Trojan horse communication feature fast extraction method based on clustering analysis of multiple data streams
A cluster analysis, multi-data stream technology, applied in text database clustering/classification, special data processing applications, unstructured text data retrieval, etc. The effect of recombination efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
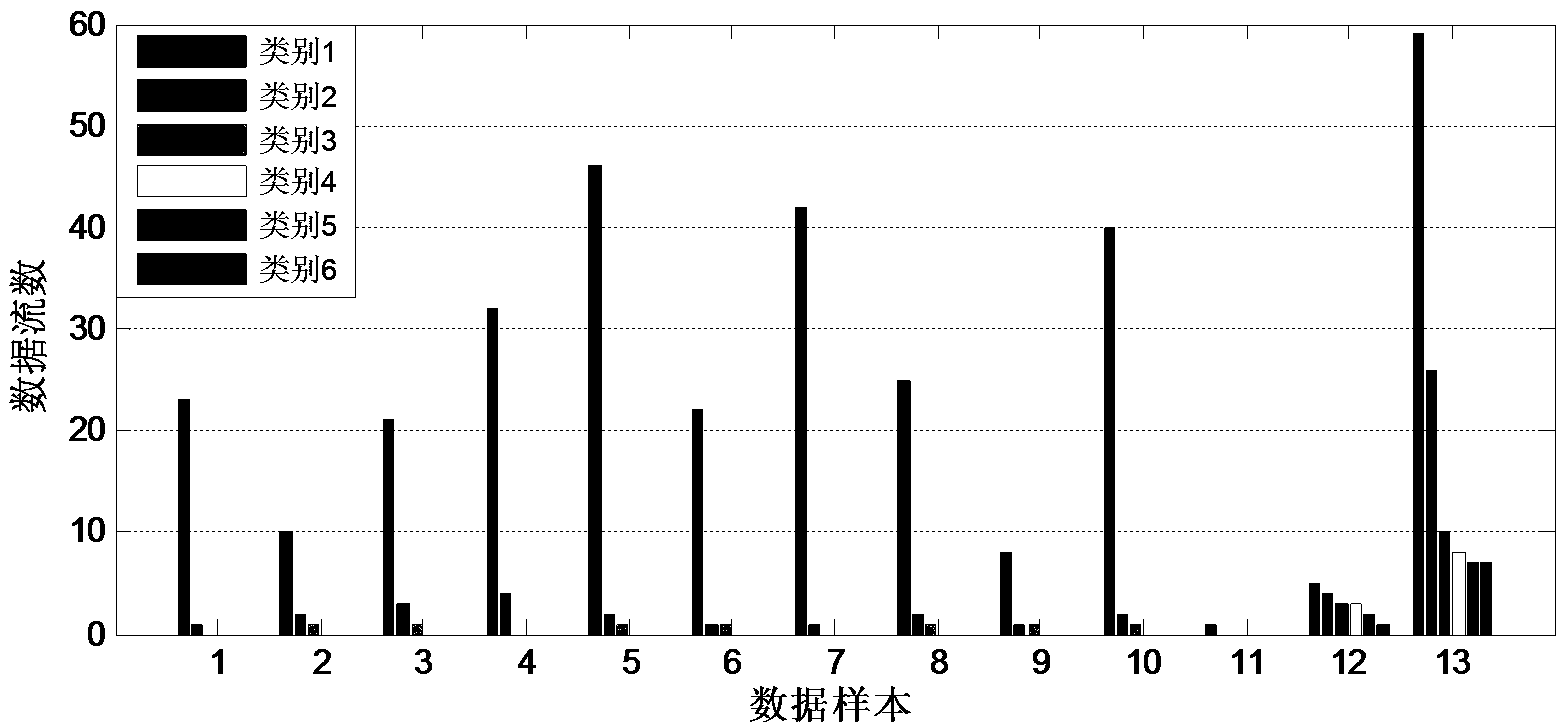
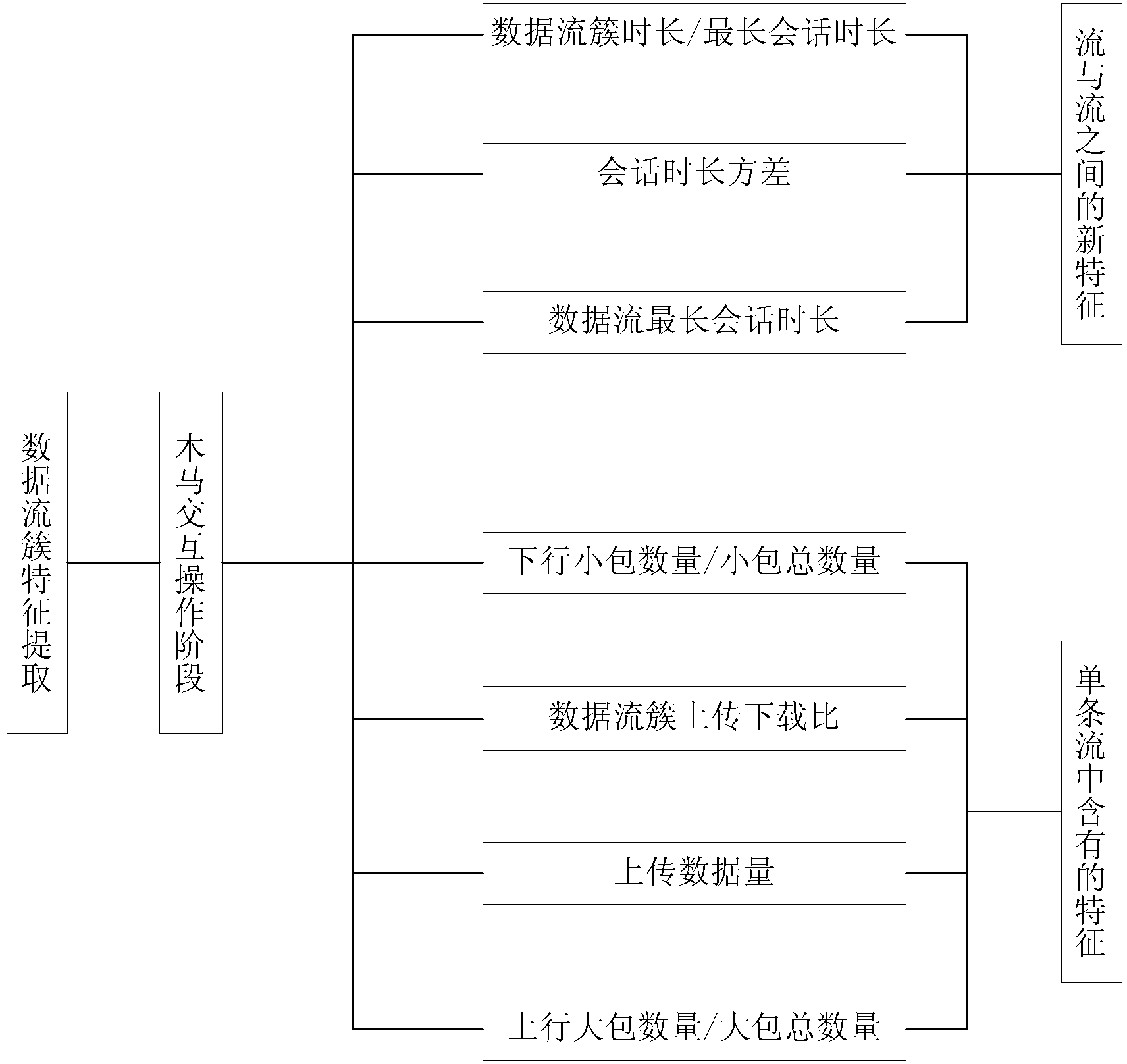
