High-grade privacy smart phone and method for protecting private information thereof
A smart phone, privacy technology, applied in telephone communication, wireless communication, security devices, etc., can solve the problems of easy theft of private information and easy intrusion of the system, so as to prevent intrusion and residue, and prevent private information from being stolen Access, high confidentiality effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
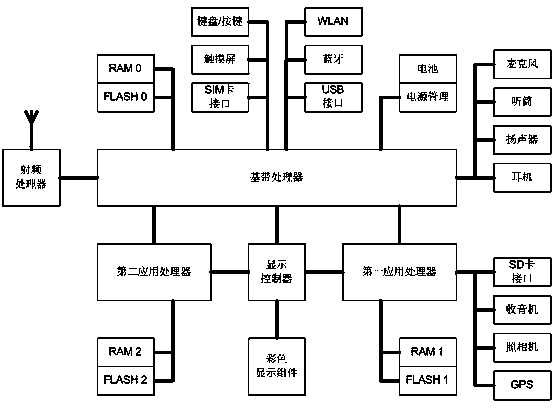
[0037] A high-level privacy smart phone includes: a baseband processor, a first application processor, a second application processor, a display controller, and a display component,
[0038] A radio frequency processor, data memory RAM 0, program memory FLASH 0 and an interface circuit are connected to the baseband processor;
[0039] The first application processor is connected to the baseband processor, a first data memory RAM 1 and a first program memory FLASH 1 are connected to the first application processor, and a first operating system is set in the first application processor;
[0040] The second application processor is connected to the baseband processor, a second data memory RAM 2 and a second program memory FLASH 2 are connected to the second application processor, and a second operating system is set in the second application processor,
[0041] The display controller is connected to a baseband processor, a first application processor, and a second application processor, r...
Embodiment 2
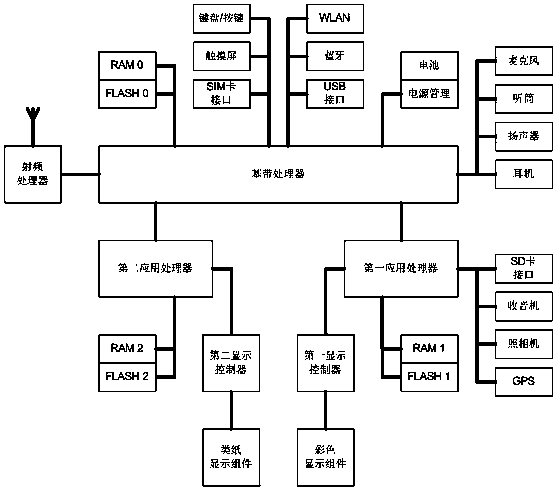
[0044] A high-level privacy smart phone includes: a baseband processor, a first application processor, and a second application processor,
[0045] A radio frequency processor, data memory RAM 0, program memory FLASH 0 and an interface circuit are connected to the baseband processor;
[0046] The first application processor is connected to the baseband processor, the first data memory RAM 1 and the first program memory FLASH 1 are connected to the first application processor, the first operating system is set in the first application processor, and A first color display controller is connected to the first application processor, and a first color display component is connected to the display controller. The color display component is responsible for multimedia application display tasks of the first operating system and with better visual performance requirements. ;
[0047] The second application processor is connected to the baseband processor, a second data memory RAM 2 and a seco...
Embodiment 3
[0050] A method for protecting private information of a smart phone, the smart phone comprising:
[0051] Baseband processor, first application processor, second application processor and display controller, display component,
[0052] A radio frequency processor, data memory RAM 0, program memory FLASH 0 and an interface circuit are connected to the baseband processor;
[0053] The first application processor is connected to the baseband processor, a first data memory RAM 1 and a first program memory FLASH 1 are connected to the first application processor, and a first operating system is set in the first application processor;
[0054] The second application processor is connected to the baseband processor, a second data memory RAM 2 and a second program memory FLASH 2 are connected to the second application processor, and a second operating system is set in the second application processor,
[0055] The display controller is connected to a baseband processor, a first application proc...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com