Terminal identification method, machine identification code registration method, and corresponding system and equipment
A technology of machine identification and terminal identification, which is applied in the transmission system, digital transmission system, digital data authentication, etc., can solve the problem of unfavorable user machine identification code privacy protection, consumption of communication and computing resources, machine identification code is easy to be decompiled and intercepted or Breakthrough and other issues
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
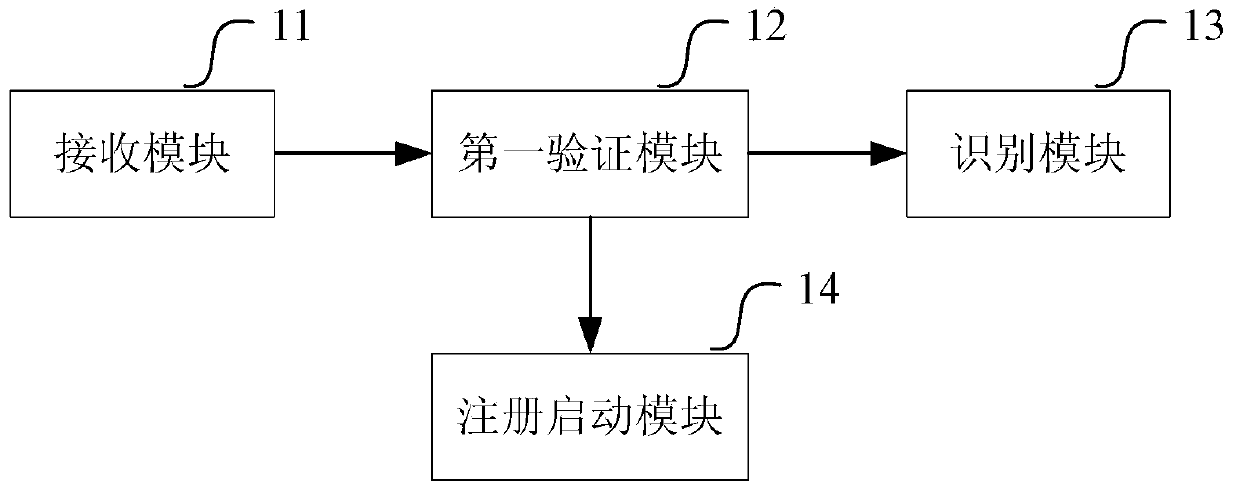
[0098] The system in this embodiment includes a terminal, a service network, and a trusted party, and the terminal may be user equipment such as a PC, a smart phone, or a PDA. The service network is used to provide network services for the terminal, such as one or more website systems or network platforms, and the service network can identify the terminal sending the request. The trusted party is used to assign machine identification code identifiers and issue signatures or certificates for terminal machine identification codes. It should be noted that the trusted party may be a node in the service network, or a node outside the service network.
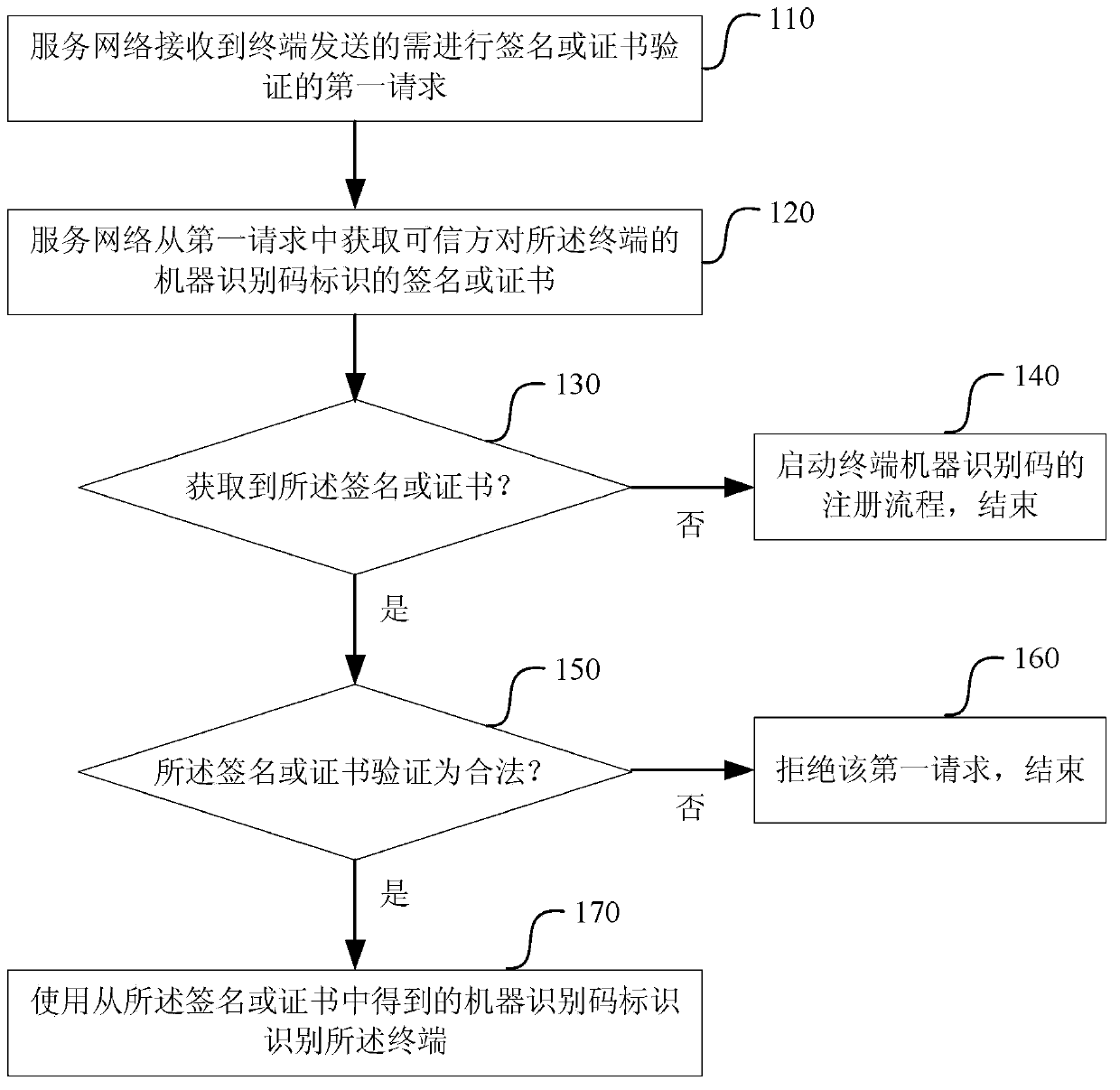
[0099] Such as figure 1 As shown, the terminal identification method in this embodiment includes:
[0100] Step 110, the service network receives the first request for signature or certificate verification sent by the terminal;
[0101] Here, the first request for signature or certificate verification is set by the service network...
