Data correlation method based on J2EE platform and correlation plug-in
A data association and plug-in technology, applied in electrical components, program control devices, transmission systems, etc., can solve problems such as unsafe events, difficult correlation of correlation models, and performance degradation of security audit products.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
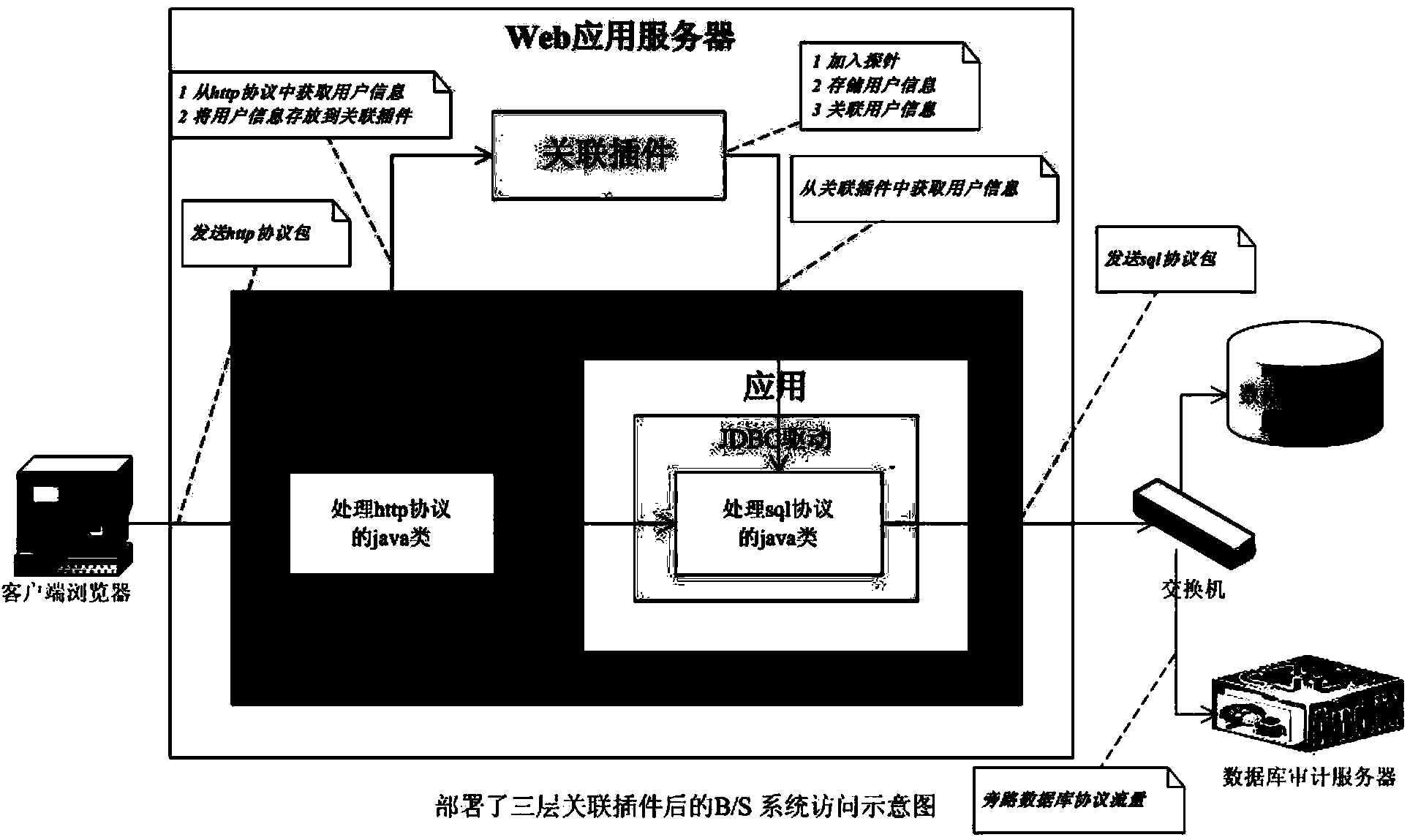
[0027] The applicant proposes that a plug-in can be deployed on the We application server. The plug-in adds a user information probe to the class that processes http requests, and adds a sql information probe to the class that processes sql statements. The user information probe will be responsible for obtaining user information and business information, the sql information probe is responsible for associating user information, business information and sql statements triggered by the business. The associated sql statement will carry user information and business information. The associated information will appear in the sql statement in the form of a comment in the form of a feature string. Deploy the database audit system to audit the database protocol traffic at the entrance switch of the database server, analyze the characteristic string in it to form a complete sql event associated with user information and business information, and record it in the database audit log. Af...
