Method for resisting replay attack on basis of early warning mechanism self-adaptive selection protocol
A technology of adaptive selection and replay attack, applied in the field of mobile communication, can solve the problem that SQN cannot effectively resist replay attack, and achieve the effect of adaptive selection, optimization of incomplete attack resistance, and reduction of traffic volume.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0034] The following will refer to Figure 1-5 Embodiments of the present invention will be described.
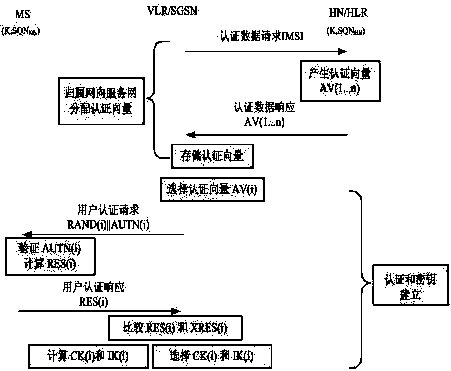
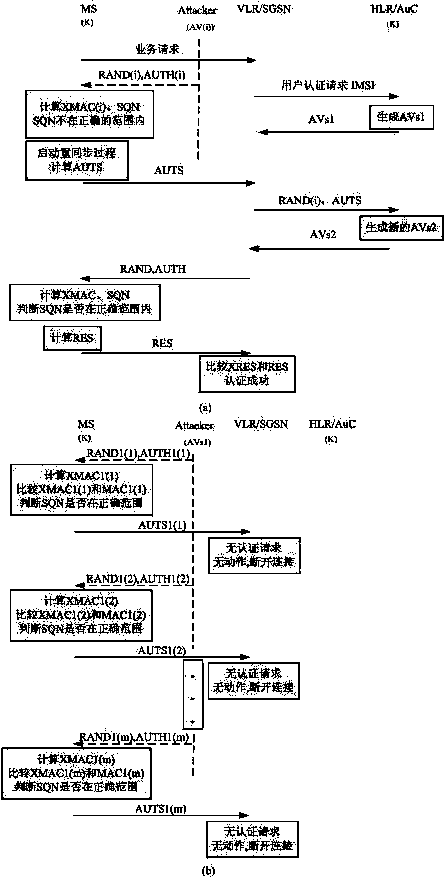
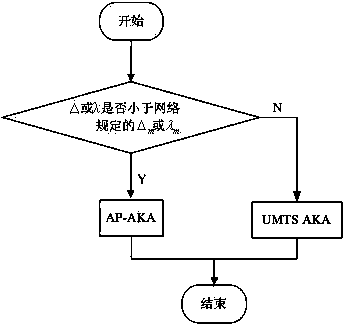
[0035] Taking UMTS AKA as an example, such as figure 1 shown. In actual network operation, three problems must be solved: First, how to judge whether there is a replay attack. The second is how to judge the type of replay attack. The third is how to adaptively select an agreement based on the early warning mechanism.
[0036] For question 1, determine whether the received message is a replay message:
[0037] During the implementation of the UMTS AKA protocol, after receiving the user authentication request messages RAND and AUTH, the MS judges whether the received message is a replay attack by judging the correctness of the AUTH. When judging the correctness of the AUTH, the MS calculates the XMAC and SQN values , and compare whether the XMAC is equal to the MAC from AUTH, and then judge whether the SQN is in the correct range. If the SQN is not in the correct range,...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com