A method and device for protection based on user network access scenarios
A network access and scene technology, applied in the field of computer security, can solve problems such as information leakage
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
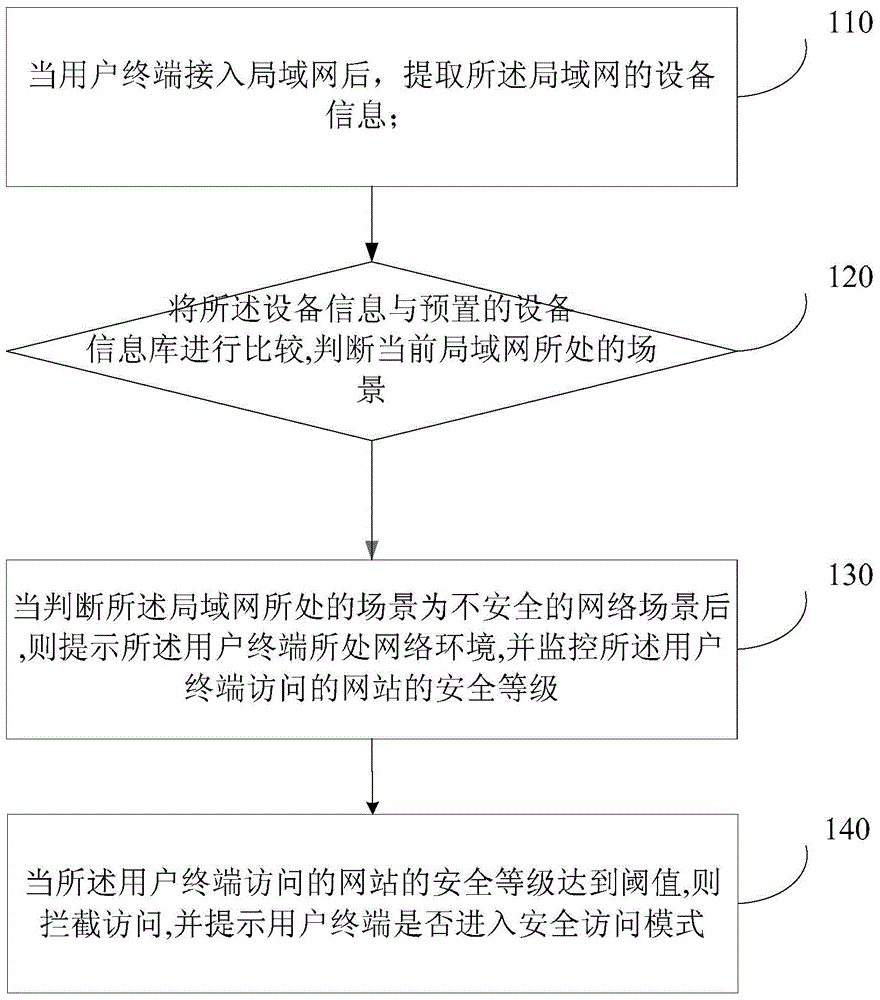
[0083] refer to figure 1 , which shows a schematic flowchart of Embodiment 1 of a protection method based on user network access scenarios of the present invention, which may specifically include:
[0084] Step 110, after the user terminal accesses the local area network, extract the device identification corresponding to the local area network;
[0085] After the user uses a mobile terminal such as a mobile phone or a laptop to access a local area network, such as a wireless local area network (such as wifi), to communicate with a wide area network (such as the Internet), then after the wireless local area network, the data corresponding to the accessed LAN can be extracted. Device identification, such as the MAC of the corresponding router, or SSID (Service Set Identifier, service set identification), etc.
[0086] Step 120, comparing the device identifier with a preset device identifier library, and judging the scene where the current local area network is located;
[008...
