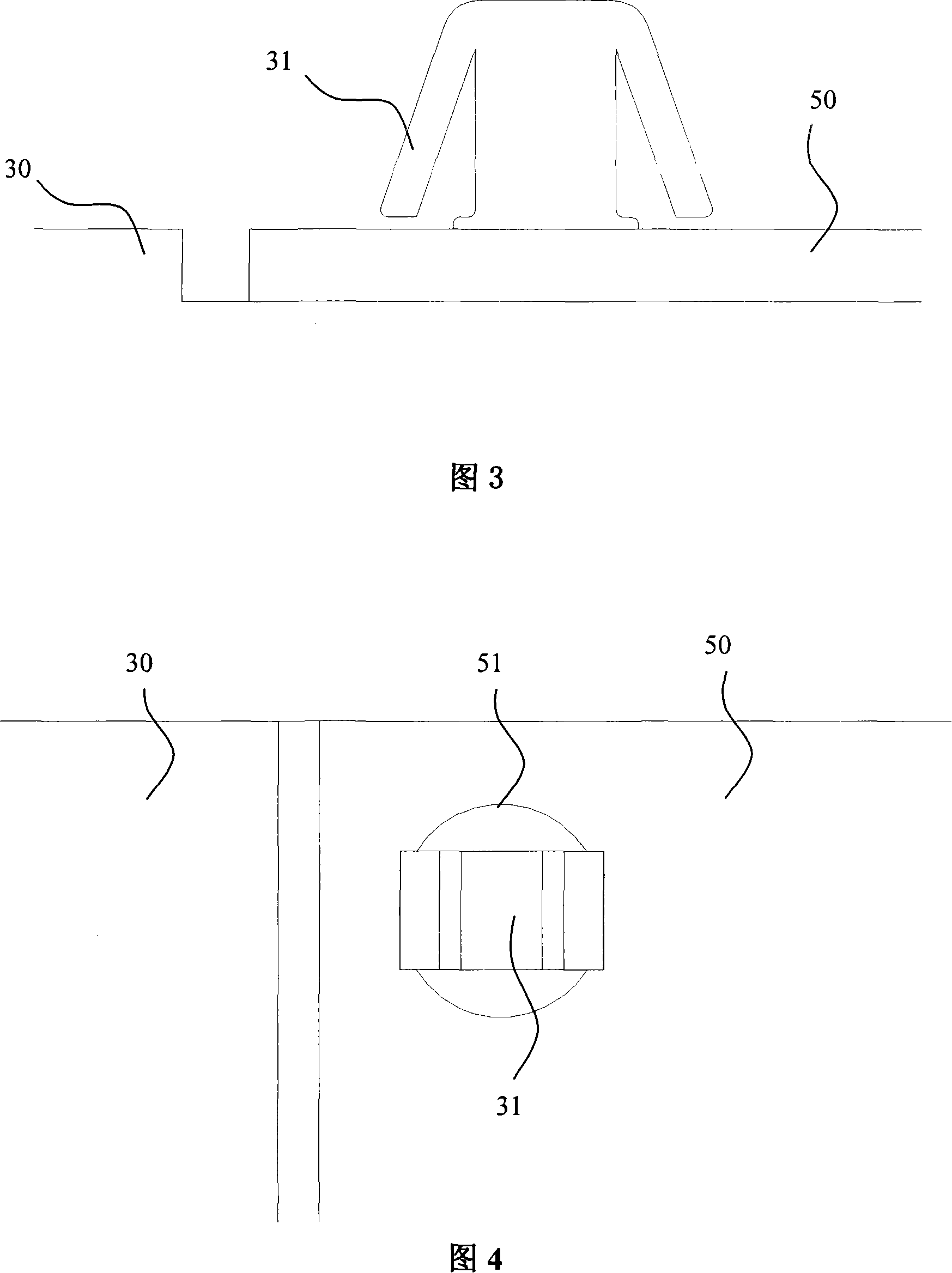
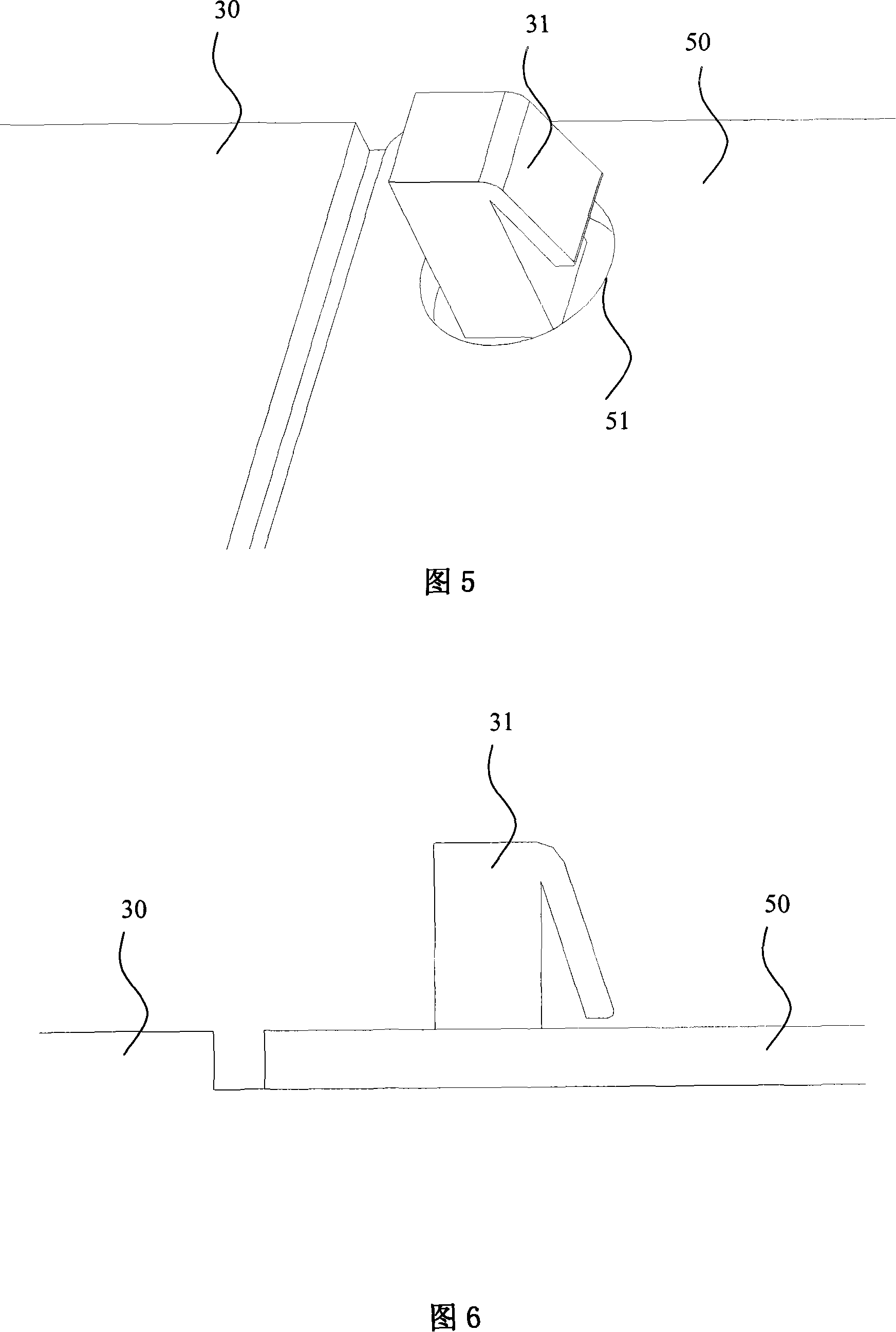
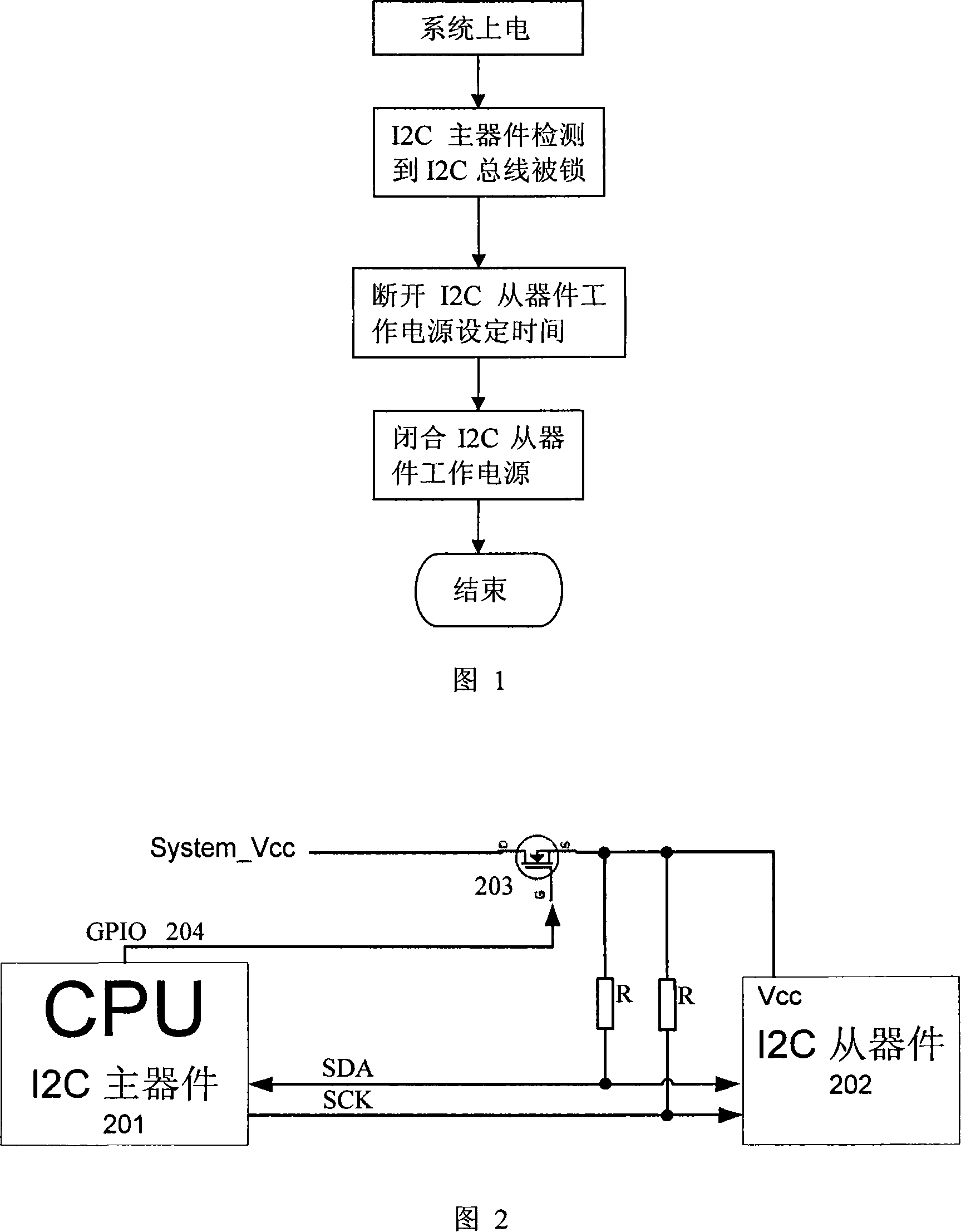
ActiveCN101118528ATroubleshoot recovery issuesLow costElectric digital data processingRestoration methodEngineering
The present invention relates to a resume device and a resume method when the I2C bus is locked by slave I2C components. The resume method when the I2C bus is locked by the I2C slave components is that using main I2C components to control the work power source of all the slave I2C components, when the main I2C components detects that the bus is locked, then the main I2C components cut off the work power source of the slave I2C components, and resume the power supply after a set time, and then the slave I2C components resume the initial state. The resume device includes main I2C components, slave I2C components and system power source, and a power source switch is also added, one end of the power source connects with the system power source, and the other end of the power source connects with the slave I2C components power sources which are connected together, and the main I2C components control the on-off of the poser source switch. With the participation of the main CPU, the resume problem of the bus after the slave I2C components lock the bus is solved, and the stability and the reliability of the system are improved.
Owner:ZTE CORP
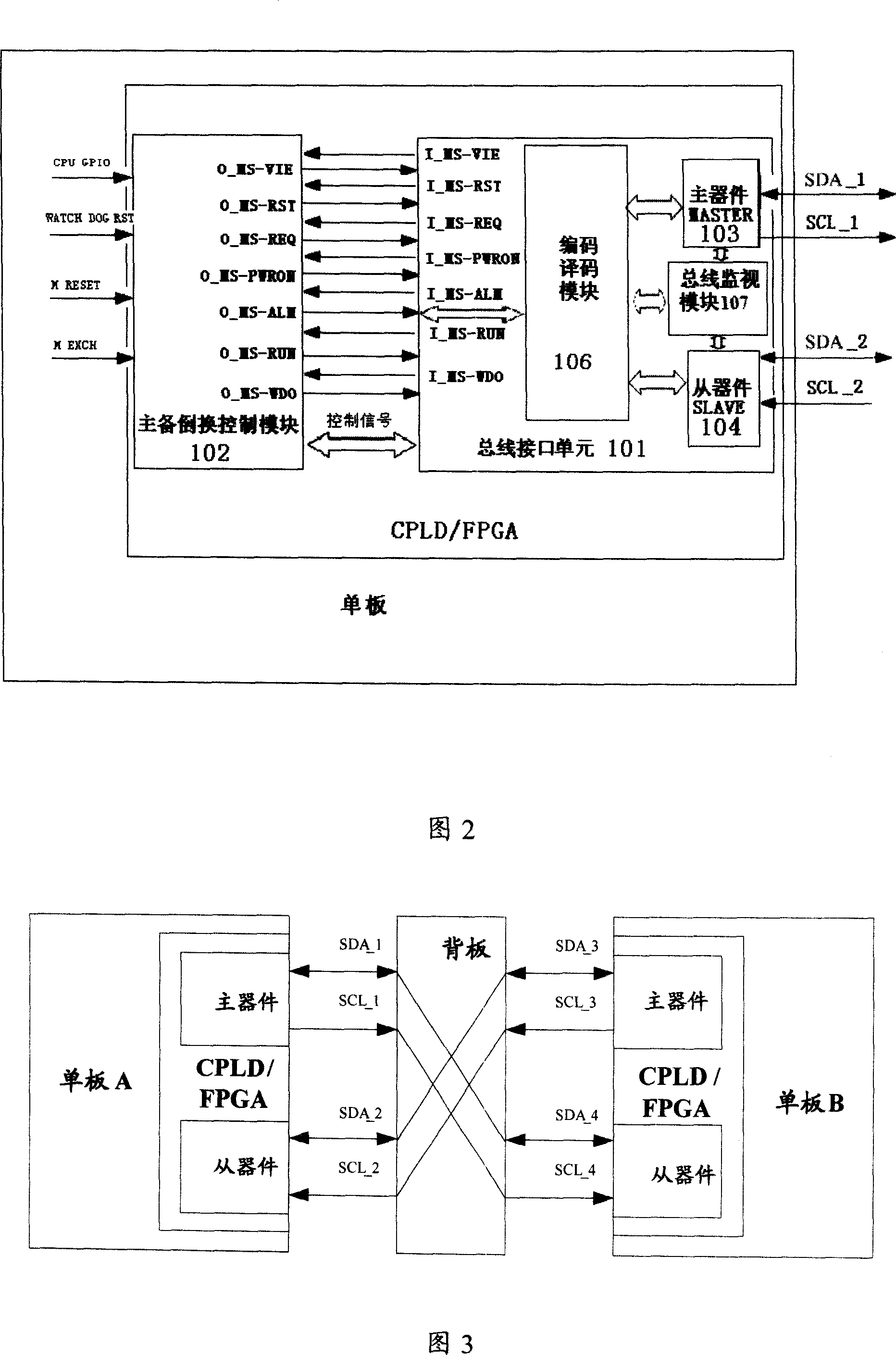
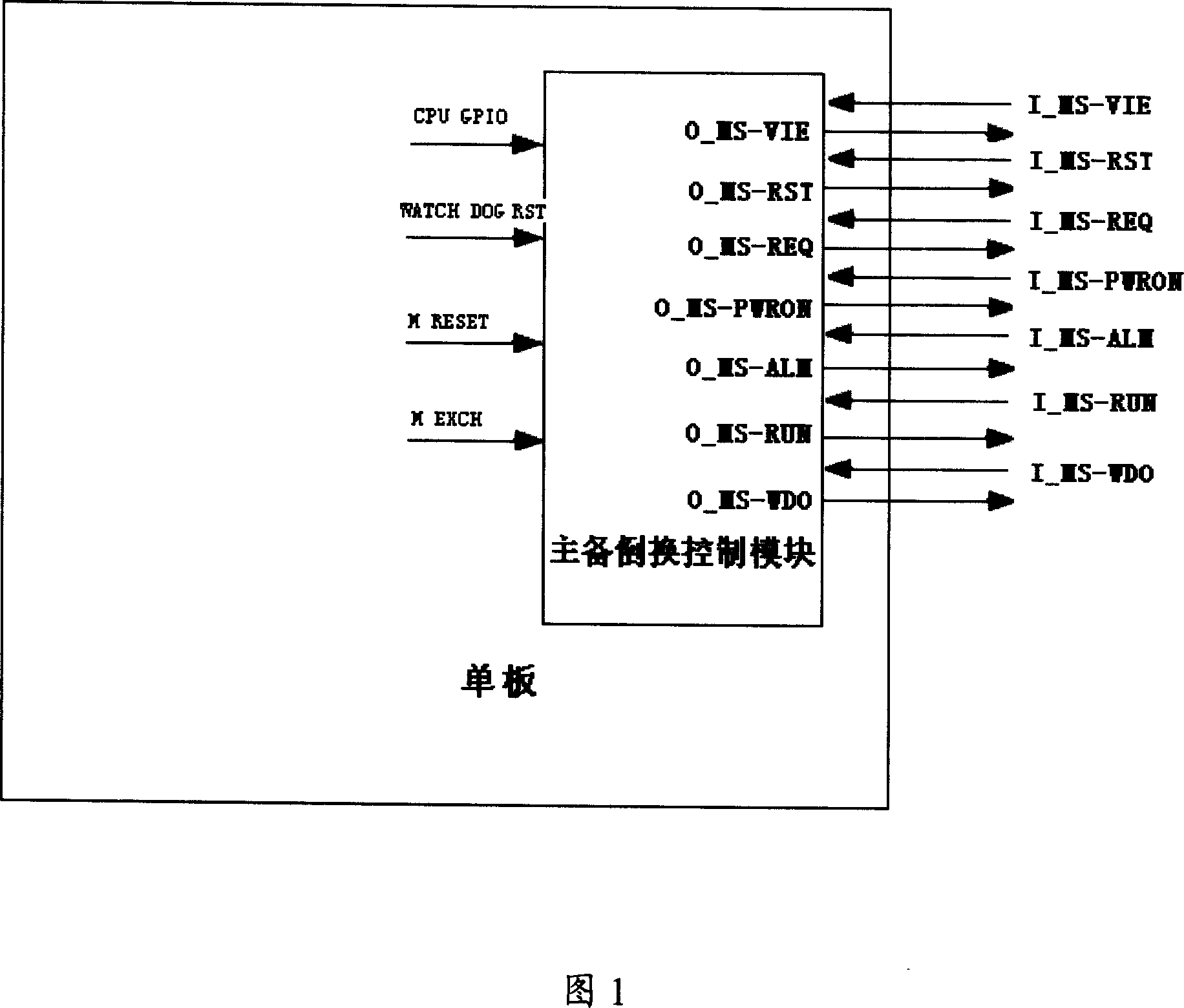
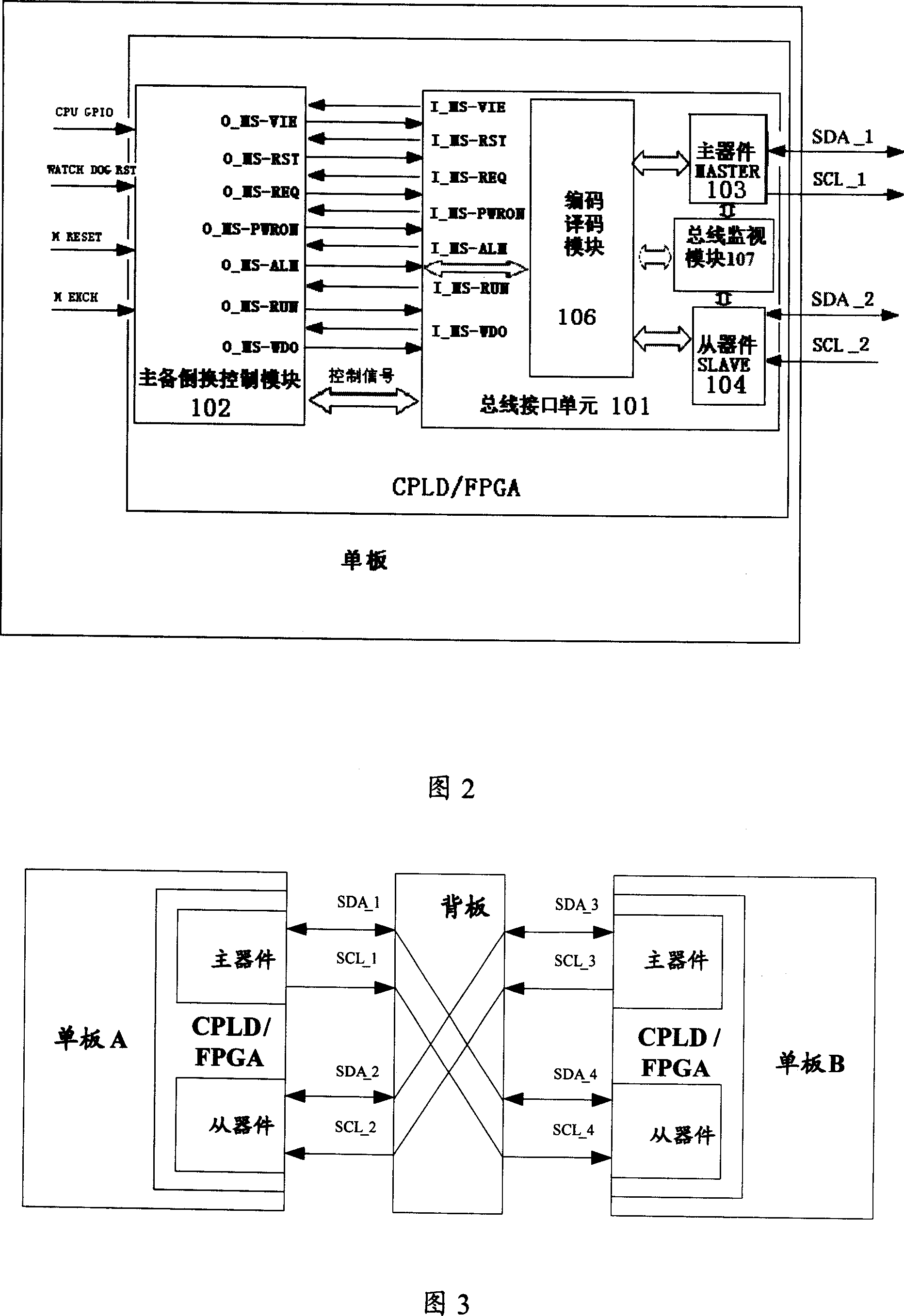
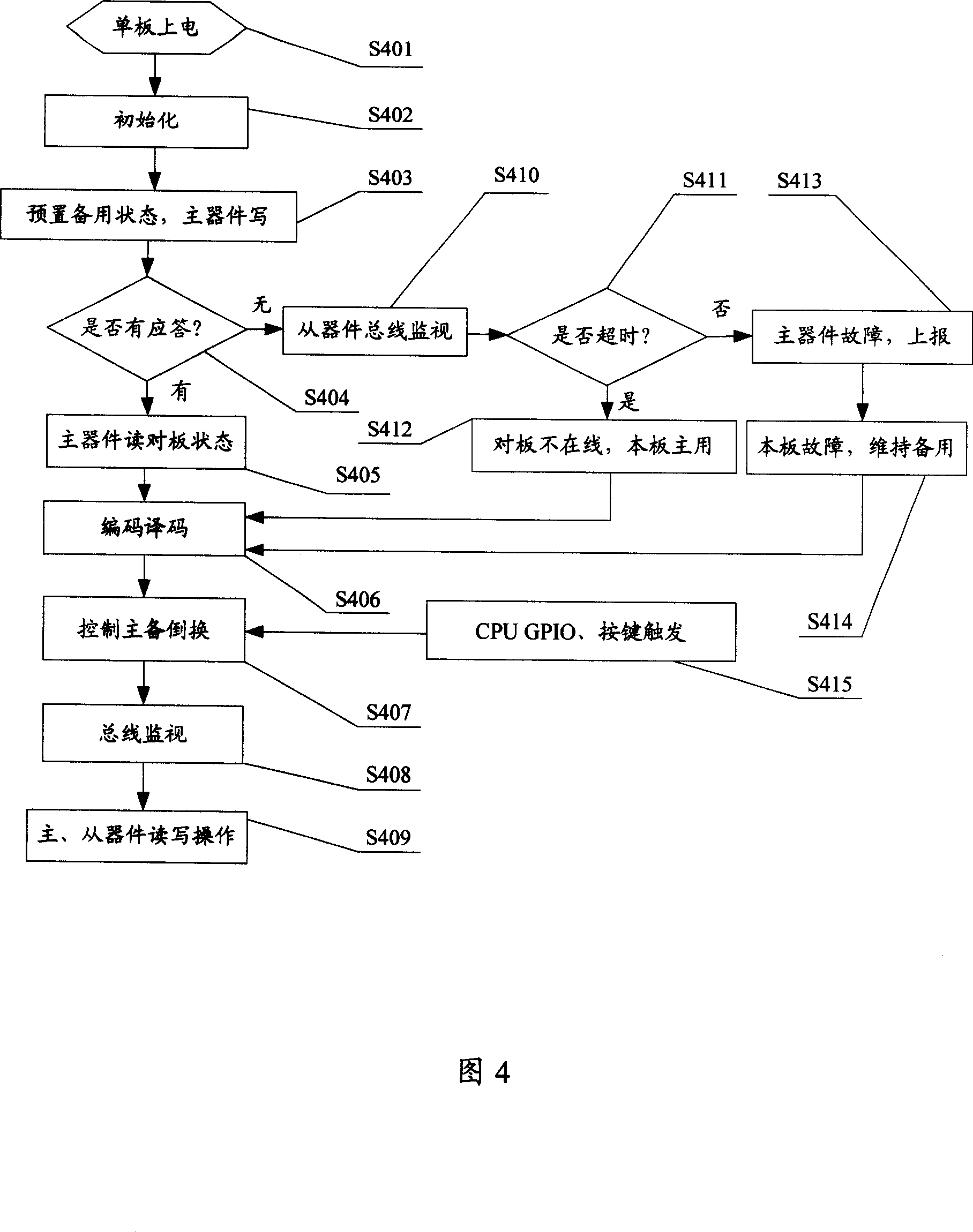
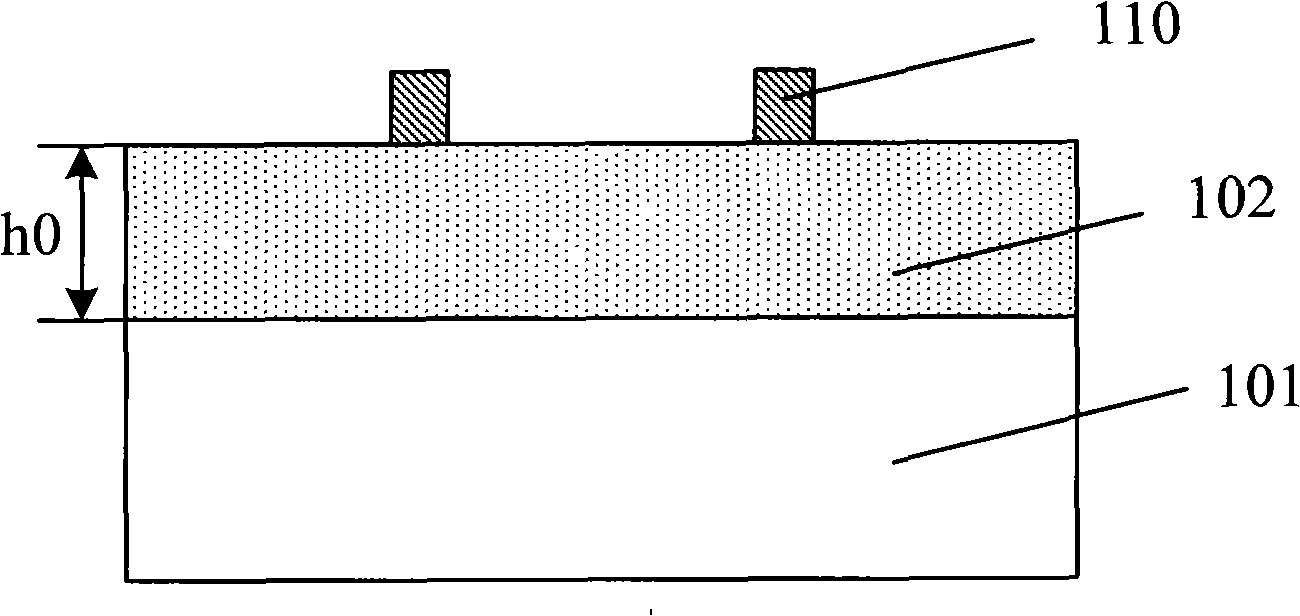
Communications device single board active/standby changeover apparatus and implementation method
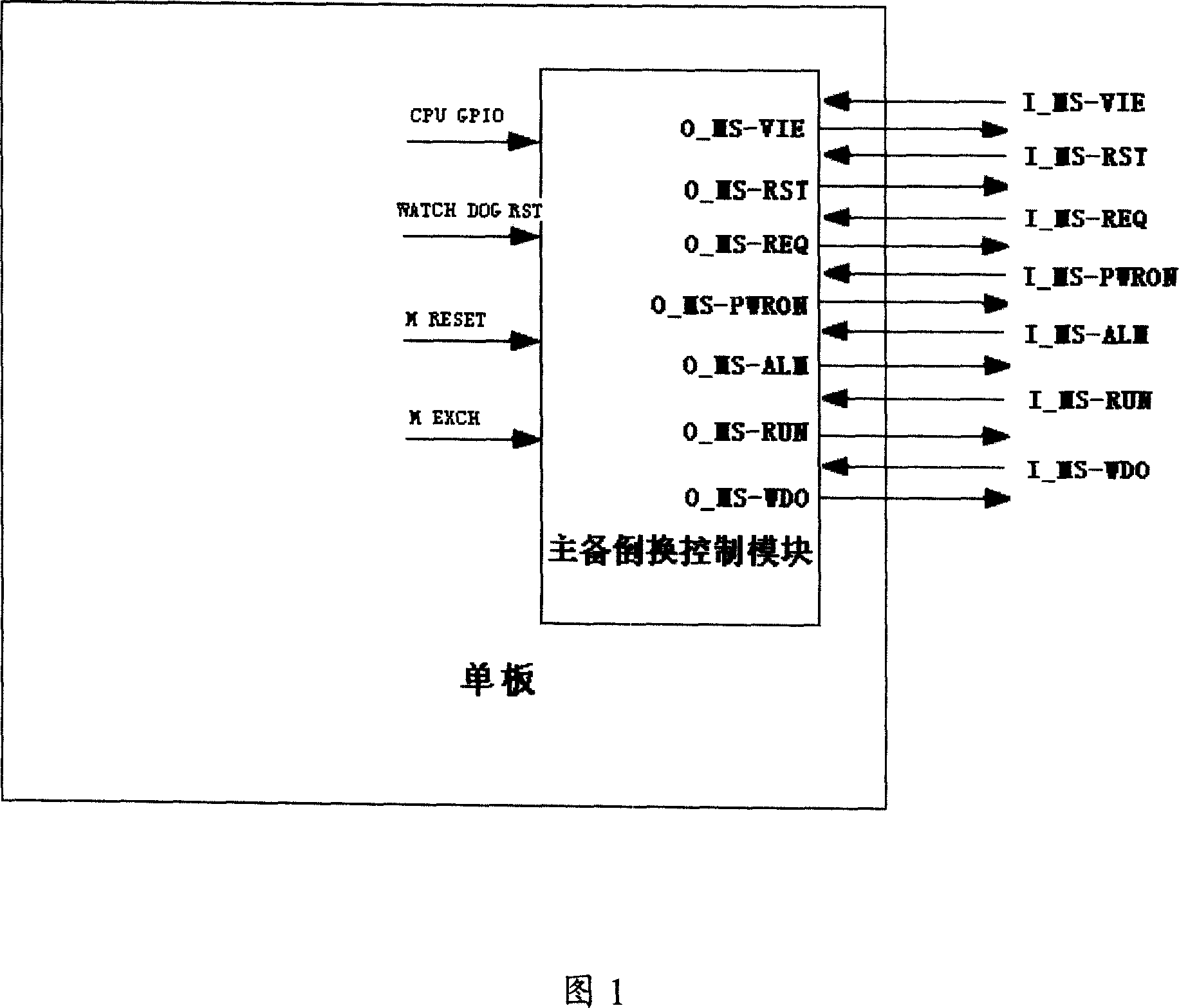
InactiveCN1972143AAvoid getting out of controlPrevent lockError preventionComputer scienceCommunication device
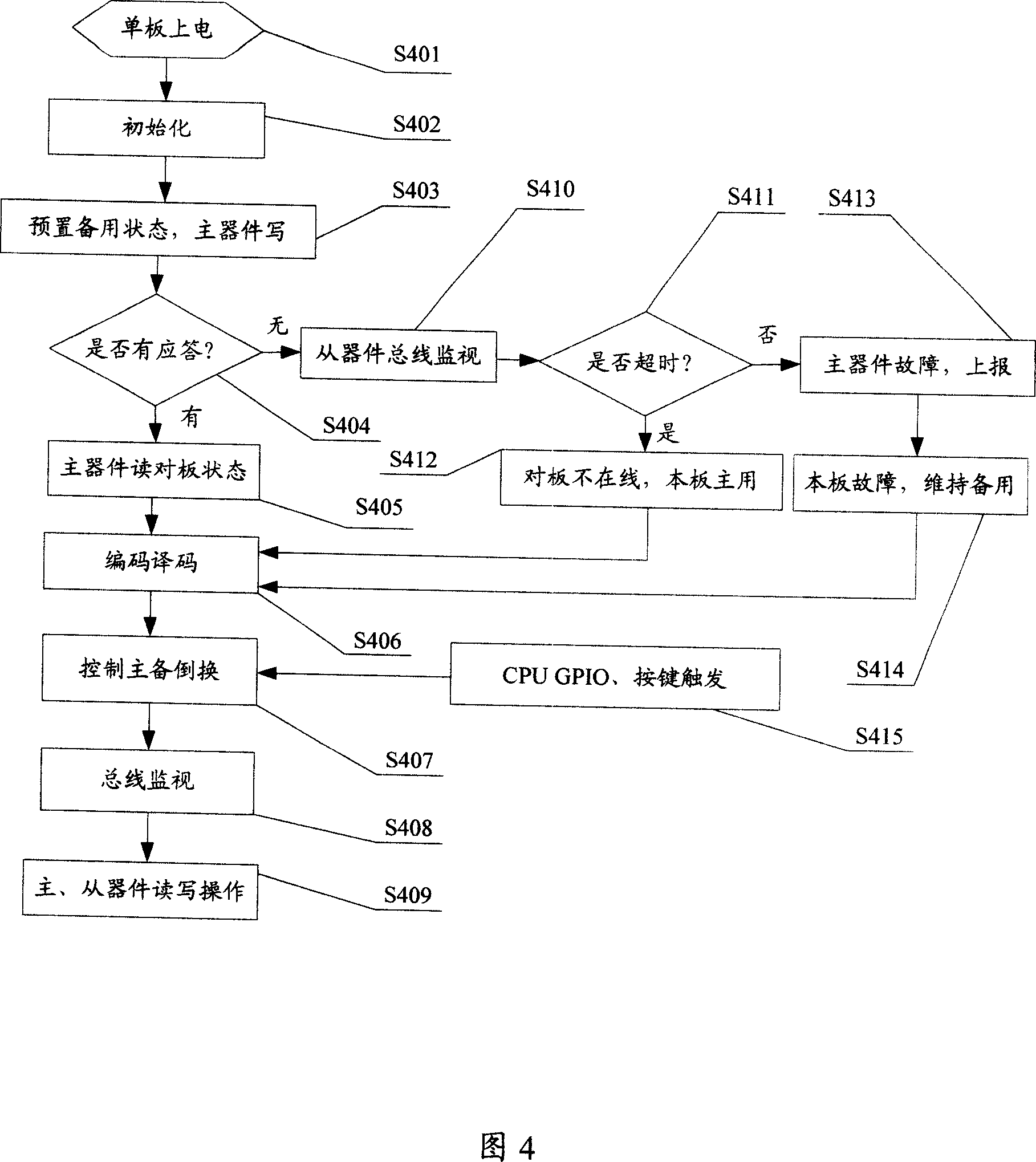
This invention discloses one method to realize communication device single board, which comprises the following steps: after initiating single board and setting it for prepare status and operating board information through main parts; when there is response, the board part reads board information to fulfill bus read or write operations and signal series and conversion and control module interface; according to the coded board information and main parts, aid parts status information and information interacting. The invention also discloses one communication device single board inverse device.
