Alignment password system, direct communication method and indirect communication method
A cryptographic system and cryptographic technology, applied in the cryptographic field, can solve problems such as incompatibility, insensitive insertion and modification of serial ciphers, and unfavorable parallel computing.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
example 1
[0044] Example 1, the pairwise cipher system A has the same double (A I and AII); C=70, that is, there are 70 cipher tables in A; taking A5 (c=5, No. 5 cipher tables) as example.
[0045] Password Form No. 5 (A5):
[0046]
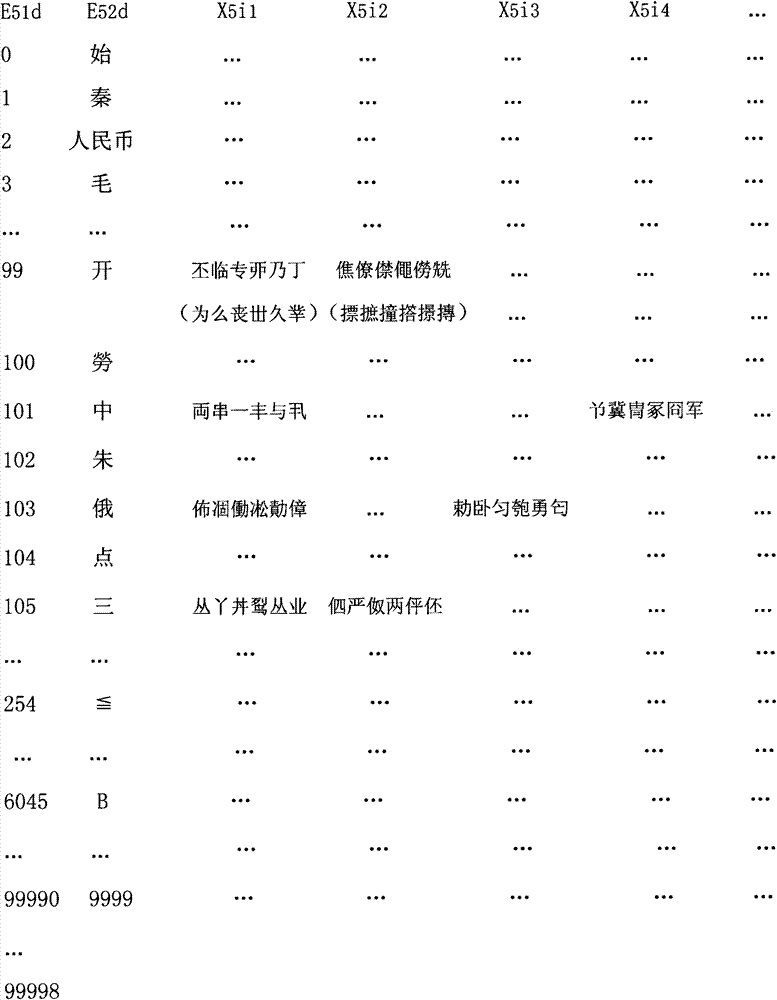
[0047] In the No. 5 password table, horizontal columns are columns and vertical columns are rows; there are a total of 2 columns and 99999 rows of starting characters, the first column is a sequence of numbers (intervals of 1, E51d, a total of 99999 rows), and the second column is comprehensive characters (E52d, 99991 rows); 99991 rows and 240 special password characters are arranged in total, and each group of special password characters wherein is 6 Chinese characters; Bc=B5=2, Dc=D5=99999, Ecbd is E5bd, Ic=I5 =99991, Hc=H5=240, Xcih is X5ih.
[0048] E51d is: 0, 1, 2, 3, ..., 99(d=100), 100(d=101), 101(d=102), 102(d=103), 103(d=104), 104(d=105), 105(d=106),..., 254(d=255),..., 6045,..., 99990(d=99991),..., 99998(d= 99999); for example, the startin...
example 2
[0088] Example 2, the pairwise cryptosystem A has identical, synchronous double (A I and AII); C=240, promptly there are 240 cipher tables in A; Take A1 (c=1, No. 1 cipher table) as example .
[0089] Password Form No. 1 (A1):
[0090]
[0091] In the No. 1 password table, vertical columns are columns and horizontal rows are rows; a total of 1 column and 99999 rows of starting characters (digital sequences, with 1 intervals, represented by E11d); the starting characters have representative characters (use E' 11d represents); There are 99999 rows in total, 1 column dedicated password characters (represented by X1i1, h=1); Among A1, Bc=B1=1, Dc=D1=99999, Ic=I1=99999, Hc=H1=1 .
