Intrusion detection method with matching algorithm automatically adjusted
A matching algorithm and automatic adjustment technology, applied in the field of network security, to achieve the effect of meeting real-time decoding requirements, accurate detection and defense, accurate identification and removal
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0055] The method of the present invention will be described in further detail below in conjunction with the accompanying drawings.
[0056] The intrusion detection method of automatic adjustment matching algorithm of the present invention, it comprises following concrete steps:
[0057] The first step is to capture the data packets in the network;
[0058] The second step is to perform full protocol stack analysis on the captured data packets;
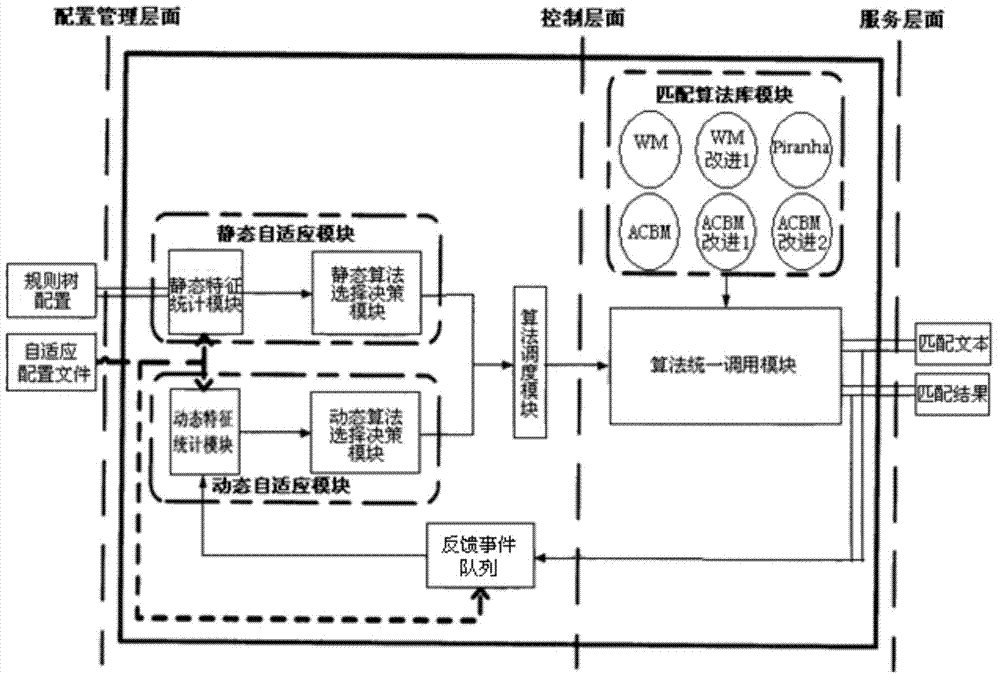
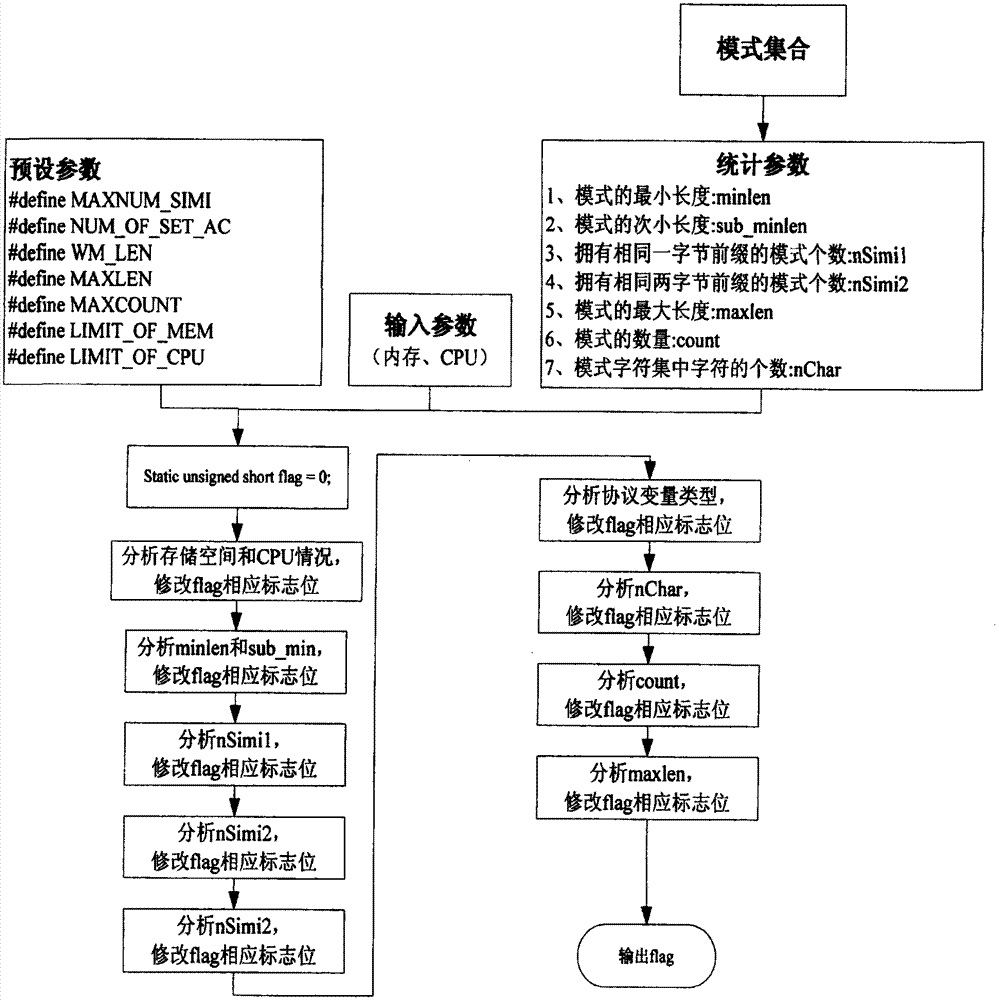
[0059] The third step is to select the most suitable multi-pattern matching algorithm according to the pre-set pattern characteristics and protocol variable characteristics, and then load the pattern matching algorithm library, and dynamically adjust the matching algorithm according to the current network status during the detection process.
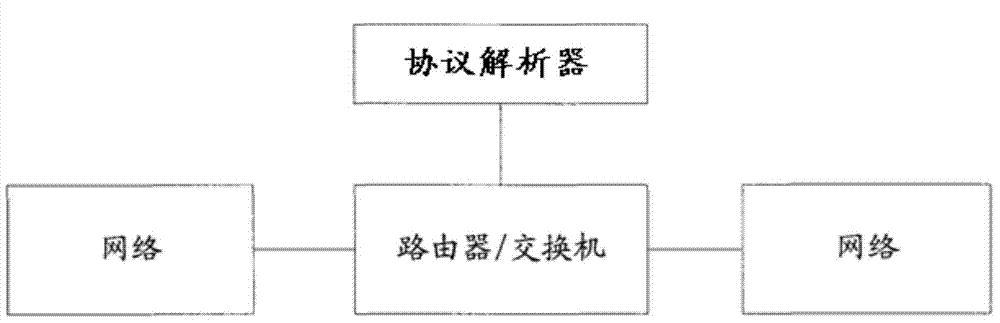
[0060] figure 1 is a schematic structural diagram of the flow-based protocol analysis system in this example, and the system includes routers and protocol analysis devices. Among them, the ro...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com