Owner:ZTE CORP
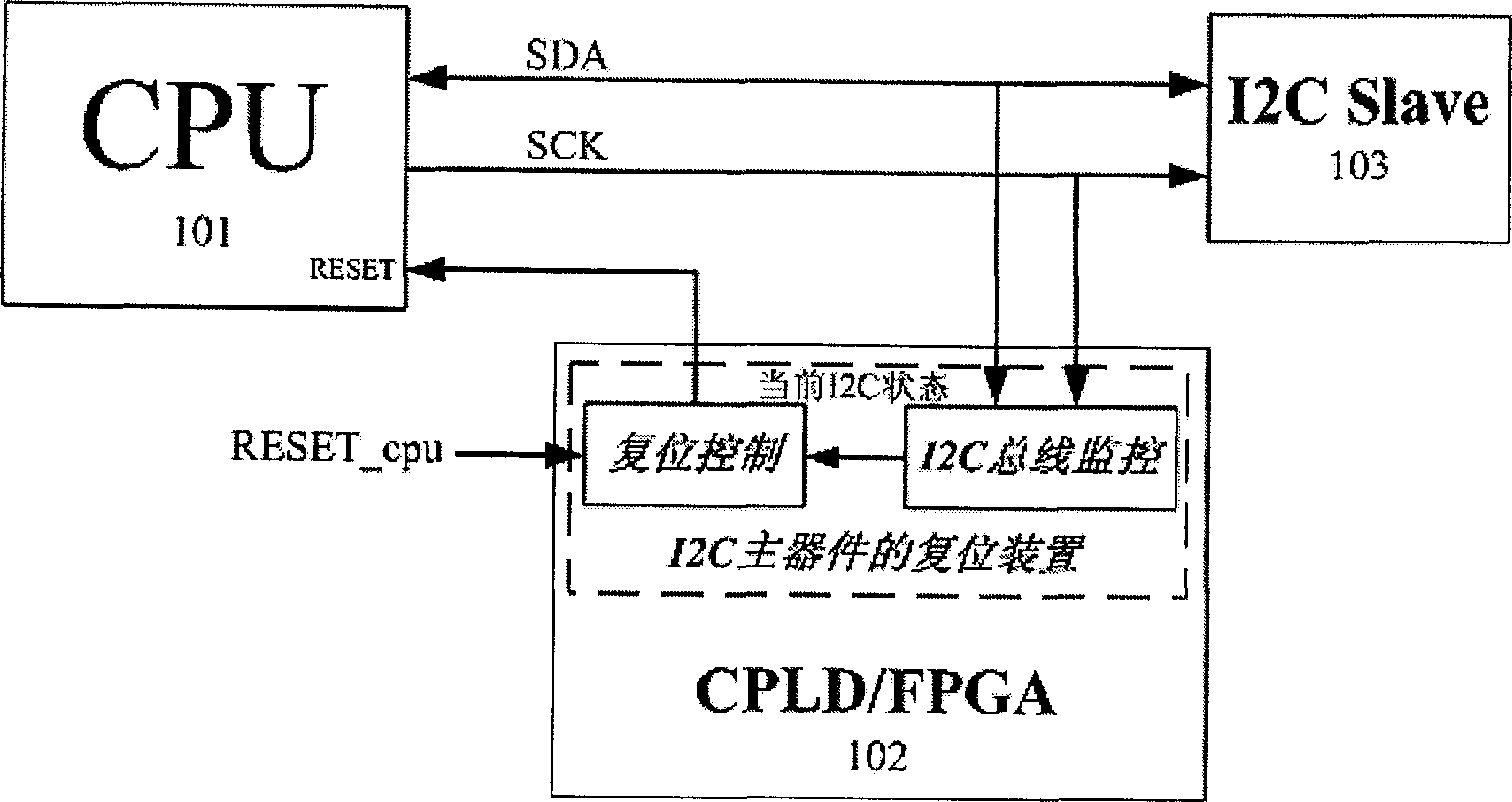
Method for realizing to reset main device in 12C bus and resetting apparatus and equipment thereof
InactiveCN1740998AImprove adaptabilityReduce hardware costsElectric digital data processingEmbedded systemSpecial design
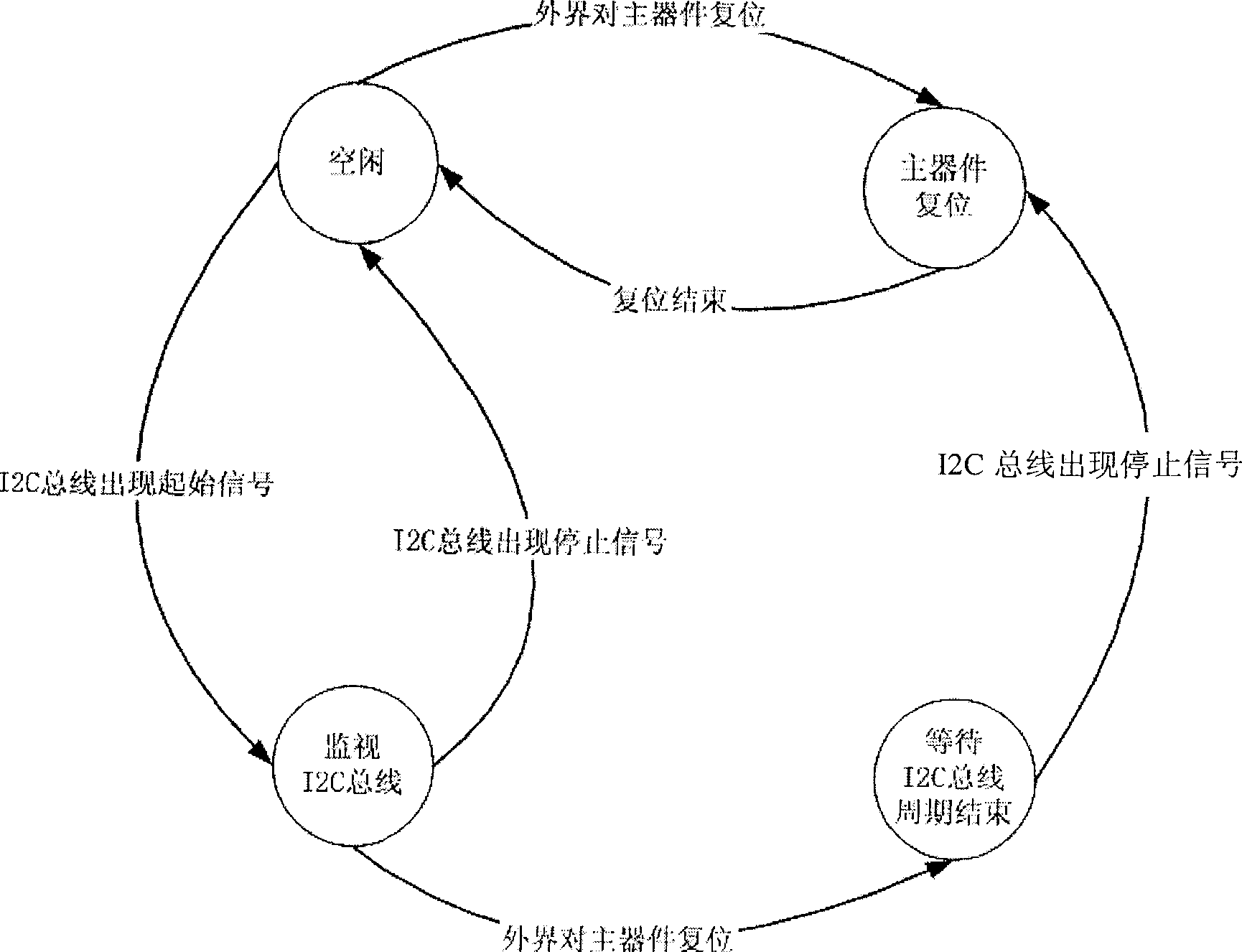
The method for implementing main device reset in 12C bus includes the following steps: real-time detecting 12C bus state, when the external signal for requiring main device to reset is received, judging current 12C bus state, if it is idle, immediately implementing main device reset, if it has 12C bus operation cycle, after said operation cycle is completed, making main device reset. Said reset device includes monitoring portion and reset control portion. Said invention also provides the concrete action of every portion.
Owner:ZTE CORP
Communications device single board active/standby changeover apparatus and implementation method
InactiveCN1972142AImprove stabilityReduce hardware costsError preventionEmbedded systemBus interface
This invention discloses one communication device signal board main prepare inversion device, which comprises main prepare inverse control module and bus, wherein, the main prepare inverse control module is to receive input signals to fulfill single board main prepare inverse control; bus interface unit connected to the bus, wherein, the bus interface unit is to receive series signals into parallel signals to main prepare inversion module; the said bus interface unit si to convert received parallel signals into series signals to bus.
Owner:ZTE CORP
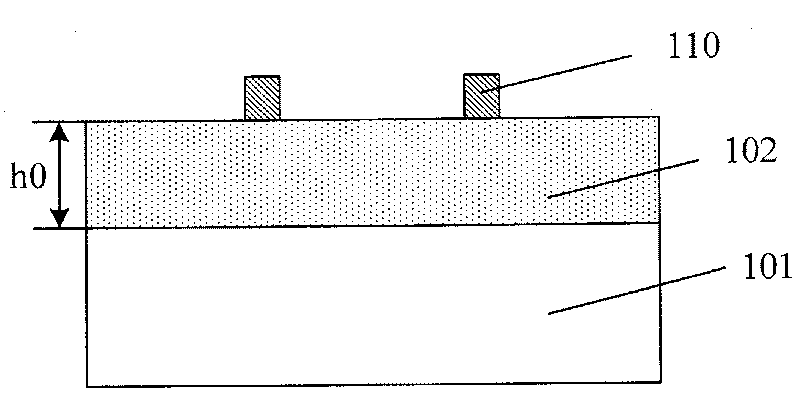
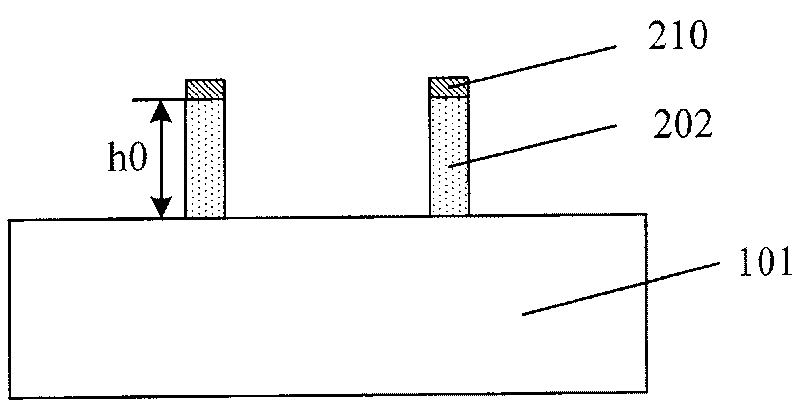
Method for forming graph
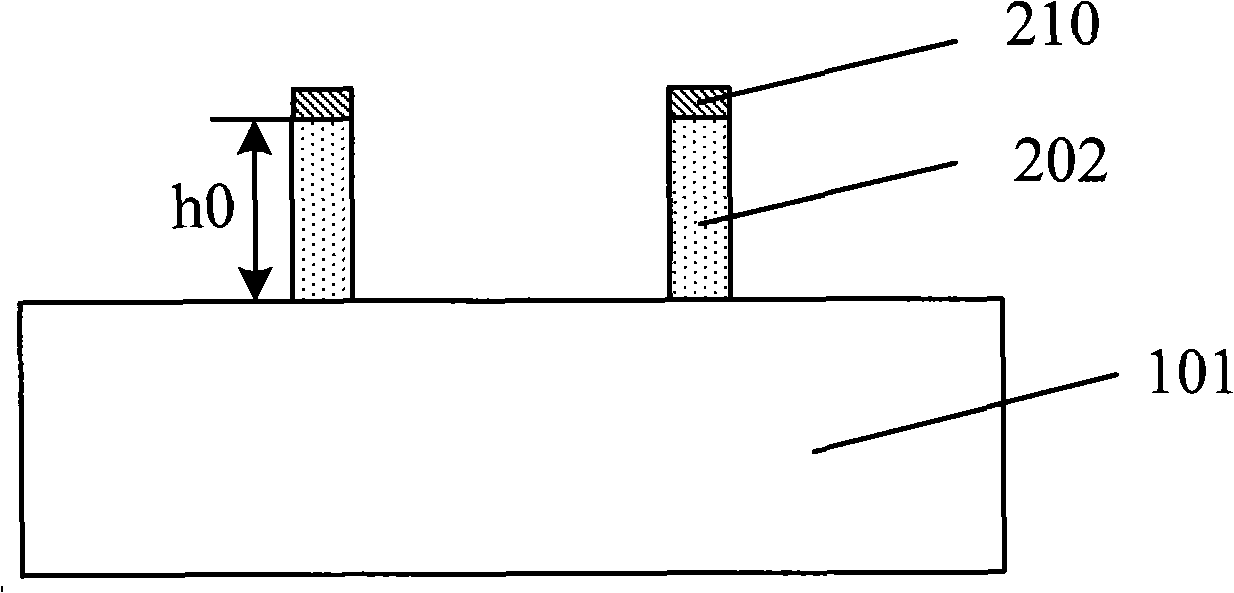
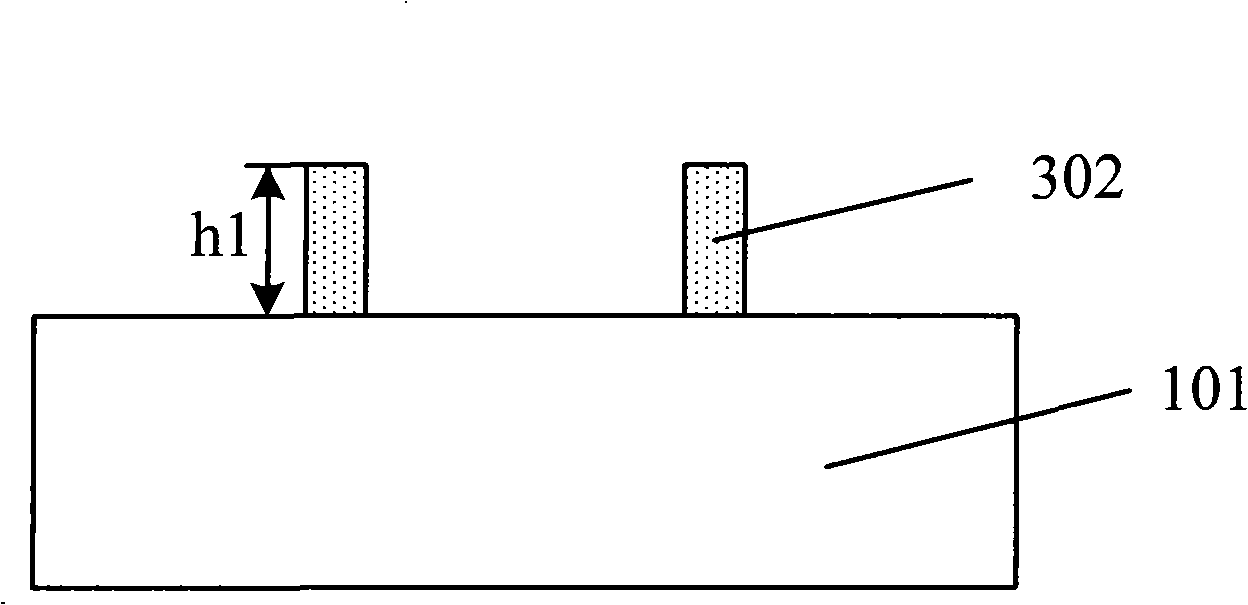
InactiveCN101312113AAchieve etch removalRelaxed ThicknessSemiconductor/solid-state device manufacturingComputer sciencePhotoresist
The invention discloses a pattern forming method, which comprises steps of providing a lining, forming sacrificers on the lining, filling a destination layer between the sacrificers to form a destination matter, defining masks on the sacrificer and the destination matter, removing the destination matter under a groove arranged among the masks by etching, and removing the masks and the sacrificers. The pattern forming method reduces requirements upon the photolithographic process in micro-pattern forming, releases limits to the thickness of photoresist, and can form much more micronic patterns beyond the exposure limit of exposure machines.
Owner:SEMICON MFG INT (SHANGHAI) CORP
Inflatable intelligent mattress
The invention discloses an inflatable intelligent mattress. The inflatable intelligent mattress is formed by a mattress module, a control panel, a pipe assembly, a temperature sensor module, an air pressure detection module, an electromagnetic valve module and a failure warning module. The mattress module mainly achieves left-right turning over, backing up, leg bending and fluctuation functions; the control panel adopts a true-color touch screen, comprises function buttons and image display, and controls movement of the intelligent turn-over mattress; the pipe assembly is mainly used for air inflation and air discharging of all air sacs in the mattress module; the temperature sensor module detects the temperature under the body of a patient, the turn-over state is controlled through feedback signals, and bedsores are prevented from being generated; the air pressure detection module detects internal gas pressure of all the air sacs in the mattress module; the electromagnetic valve module controls on-off states of all air ways in the pipe assembly. The inflatable intelligent mattress is scientific and reasonable in layout, low in energy consumption, low in cost, convenient and flexible in achievement and high in efficiency and is capable of being applied and popularized.
Owner:HEBEI UNIVERSITY OF SCIENCE AND TECHNOLOGY
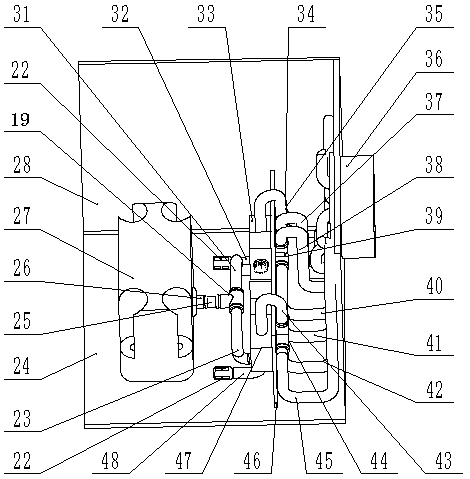
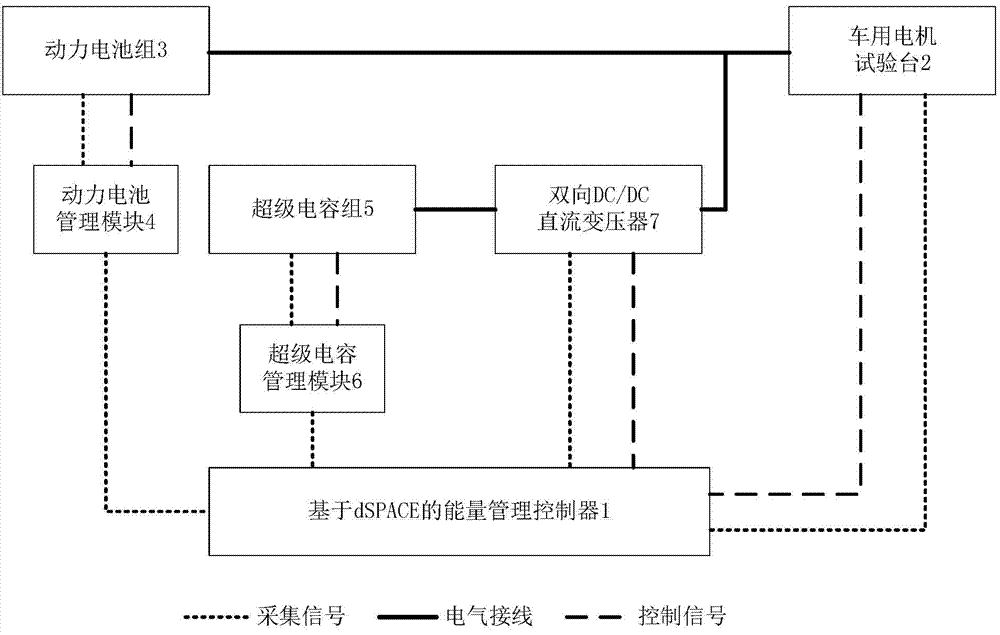
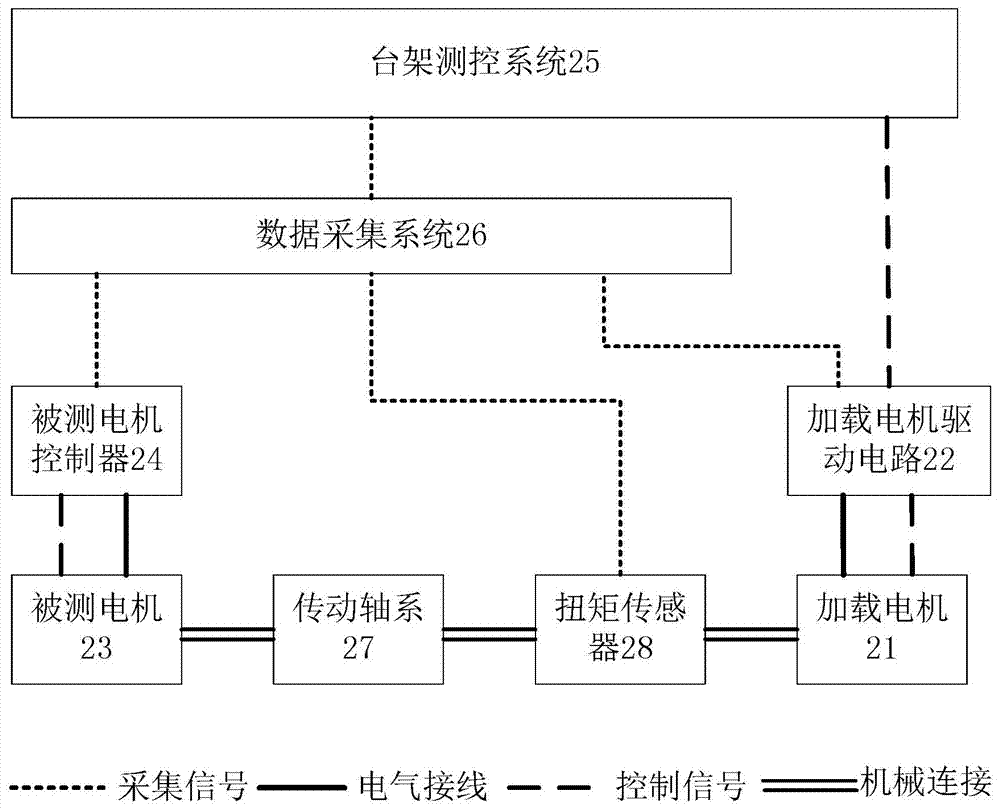
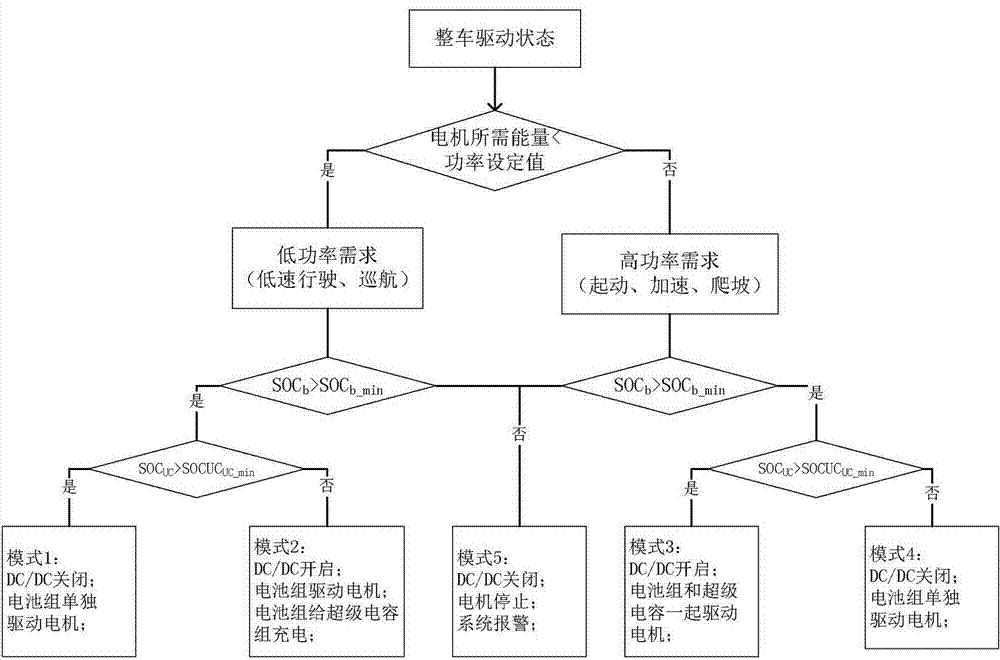
Vehicle-used hybrid energy storage control system based on dSPACE and motor test bench
InactiveCN107957720AEasy to modifyFlexible and convenient designElectric testing/monitoringVehicular energy storageCapacitanceDC - Direct current
The invention discloses a vehicle-used hybrid energy storage control system based on dSPACE and a motor test bench. The vehicle-used hybrid energy storage control system comprises a dSPACE-based energy management controller, the vehicle-used motor test bench, a power battery pack, a power battery management module, a supercapacitor bank, a supercapacitor management module, and a bidirectional DC / DC direct current transformer, wherein the dSPACE-based energy management controller is connected with the power battery management module, the supercapacitor management module, the bidirectional DC / DCdirect current transformer and a tested motor controller on the vehicle-used motor test bench; and one end of the bidirectional DC / DC direct current transformer is connected with the supercapacitor bank, and the other end is connected with the power battery pack and a DC power supply terminal of a tested motor. The vehicle-used hybrid energy storage control system can implement various energy management control strategies simply and flexibly, and is convenient for testing energy utilization efficiency and energy distribution among various energy storage devices by means of the energy management controller under various typical operating conditions.
