Webpage trojan-linking real-time protection method and system based on cloud
A technology of real-time protection and web security, applied in transmission systems, electrical components, etc., can solve the problems of inability to perform web security real-time protection, web security real-time protection, and large impact range, and achieve zero deployment and zero calculation. Overhead, the effect of preventing proliferation
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0052] The present invention will be further described below in conjunction with the accompanying drawings and embodiments.
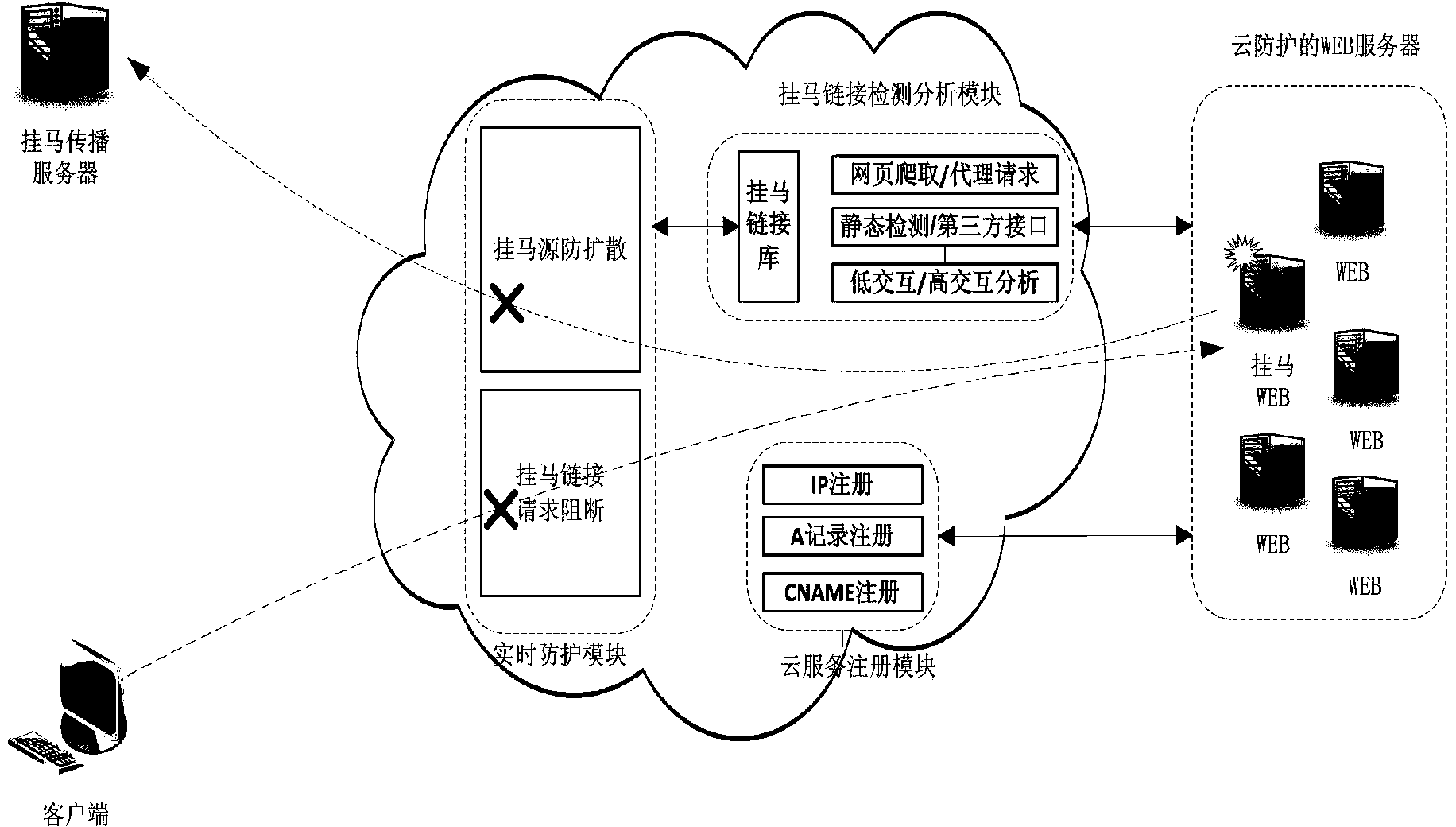
[0053] Such as figure 1 As shown, the cloud platform of the web page Trojan real-time protection system includes: a real-time protection module, a Trojan link detection and analysis module, and a cloud service registration module.
