Method and device for detecting website backdoor program
A program detection and backdoor technology, applied in the Internet field, can solve problems such as lack of detection methods, website harm, and impact on website image, so as to achieve the effect of improving the security level and reducing the probability of harm.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
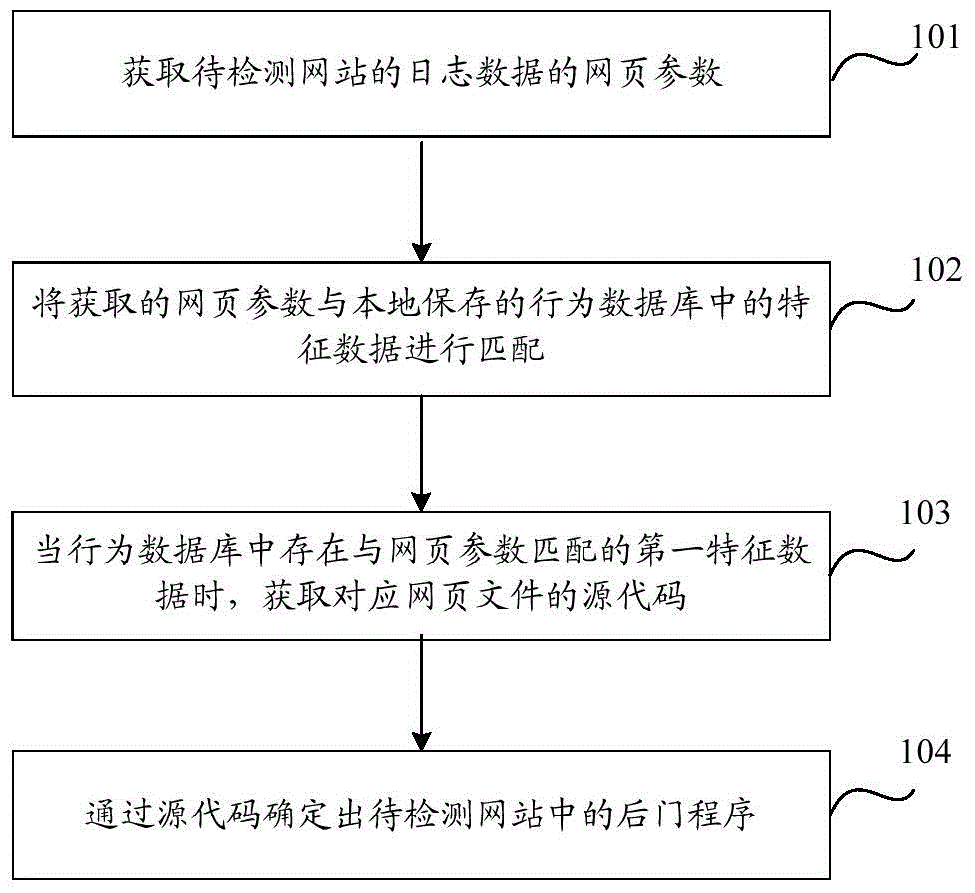
[0025] Embodiment one: see figure 1 , the process of backdoor program detection includes:
[0026] Step 101: Obtain web page parameters of log data of the website to be detected.
[0027] Generally, the log data of a website includes: host, time, IP address, Uniform Resource Locator (Uniform Resource Locator, URL), web page parameters and other information. The web page parameters of the log data of the website to be detected can be extracted.
[0028] Step 102: Match the obtained web page parameters with the characteristic data in the locally saved behavior database.
[0029] In the embodiment of the present invention, the behavior database has been saved locally, and the characteristic data in the behavior database are all formed according to the disclosed backdoor program. Therefore, the webpage parameters can be matched with the characteristic data in the locally saved behavior database.
[0030] Step 103: When there is the first characteristic data matching the web pag...