Embodiment 2
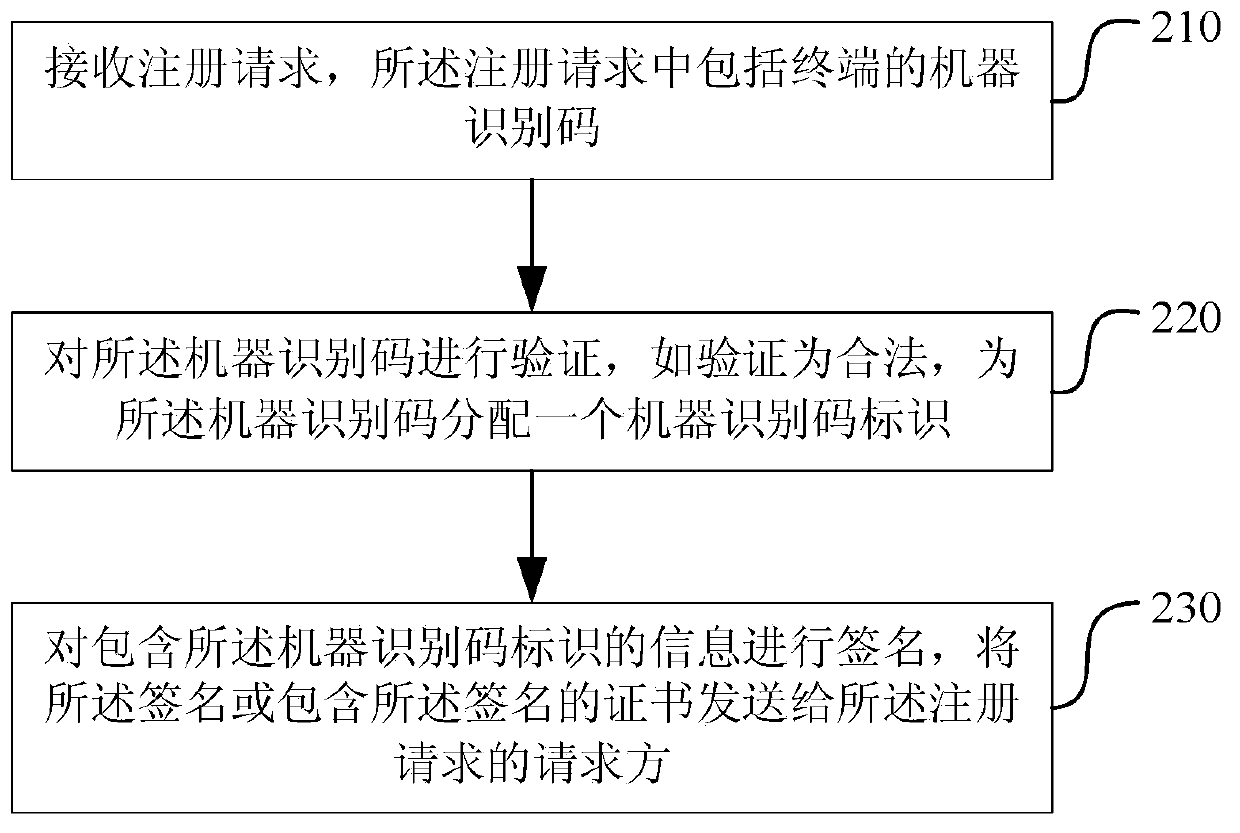
[0141] The service network in Embodiment 1 uses the machine identification code identifier as the terminal identifier to realize the identification of the terminal. However, illegal users may store a large number of signatures or certificates issued by trusted parties on the same machine, just like the existing spam accounts, there are a large number of spam The cost is higher. Then send requests to the service network through malicious programs, and use different signatures or certificates in different requests. At this time, the service network will not be able to effectively identify the terminal. Therefore, on the basis of the first embodiment, this embodiment adds the processing of machine identification code verification.
[0142] In this embodiment, the machine identification code and the corresponding machine identification code or its derivative code need to be stored in the database. Specifically, the trusted party can associate the machine identification code of t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com