Sensitive operation verification method, terminal device, servers and verification system
A technology for verifying servers and sensitive operations, which is applied in the fields of servers and verification systems, terminal equipment, and sensitive operation verification methods, and can solve problems such as increasing user learning costs and operating costs
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
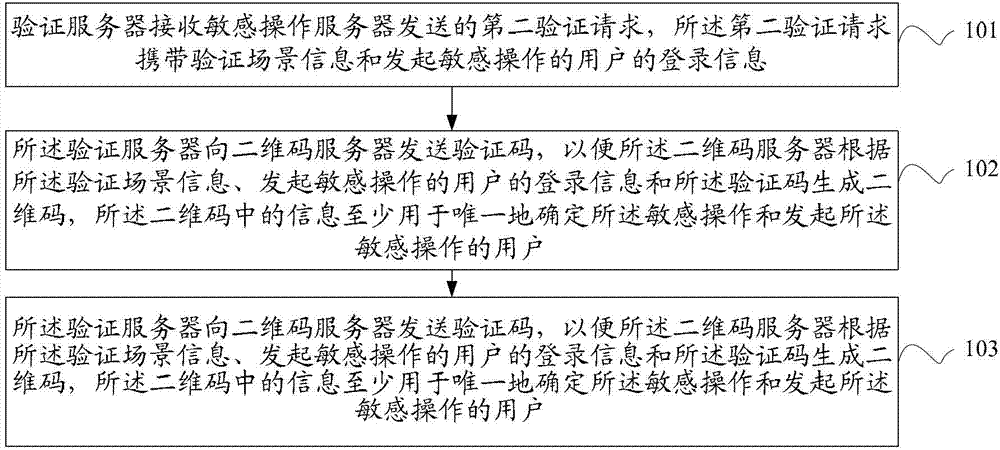
[0107] figure 1 It is a flowchart of a sensitive operation verification method provided by an embodiment of the present invention. see figure 1 , the example includes:
[0108] 101: The verification server receives a second verification request sent by the sensitive operation server, where the second verification request carries verification scene information and login information of the user who initiates the sensitive operation;
[0109] 102: The verification server sends a verification code to the two-dimensional code server, so that the two-dimensional code server generates a two-dimensional code according to the verification scene information, the login information of the user who initiates the sensitive operation, and the verification code, and the two-dimensional code The information in the QR code is at least used to uniquely identify the sensitive operation and the user who initiated the sensitive operation;
[0110] 103: When the verification server receives a fir...
Embodiment 2
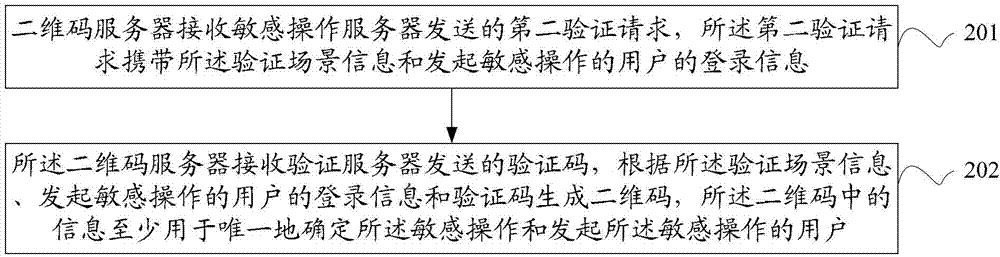
[0121] figure 2 It is a flowchart of a sensitive operation verification method provided by an embodiment of the present invention. see figure 2 , the example includes:
[0122] 201: The two-dimensional code server receives a second verification request sent by the sensitive operation server, where the second verification request carries the verification scene information and the login information of the user who initiates the sensitive operation;
[0123] 202: The two-dimensional code server receives the verification code sent by the verification server, and generates a two-dimensional code according to the verification scene information, the login information of the user who initiates the sensitive operation, and the verification code, and the information in the two-dimensional code is at least used for Uniquely determine the sensitive operation and the user who initiated the sensitive operation.
[0124] Optionally, the login information is account information, or the l...
Embodiment 3
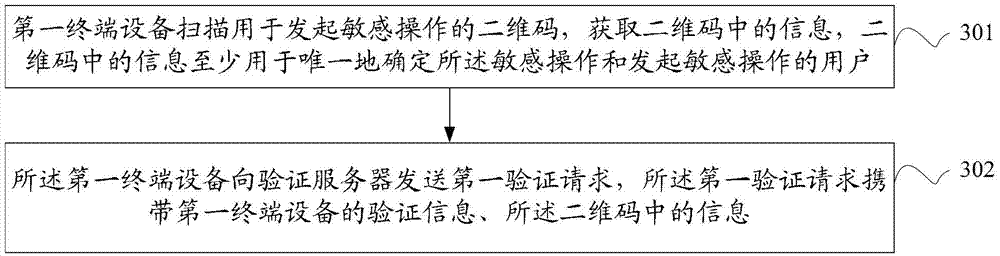
[0128] image 3 It is a flowchart of a sensitive operation verification method provided by an embodiment of the present invention. see image 3 , the example includes:
[0129] 301: The first terminal device scans a two-dimensional code used to initiate a sensitive operation, and obtains information in the two-dimensional code, where the information in the two-dimensional code is at least used to uniquely determine the sensitive operation and initiate the sensitive operation. operating user;
[0130] 302: The first terminal device sends a first verification request to the verification server, and the first verification request carries verification information of the first terminal device and information in the two-dimensional code, so that the verification server uses the verification information of the first terminal device The verification information of the device and the information in the two-dimensional code are verified, and the verification information is used to de...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com