Sensitive data secure exchange method and system
A technology for sensitive data and secure exchange, applied in key distribution, it can solve the problems of difficult key transfer, decreased key security, and key leakage risk, and achieves the effect of simple operation, fast process, and high security.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
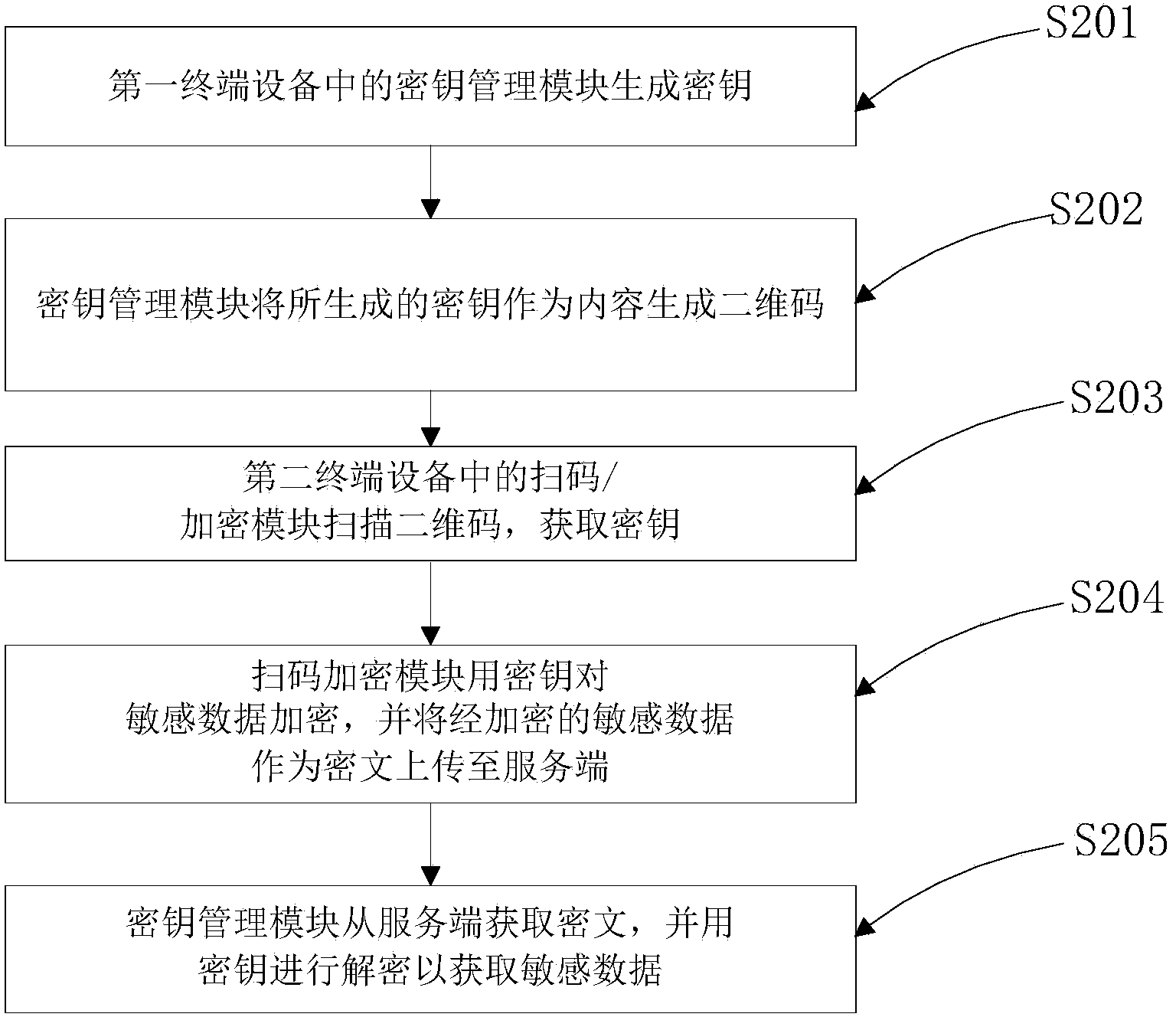
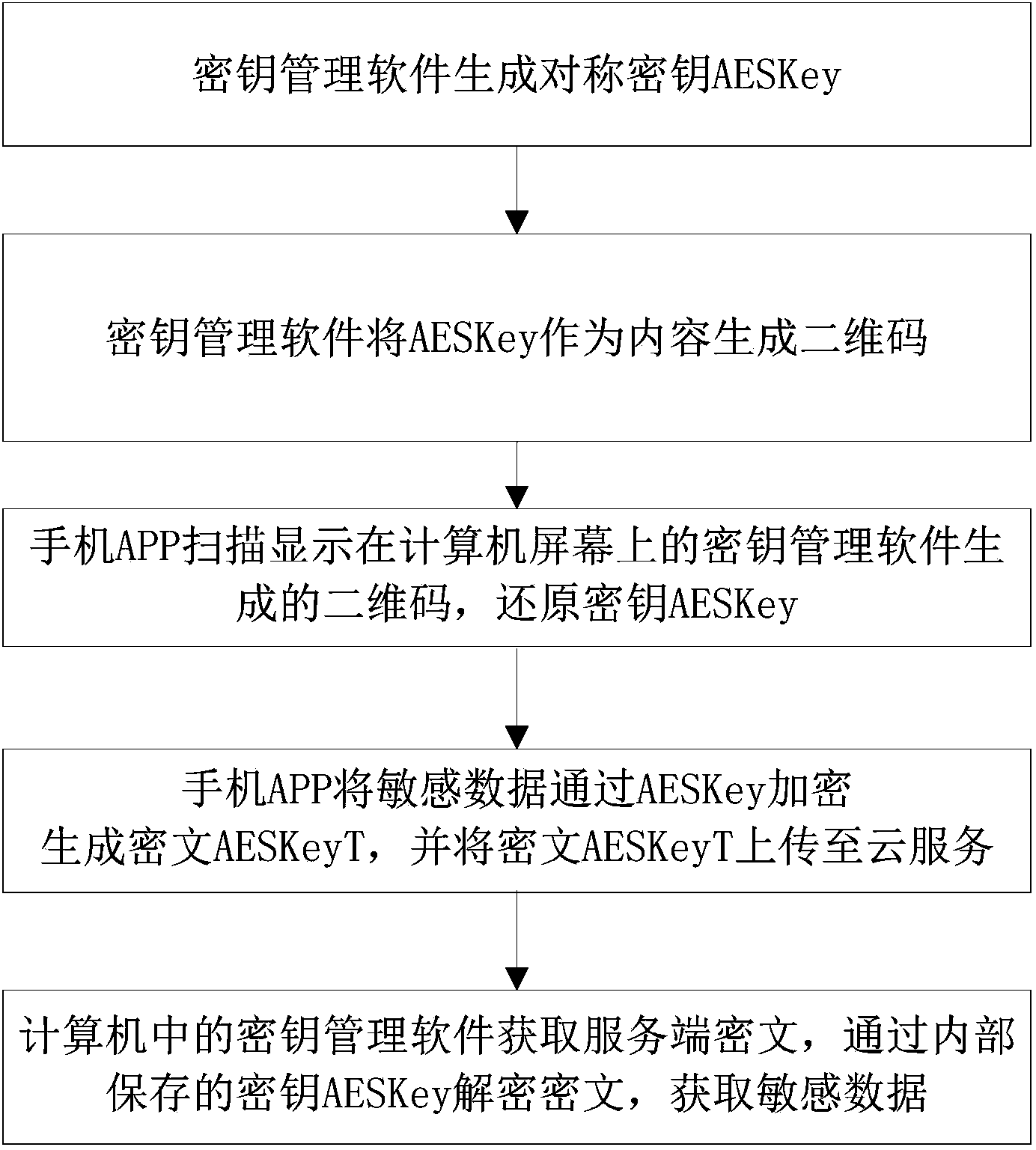
[0034] The method and system for securely exchanging sensitive data according to the embodiments of the present invention will be further described in detail below in conjunction with the accompanying drawings and specific embodiments, but this is not intended to limit the present invention.
