DDoS (distributed denial of service) attach detection method based on information entropy
An attack detection and information entropy technology, applied in the field of cloud computing, can solve problems such as restricting the effective detection and identification of DDoS attacks, difficulty in detecting victim terminals, and limited processing capacity, achieving the effects of good security, easy promotion, and strong practicability.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0019] The present invention will be further described below in conjunction with the accompanying drawings and specific embodiments.
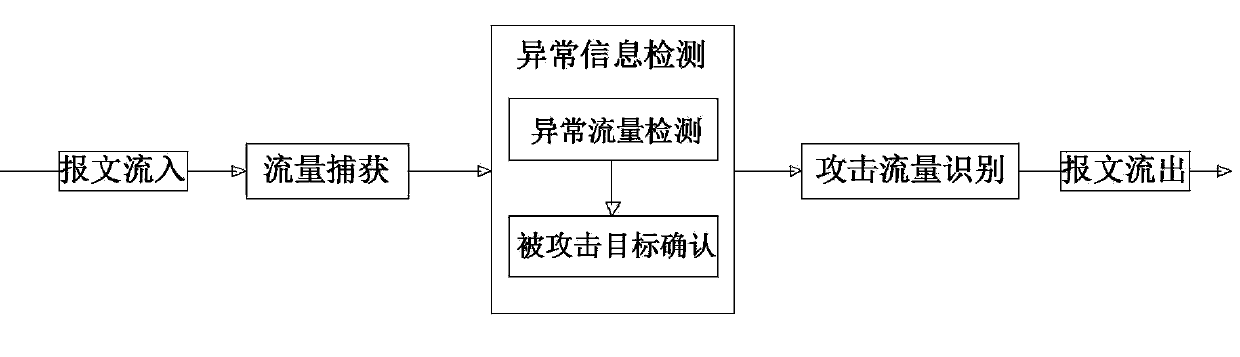
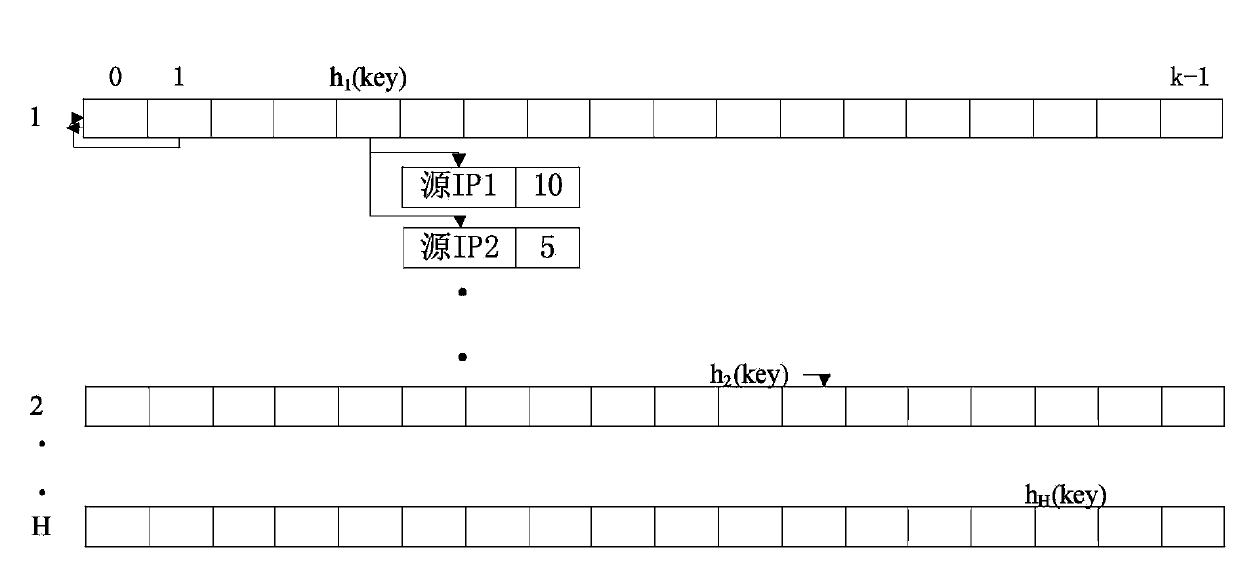
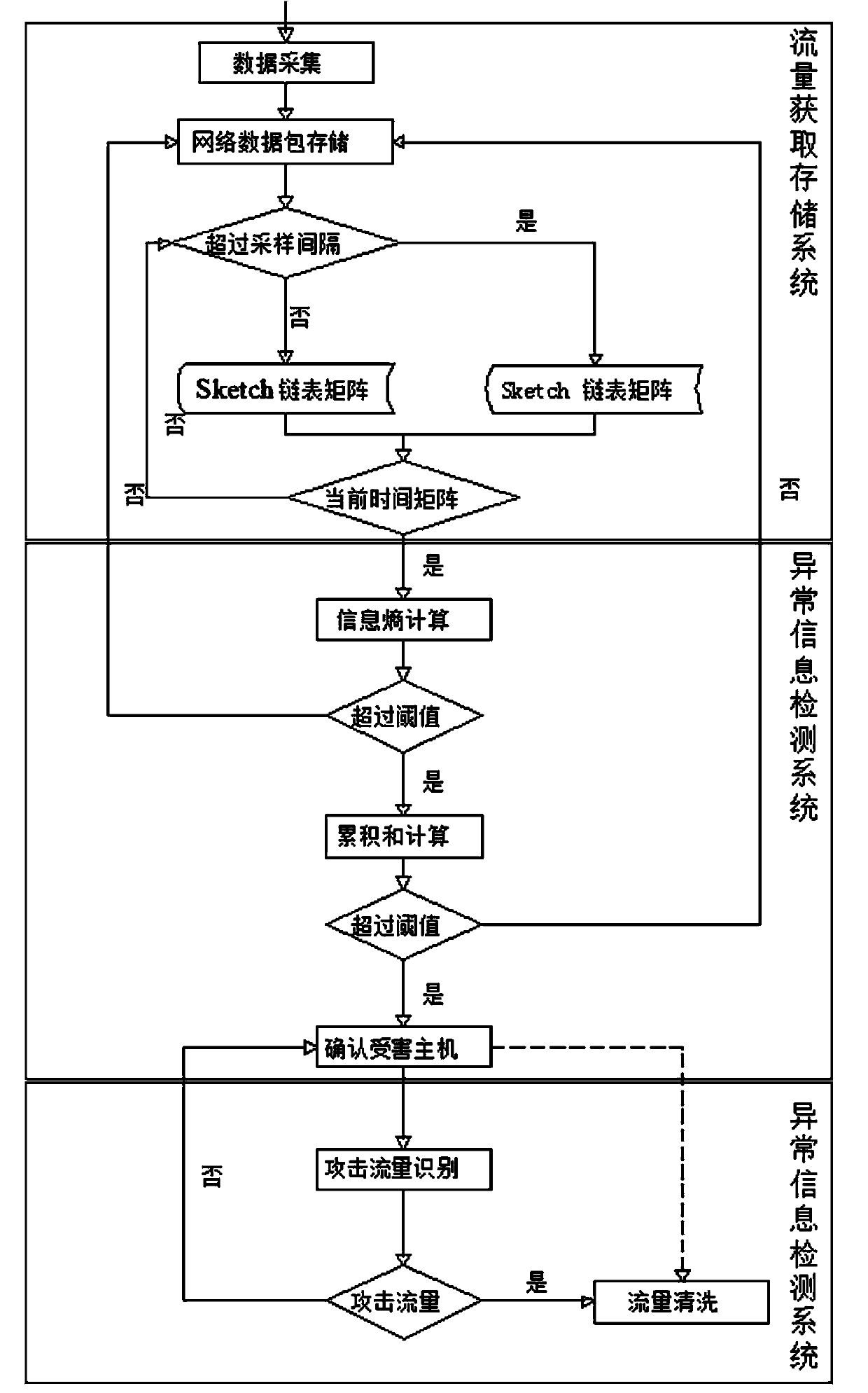
[0020] The present invention provides a DDoS attack detection method based on information entropy. The present invention determines the occurrence of abnormal traffic through information entropy, uses two sketch linked list matrices to alternately store network traffic in real time, and conducts information on the matrix at the current moment. The entropy operation is used to judge whether there is abnormal flow. For the abnormal traffic matrix, the cumulative error of the cumulative sum (CUSUM) algorithm is used to detect the offset between the object to be inspected and the target to determine the IP address of the victim. For the determined attacked IP address traffic, the Pearson correlation system method is used to classify the linked list information to determine the attack traffic and prepare for the next traffic cleaning work. Based on...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com