Embodiment 2
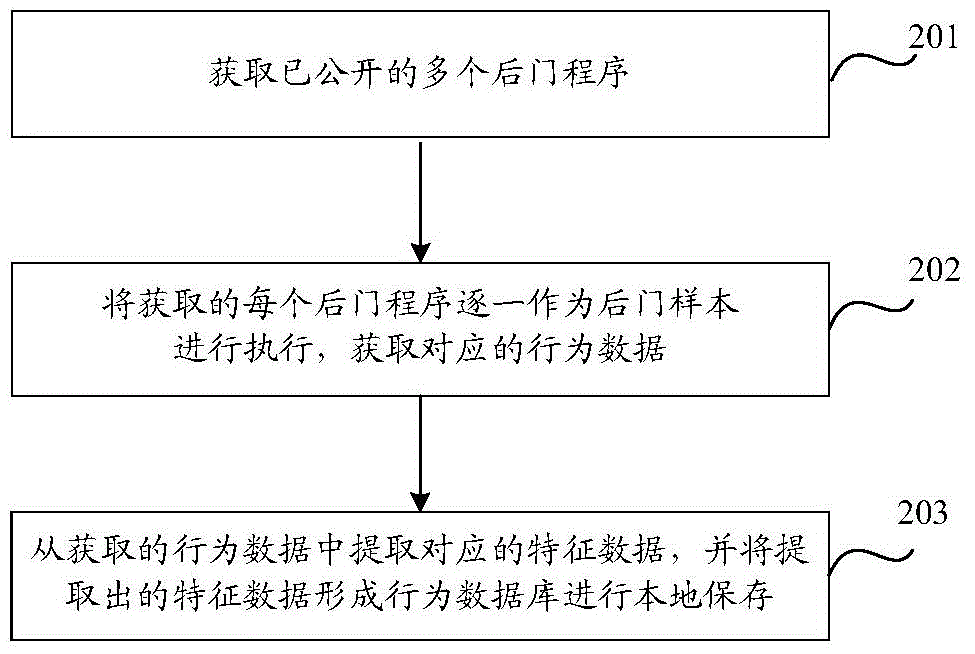
[0038] Embodiment 2: In the process of detecting backdoor programs, a locally stored behavior database is required, and this behavior database can be formed based on published backdoor programs. see figure 2 , the local preservation process of the behavior database in this embodiment includes:
[0039] Step 201: Obtain multiple backdoor programs that have been published.
[0040] Many common backdoor programs are generally disclosed, or some backdoor programs will be disclosed once they are detected. In this way, there will be many disclosed backdoor programs, and these disclosed multiple backdoor programs will be obtained automatically or manually.
[0041] Step 202: execute each obtained backdoor program as a backdoor sample one by one, and obtain corresponding behavior data.
[0042] After obtaining the backdoor program, it needs to be executed as a backdoor sample, so that the corresponding behavior data can be obtained.
[0043] Each obtained backdoor program can be e...
Embodiment 3
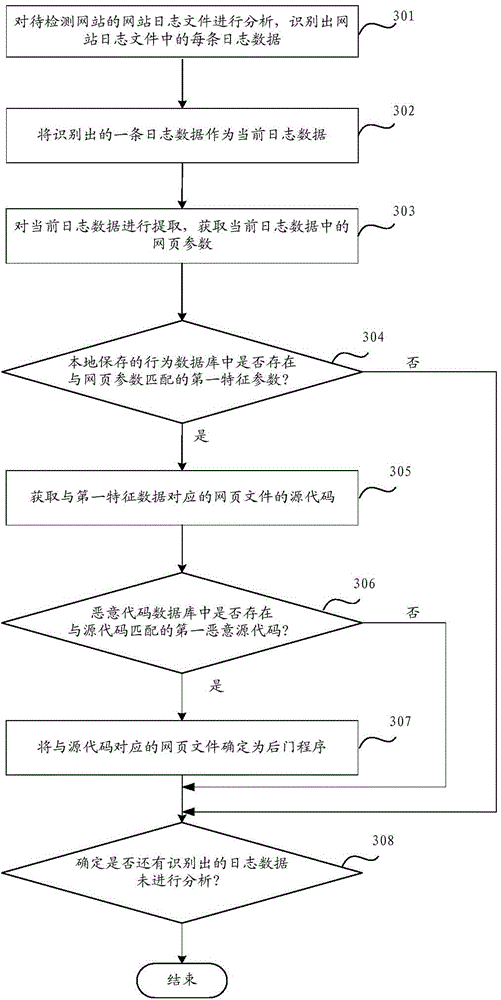
[0049] Embodiment 3: In this implementation, the log data of the website to be detected is analyzed to determine the backdoor program in the website to be detected. For the specific process, see image 3 ,include:
[0050] Step 301: Analyze the website log files of the website to be detected, and identify each piece of log data in the website log files.
[0051] For example: record the website log files of the website to be detected through the CDN, analyze the website log files, and identify each piece of log data in the website log files.
[0052] Step 302: Use the identified piece of log data as current log data.
[0053] The log data includes basic information such as host, time, IP address, URL, web page parameters, etc., preferably, cookie information may also be included.
[0054] A piece of log data among the identified log data can be used as the current log data according to the set rules, for example: in chronological order, or in the order of the set hosts, etc.
...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com