[0059] Embodiment 1: the Trojan horse communication feature extraction method based on multi-data flow clustering analysis is:
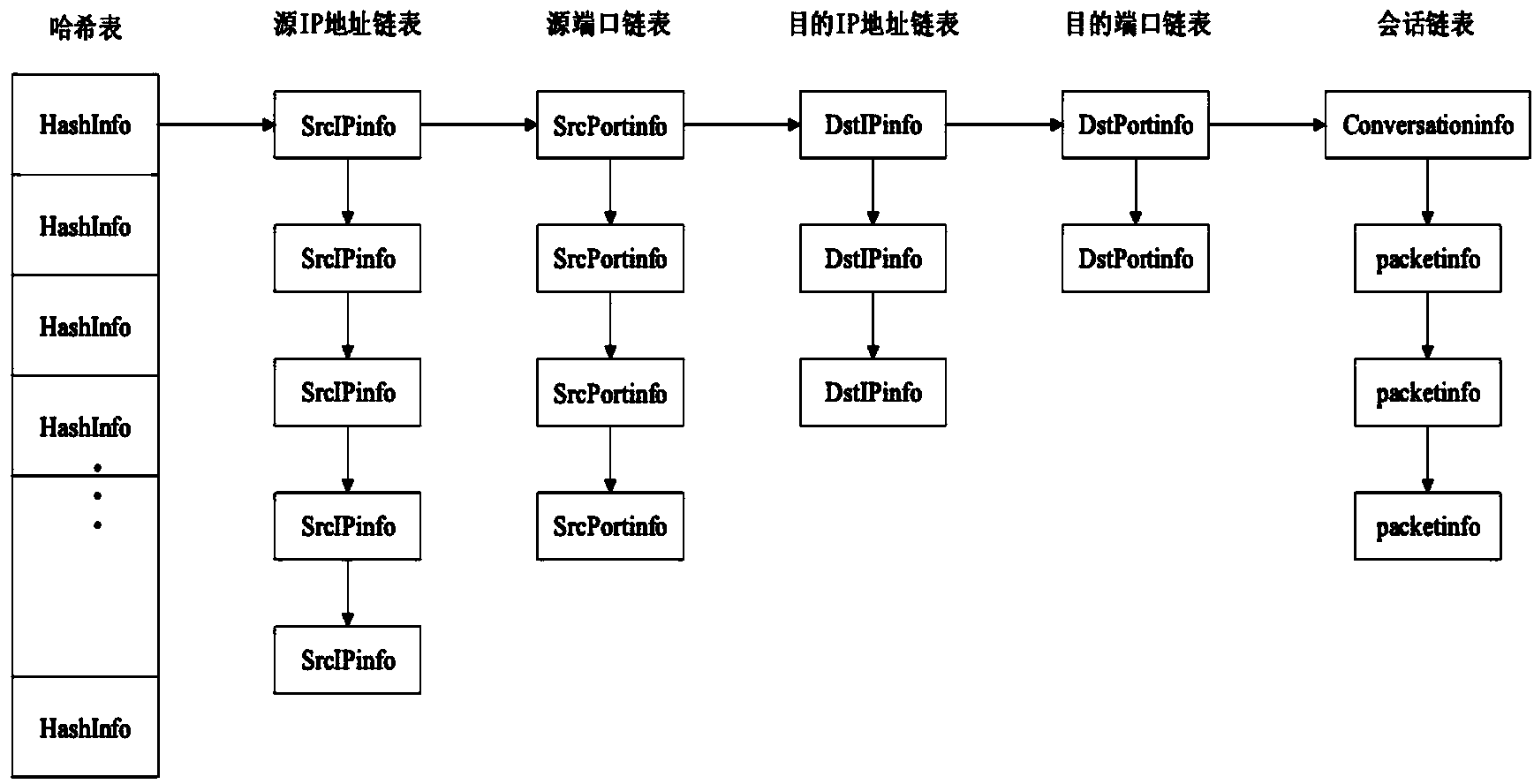
[0060] First, organize the captured network data packets according to network sessions: use the IP address and port of the monitored object as the source IP address and source port. The data packet is divided into sessions according to the equivalent quadruple (source IP address, source port, destination IP address, destination port), that is, each session is uniquely identified by the equivalent quadruple (at this time, each session linked list contains two-way data stream), and use the session linked list as the data structure for storing sessions. The reason for choosing the session linked list as the data structure for recording the session is: since the network communication is a dynamic process, the data packets in the session will continue to increase as the communication progresses, and the data structure used to save the session will also ch...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com