Embodiment 2
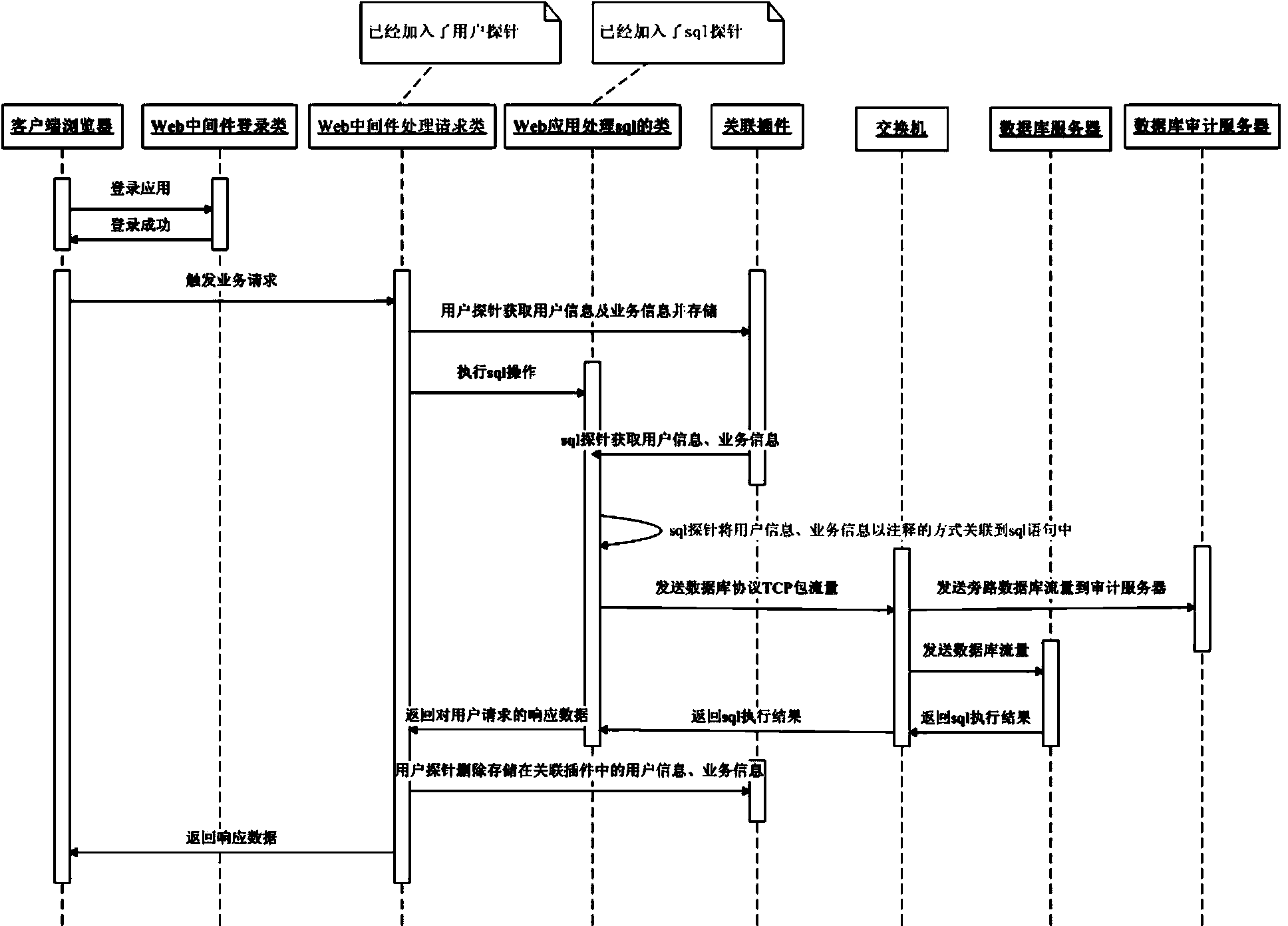
[0058] This embodiment provides a precise data association method based on the J2EE platform, which can be realized by the association plug-in in the first embodiment above. The method includes the following operations:
[0059] When the WEB application server receives a service request triggered by a logged-in user, the associated plug-in acquires and stores the associated information of the service request, which includes the user information and service information corresponding to the service request;
[0060] When the WEB application server requests data from the database according to the business request, the association plug-in associates the stored association information of the business request with the SQL statement in the form of comments, and then sends the SQL statement carrying the association information in the form of a database protocol packet to the switch.
[0061] In this way, the switch sends the database protocol packet to the database audit server for a...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com