Owner:HONG KONG PRODUCTIVITY COUNCIL
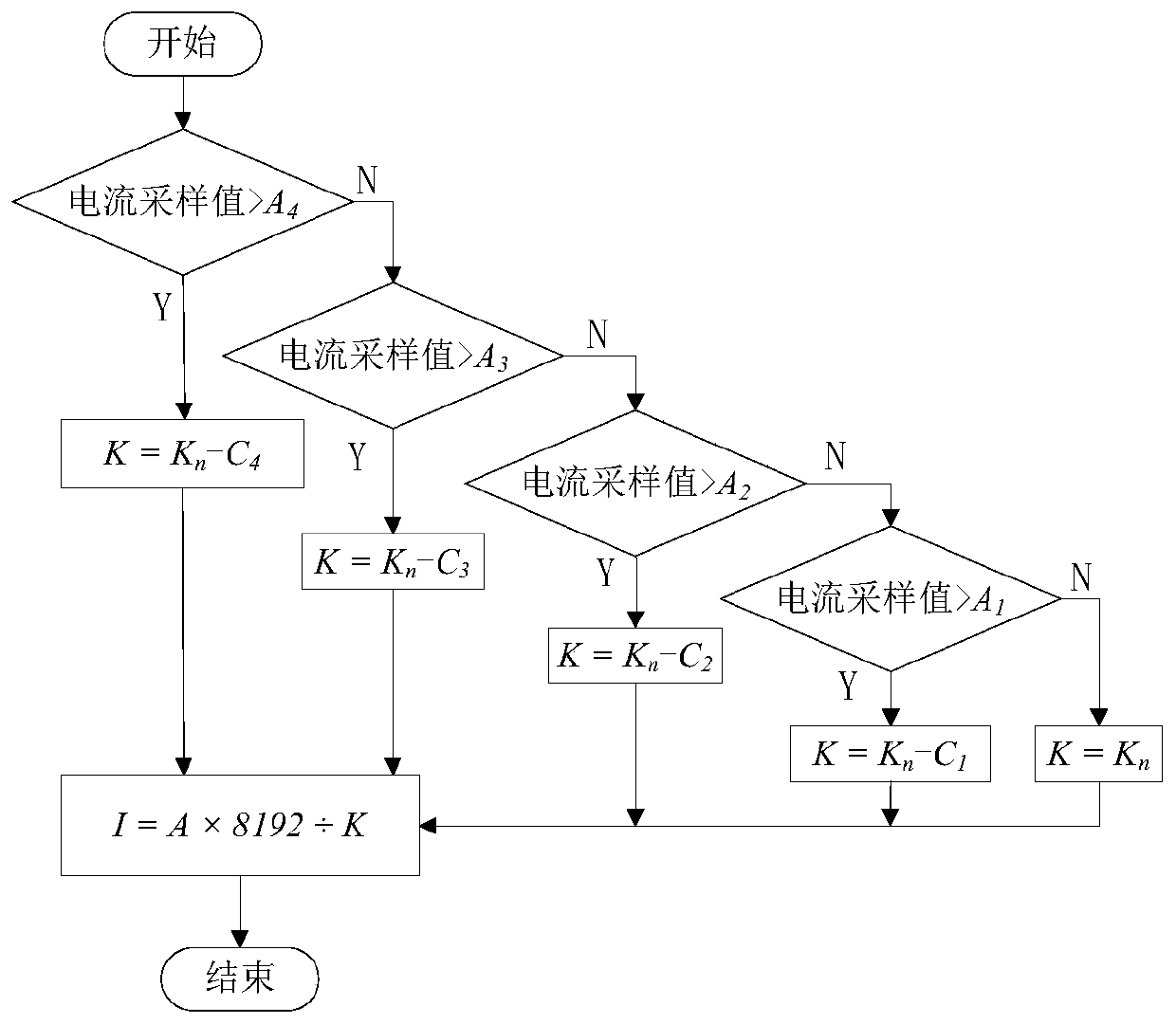
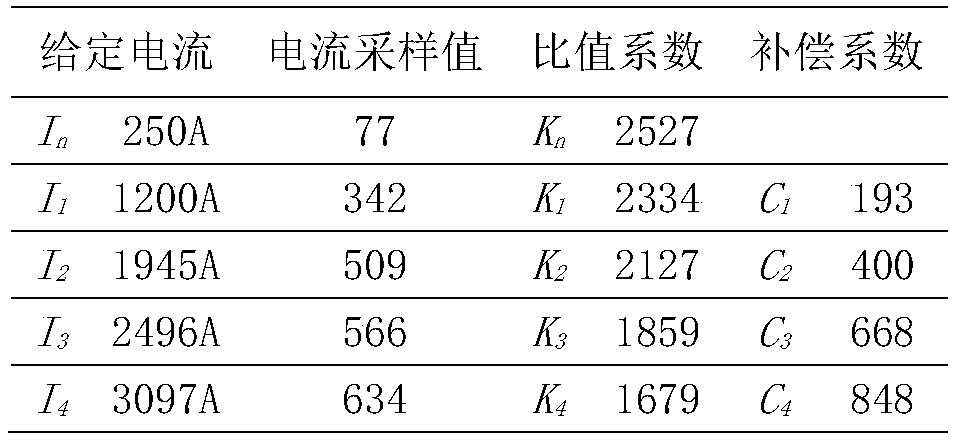
Current non-linear compensation method of residual current protection circuit breaker
The present invention relates to a current non-linear compensation method of a residual current protection circuit breaker, pertaining to the field of the residual current protection circuit breaker.The method comprises the following steps: a current transformer converting a large alternating current at a primary side into a small current at a secondary side; outputting a direct current via rectification; inputting the direct current into an ADC to perform digital sampling via current and voltage conversion and signal conditioning; and finally performing piecewise linear fitting processing ondata digitally sampled by the ADC via a microprocessor. By modifying the ratio coefficient K value of each interval, the linear compensation of the non-linear interval of the current transformer is realized, and the current detection accuracy requirement(s) in a full current input range are met. The method does not need circuit component establishment, the cost is low, debugging, verification andproduction are more convenient, and higher precision is easier to reach; and because of the software segmentation by adopting the microprocessor, the segmentation can be finer, and the implementationis more convenient and flexible.
Owner:HANGZHOU SHICHUANG ELECTRONICS TECH
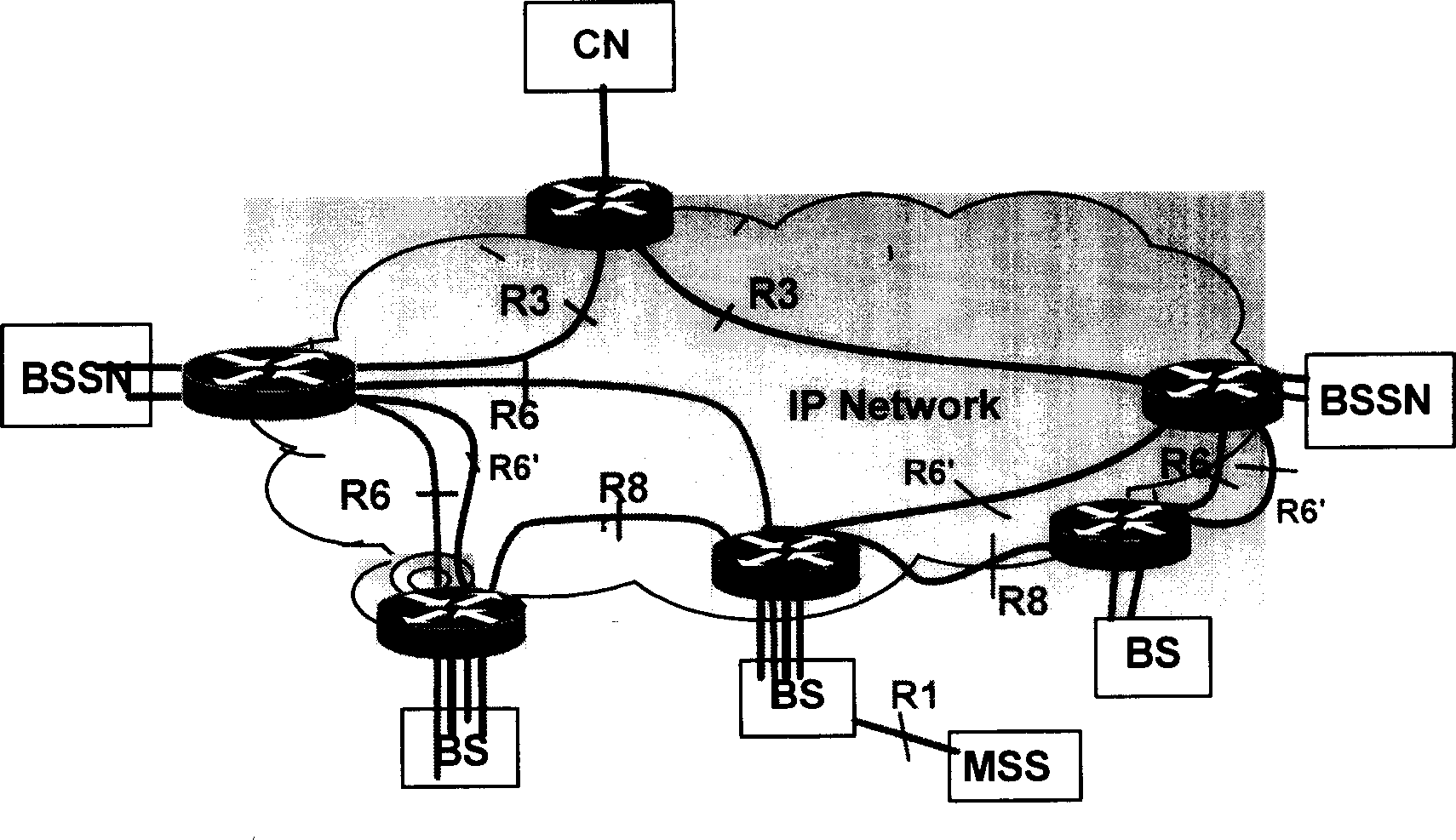
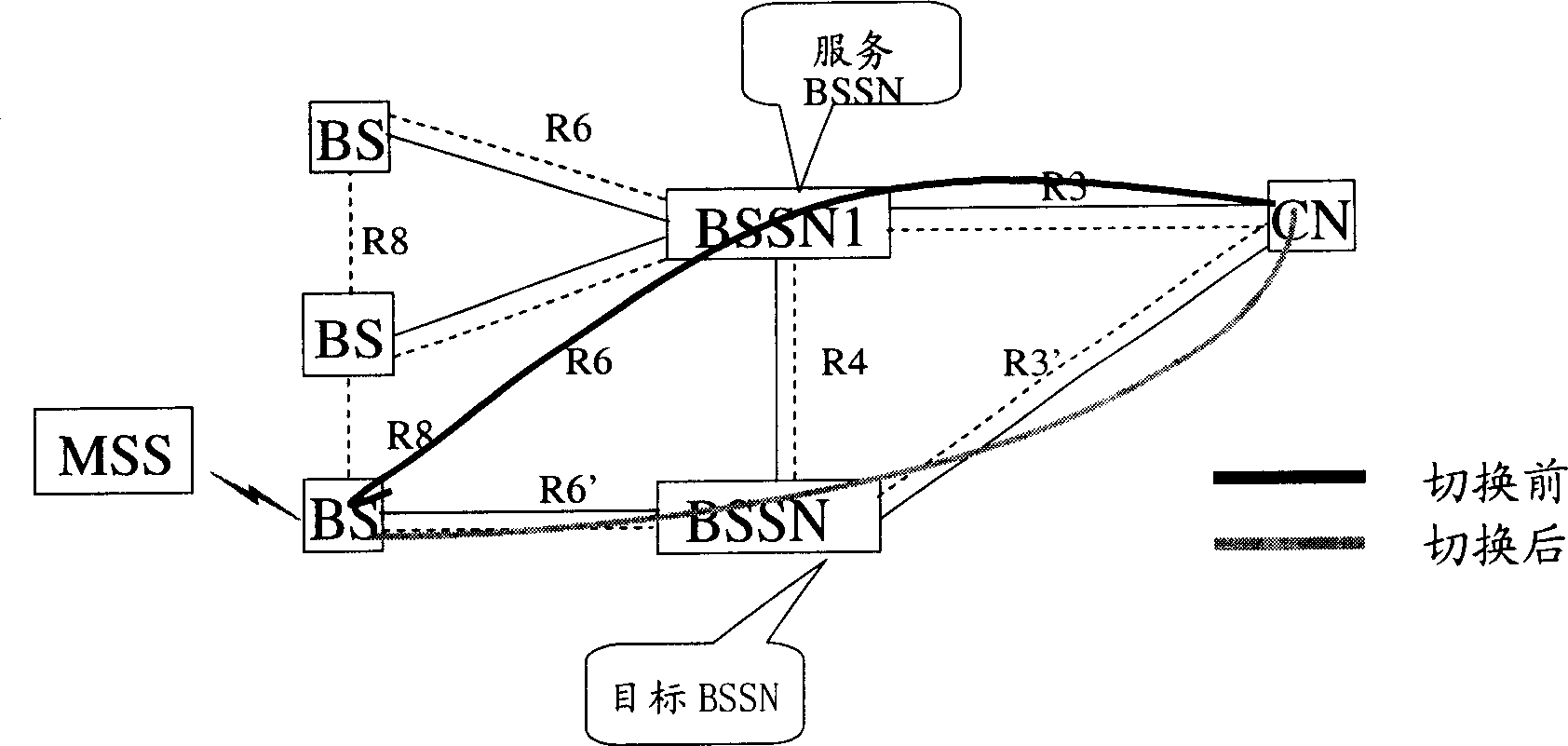
Network optimization based on distributive wireless access network
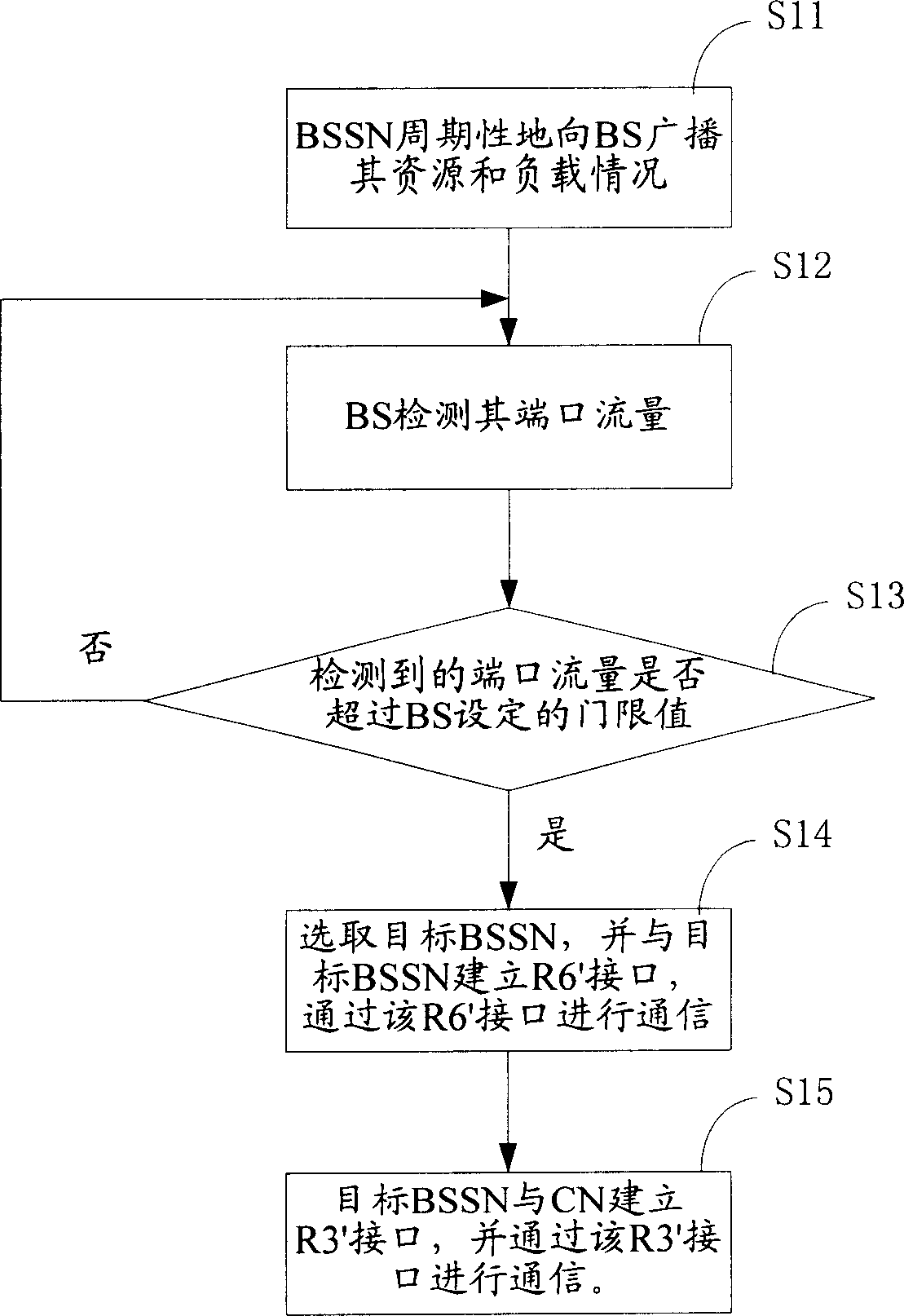
InactiveCN1855857AAchieve flexibility and convenienceEfficient use ofData switching by path configurationAccess networkBase station
A network optimizing method which based on announcement type wireless access network, the base station (BS) accesses the base station service node (BSSN) by the first R6 interface, the BSSN access the central network (CN) by the first R3 interface, it includes the following steps: A) the base station detects the capability parameter of the network, estimates the network capability parameter whether or not exceed the fixed threshold value, enter the step B if it is, repeat the step A if it is not; B) the base station choose the aiming base station service node, set the second R6 interface with the aiming base station service node, processes the communication by the second R6 interface; C) the aiming base station service node sets the second R3 interface with the central network, and processes the communication by the second R3 interface.
