A Defense Method for Side Channel Attack and Fault Attack
A side-channel attack and fault attack technology, which is applied to secure communication devices, encryption devices with shift registers/memory, digital transmission systems, etc., can solve the problems of being unable to resist fault attacks, occupying more resources, and low efficiency. Achieve the effect of easy implementation, reduction of additional resources, and strong security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0029] The present invention will be further described below in conjunction with accompanying drawing.
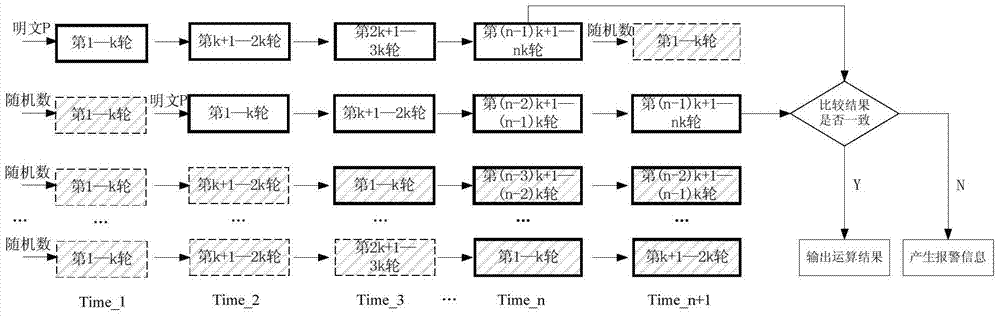
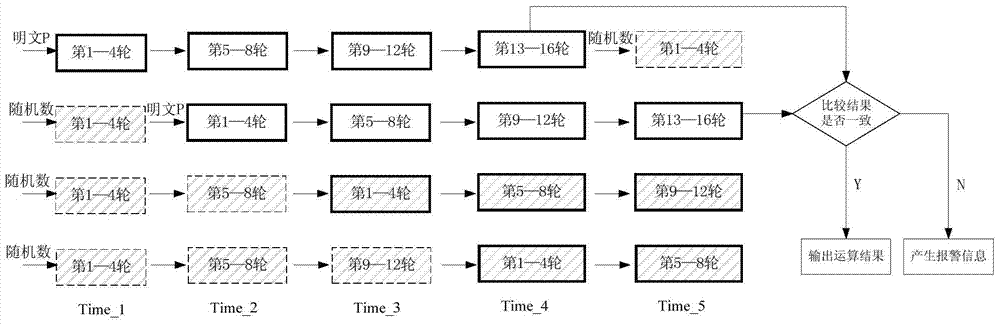
[0030] The invention provides a protection method against side channel attack and fault attack, and the method adopts pipeline technology. The method of the present invention is as follows: the operation of the block cipher algorithm is divided into several stages of pipelines, and two stages of pipelines are randomly selected, the input of the two stages of pipelines is real plaintext, and the input of other stages is random numbers.
[0031] Because at the same time, different levels of pipelines use different data to participate in the operation, and the side information generated when the random number participates in the operation is used as noise to cover up the side information generated by the real data participating in the operation, so that it can resist side channel attacks.
[0032] By comparing the operation results of the two real data at the end of the operat...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com