Sensitive operation verification method, terminal equipment, server and verification system
A technology for verifying servers and sensitive operations, applied in the field of terminal equipment, sensitive operation verification methods, servers and verification systems, can solve problems such as increasing user learning costs and operating costs, and achieve the goal of improving security assurance, simplifying user operations, and simplifying processes. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
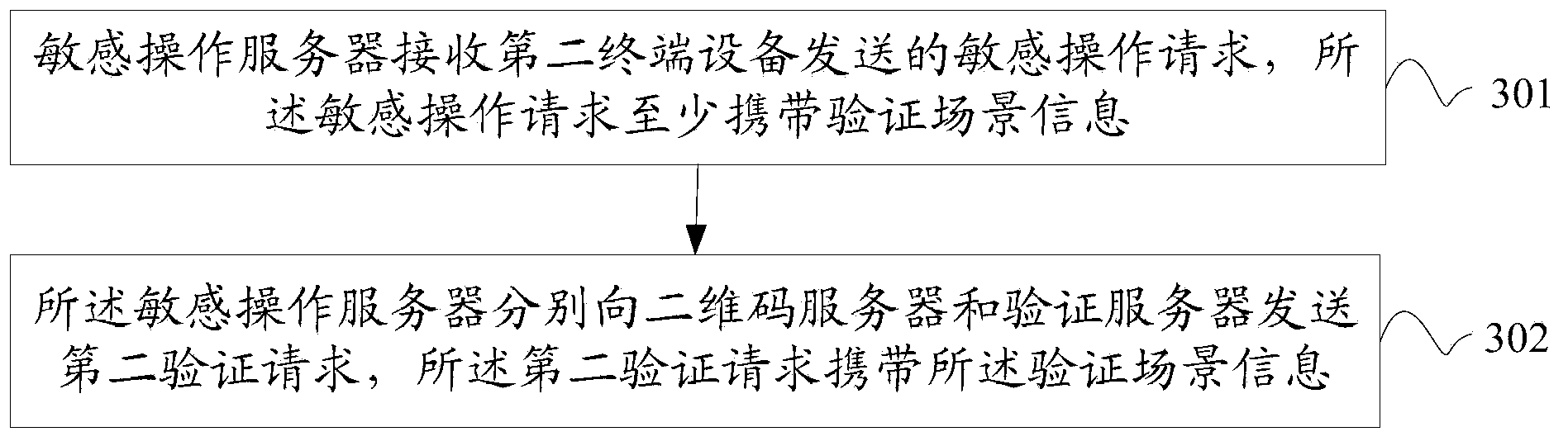
[0045] Flowchart of the Sensitive Operations Verification Methodology. The terminal device in this embodiment may be a fixed terminal or a mobile terminal. see figure 1 ,include:
[0046]101. The first terminal device scans a two-dimensional code used to initiate a sensitive operation, and acquires information in the two-dimensional code, where the information in the two-dimensional code is at least used to uniquely determine the sensitive operation;
[0047] 102. The first terminal device sends a first verification request to the verification server, and the first verification request carries the verification information of the first terminal device and the information in the two-dimensional code, so that the verification server according to the verification information of the first terminal device The verification information of the device is verified, and the verification information is used to determine the user identity information; when the verification is passed, the ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com