Remote wireless identity authentication system
An identity authentication and remote wireless technology, which is applied in the field of remote wireless identity authentication system, can solve problems such as unfavorable development of integrated equipment, increase of system development cost, and poor adaptability to the environment, so as to ensure safety, ensure safety, and ensure leaked effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
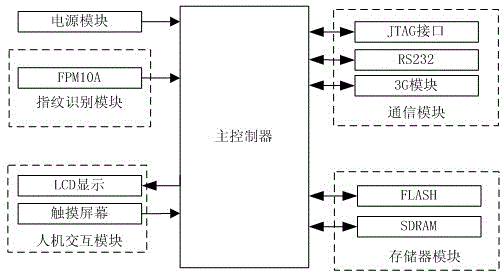
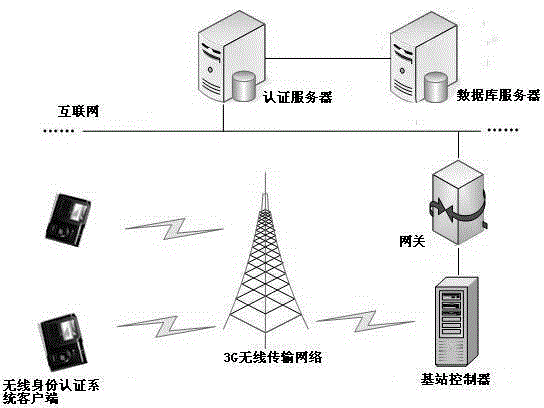
[0033] figure 1 It is the overall block diagram of the system of the present invention, figure 2 It is a general diagram of the client design of the wireless identity authentication system of the present invention. The remote wireless identity authentication system is composed of a wireless identity authentication system client and a remote server. The client side of the wireless identity authentication system is equipped with a fingerprint collection module and a communication module A, and the fingerprint collection module is used to collect fingerprint grayscale images and extract fingerprint feature data from the grayscale images , The fingerprint collection module is connected with the communication module A, and the communication module A sends the request message of the fingerprint feature data from the wireless identity authentication system client to the remote server end by means of wireless communication; the remote server end is a server group, composed of It co...
Embodiment 2
[0035] figure 1 It is an overall block diagram of the system of the present invention, and the remote wireless identity authentication system is composed of a wireless identity authentication system client and a remote server. The client side of the wireless identity authentication system is equipped with a fingerprint collection module and a communication module A, and the fingerprint collection module is used to collect fingerprint grayscale images and extract fingerprint feature data from the grayscale images , The fingerprint acquisition module is connected with the communication module A, and the communication module A sends the request message of the fingerprint feature data from the wireless identity authentication system client to the remote server end through wireless communication; the remote server end is a server group, composed of a It consists of a hardware firewall device, an authentication server, and two fingerprint database servers. The authentication server ...
Embodiment 3
[0042] figure 1 It is an overall block diagram of the system of the present invention, and the remote wireless identity authentication system is composed of a wireless identity authentication system client and a remote server. The client side of the wireless identity authentication system is equipped with a fingerprint collection module and a communication module A, and the fingerprint collection module is used to collect fingerprint grayscale images and extract fingerprint feature data from the grayscale images , The fingerprint acquisition module is connected with the communication module A, and the communication module A sends the request message of the fingerprint feature data from the wireless identity authentication system client to the remote server end through wireless communication; the remote server end is a server group, composed of a It consists of a hardware firewall device, two authentication servers, and a fingerprint database server. The authentication server i...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com