Method and system for intrusion detection
An intrusion detection and to-be-detected technology, applied in special data processing applications, instruments, electrical digital data processing, etc., can solve the problem of not being able to detect new behavior categories, and achieve the effect of reducing data redundancy and improving efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
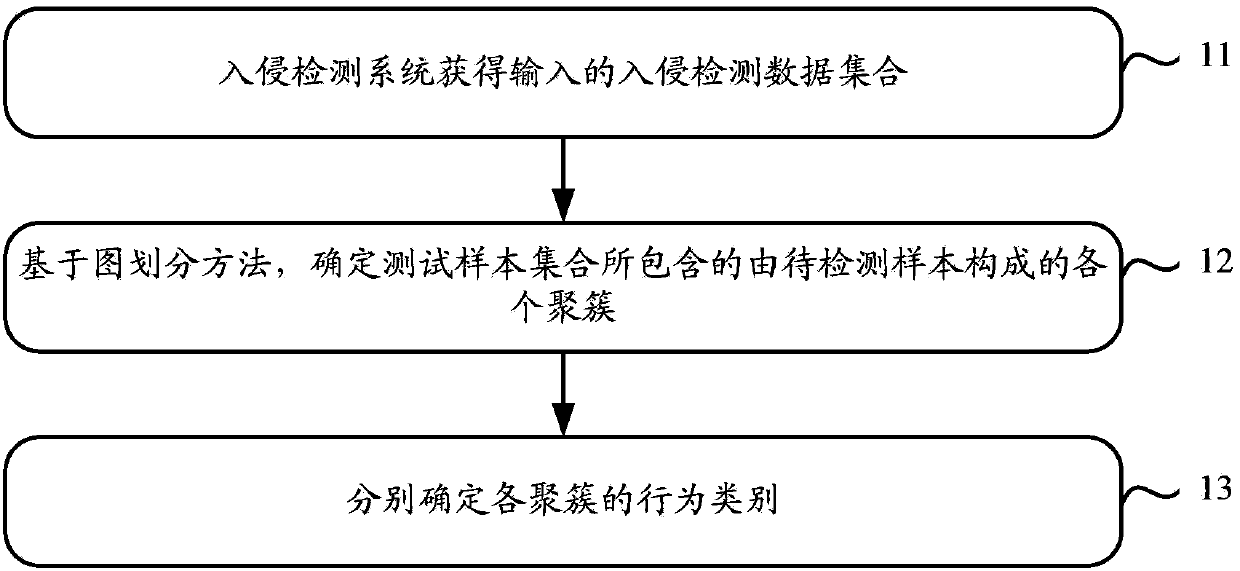
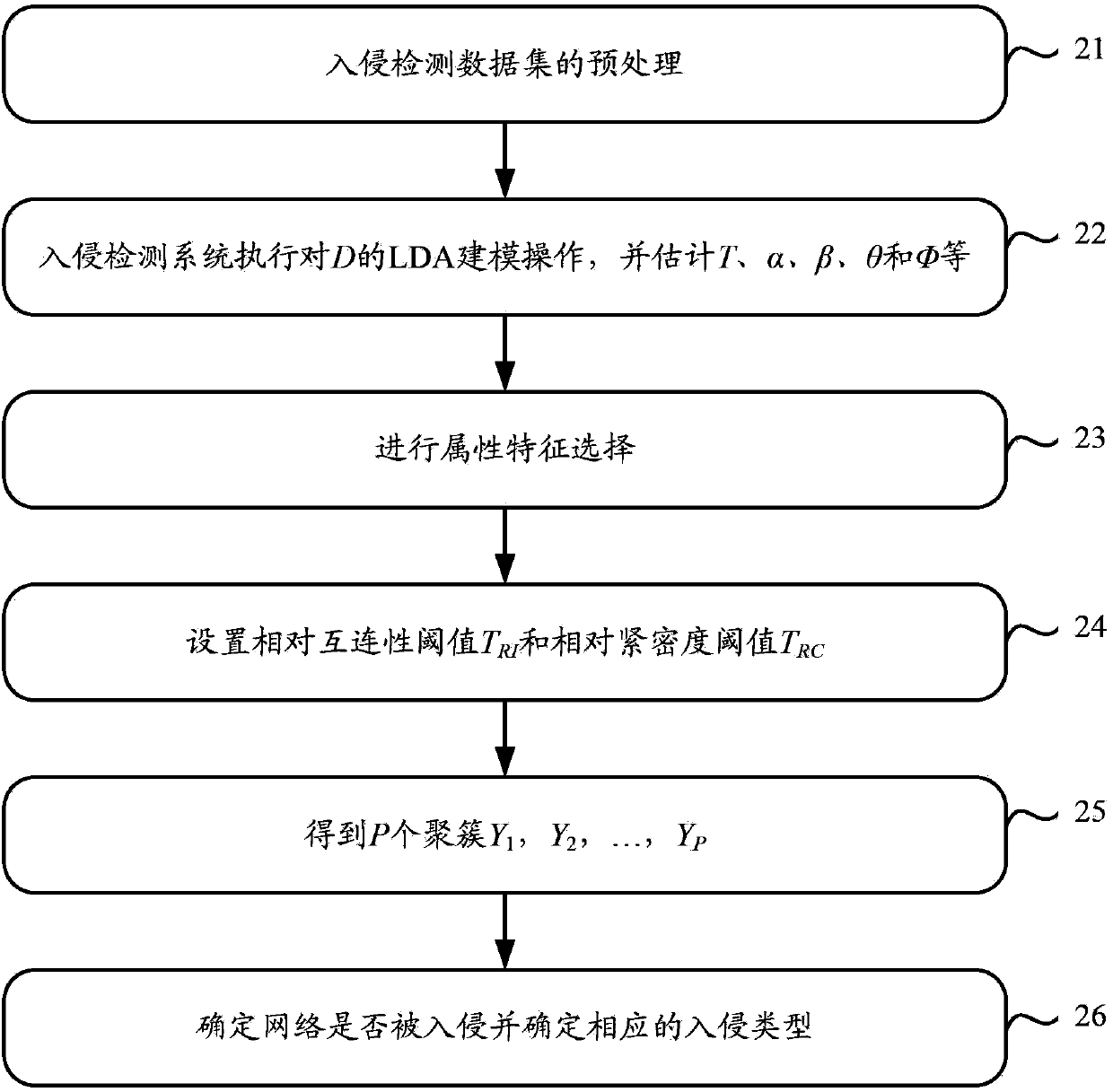
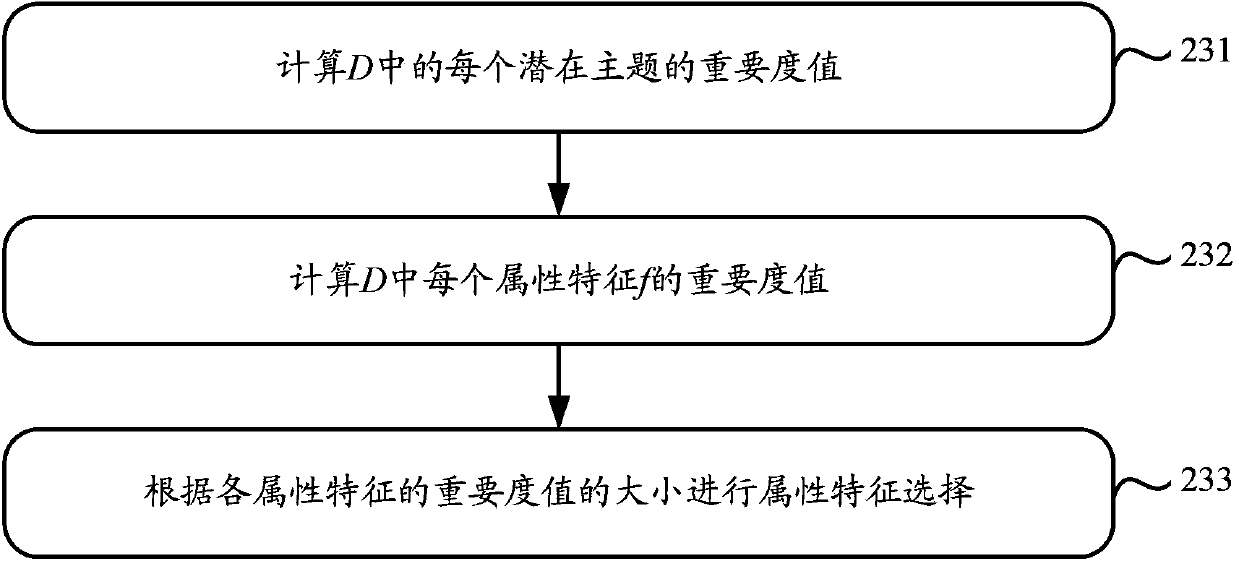
[0029] In order to solve the problem that the intrusion detection method adopted in the prior art cannot detect new behavior categories, the embodiment of the present invention provides a novel intrusion detection scheme. The scheme uses the graph partition method to perform cluster analysis on the test sample set, and then uses the training sample set to determine the behavior category of the clusters obtained by clustering the test sample set, thus realizing the behavior category of the test sample set. Sure. Since the determination process of the behavior category of the test sample set does not completely depend on the behavior categories of the training samples included in the training sample set as in the prior art, new behavior categories can be discovered by adopting the solutions provided by the embodiments of the present invention.
[0030] The solutions provided by the embodiments of the present invention will be described in detail below in conjunction with the acc...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com