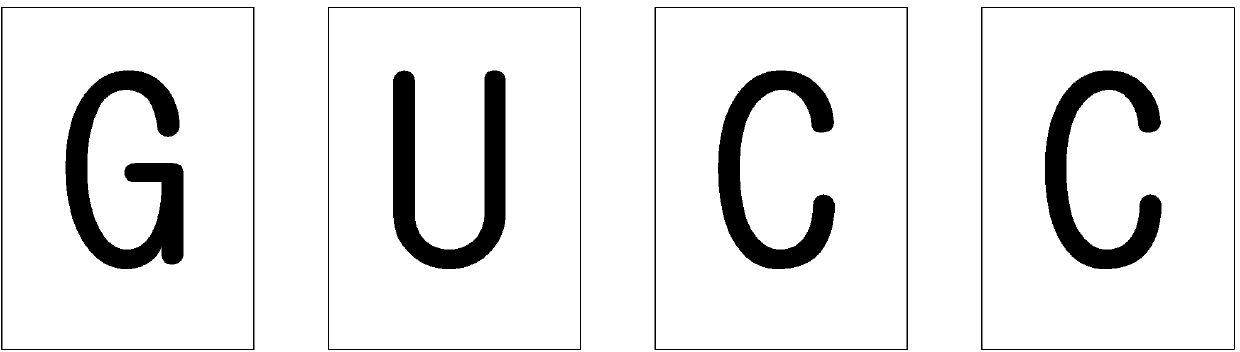Method and device for generating dynamic verification code picture, and verification method and device
A technology for dynamic verification code and generating device, applied in the field of network security, can solve problems such as endangering network security, and achieve the effects of increasing difficulty, improving network security, and reducing automatic recognition rate
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example
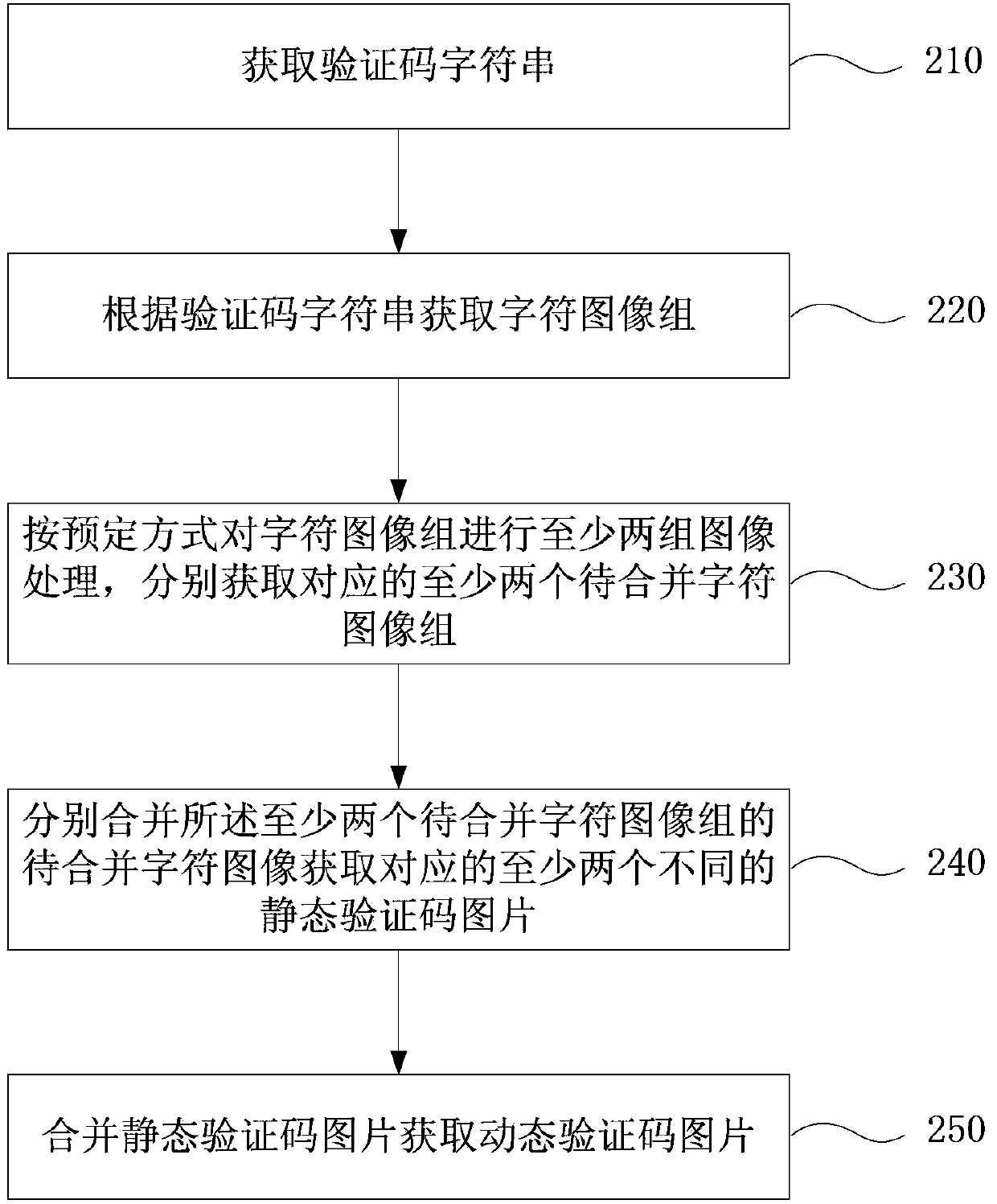
[0051] figure 2 It is a flow chart of the method for generating a dynamic verification code picture according to the first embodiment of the present invention. Such as figure 2 As shown, the method includes:
[0052] Step 210, obtaining a verification code string.
[0053] Specifically, the verification code string includes at least two characters. In the embodiment of the present invention, a character refers to the smallest ideographic symbol of human language, which includes numbers, letters, Chinese characters and symbols, wherein the letters may include English letters, Latin letters, Greek letters and so on. Meanwhile, a character string refers to a character sequence consisting of at least two characters. For example, the verification string "GUCC" is a string consisting of 4 uppercase English letters.
[0054] In this step, the verification code string can be generated by a random function or a pseudo-random function. For example, several random numbers are gen...
no. 2 example
