Mobile secret communication method based on quantum key distribution network
A quantum key distribution and secure communication technology, which is applied in the field of mobile communication encryption, can solve problems such as the limitation of the shared quantum key generation distance, the long consumption of business keys, and the impact on service quality, etc., to expand the scope of business application and shorten the construction period. The effect of short and low modification cost
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
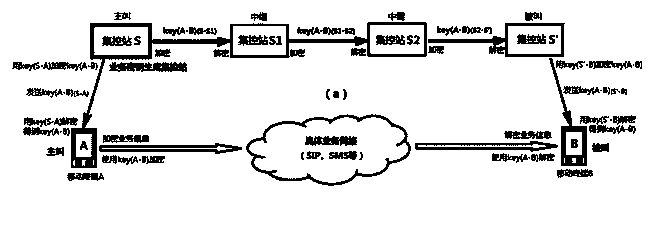
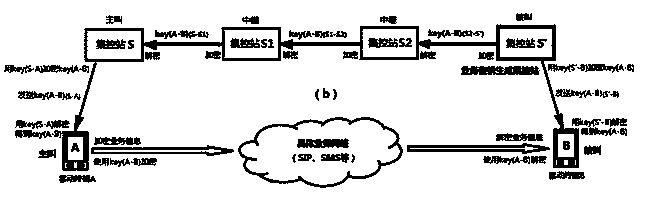
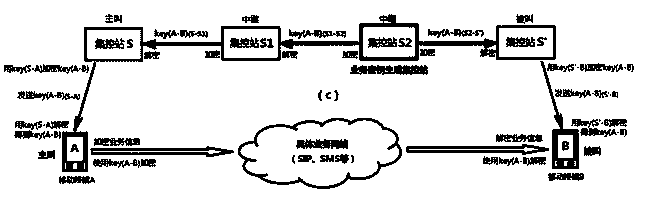
[0067] Below in conjunction with accompanying drawing and embodiment the present invention will be further described:
[0068]The main hardware devices involved in the mobile secure communication method based on the quantum key distribution network include: ① mobile terminal, which can be a smart phone, a tablet computer, a set-top box, a notebook computer, a PDA or other mobile devices, it is the initiator of communication services and receiver. There should be a permanent storage device inside it, such as a flash memory chip, for storing the downloaded shared key with the centralized control station; there should be a temporary storage device, such as a memory, for storing the downloaded business key; Hardware modules capable of supporting network access can exchange data with the outside world through traditional uplink and downlink network channels (including various wireless networks); should have the ability to exchange information with quantum key distribution networks;...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com