Embodiment 2
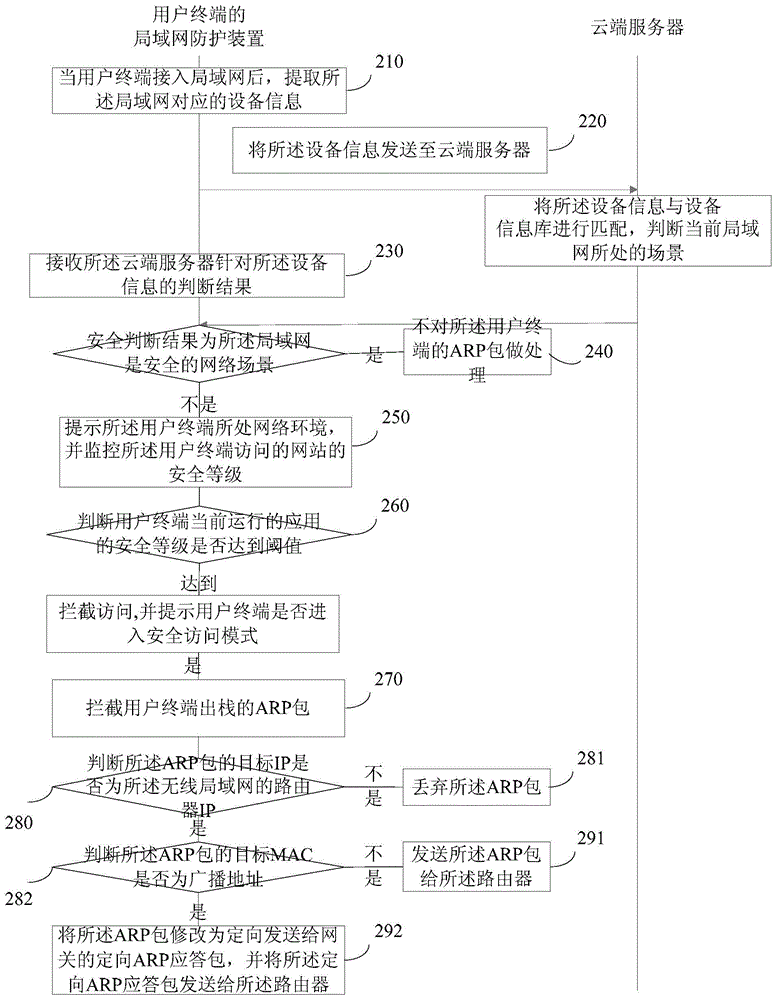
[0128] refer to figure 2 , which shows a schematic flowchart of Embodiment 2 of a protection method based on user network access scenarios in the present invention, which may specifically include:
[0129] Step 210, after the user terminal accesses the local area network, extract the device identification corresponding to the local area network;
[0130] For example, obtain information such as the SSID of the wireless LAN and the MAC address of the network card.
[0131] Step 220, sending the device identifier to a cloud server; the cloud server is suitable for matching the device identifier with a device identifier library, and judging the current local area network scene;
[0132] Step 230, receiving the judgment result of the cloud server for the device identification; if the security judgment result is that the local area network is a safe network scene, proceed to step 240; if the security judgment result is that the local area network is not In a safe network scenario...
Embodiment 3
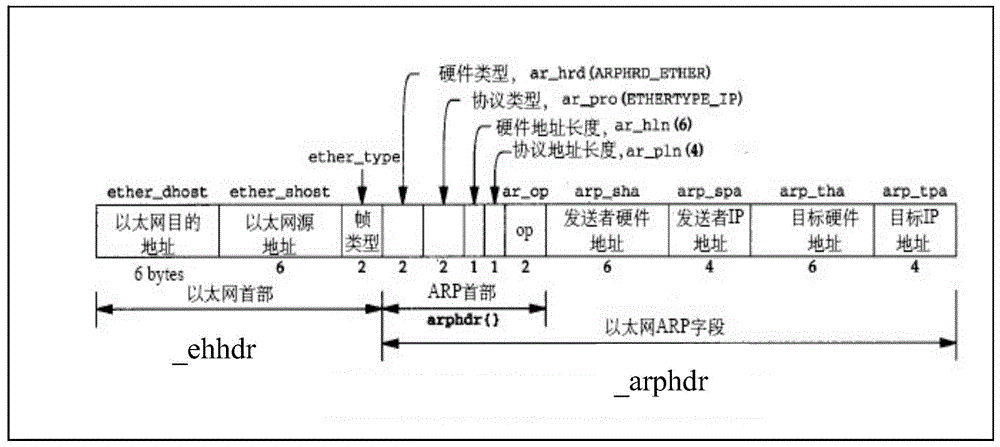
[0177] refer to image 3 , which shows a schematic structural diagram of a protection device based on user network access scenarios of the present invention, which may specifically include:
[0178] The device identification extraction module 310 is adapted to extract the device identification corresponding to the local area network when the user terminal accesses the local area network;
[0179] The scene judging module 320 is adapted to compare the device identification with a preset device identification library, and judge the scene where the current local area network is located;
[0180] The first prompting module 330 is adapted to prompt the network environment where the user terminal is located when the scene where the local area network is located is an unsafe network scene, and monitor the security level of the website visited by the user terminal;
[0181] The second prompt module 340 is adapted to intercept the access when the security level of the website accessed...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com