Encryption and decryption method of transmission data based on audio interface
An audio interface and data transmission technology, applied in the field of communication, can solve problems such as account security risks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
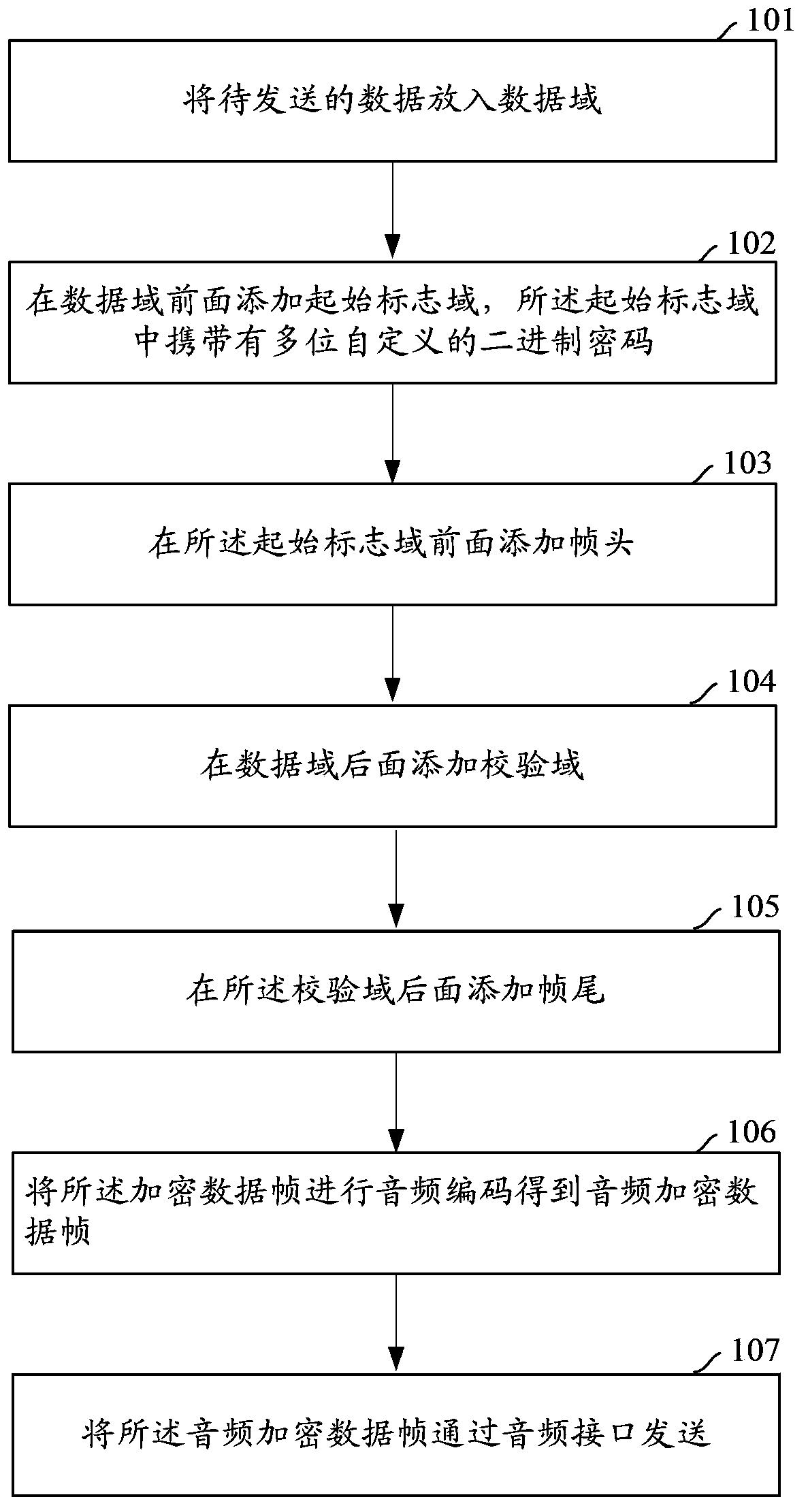
[0059] figure 1 Shown is a schematic flow chart of a method for encrypting data transmitted based on an audio interface in the present invention, including:
[0060] Step 101: Put the data to be sent into the data field.
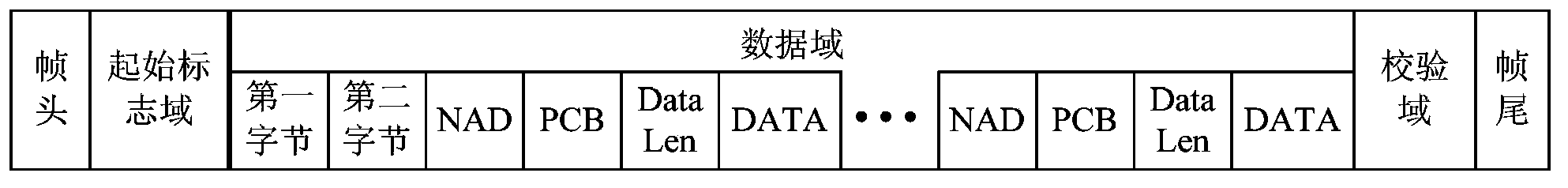
[0061] The data field specifically includes: the first byte, the second byte, and at least one data packet, and each data packet carries a node address (node address, NAD), a protocol control byte (protocol control byte, PCB), a data packet Length (Data Len) and a data (Data); wherein, the data length (Data Len) is used to identify the number of bytes occupied by the data (Data) in each data packet.
