Method and device for eliminating sensitive data of Linux system memory
A technology of sensitive data and system memory, applied in the direction of program control device, program loading/starting, etc., can solve the problems of inability to completely clear sensitive data, low efficiency, etc., and achieve the effect of low power consumption and strong compatibility
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0042] Embodiment 1. A method for clearing sensitive data in Linux system memory, including:
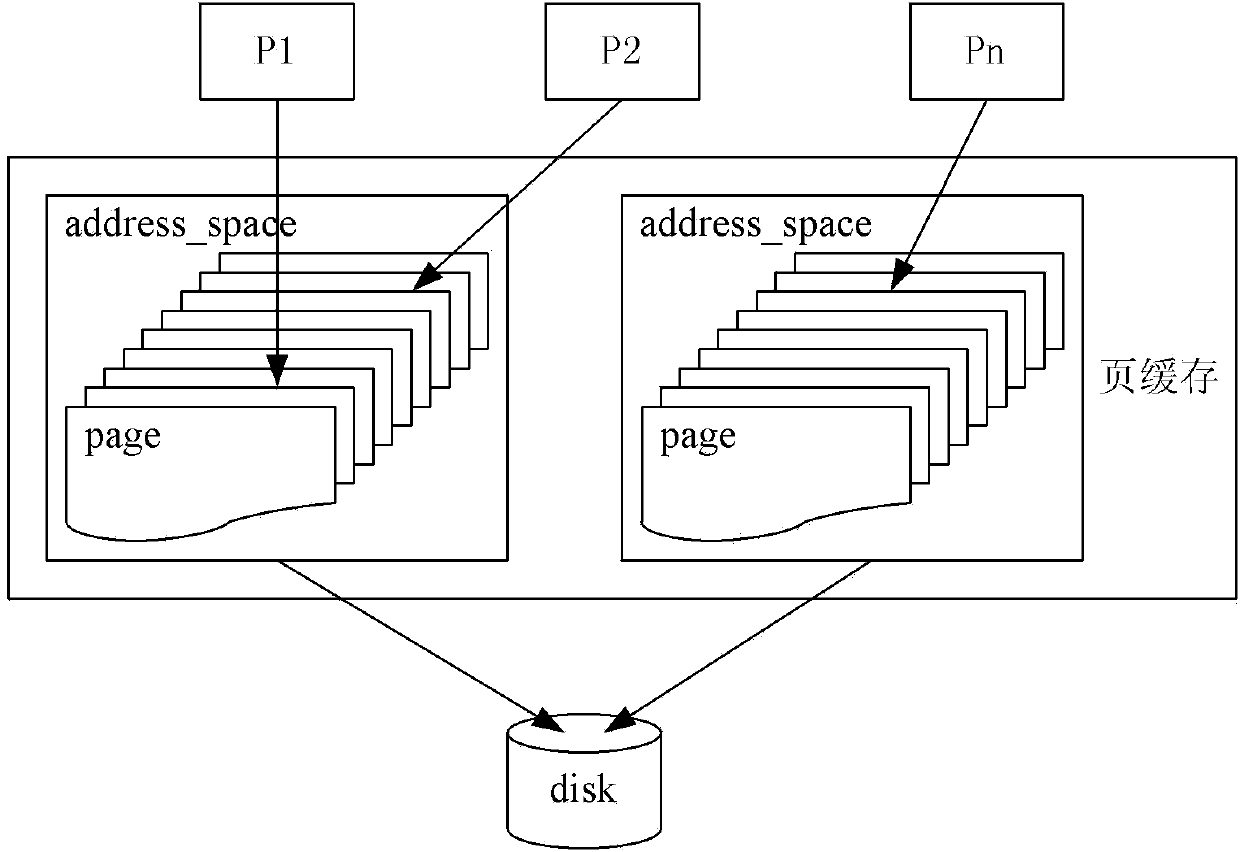
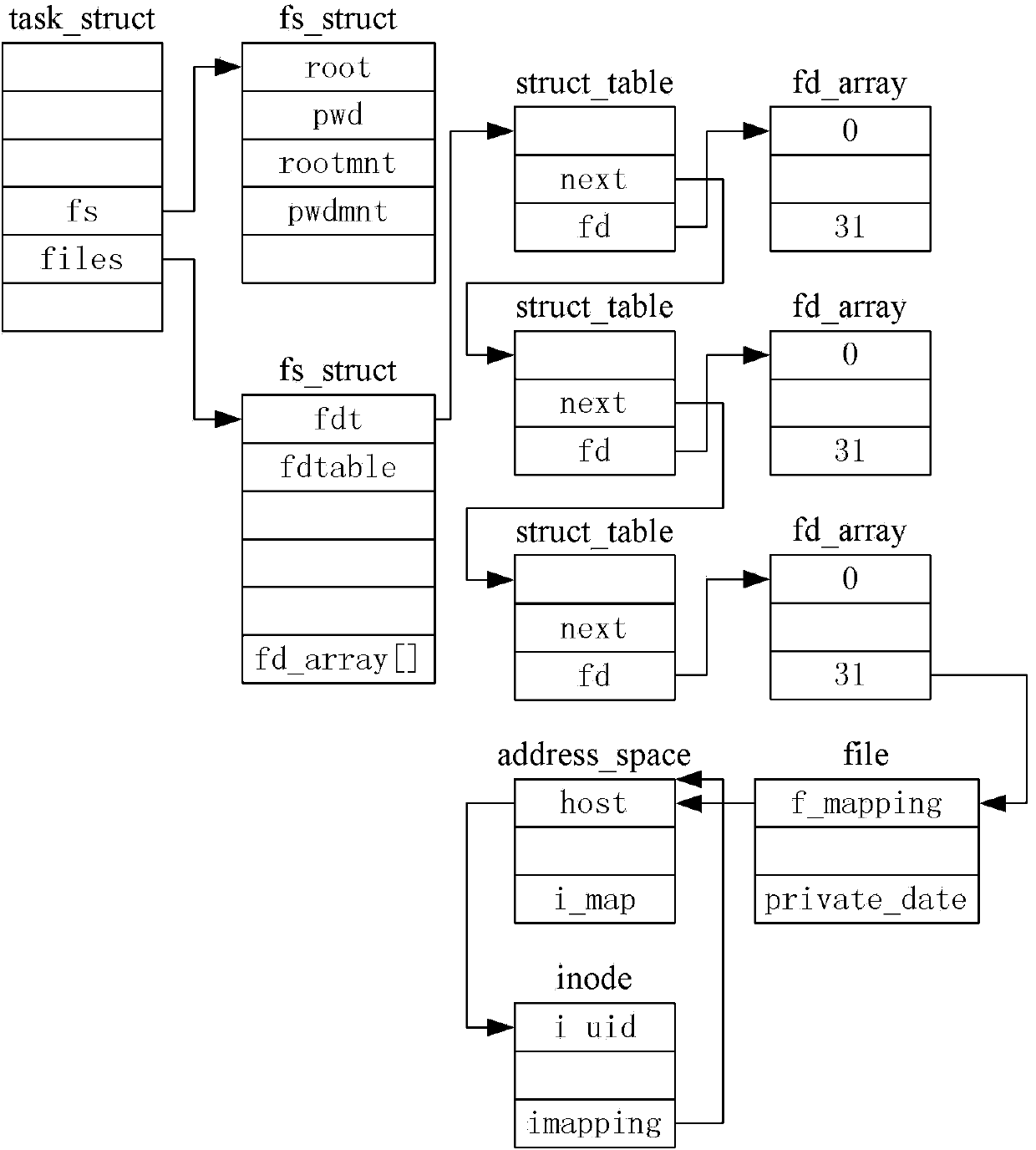
[0043] 101. When the process calls the close system call to close the file, or when the process exits and calls exit_files to close the unclosed file, locate the corresponding address space structure struct address_space through the file structure struct file, and determine the inode corresponding to the file to be closed Whether the structure has dirty pages, if so, call the vfs_fsync function to only write back the dirty pages in the file to the disk; traverse the radix tree in the address space structure that is located, and delete all pages in the radix tree. Release to free area after zero;
[0044] 102. Construct a read-write linked list in each process to record the starting address address and data length length in the device cache when reading or writing data to the device file; when the read system call or the write system call exits, pass through the To read and write the link...
Embodiment 2
[0132] Embodiment 2. A device 90 for clearing sensitive data in Linux system memory, such as Picture 9 Shown, including:
[0133] The file data clearing module 901 is used to locate the corresponding address space structure struct address_space through the file structure struct file when the process calls the close system call to close the file, or when the process exits and calls exit_files to close the unclosed file, to determine what is needed Whether the inode structure corresponding to the closed file has dirty pages, if so, call the vfs_fsync function to only write back the dirty pages in the file to the disk; traverse the radix tree in the address space structure that is located, and change the radix tree All pages are deleted and cleared and released to the free area;
[0134] The device data clearing module 902 is used to construct a read-write linked list in each process to record the starting address address and data length length in the device cache when reading or wr...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com