[0081] Figure 9 It is a flow chart of fuzzy processing in the method for generating a dynamic verification code picture according to the second embodiment of the present invention. The overall steps of the second embodiment of the present invention are the same as those of the first embodiment, but at least two sets of fuzzy processing and rigid body transformation processing are performed on the character image groups in a predetermined manner, and the corresponding at least two character image groups to be merged are obtained respectively. Among them, different methods are used for fuzzy processing. The flow of fuzzy processing is as follows: Figure 9 shown, including:
[0082] Step 910, selecting a specific character in the verification code string as an anchor character.
[0083] Selecting the anchor character is to provide a reference position for subsequent steps to set different blur levels for characters at different positions. For the blurring of different groups...
no. 3 example
[0093] Figure 10 It is a flow chart of fuzzy processing in the method for generating a dynamic verification code picture according to the third embodiment of the present invention. The overall steps of the third embodiment of the present invention are the same as those of the first embodiment, but at least two sets of fuzzy processing and rigid body transformation processing are performed on the character image groups in a predetermined manner, and the corresponding at least two character image groups to be merged are respectively obtained. In , different methods are used for fuzzy processing. The flow of fuzzy processing is as follows Figure 10 shown, including:
[0094] Step 1010, selecting a specific character in the verification code string as an anchor character.
[0095] Selecting the anchor character is to provide a reference position for the subsequent steps to set different blurring methods for characters at different positions. For the blurring of different grou...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com