[0062] The first byte and the second byte carry a length identifier, and the length identifier is used to determine the length of bytes in the data field to be read during decryption.
[0063] Step 102: Add an initial flag field in front of the data field, and the initial flag field carries multiple self-defined binary passwords.
[0064] The start flag fi...
Embodiment 2
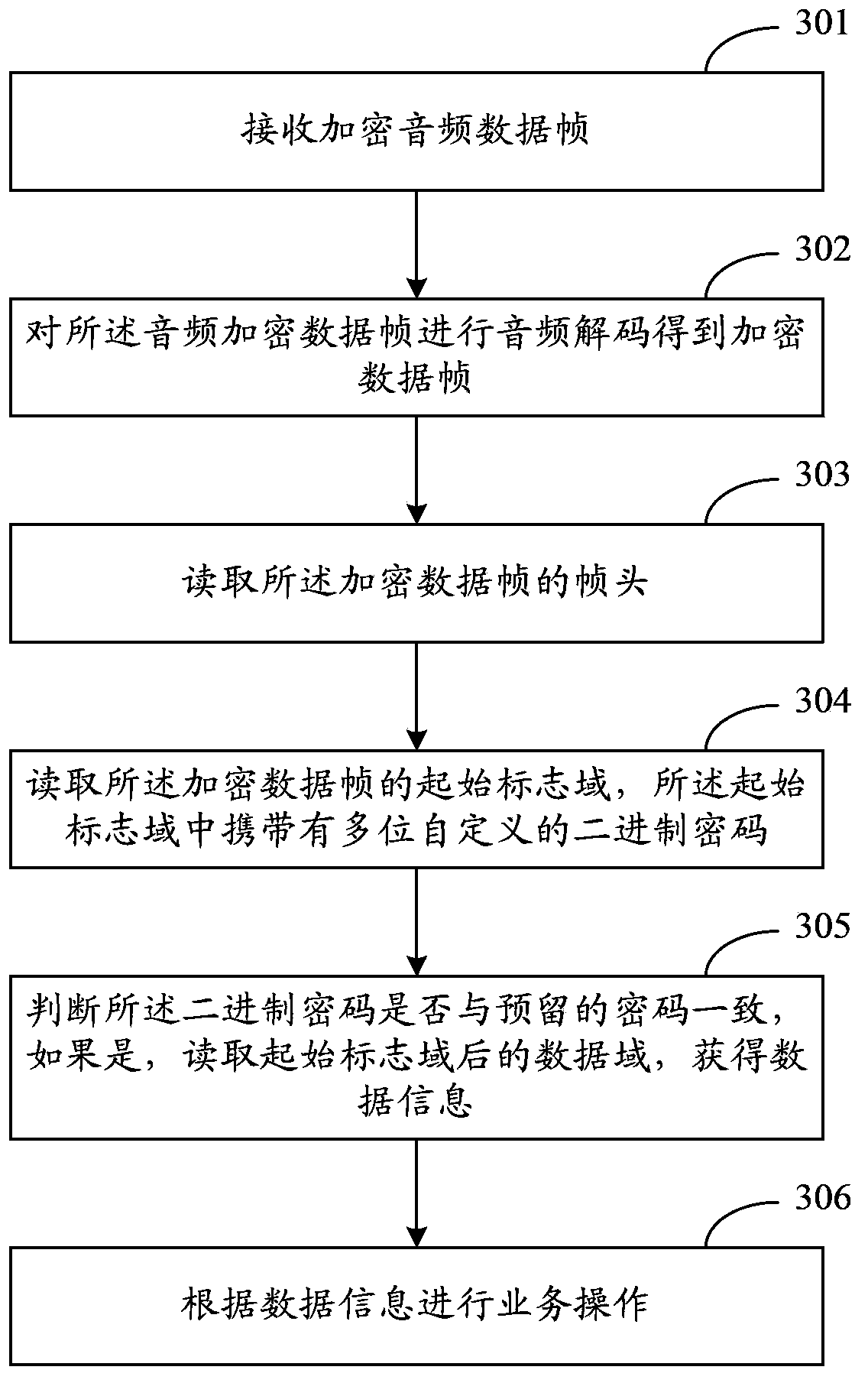
[0081] image 3 Shown is a schematic flow chart of a method for decrypting data transmitted based on an audio interface in the present invention, which is a decryption method corresponding to the encryption method in Embodiment 1, specifically including:
[0082] Step 301: Receive an encrypted audio data frame.
[0083] Step 302: Perform audio decoding on the audio encrypted data frame to obtain an encrypted data frame.
[0084] Decapsulating the encrypted data frame to obtain data information, specifically:
[0085] Step 303: Read the frame header of the encrypted data frame.
[0086] When reading the high level for more than 16 consecutive cycles, it is used as the frame header of an encrypted data frame.
[0087] Step 304: Read the start flag field of the encrypted data frame, and the start flag field carries multiple self-defined binary passwords.
[0088] Read the binary password carried in the start flag field.
[0089] Step 305: Judging whether the binary password ...
PUM
 Login to view more
Login to view more Abstract
Description
Claims
Application Information
 Login to view more
Login to view more - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap