File information storage method and file information read-write method based on separate storage
A file information, separate storage technology, applied in the file information storage based on separate storage, the file information read and write field, can solve the problems of inflexible processing, error-prone, extended metadata size limit, etc., to achieve wide adaptability. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
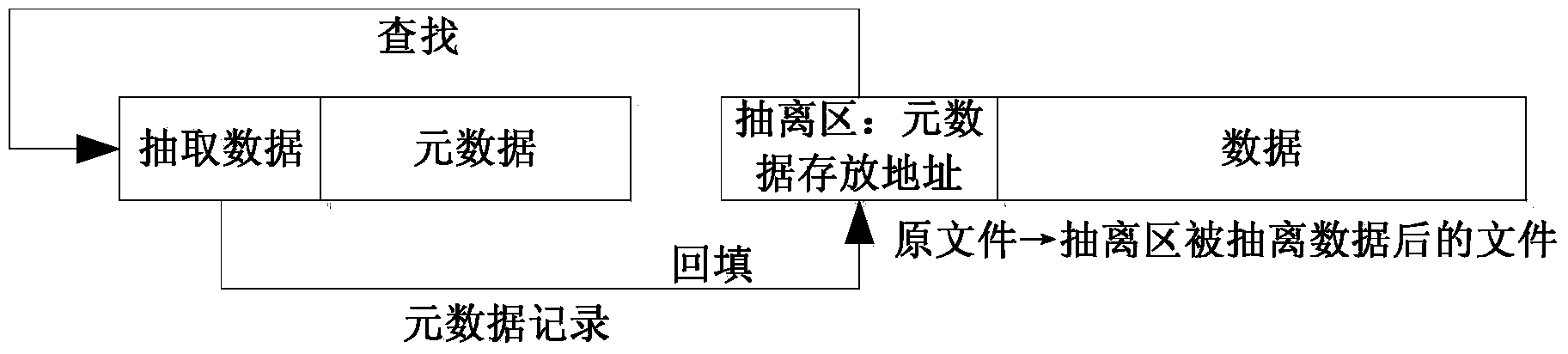
[0046] Such as figure 1 and figure 2 As shown, this example provides a file information storage method based on separate storage, including the following steps:
[0047] In the detection record step, when opening a file, first check whether there is a record of the metadata storage address in the file, if it does not exist, jump directly to the new record step; if it exists, first judge whether it is a valid record, when the record is valid When accessing and reading back metadata and extracting data based on records;
[0048] Update the metadata judging step to judge whether the content in the metadata file has changed. When the access operation involves a change in the content of the extracted data, update the extracted data backed up in the metadata file and then jump to the step of backfilling the file; when the access operation involves When the content of the metadata changes, update the metadata backed up in the metadata file and jump to the step of backfilling the f...
Embodiment 2
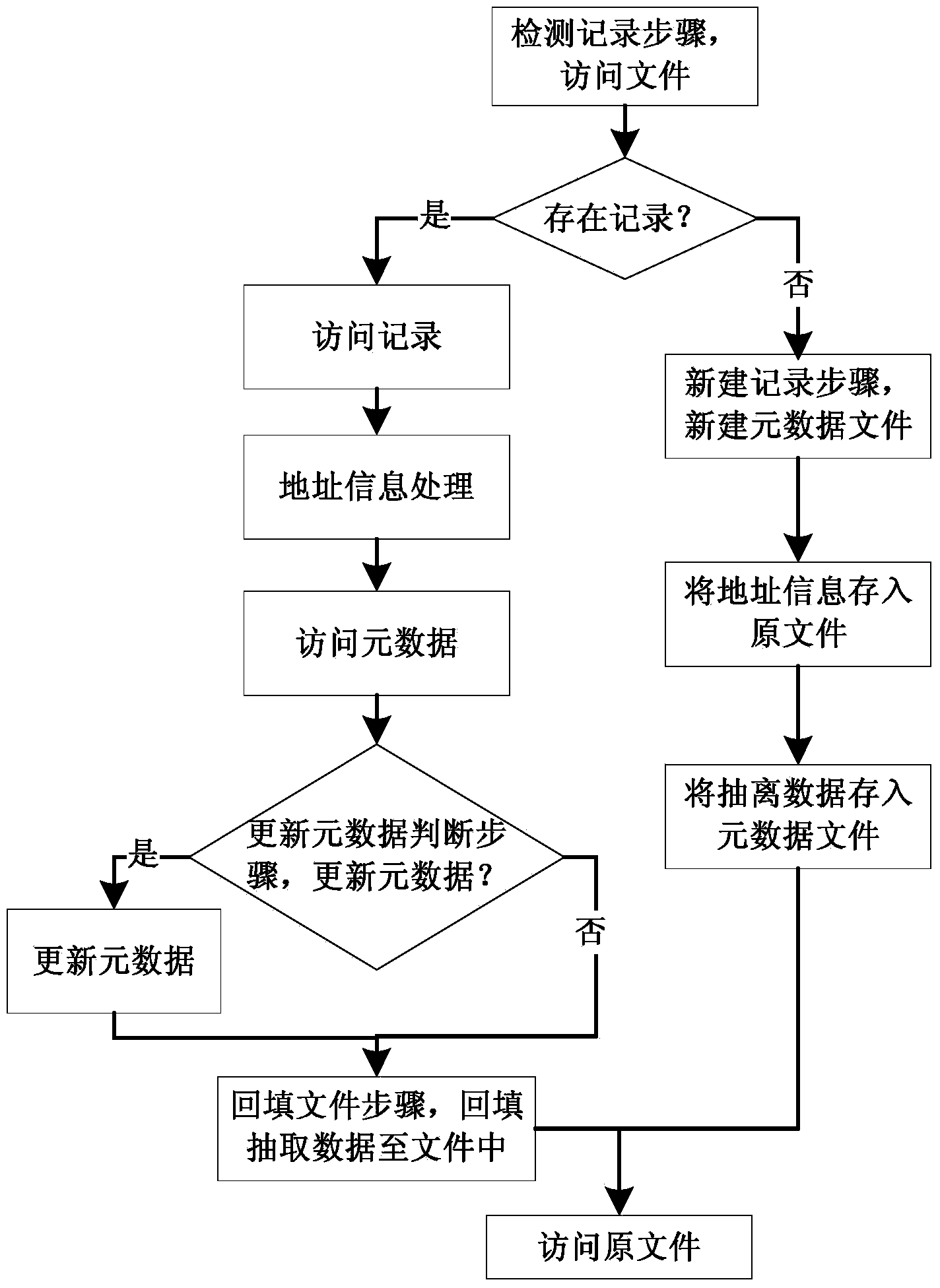
[0068] Such as image 3 As shown, this example also provides a method for reading and writing file information based on separate storage. In this example, the method for storing file information based on separate storage described in Embodiment 1 is used for file storage. The method for reading and writing file information includes the following reading and writing methods: Take steps:
[0069] Judging the record step, when the file is opened, read the record of the metadata storage address in the file, judge whether the record is valid, if it is valid, jump to the safety monitoring judgment step, if it is invalid, create a new record and jump to the information saving step ;
[0070] The security monitoring judgment step is to judge whether the file has been encrypted and split, if not, jump directly to the information saving step; if so, then access the file access counter in the file index and the metadata file access counter in the metadata file, and compare the two Whet...