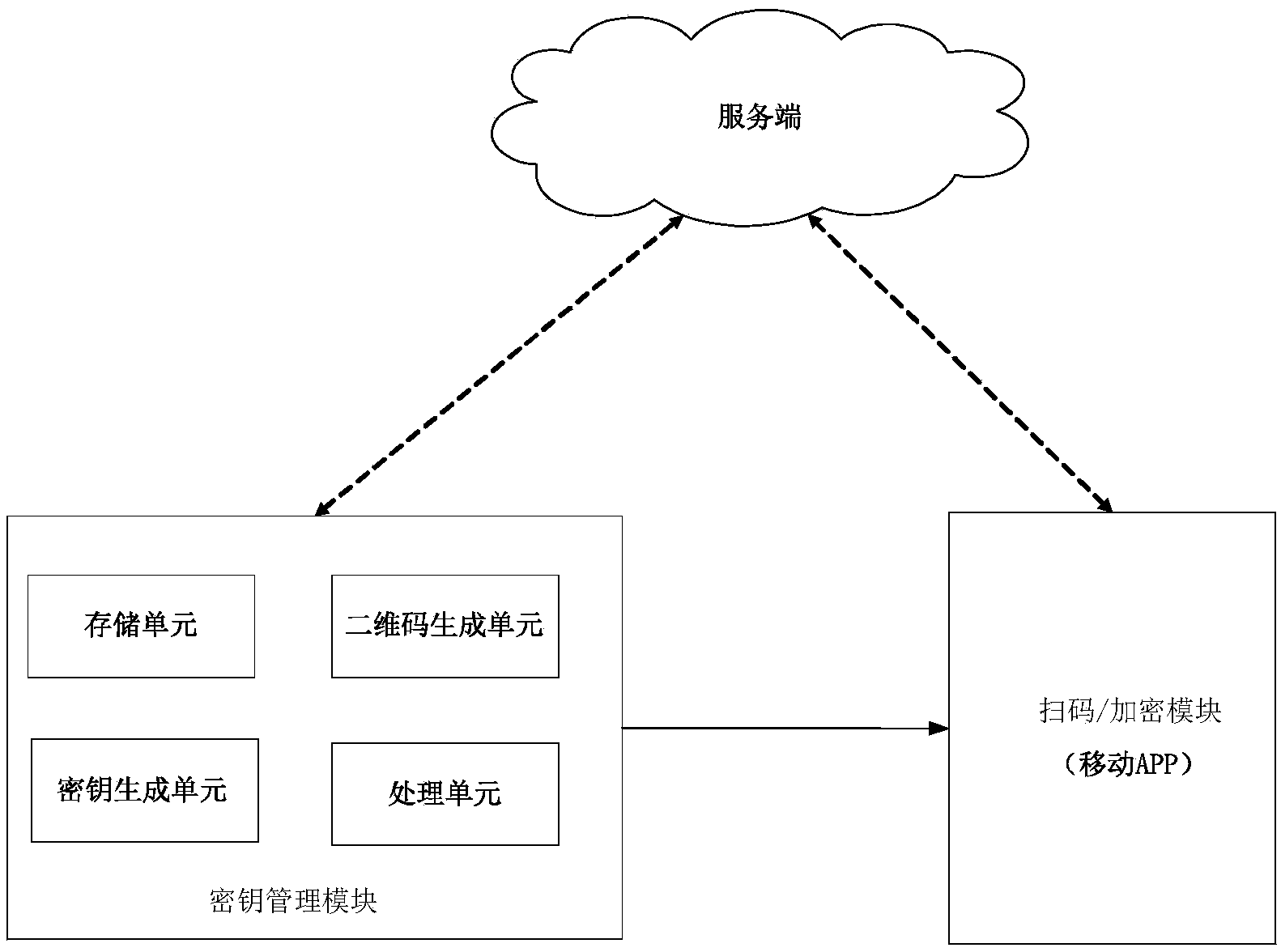
[0035] Before describing the embodiments of the present invention in detail, some technologies related to two-dimensional codes are firstly introduced. Two-dimensional bar code (two-dimensional bar code, two-dimensional bar code) is to use certain specific geometric figures on a two-dimensional plane (commonly black and white figures) to record text, pictures, URLs, etc. Barcode image of the information. Two-dimensional codes have the characteristics of large information capacity, wide coding range, strong fault tolerance, encryption measures can be introduced, good confidentiality, low cost, easy production, and durability. Therefore, two-dimensional codes are used more and more frequen...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com