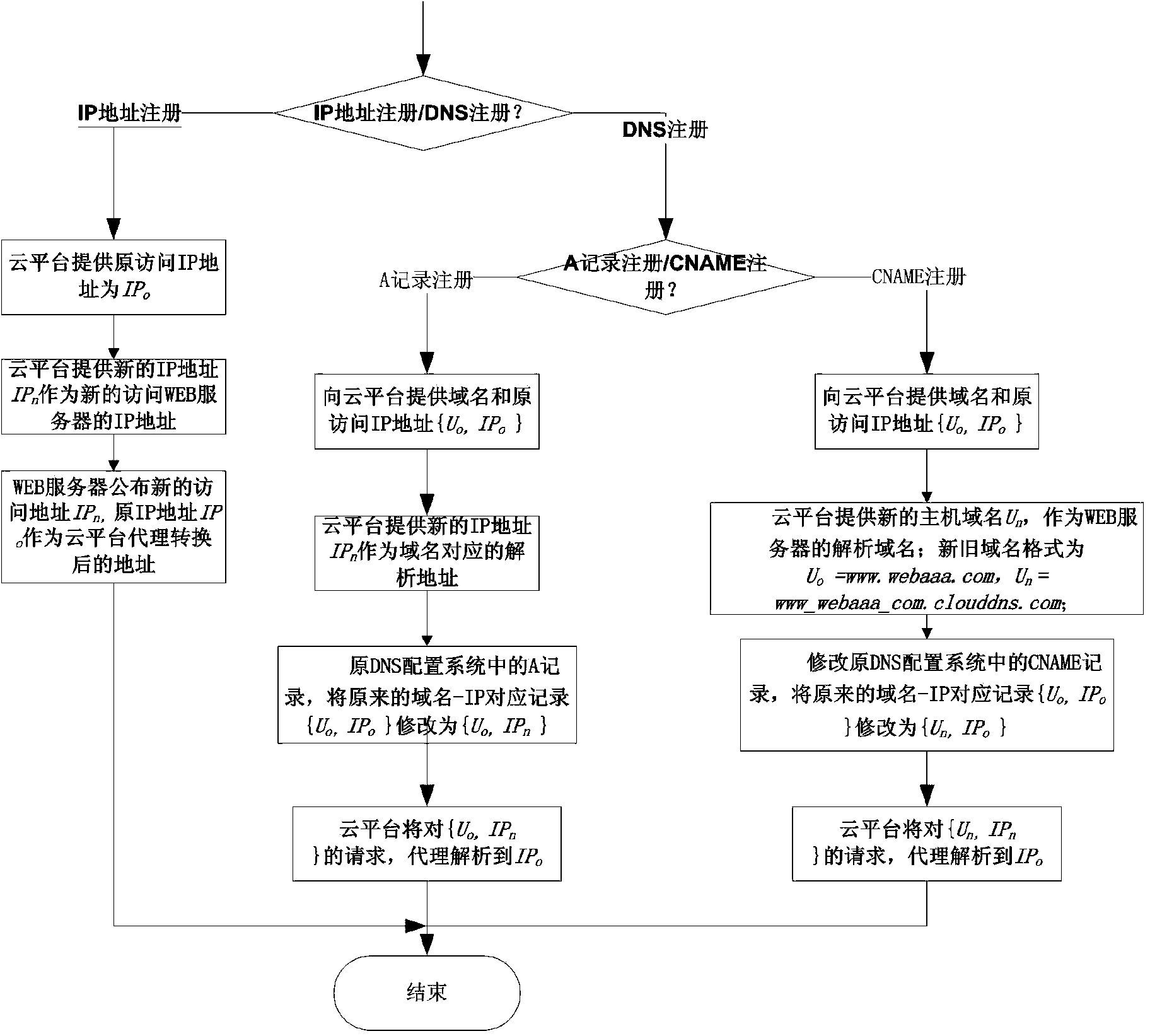
[0054] The real-time protection module includes two sub-modules: blocking of link requests of Trojans and non-proliferation of Trojan sources. After the real-time protection module receives the access request from the client or the hotlinking request sent by the third-party untrusted server, it quickly queries and matches the requested link with the Trojan link information library provided by the Trojan link detection and analysis module, so as to determine whether Visited the hanging horse link. If it is to access the linked horse link, then block the request to achieve a real-time protection effect, prevent the client fr...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com