Dynamic selection of security protocol
A security protocol and protocol technology, applied in the transmission system, electrical components, etc., can solve problems such as waiting time penalty, handshake failure, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0013] review
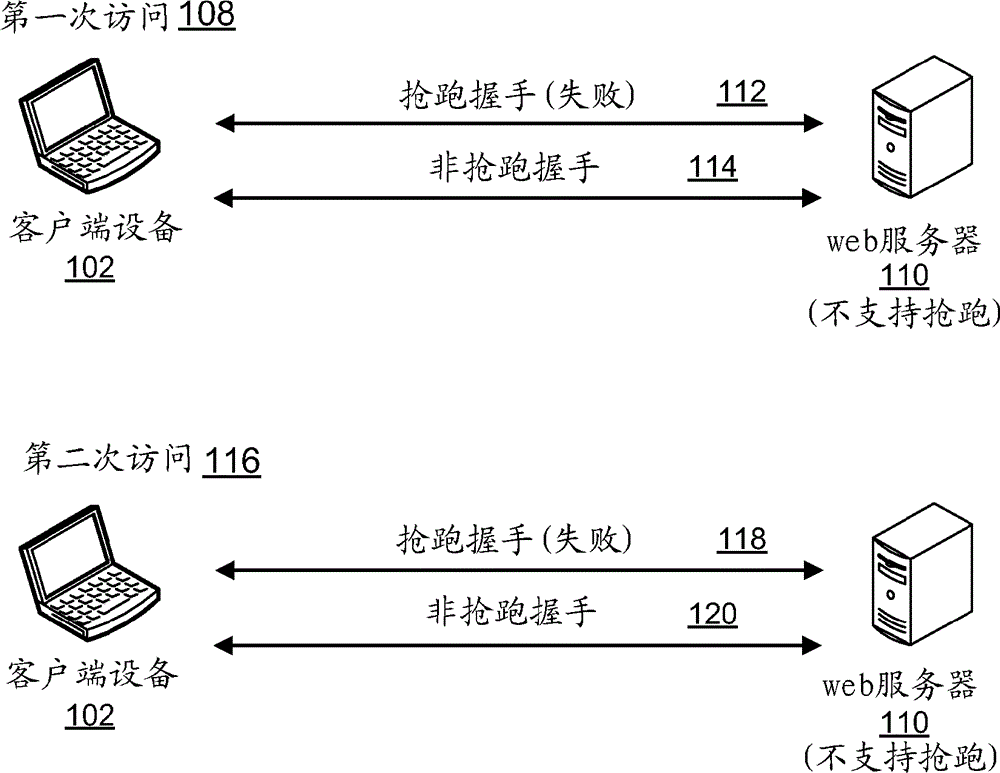
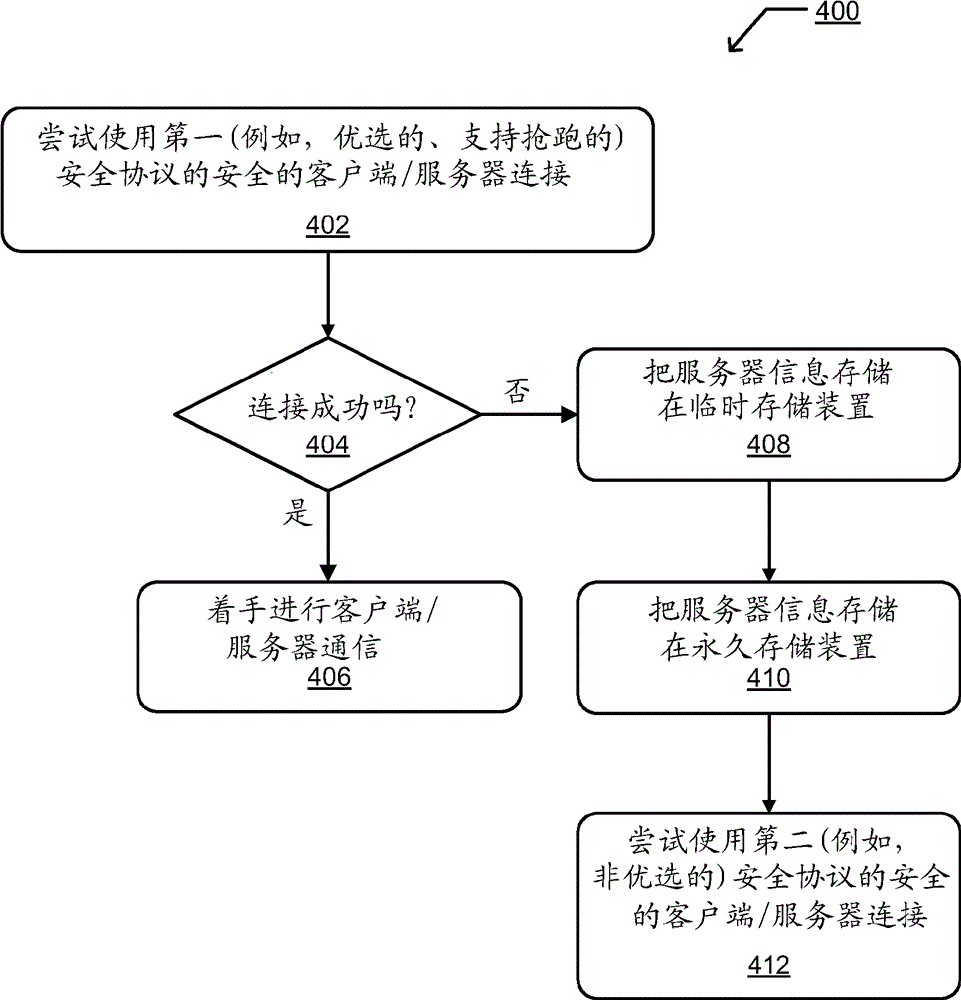
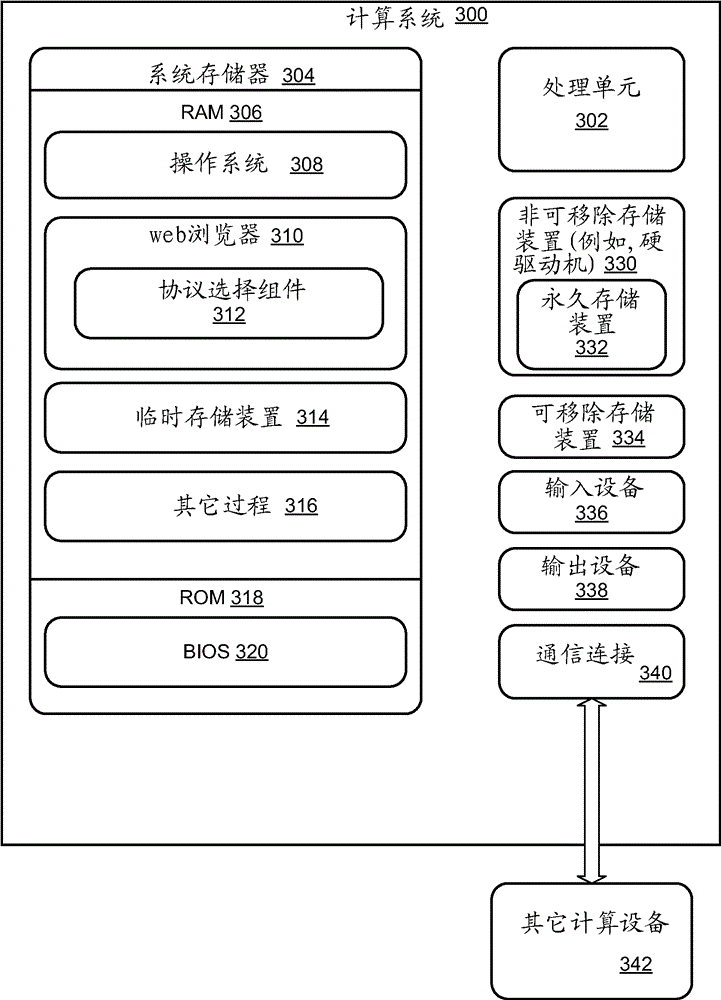
[0014] Embodiments described herein provide techniques for a preemptively enabled client to determine whether to use a preemptively modified protocol to attempt to establish a secure connection with a server or host. The front-running modification for SSL (for example, SSL 3.0 and later) and TLS (for example, TLS 1.0, 1.1, 1.2 and later) reduces Little waiting time. However, not all servers support the protocol with the preemptive modification. When a client that supports preemption attempts to handshake with a server that does not support preemption, the handshake fails and the client retries the handshake without preemption. A first failed handshake attempt can cause increased latency in establishing a connection, thus potentially degrading the performance of a web browser or other client-side application attempting to establish a secure communication with the server. To prevent such performance degradation, embodiments enable storing information or metada...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com