Android malware detection method based on program flow chart
A technology of program flow and detection method, applied in the fields of instruments, digital data processing, platform integrity maintenance, etc., can solve the problems of difficult to prevent malware variants, and the difficulty of file signature-based solutions to take effect, so as to reduce the size Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0019] Below in conjunction with specific embodiment, further illustrate the present invention, should be understood that these embodiments are only used to illustrate the present invention and are not intended to limit the scope of the present invention, after having read the present invention, those skilled in the art will understand various equivalent forms of the present invention All modifications fall within the scope defined by the appended claims of the present application.
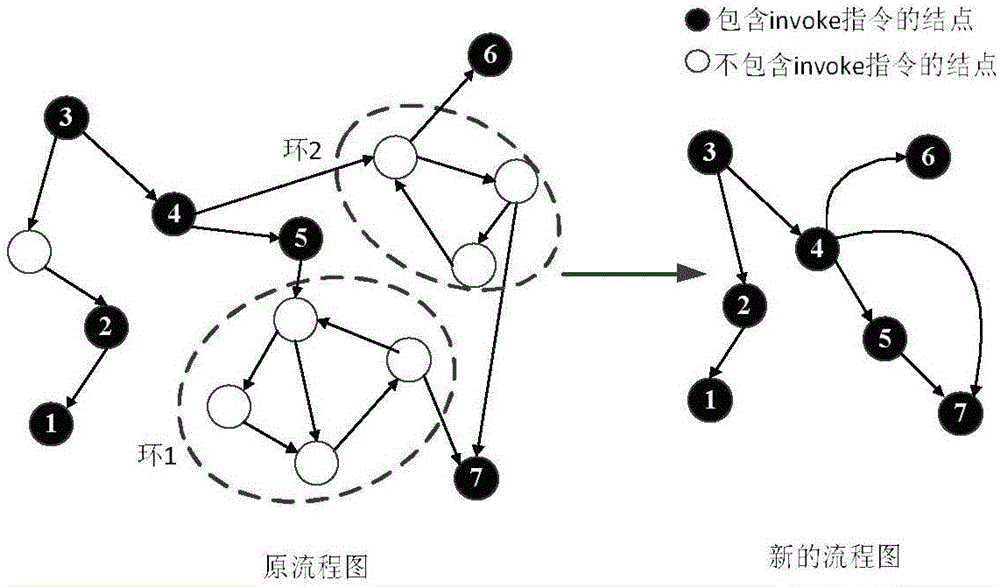
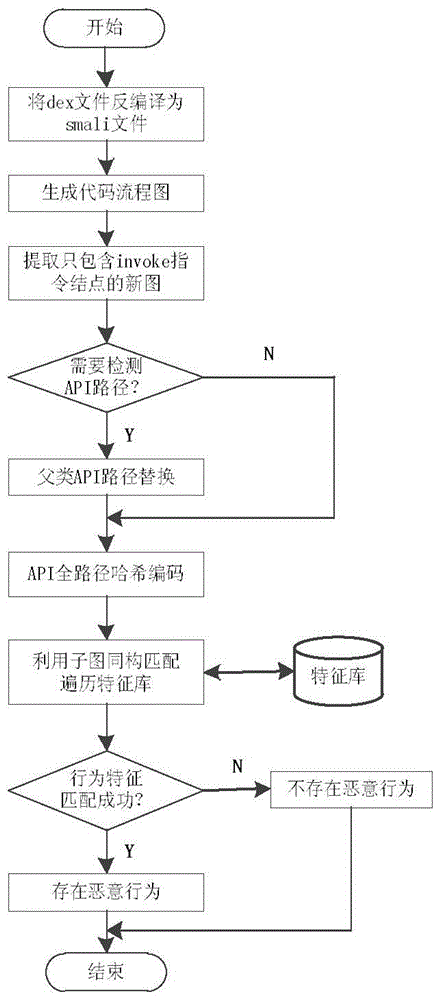
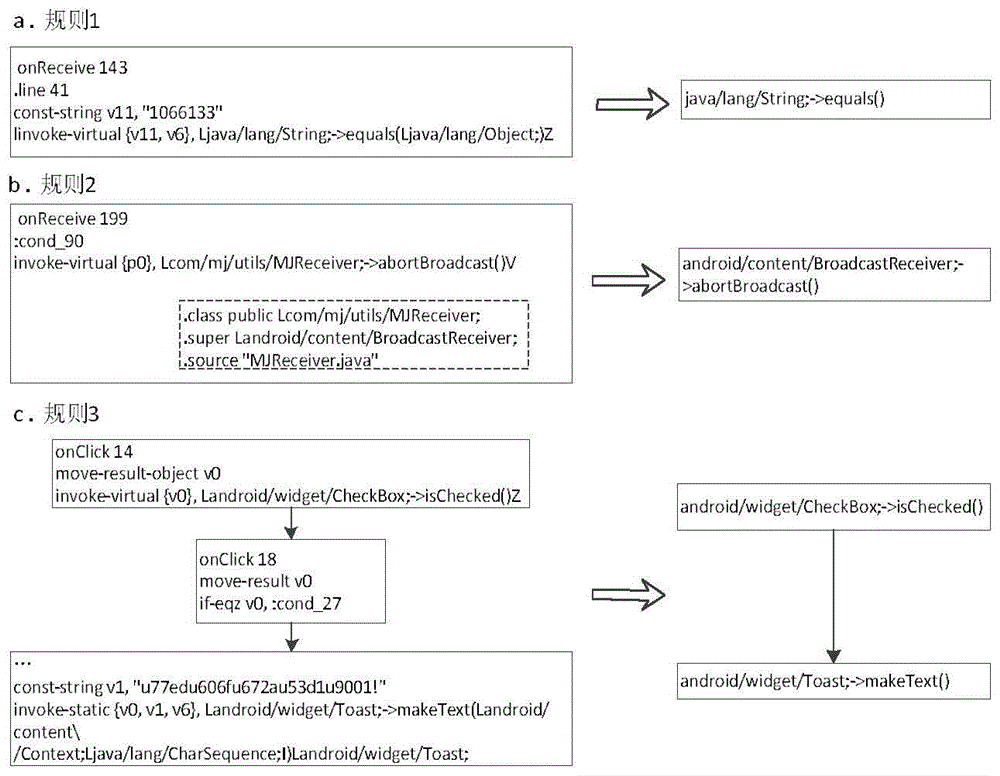
[0020] A kind of Android malicious software detection method based on program flow chart, its specific implementation flow chart is as follows figure 1 shown. Introduce the implementation steps of the present invention below in conjunction with zsone malicious software:
[0021] 1) Establishment of Malicious Behavior Feature Database
[0022] Step 1, extract the dex code file of the APK (SHA1:9458cfb51c90130938abcef7173c3f6d44a02720) application program;
[0023] Step 2. For the dex file extrac...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com