Owner:HUAWEI TECH CO LTD
Network management implementation method based on simple network management protocol
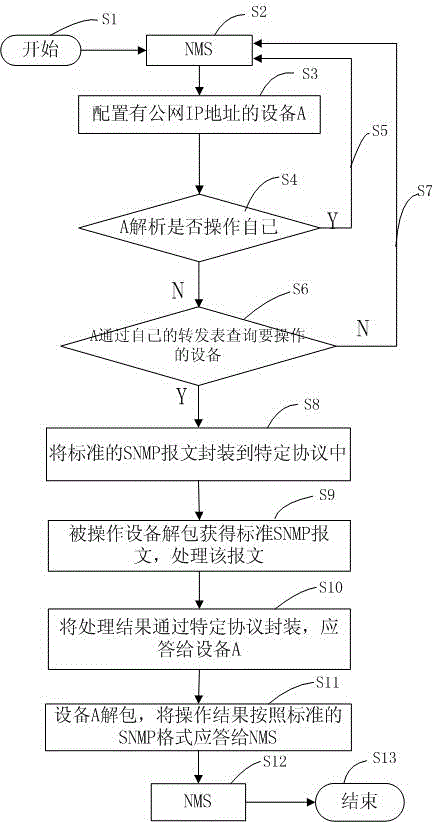
InactiveCN102984006ASave public network IP address resourcesSimple and clear functionData switching networksIp addressMedia access control
The invention discloses a network management implementation method based on a simple network management protocol (SNMP). The method comprises the following steps: an NMS (Network Management System) is connected with equipment A, to which a public network IP (Internet Protocol) address is allocated, and operational commands carrying an equipment MAC (Media Access Control) address are sent through the NMS; the equipment A receives standard SNMP (Simple Network Management Protocol) message sent by the NMS and analyzes and compares the MAC address in the message with an MAC address of the equipment A; if the MAC addresses are not the same, the equipment A searches a forwarding table of the equipment according to the analyzed MAC address, packages the complete SNMP message to a specific protocol message when finding out a forwarding table item, and then forwards the message to specified equipment operated according to the forwarding table item; when the equipment operated receives the protocol message, standard SNMP message is analyzed and processed, so as to obtain response message; the response message is packaged into a specific protocol and fed back to the equipment A; and response message is analyzed through the equipment A and sent to the NMS. By adopting the method, the network management efficiency can be improved, and limited public network IP address resources can be saved.
Owner:WUHAN FIBERHOME NETWORKS
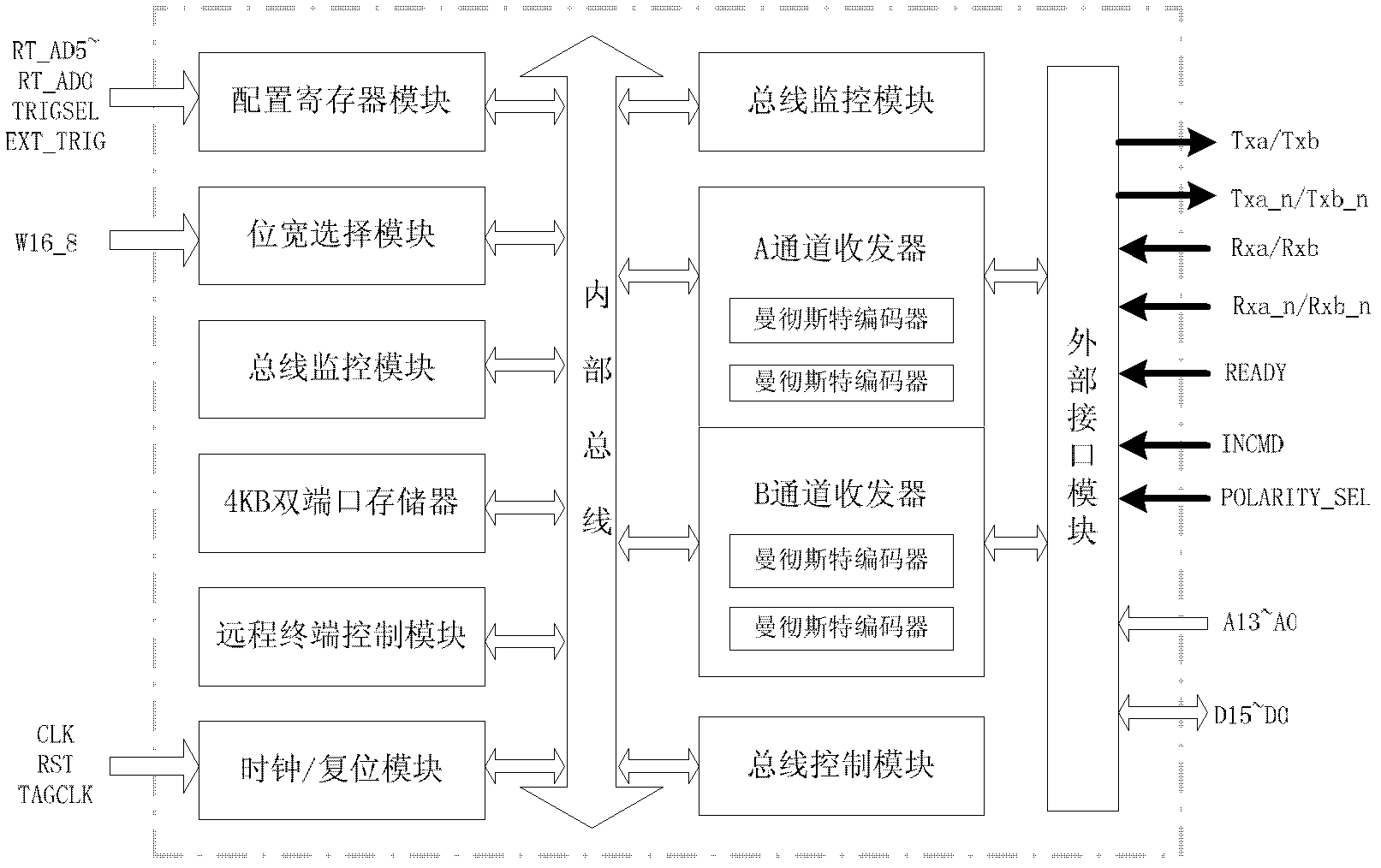
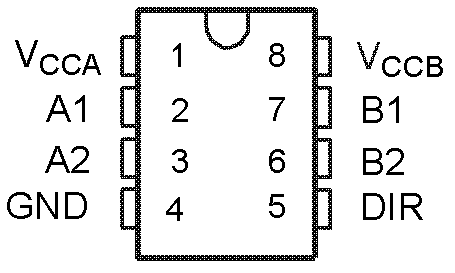
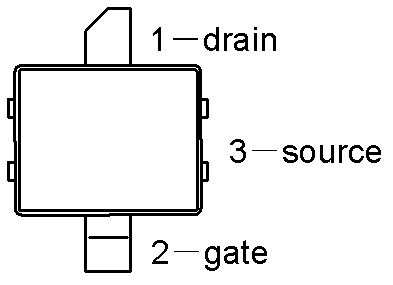
Discrete transceiver circuit suitable for high-speed 1553 bus
The invention aims at overcoming the defects in the prior art and provide a discrete transceiver circuit suitable for a high-speed 1553 bus. The discrete transceiver circuit suitable for the high-speed 1553 bus comprises a transmitter and a receiver; wherein the transmitter is connected with a protocol processor to finish the transmitting of a high-speed Manchester code, and the discrete transceiver circuit also comprises a voltage conversion driving circuit, a lateral double-diffused metal-oxide semiconductor (LDMOS) (or N-metal-oxide-semiconductor (NMOS)) and a resistor / capacitor with certain resistance and capacitance. The receiver comprises a first-order active filter, a comparator, a voltage reference and a voltage conversion driving circuit and is connected with the protocol processor through the voltage conversion driving circuit. The discrete transceiver circuit suitable for the high-speed 1553 bus has the advantages that the discrete transceiver circuit achieves the transmission of 1553 bus data at 10Mbps rate by cooperating with the external protocol processor to work, is built by adopting a discrete device without changing the original bus structure and is flexible and convenient in realization.
Owner:58TH RES INST OF CETC
Method and device for resisting energy analysis attacks in block encryption operation
ActiveCN108737073AGuaranteed cover upResistance to analysis attacksEncryption apparatus with shift registers/memoriesCryptographic attack countermeasuresPower analysisEncryption
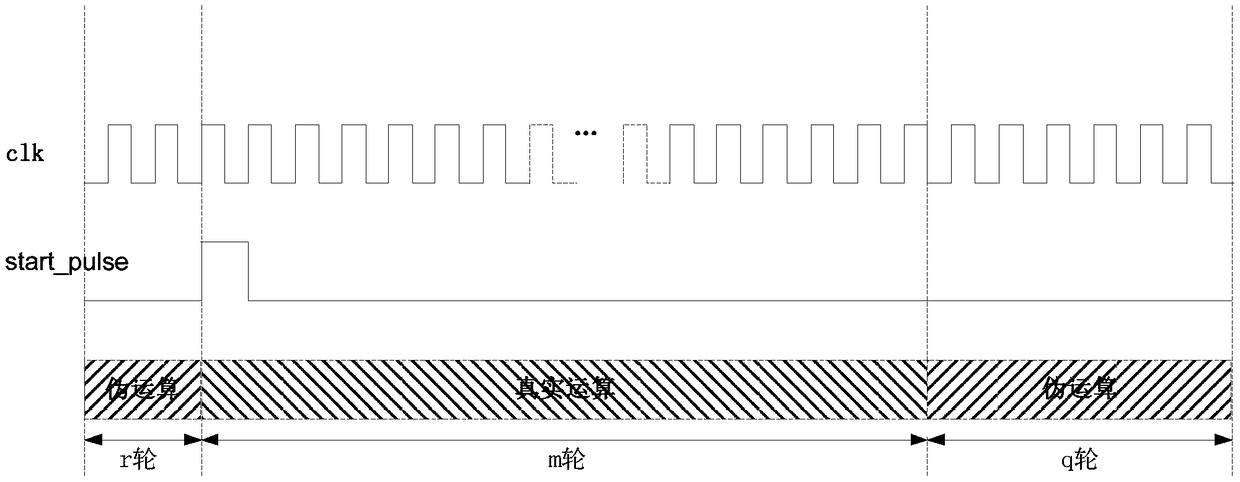
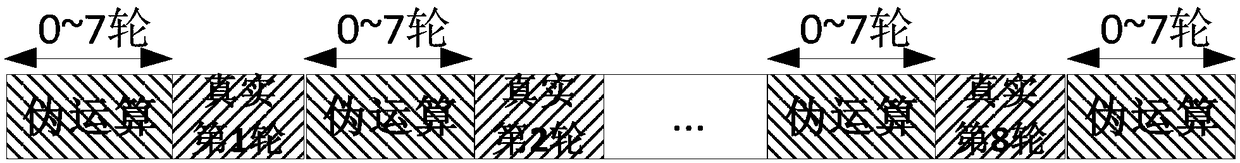
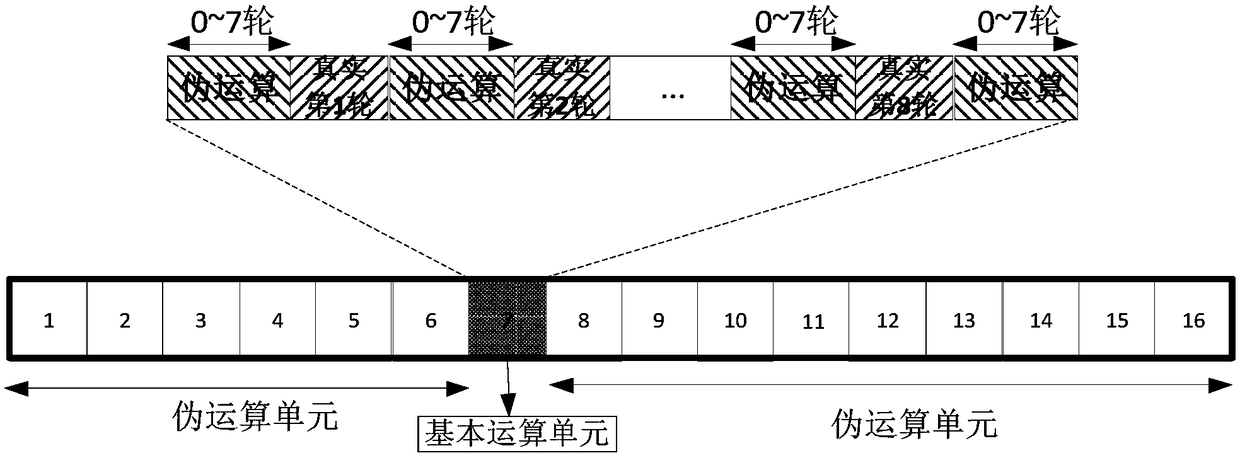
The invention discloses a method and device for resisting energy analysis attacks in block encryption operation. The method comprises the following steps: generating a pseudo encryption operation, andencrypting the pseudo encryption operation by adopting a pseudo key; combining a real encryption operation with the pseudo encryption operation to form a basic encryption operation unit; generating apseudo encryption operation unit, wherein the pseudo encryption operation unit only includes the pseudo encryption operation; and combining the basic encryption operation unit with the pseudo encryption operation unit to perform the encryption operation. Compared with the prior art, according to the block encryption operation disclosed by the invention, the pseudo encryption operation is randomlyinserted between every round of operations to ensure that sensitive information is covered by noises, and based on the basic operation unit after inserting the pseudo operation between each round ofoperations, the operation unit is called circularly and input data are random numbers, so that the noises can be further increased, and side channel energy analysis attacks can be effectively resisted.
Owner:BEIJING SMARTCHIP MICROELECTRONICS TECH COMPANY +3
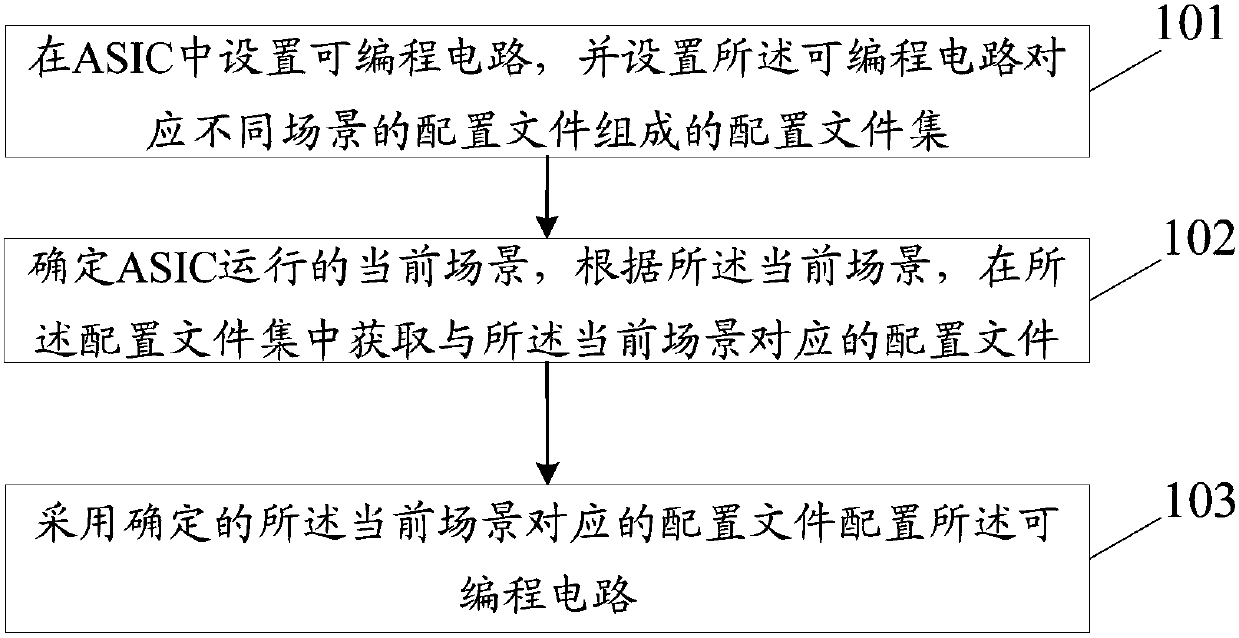
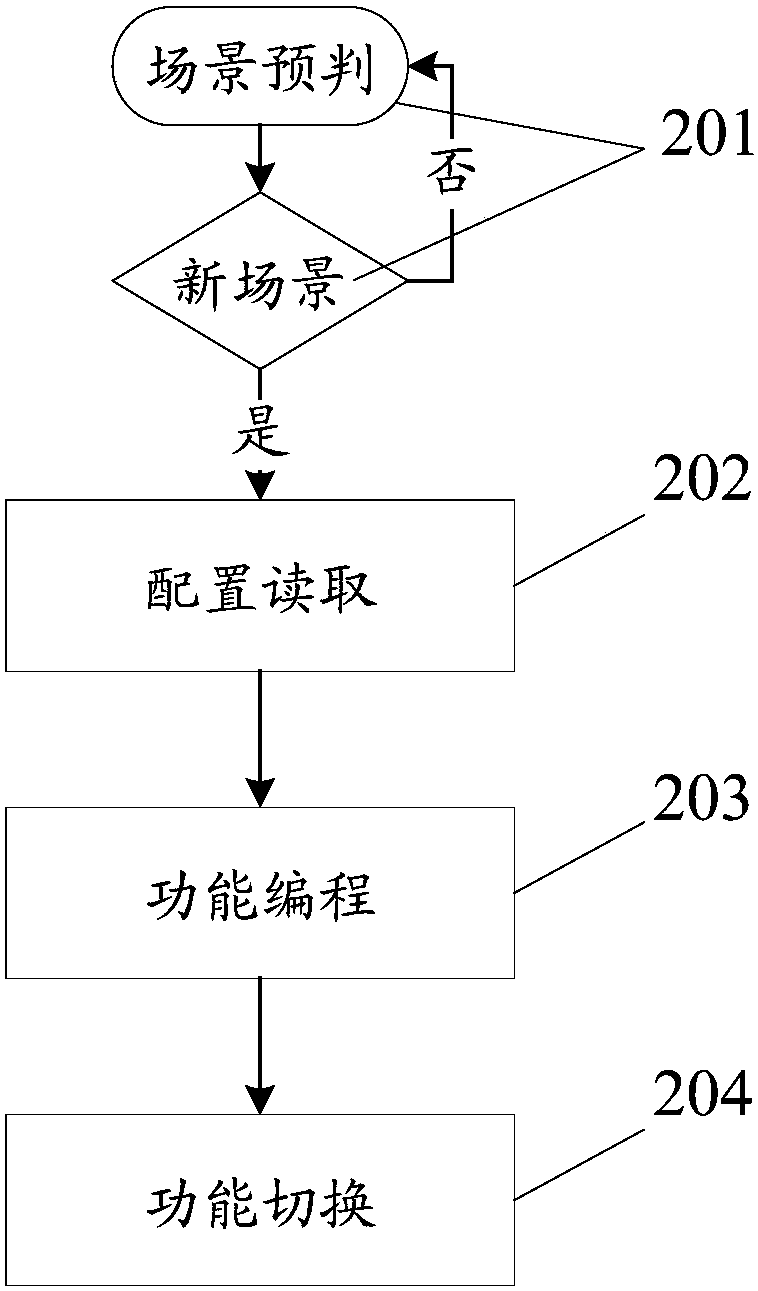
Chip architecture reconstruction method and device
InactiveCN107608255AMeet different needsAchieve flexibility and convenienceProgramme controlComputer controlReconstruction methodChip architecture
The invention discloses a chip architecture reconstruction method, which includes the steps of arranging a programmable circuit in an ASIC and setting a configuration file set of configuration files corresponding to different scenes of the programmable circuit; determining a current scene of the ASIC running, and according to the current scene, acquiring a configuration file corresponding to the current scene in the configuration file set; and configuring the programmable circuit by using the determined configuration file corresponding to the current scene. The invention also discloses a chiparchitecture reconstruction device.
Owner:SANECHIPS TECH CO LTD
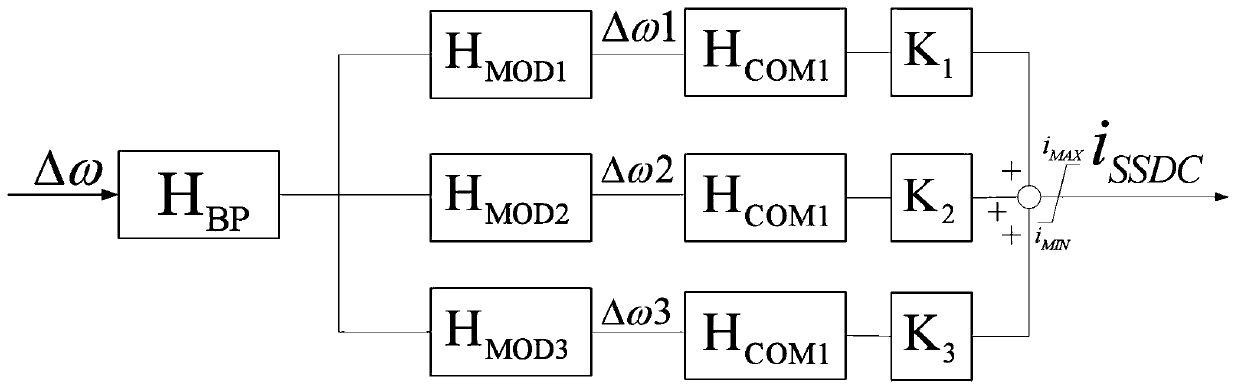
Additional damping inner loop control method for multi-terminal flexible direct current system and additional damping controller
PendingCN111262258AImprove general performanceThe design idea is simplePower oscillations reduction/preventionAC - Alternating currentControl system
The invention relates to an additional damping inner loop control method for a multi-terminal flexible direct current system and an additional damping controller. The method comprises the steps of 1,obtaining modal deviation signals in the system from an alternating current bus voltage of a converter station through a phase locking link; 2, filtering the modal deviation signals which are extracted in the step 1 and contain frequency information and phase information at the same time, and extracting sub-synchronous frequency signals from the frequency signals; 3, based on the sub-synchronous frequency signals in the frequency signals extracted in the step 2, carrying out phase compensation on the magnitude of phase change generated when each sub-synchronous modal component passes through the alternating current and direct current system; and 4, superposing the signals after the phase compensation link in the step 3 to a control system of the converter. The method can be applied to themulti-terminal flexible direct current system and a traditional double-terminal flexible direct current system at the same time.