Embodiment 3
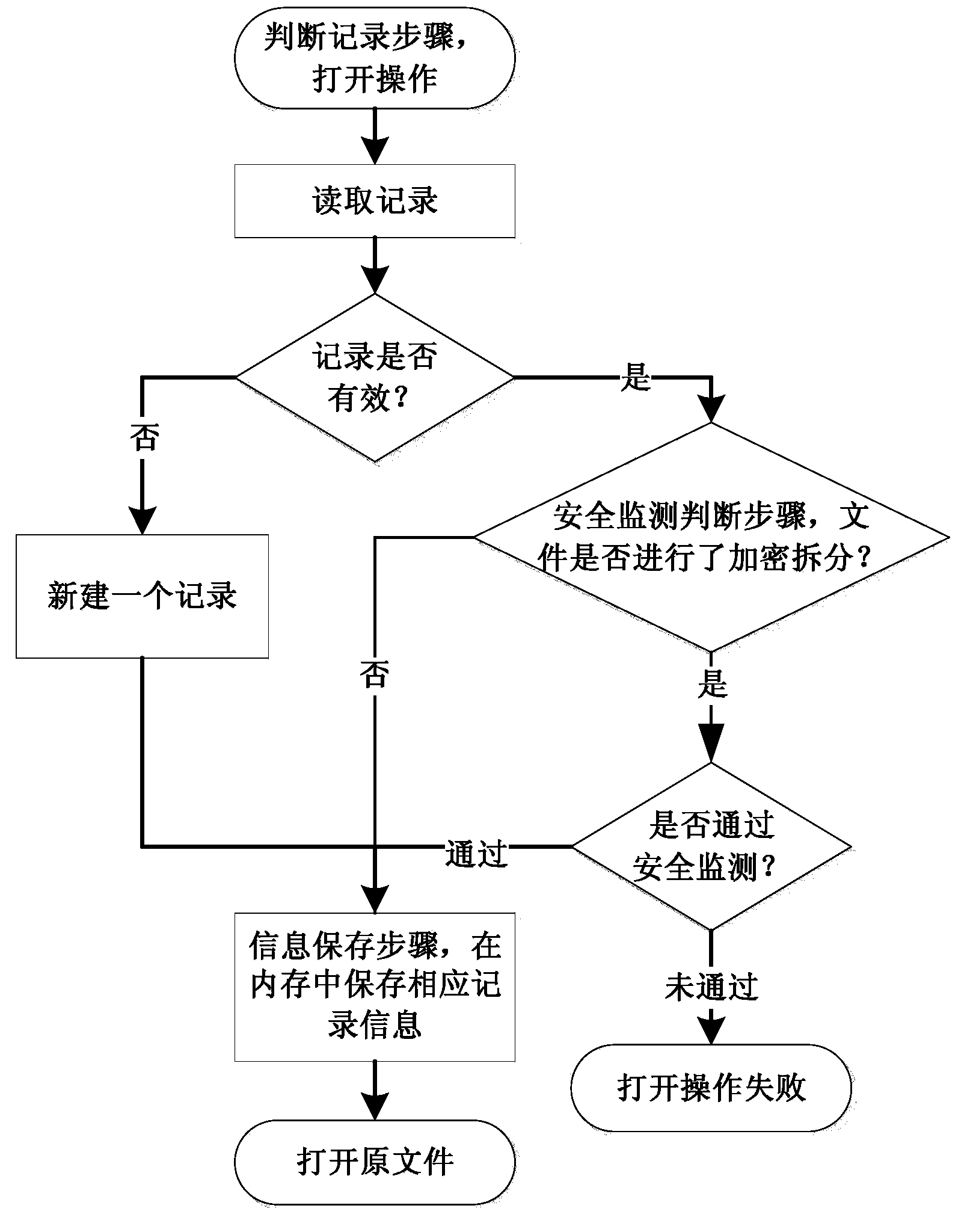
[0077] Such as Figure 4 As mentioned, on the basis of Embodiment 2, the file information reading and writing method described in this example includes the following writing steps:
[0078] Read step, start to write the file operation, read the corresponding record in the memory, judge whether there is a record, if not, directly realize the operation of writing the original file, if so, skip to the update judgment step;
[0079] The update judging step is to judge whether the record needs to be updated, if so, update the record information and jump to the judgment step of writing into the detachment area, otherwise directly jump to the judgment step of writing into the detachment area;
[0080] Write into the detachment area judging step, judging whether the update record needs to be written into the detachment area of the original file, if so, modify the metadata file and then jump to the splitting step, otherwise directly jump to the splitting step;
[0081] And, in the s...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com