Method and equipment for protecting JAVA executable program
A technology for executing programs and devices, applied in the field of software protection, which can solve problems such as attacks, name and symbol confusion, and unsatisfactory automatic algorithm effects, so as to protect logic and processes, increase the difficulty of analysis and cracking, and improve security.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
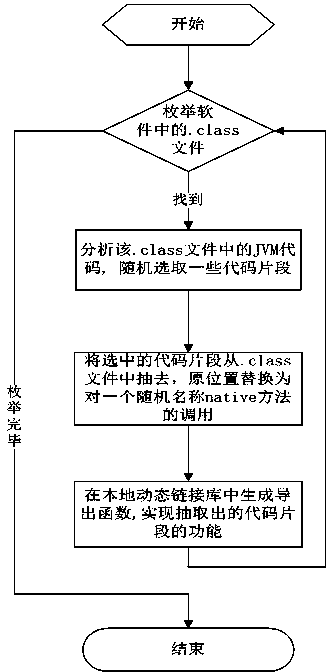
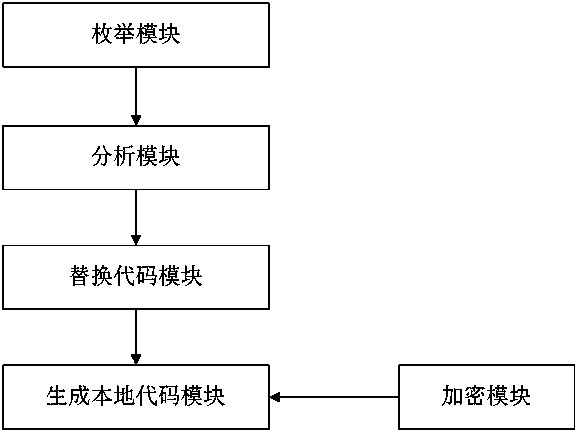
Method used
Image
Examples
specific example
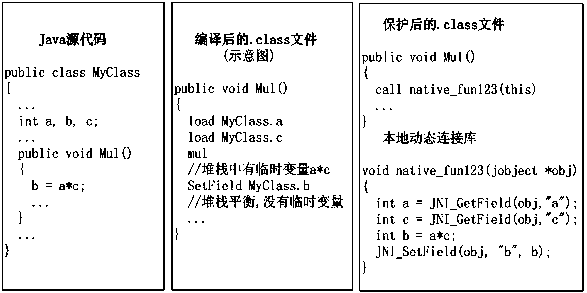
[0050] According to an embodiment of the present invention, such as figure 1 as shown, figure 1 Including the code snippets of each part in this embodiment. The specific example is as follows: A certain software written by JAVA has a class MyClass in the source code, which defines three fields a, b, c and an instance method Mul, the logic of this method is to compare the value of field b with c Multiply, and assign the result to field a.
[0051] When the Java source code is compiled, a .class file will be generated for each class. The structure of the .class file is defined in the JVM document and is a collection of a series of attributes and values. By parsing the class name-related attributes in the .class file, you can know which class it comes from in the source code; and then parsing the method table attributes, you can get a list of all methods in the class; parsing the Code attribute of each method, you can get The JVM bytecode of the method.
[0052] E.g figure 1...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com