Owner:ELECTRIC POWER SCI & RES INST OF STATE GRID TIANJIN ELECTRIC POWER CO +2
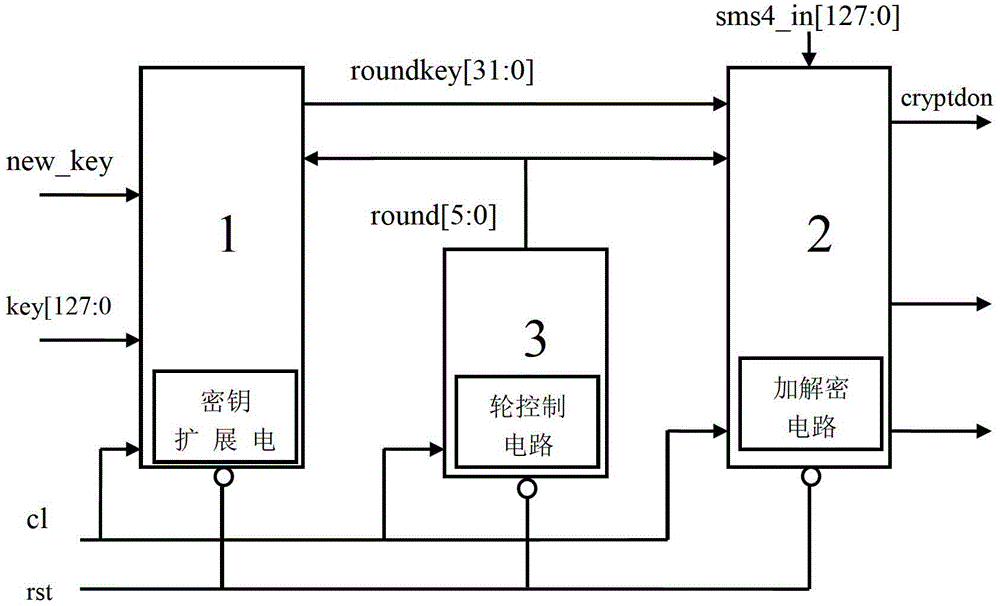
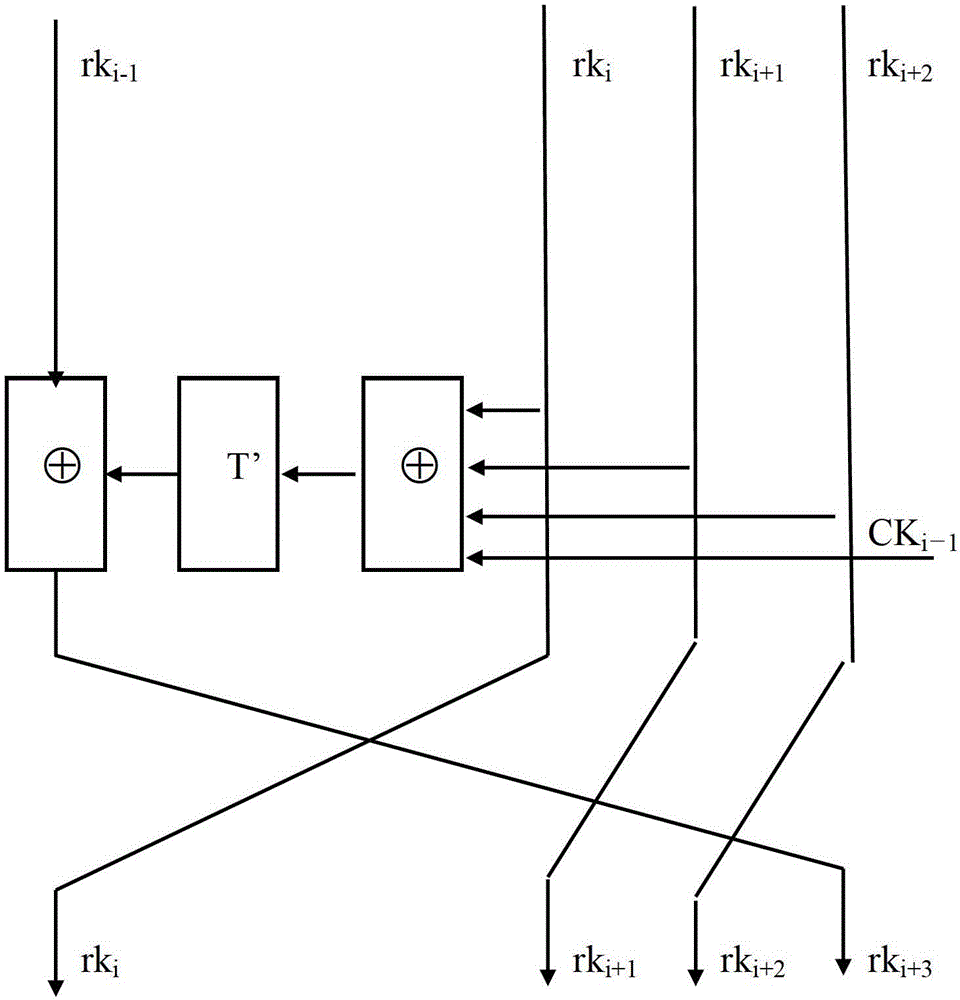
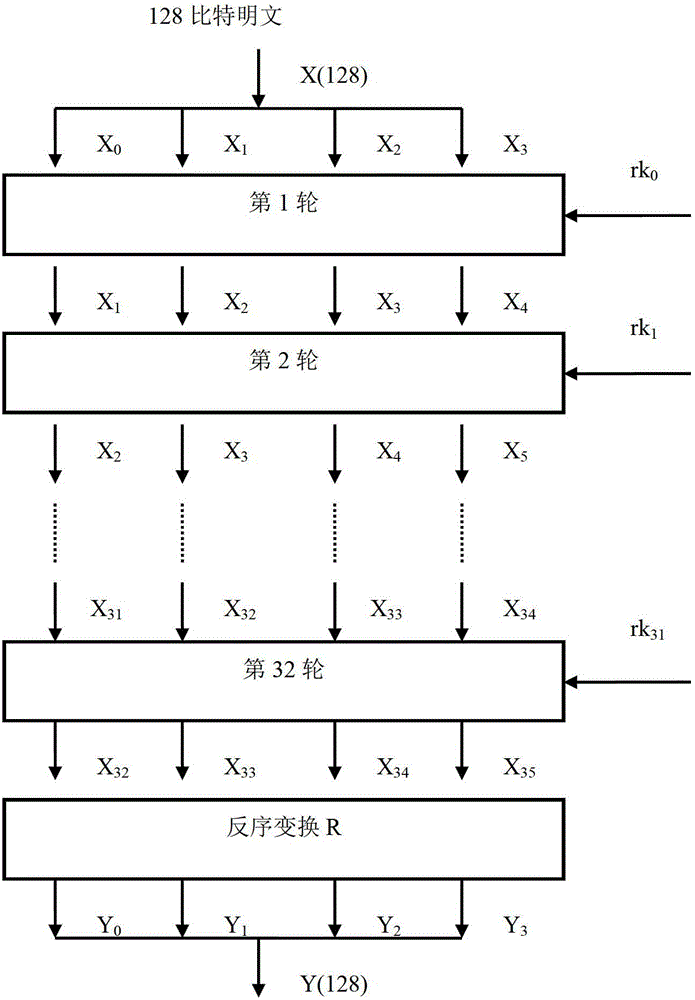
Algorithm hardware realizing method for improving network safety
InactiveCN103338449ASimple designIncrease profitNetwork topologiesSecurity arrangementExclusive orComputer science
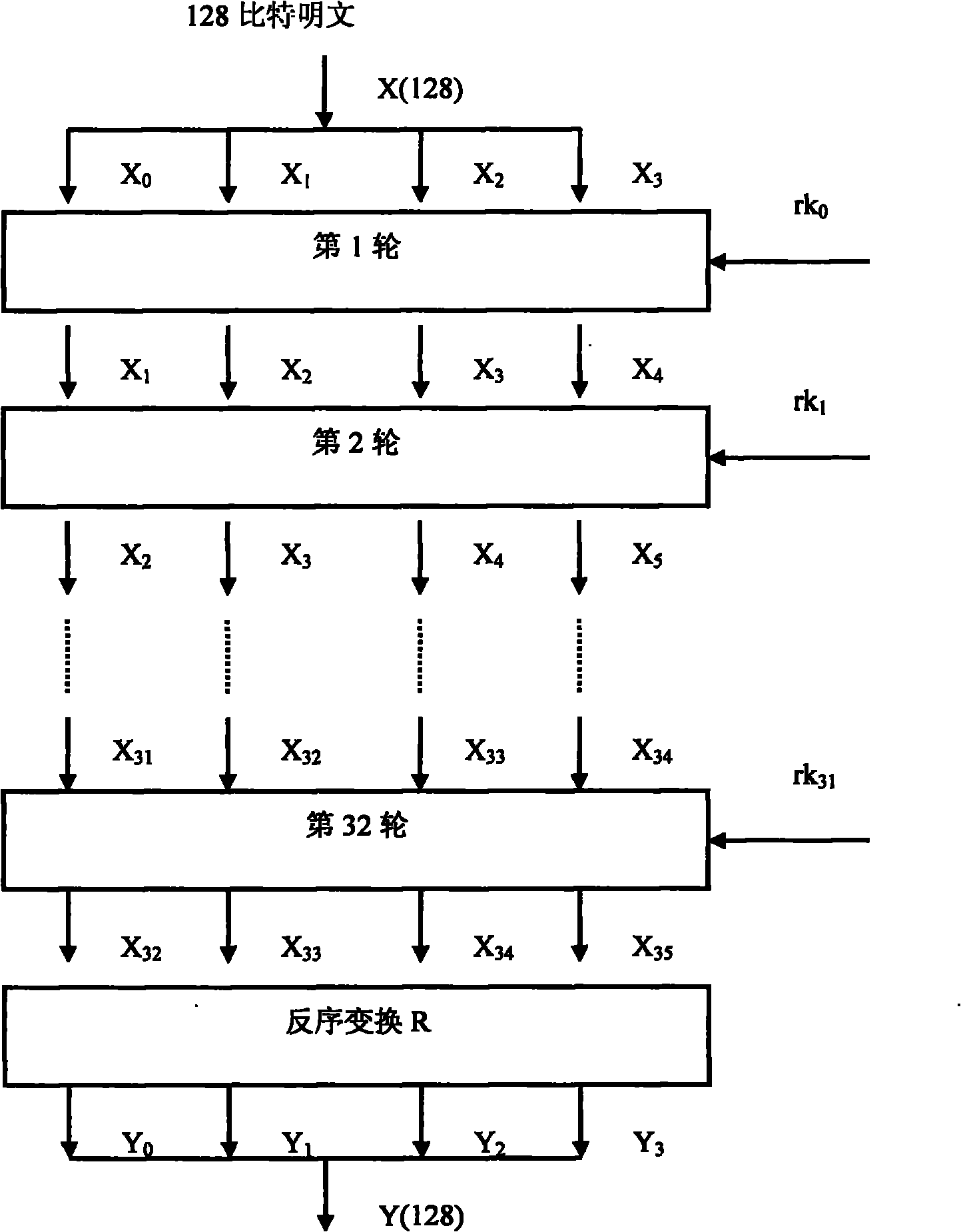
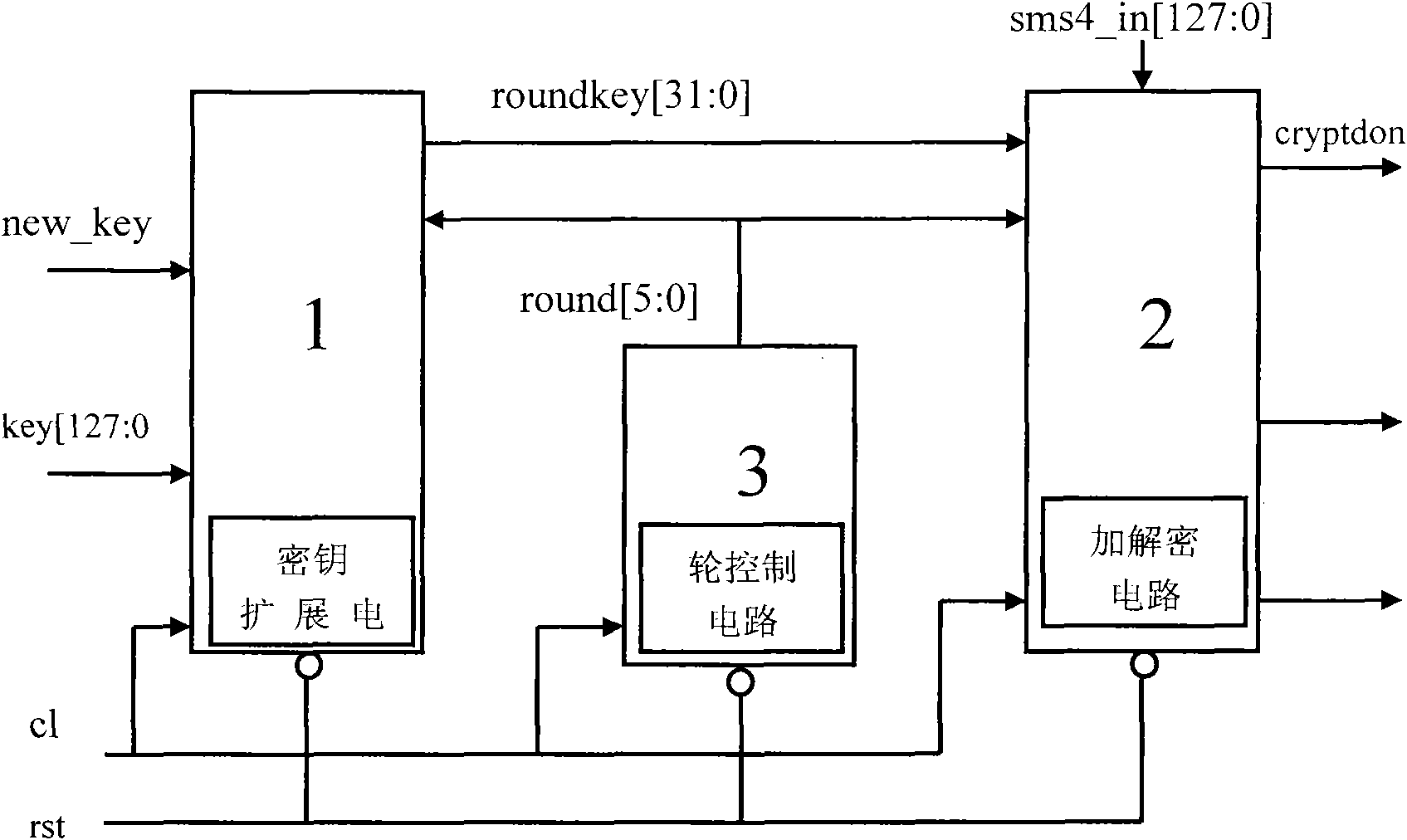
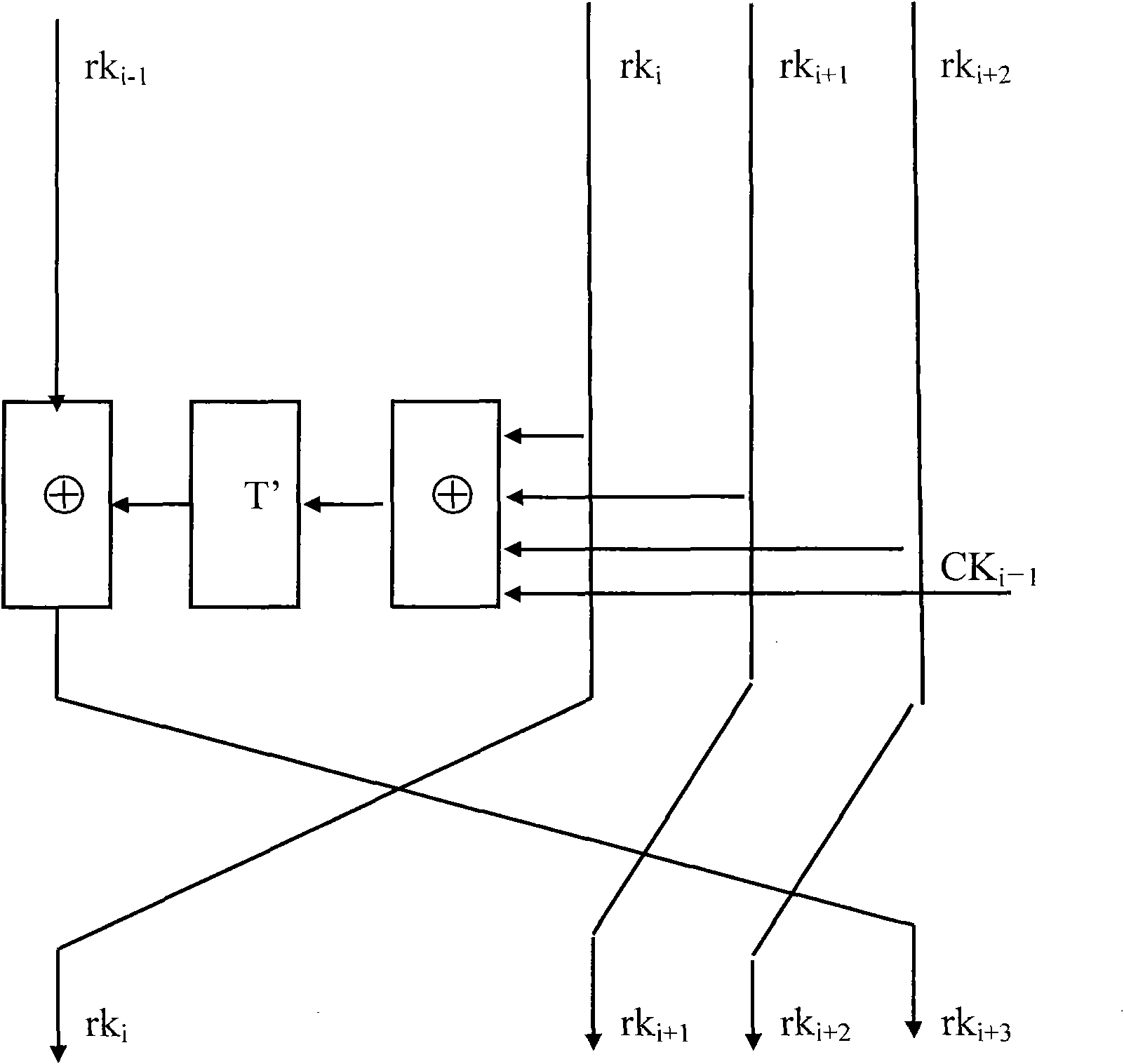
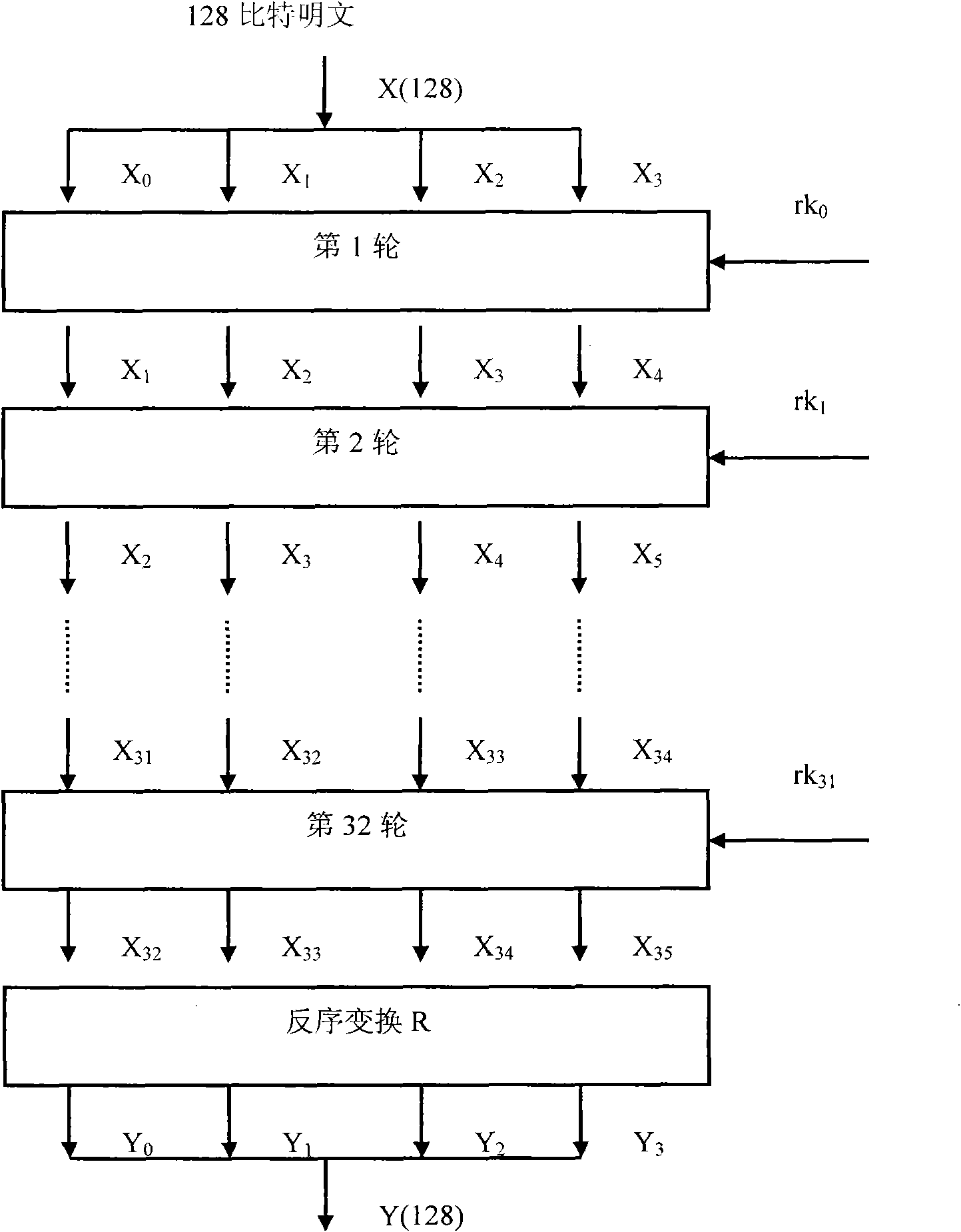
The invention relates to an algorithm hardware realizing method for improving network safety. The method comprises the following steps: dividing plaintext codes into 4 coded words by taking a word as a unit and dividing key codes into 4 key words by taking a word as a unit; after performing operation on the first key word to the third key word and a constant, performing exclusive-or operation on the zeroth key word to generate a first turn of key with one word length, forwards moving the position of from the first key word to the third key word to the position of from the zeroth key word and the second key word, and moving the first turn of key to the position of the third key word; after performing operation on the first turn of key and the first coded word to the third coded word, performing exclusive-or operation on the zeroth key word to generate a first turn of ciphertext word, forwards moving the position of from the first coded word to the third coded word to the position of from the zeroth coded word to the second coded word, and moving the first turn of ciphertext word to the position of the third coded word. By the method, the area for realizing algorithm hardware is compact, and the circuit area for realizing the algorithm hardware is greatly reduced on the premise of guaranteeing the algorithm realizing efficiency.