[0092] From right to left, the E11d is: 0(d=1), 1(d=2), 2(d=3), 3(d=4), 4(d=5), ..., 99998(d =99999, not shown in the No. 1 password table), that is, the 1st row initial character E111=0 (c=1, b=1, d=1) in the 1st column initial character, the 2nd row The starting character E112=1, the starting ch...
example 3
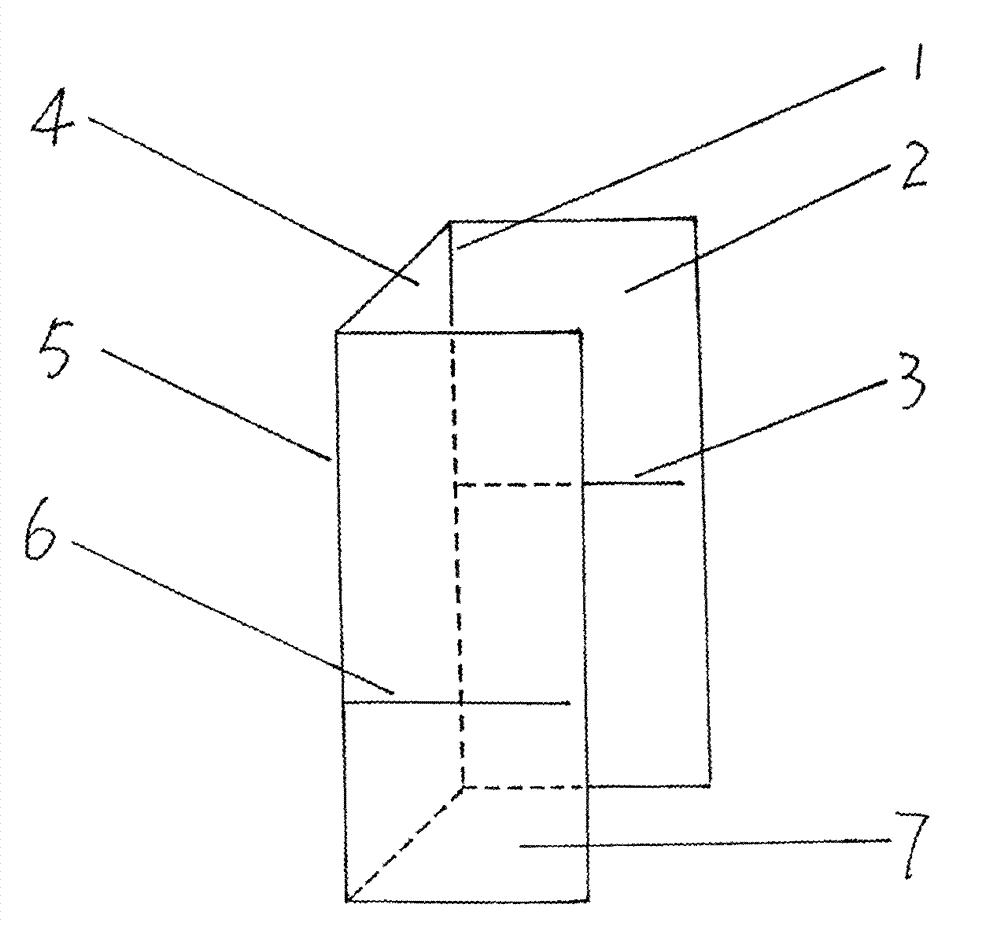
[0116] Example 3, the three-dimensional parametric cipher table (A'5, such as figure 1 ), A'5 has two parts, the first part comes from the No. 5 password table (A5) in example 1, and the second part is the imitated z1 plane.
[0117] With the 2nd column starting character (comprehensive character, b=2 in Ecbd, i.e. E52d) in the No. 5 password table in example 1 as dividing line, vertically, A5 is divided into two parts, the left side The part is named as XY plane, and the part on the right side is named as z2 plane (2 in z2 comes from b in zb, b=2, and zb comes from claim 5); again with E52d as the longitudinal axis, the XY plane Rotate 90 clockwise. And form the first part of A'5 (made up of XY plane and z2 plane); On the plane (then Ecbd becomes Ecbxydxy), the special-purpose password character Xcih among the A5 is on the z2 plane (then Xcih becomes Xciz2hz2); Equivalent, the original 99991 row special-purpose password characters among the A5 are 99991 Z axes (each row is ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com