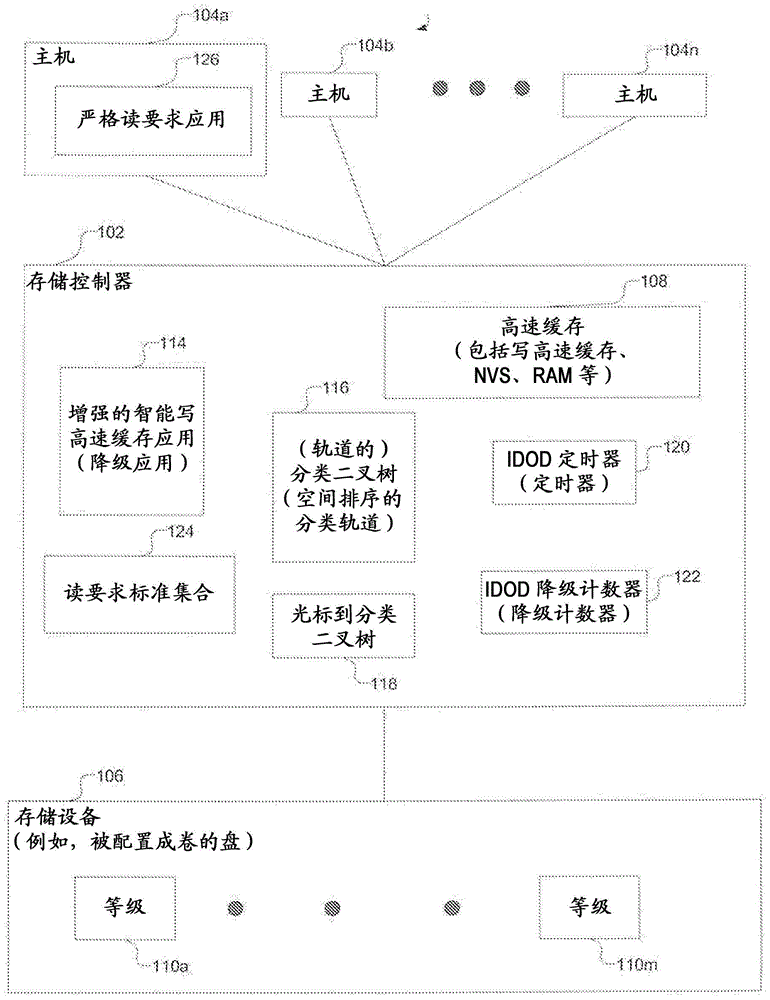
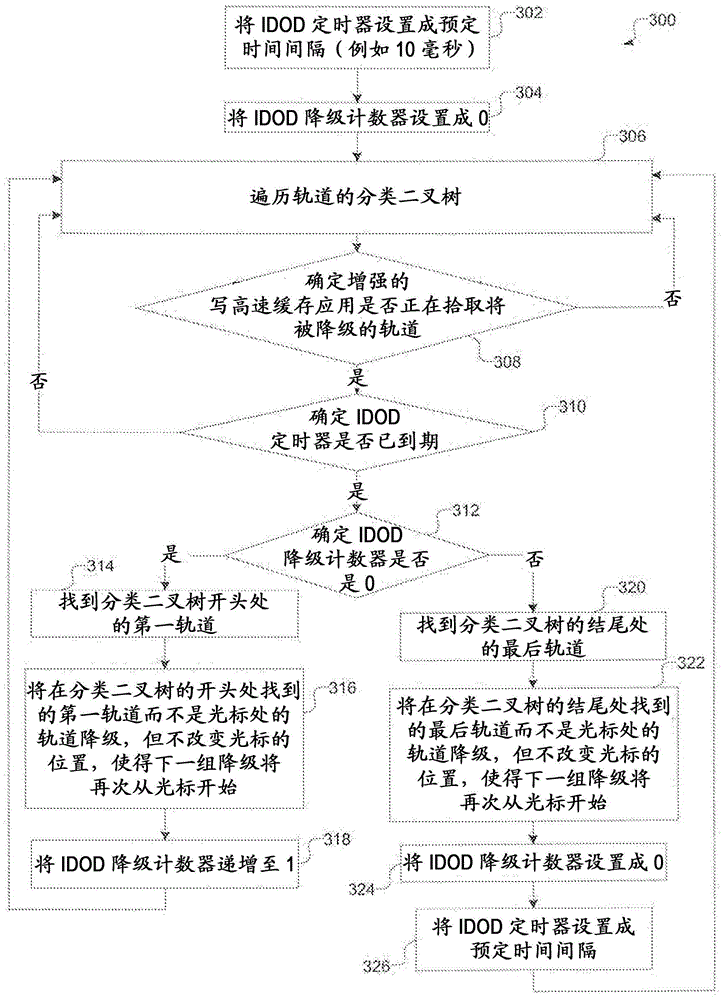
Periodically degrades the inner and outer diameters from the disk to improve read response time
A response time, periodic technology, applied in the field of periodic degradation of the inner and outer diameters of the slave disk to improve the read response time, which can solve the problems of affecting the response time, low average NVS cache size, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0019] In the following specification, reference is made to the accompanying drawings which constitute a part of this specification and which illustrate various embodiments. It is understood that other embodiments may be utilized and structural and operational changes may be made.
[0020] Degradation and read response time requirements based on spatial locality
[0021] Intelligent Cache Write (IWC) is a hybrid of two other cache management mechanisms called CLOCK and CSCAN. CLOCK is a least recently used (LRU) based mechanism that demotes tracks based on which tracks are LRU or least recently used. In order to emulate the CLOCK properties, the IWC maintains a time bit for each track. This time bit is set when the host writes to the track. Time bits are reset when a downsweep encounters a track with a time bit set. If the downscan finds a stride of the track that does not have a time bit set, the downscan can select that stride for downscaling. CSCAN downgrades orbits ba...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com