Owner:苏州国芯科技股份有限公司
Service realizing method and apparatus
InactiveCN1949257AAchieve flexibility and convenienceResourcesRelationship - FatherReal-time computing
Owner:HUAWEI TECH CO LTD
Implementation method of area-compact arithmetic hardware for wireless local area network
ActiveCN101945383ASimple designIncrease profitNetwork topologiesSecurity arrangementComputer hardwareCiphertext
The invention relates to an implementation method of area-compact arithmetic hardware for a wireless local area network. The method comprises the following steps of: dividing a plaintext code into four coded words by taking words as units, and dividing a secret key code into four secret key words by taking words as units; operating the secret key words from a first bit to a third bit and a constant; performing WXOR operation on the secret key word of a zeroth bit to generate a first round secret key with one word length; shifting the secret key words from the first bit to the third bit to thepositions of the secret key words from the zeroth bit to the second bit forwards; shifting the first round secret key to the position of the secret key word of the third bit; operating the first round secret key and the coded words from the first bit to the third bit, and performing the WXOR operation on the coded word of the zeroth bit to generate a first round ciphertext word with one word length; shifting the coded words from the first bit to the third bit to the positions of the coded words from the zeroth bit to the second bit forwards; and shifting the first round ciphertext word to theposition of the coded word of the third bit. The method of the arithmetic hardware is implemented with a compact area and greatly reduces circuit areas for realizing the arithmetic hardware on the premise of ensuring algorithm implementation efficiency.
Owner:苏州国芯科技股份有限公司
Method for controlling digital type controller of car electrical motor for scraping rain
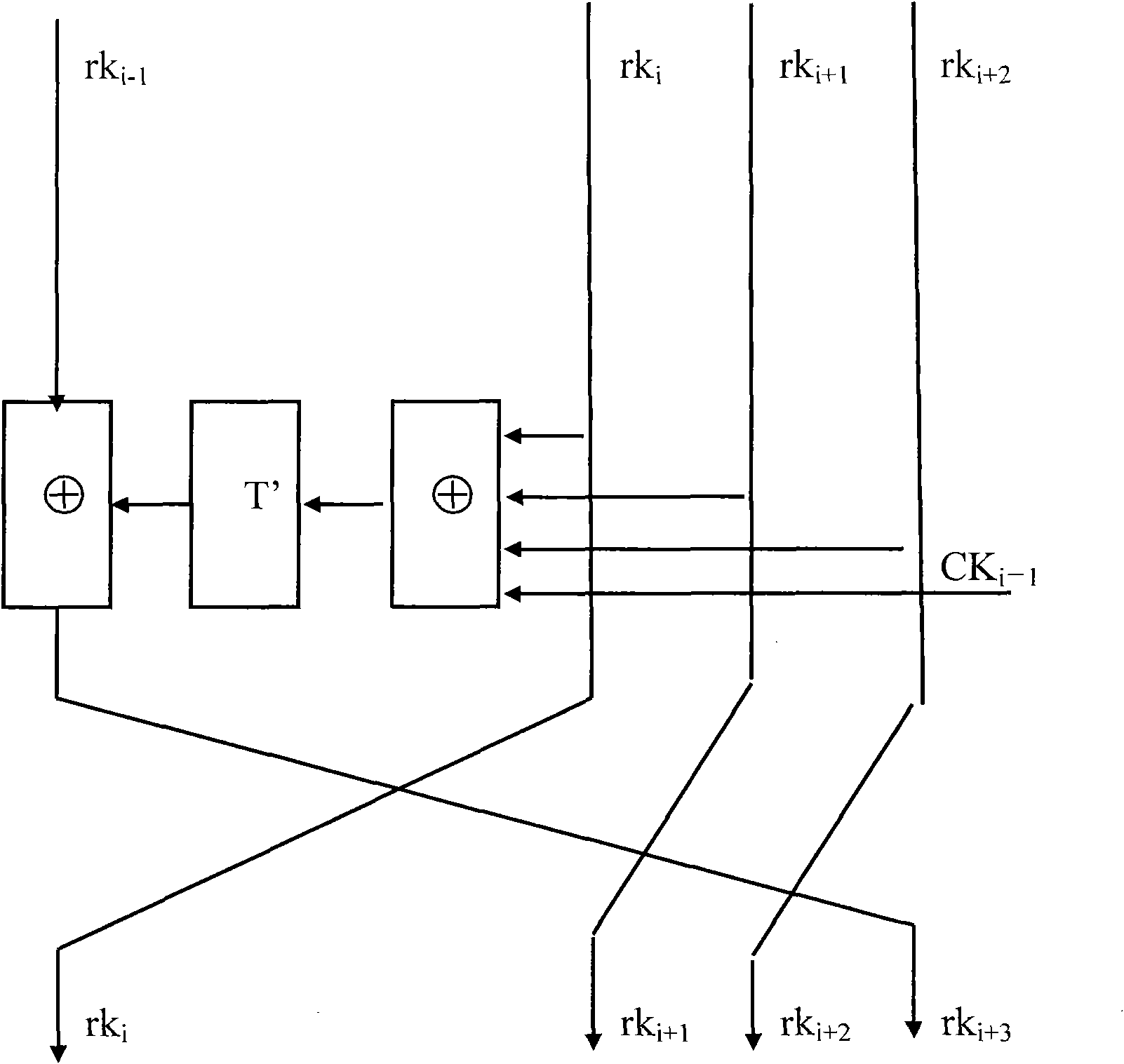
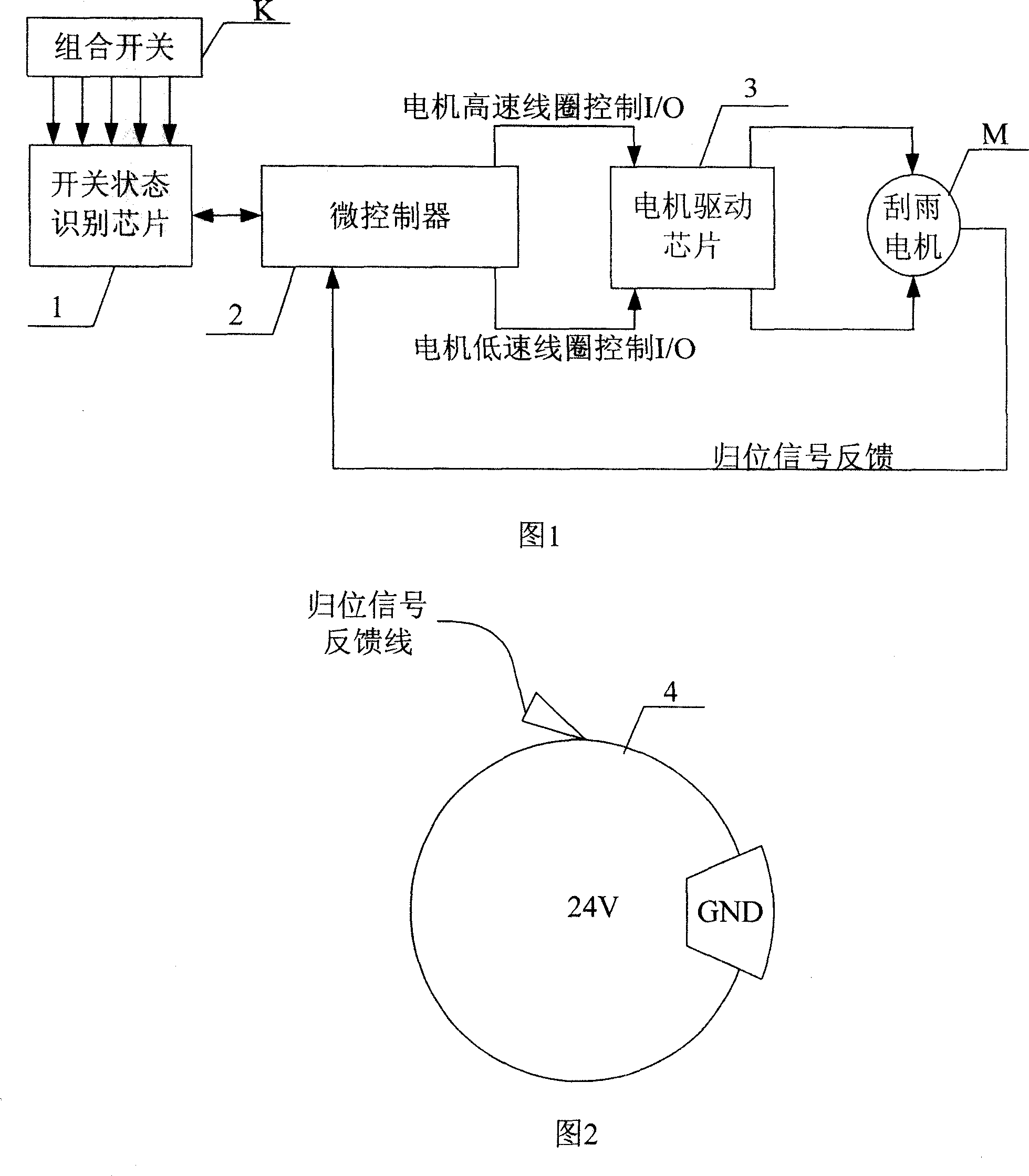
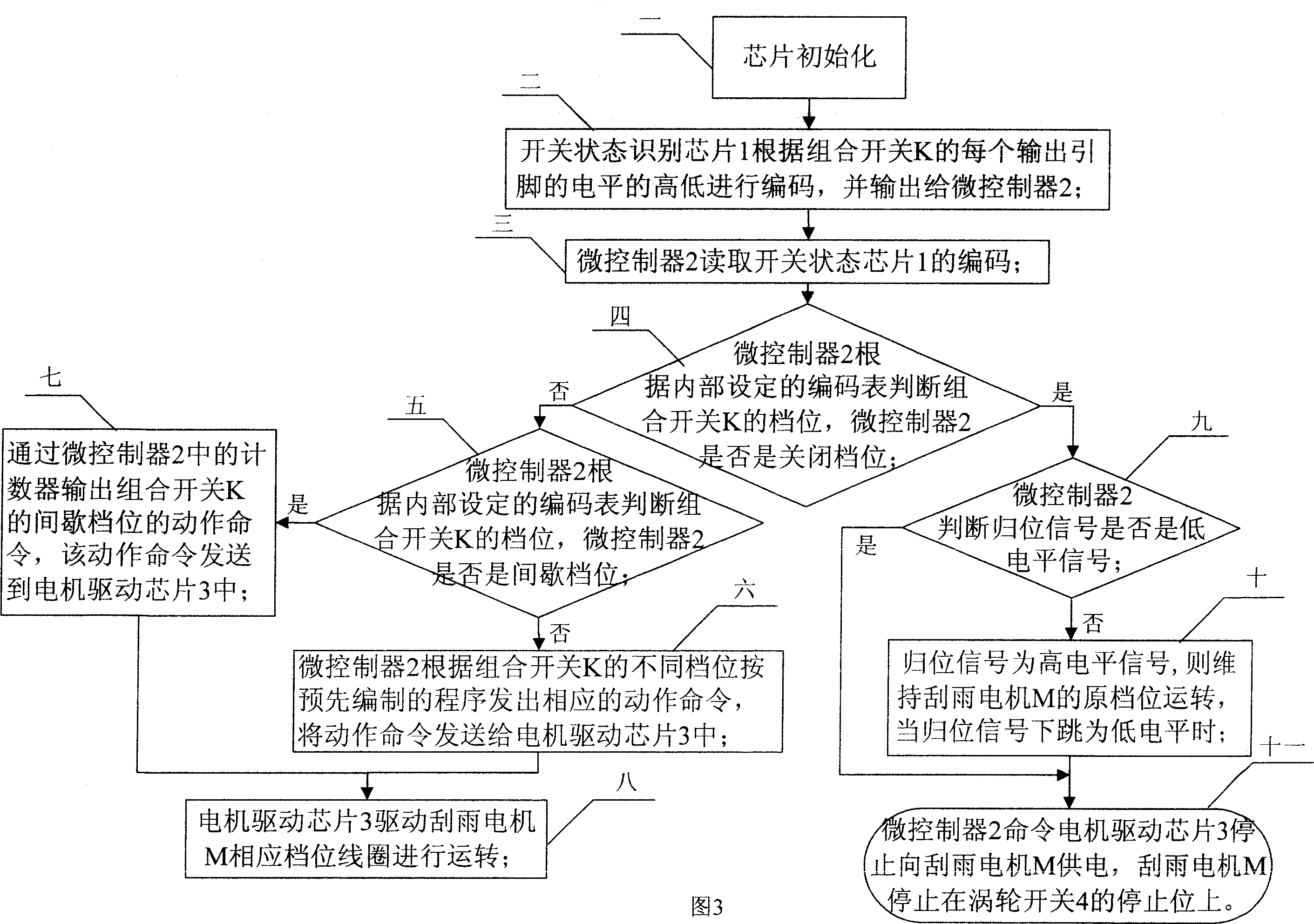
InactiveCN101004600AAccurate and reliable programmingHigh precisionProgramme controlComputer controlMicrocontrollerElectricity
A method for controlling digital controller of wiper motor on automobile includes initializing chip and carrying out coding as per level size, judging whether it is on closed gear or not by microcontroller according to coding table, judging whether it is on intermittent gear or not if it is not, sending action command to motor driving chip as per different gear program if it is not or otherwise driving relevant gear coil to be operated by driving motor, judging whether homing signal is on low level or not and stopping execution if it is or otherwise maintaining operation on original gear and stopping wiper when homing signal is jumped to low level.
Owner:HARBIN INST OF TECH
Discrete transceiver circuit suitable for high-speed 1553 bus
The invention aims at overcoming the defects in the prior art and provide a discrete transceiver circuit suitable for a high-speed 1553 bus. The discrete transceiver circuit suitable for the high-speed 1553 bus comprises a transmitter and a receiver; wherein the transmitter is connected with a protocol processor to finish the transmitting of a high-speed Manchester code, and the discrete transceiver circuit also comprises a voltage conversion driving circuit, a lateral double-diffused metal-oxide semiconductor (LDMOS) (or N-metal-oxide-semiconductor (NMOS)) and a resistor / capacitor with certain resistance and capacitance. The receiver comprises a first-order active filter, a comparator, a voltage reference and a voltage conversion driving circuit and is connected with the protocol processor through the voltage conversion driving circuit. The discrete transceiver circuit suitable for the high-speed 1553 bus has the advantages that the discrete transceiver circuit achieves the transmission of 1553 bus data at 10Mbps rate by cooperating with the external protocol processor to work, is built by adopting a discrete device without changing the original bus structure and is flexible and convenient in realization.
Owner:58TH RES INST OF CETC
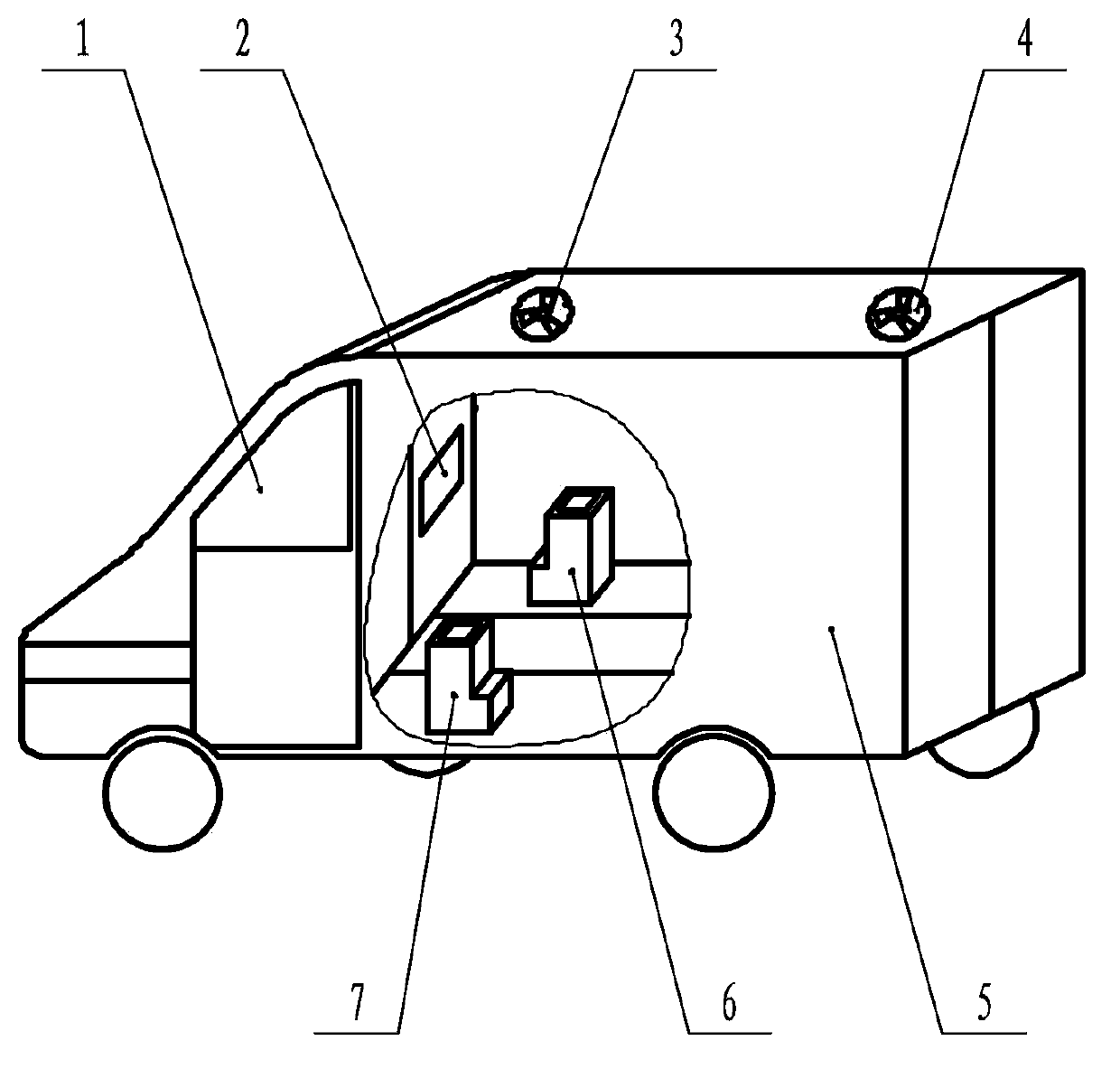
Temperature control system of tool car
InactiveCN104210326AAutomatic temperatureAutomatic humidityAir-treating devicesVehicle heating/cooling devicesTemperature controlSwitching signal
The invention relates to a temperature control system of a tool car. The temperature control system comprises an exhaust fan, an air inlet fan, a first air heater, a second air heater and a temperature and humidity measurement and control device, a relay is arranged on the temperature and humidity measurement and control device, the temperature and humidity measurement and control device is arranged in a tool car compartment and used for monitoring and displaying temperature and humidity in the tool car compartment in real time, and switching signals are sent to the relay. The temperature and humidity in the tool car compartment can be controlled, and therefore the electric power operation is safer. The temperature control system is scientific and reasonable in layout, low in energy consumption, low in cost, convenient and flexible to implement, high in efficiency and beneficial to application and popularization.
Owner:WUXI JINDANG MACHINERY FACTORY
Implementation method of area-compact arithmetic hardware for wireless local area network
ActiveCN101945383BSimple designIncrease profitEncryption apparatus with shift registers/memoriesComputer hardwareCiphertext
The invention relates to an implementation method of area-compact arithmetic hardware for a wireless local area network. The method comprises the following steps of: dividing a plaintext code into four coded words by taking words as units, and dividing a secret key code into four secret key words by taking words as units; operating the secret key words from a first bit to a third bit and a constant; performing WXOR operation on the secret key word of a zeroth bit to generate a first round secret key with one word length; shifting the secret key words from the first bit to the third bit to the positions of the secret key words from the zeroth bit to the second bit forwards; shifting the first round secret key to the position of the secret key word of the third bit; operating the first round secret key and the coded words from the first bit to the third bit, and performing the WXOR operation on the coded word of the zeroth bit to generate a first round ciphertext word with one word length; shifting the coded words from the first bit to the third bit to the positions of the coded words from the zeroth bit to the second bit forwards; and shifting the first round ciphertext word to the position of the coded word of the third bit. The method of the arithmetic hardware is implemented with a compact area and greatly reduces circuit areas for realizing the arithmetic hardware on the premise of ensuring algorithm implementation efficiency.
Owner:苏州国芯科技股份有限公司
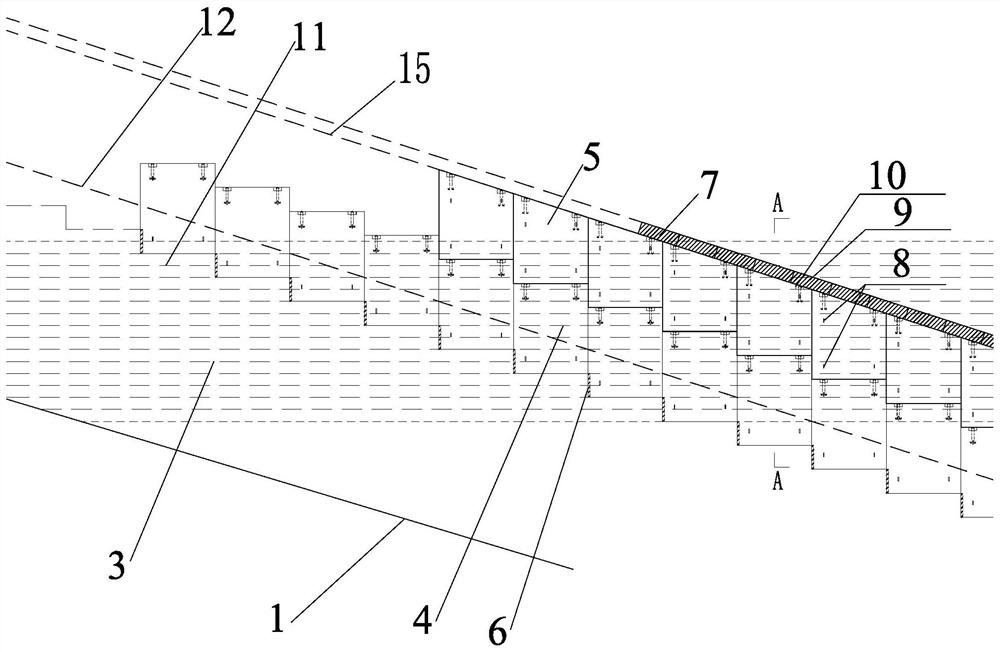
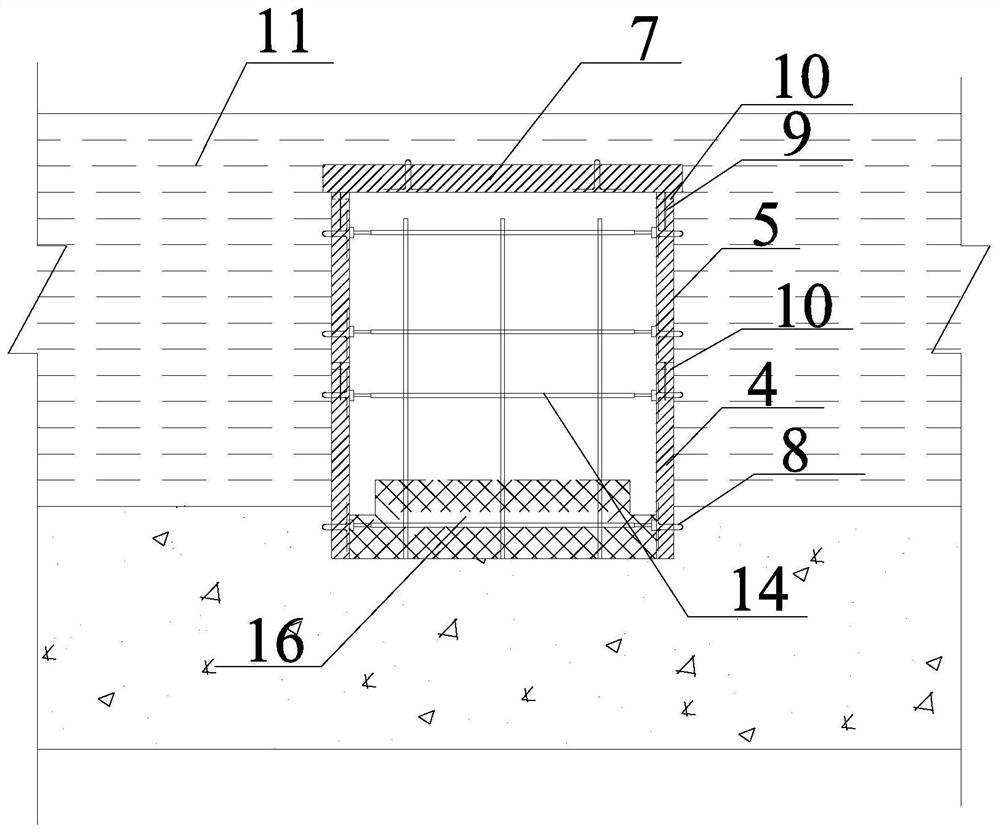
A kind of construction method of concrete in the climbing corridor part of roller compacted concrete dam
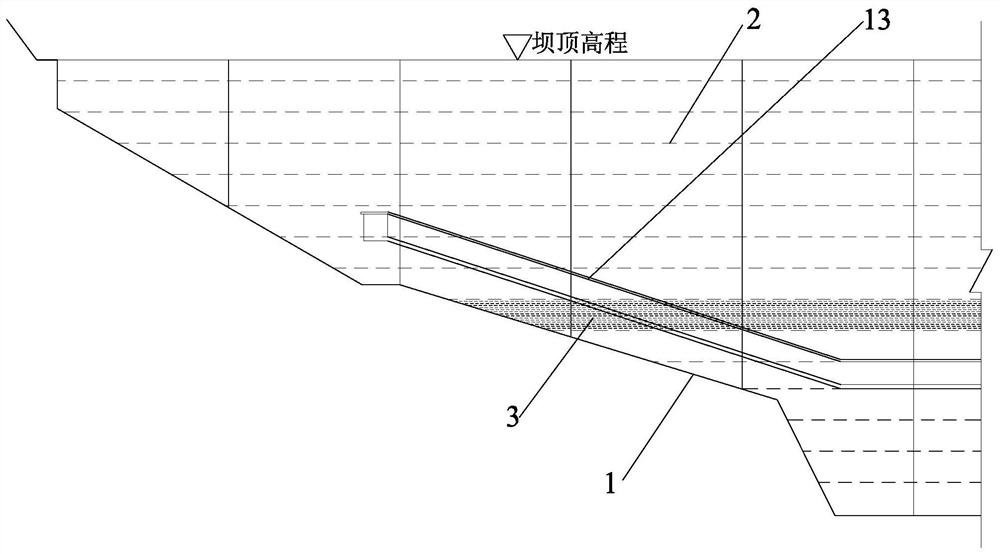
ActiveCN113684790BFast constructionReduce the amount requiredBarrages/weirsHydro energy generationRoller-compacted concreteButtress
The invention discloses a construction method for concrete at the part of the climbing corridor of a roller compacted concrete dam, comprising the steps of: first, layering the roller compacted concrete dam; When pouring the roller compacted concrete layer of any dam to be poured, the steps are as follows: 201. Set the control line of the corridor surface layer, 202. Install the prefabricated formwork and cover of the side wall of the corridor that meets the height of the two germ layers of RCC Slab formwork, 203. The first RCC pouring, 204, The formwork is extended forward, 205. The second RCC pouring, 206. Repeat 204 to 205 until the RCC pouring reaches the closing level, 207. Remove the formwork buttresses, and 208. Concrete the second-phase normal concrete pouring layer of the bottom surface layer of the pouring corridor. The template of the invention is prefabricated by upper and lower blocks, which is convenient and flexible, and the template assembly and the layer-by-layer laying and pouring of the roller compacted concrete germ layer are constructed synchronously.
Owner:SINOHYRDO ENG BUREAU 3 CO LTD
A Defense Method for Side Channel Attack and Fault Attack
ActiveCN103634102BImprove securityAchieve flexibility and convenienceEncryption apparatus with shift registers/memoriesPlaintextBlock cipher
The present invention provides a kind of protection method of side-channel attack and fault attack, and this method comprises the following steps: 1, the operation of block cipher algorithm is divided into several stages of pipelines; II, randomly select two stages of pipelines to input real plaintext, other levels The input is a random number; III, carry out the operation, when the operation is over, compare the two real data to see if the operation results are consistent. The method can resist both side-channel attack and fault attack, and has strong security and high execution efficiency.
Owner:STATE GRID CORP OF CHINA +4
Method and apparatus for recovering I2C bus locked by slave device
ActiveCN100504831CTroubleshoot recovery issuesLow costElectric digital data processingRecovery methodPower switching
Owner:ZTE CORP
Method for forming graph
InactiveCN101312113BAchieve etch removalRelaxed ThicknessSemiconductor/solid-state device manufacturingPhotoresistComputer science
The invention discloses a pattern forming method, which comprises steps of providing a lining, forming sacrificers on the lining, filling a destination layer between the sacrificers to form a destination matter, defining masks on the sacrificer and the destination matter, removing the destination matter under a groove arranged among the masks by etching, and removing the masks and the sacrificers.The pattern forming method reduces requirements upon the photolithographic process in micro-pattern forming, releases limits to the thickness of photoresist, and can form much more micronic patternsbeyond the exposure limit of exposure machines.
Owner:SEMICON MFG INT (SHANGHAI) CORP
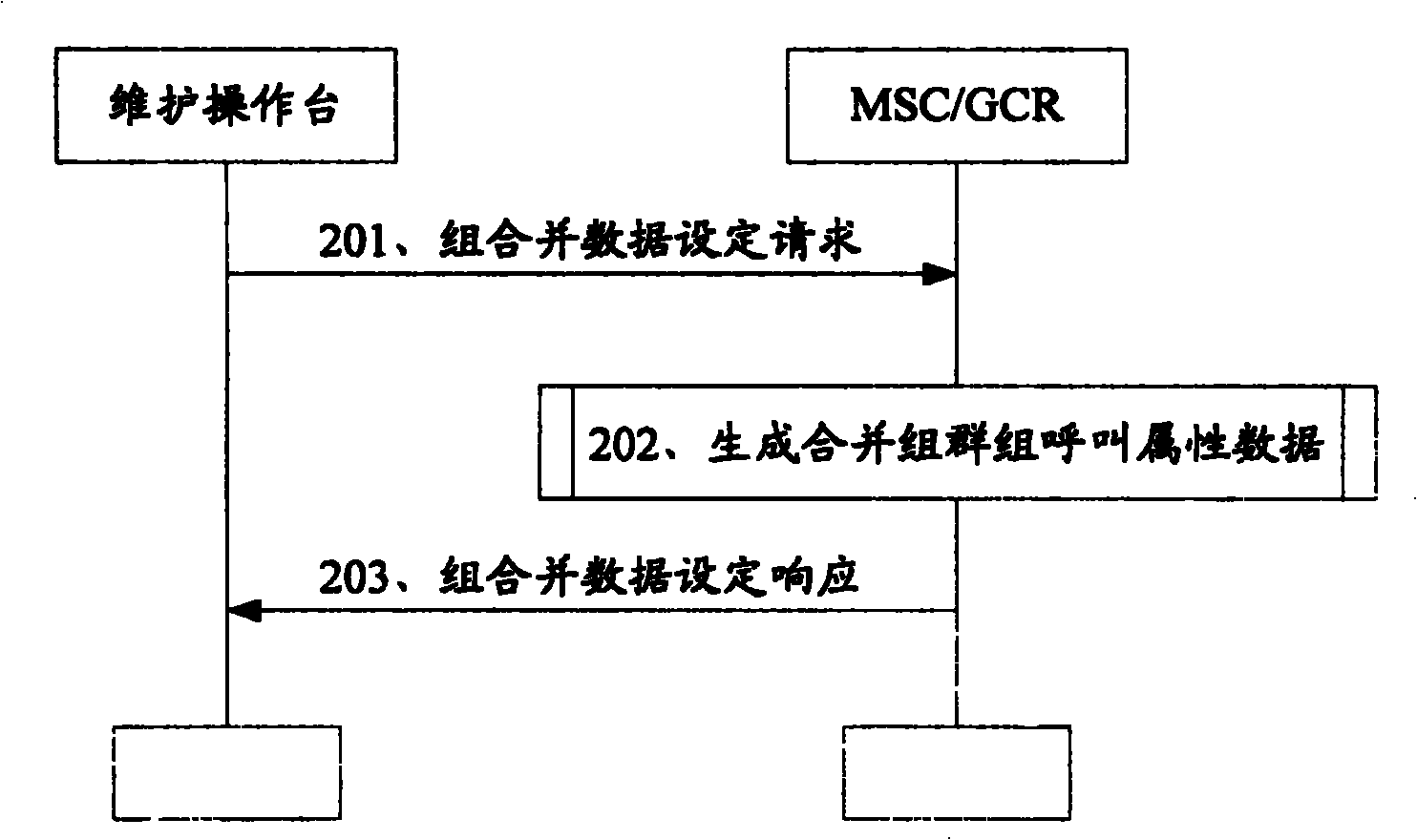
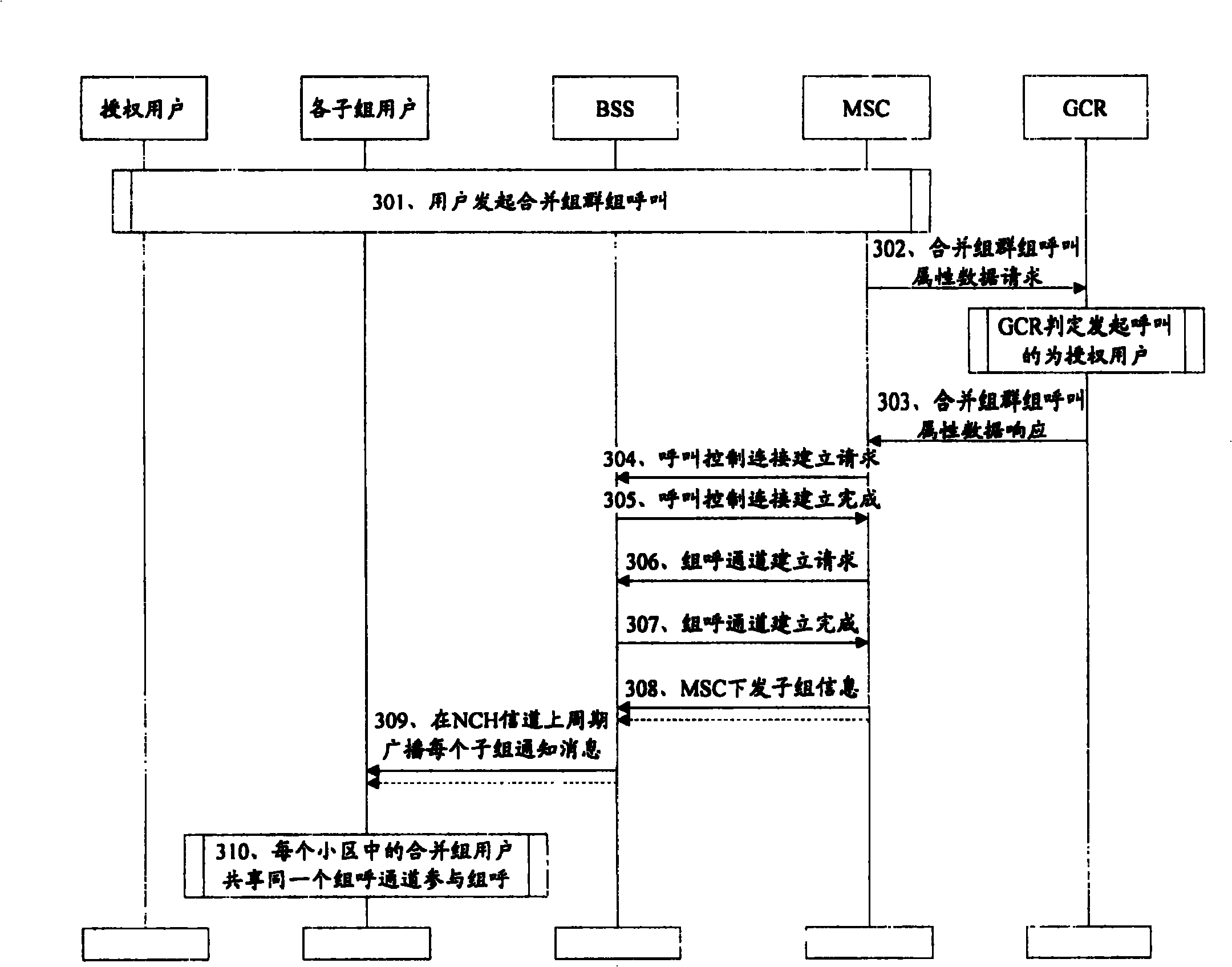
Method for realizing cluster call merging
InactiveCN100421477CMeeting Joint Communications NeedsAchieve flexibility and convenienceRadio/inductive link selection arrangementsTelecommunicationsSpeech sound
The present invention discloses realizing groups calling merged method. It contains network side pre-establishing mergence group containing at least one subgroup, saving mergence group and subgroup message, user terminal sending mergence group groups calling request carrying mergence group information to network side, network side according to mergence group message obtaining said mergence subgroup message from stored message; network side sending relevant subgroup information carried groups calling notification message in cell, any subgroup user terminal according to said groups calling notification message accessing groups call channel, to participate groups calling. Said invented method make having different group ID user capable of making speech communication in same mergence groups calling.
Owner:HUAWEI TECH CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com