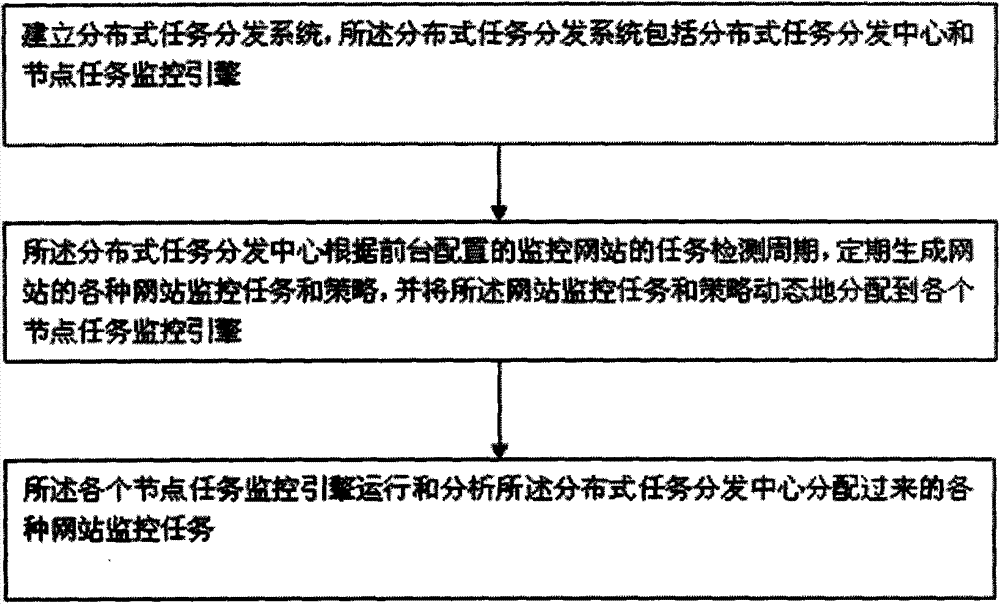
Website security monitoring method based on cloud architecture
A technology of security monitoring and cloud architecture, applied in the direction of data exchange network, digital transmission system, electrical components, etc., can solve the problems of insufficient protection, loss, high cost, etc., to reduce losses and risks, reduce false positives, improve The effect of security capabilities
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0084] The present invention will be described more fully hereinafter with reference to the accompanying drawings, in which exemplary embodiments of the invention are illustrated.
[0085] Cloud Computing is the development of Distributed Computing, Parallel Computing and Grid Computing. It is the automatic splitting of huge computing processing programs into countless smaller subroutines through the network. , and then handed over to a huge system composed of multiple servers for calculation and analysis, and then return the processing results to the user. Through cloud computing technology, network service providers can process tens of millions or even billions of information in a few seconds, and achieve network services as powerful as "supercomputers".
[0086] As an emerging computing model, cloud computing can deliver various IT resources and functions to users through the network in the form of services. These services include a wide variety of Internet applications, p...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com