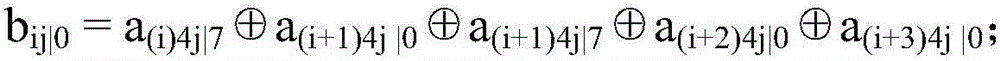A fast protection method against timing and cache side channel attacks in Klein encrypted AVR environment
A side-channel attack and environment technology, applied in the field of cryptographic algorithms, can solve the problems that there is no anti-timing or cache boundary channel attack implementation.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
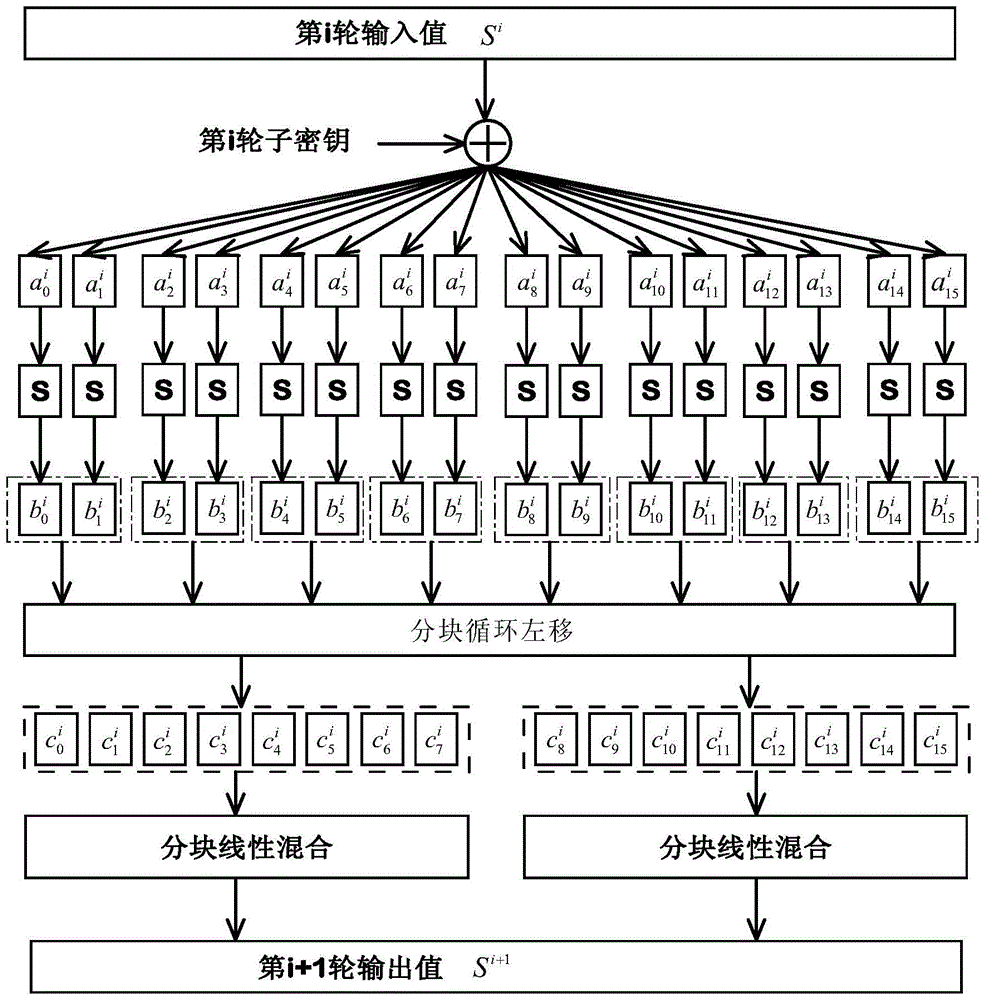
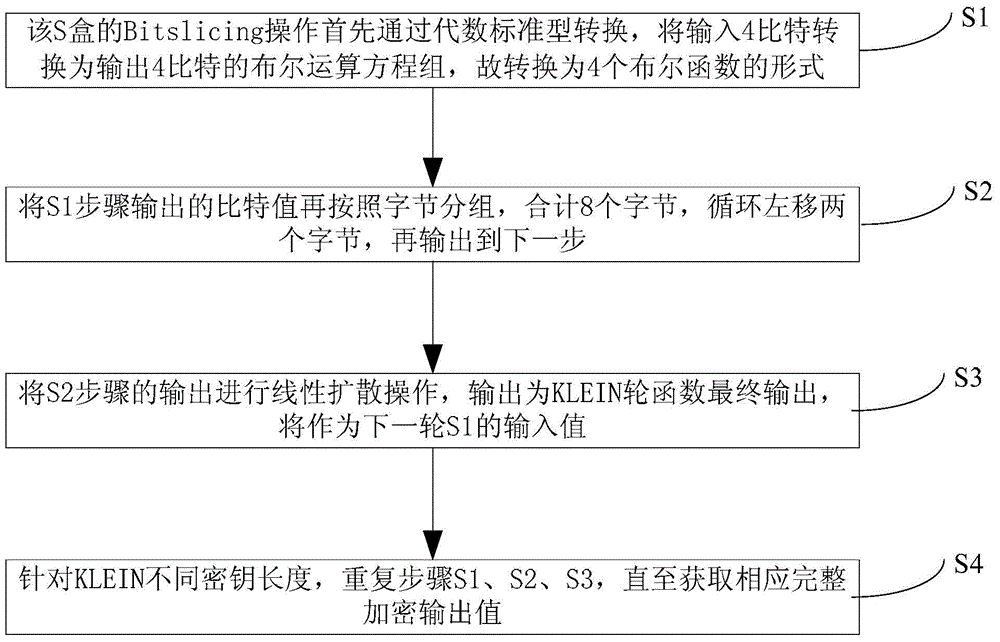
[0039]This embodiment starts from the characteristics of the AVR microprocessor, and based on the AVR ASM language, provides the Bitslicing implementation level and related optimization methods of the lightweight packet encryption algorithm KLEIN for Internet of Things applications. In the process of implementation, firstly, the optimized processing method under Bitslicing is given for the ANF expression of Sbox. Secondly, corresponding optimizations are carried out based on the reading and storage operations, which reduces the computational complexity of the algorithm in the MixNibbles step, so that the KLEIN algorithm can defend against border channel attacks such as timing and cache through Bitslicing. From the actual test results on the AVR platform, the optimized KLEIN algorithm Bitslicing is practicable under the AVR microprocessor platform. Such as figure 2 As shown, in this embodiment, the protection method against high-speed anti-timing and cache under the avr envir...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com