ID authentication
A password and device technology, used in digital data authentication, electronic certificates, payment systems, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
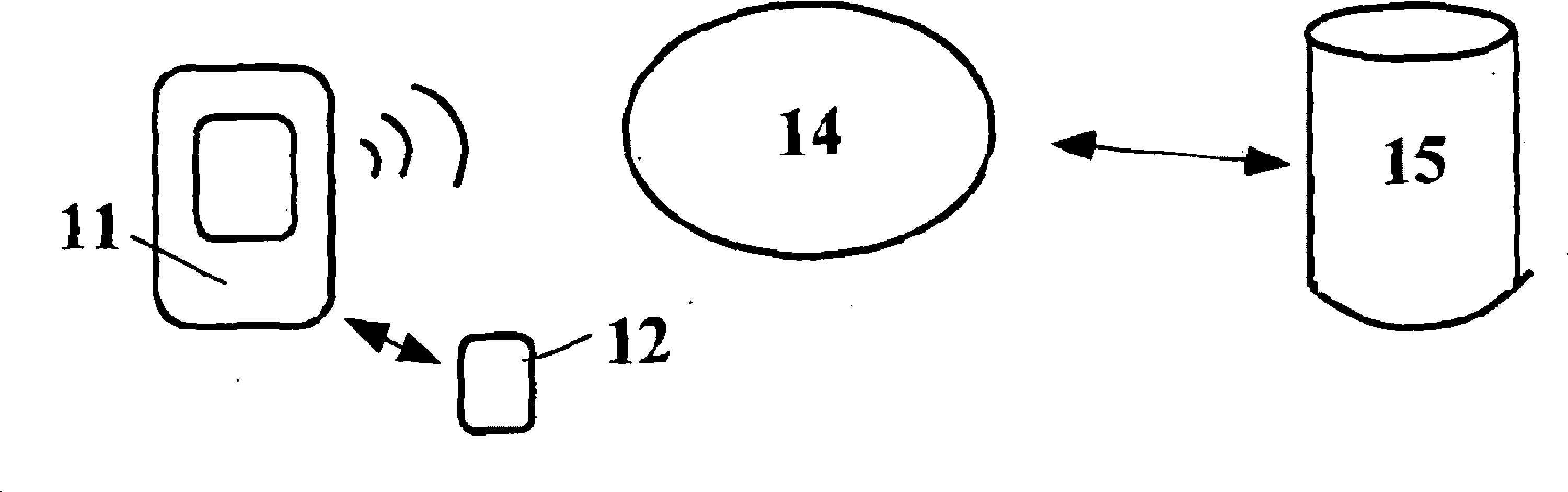
[0033] The figure illustrates a method for ID authentication in which a device 11 involved in a transaction requests a password from a physically separate but limited-range communication device 12 which, in response to such a request, automatically supplies and communicates the password to the device 11. The password is evaluated as valid or invalid and the transaction is approved or disapproved accordingly.
[0034] Devices 11 include mobile phones or other mobile devices operating in an environment 14 such as a cellular network, or computers communicating with a server 15 over the Internet, which require ID authentication. This could be a credit or debit card transaction system, or an online banking portal, or any other entity where information is stored.
[0035] Physical separation means that both the compromised device (mobile phone or computer 11 ) and device 12 will be required to enable unauthorized access. The mobile phone itself will not allow ID authentication, it ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com