Parallel lookup method for high-capacity access control list
An access control list and large-capacity technology, which is applied in the search field of large-capacity access control lists, can solve problems such as difficult to meet the needs of practical applications, low algorithm operation efficiency, complex data structure organization, etc., to achieve fast and flexible design, eliminate Technical bottlenecks and the effect of improving resource utilization
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
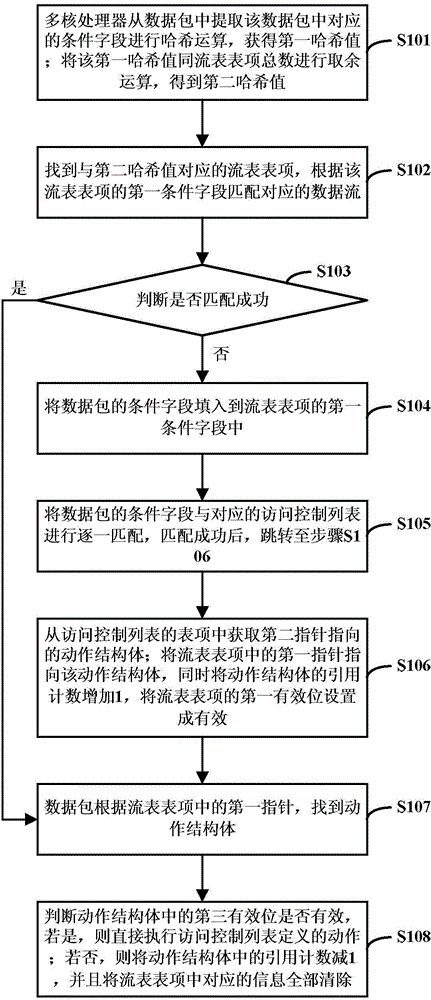
[0027] The present invention will be described in further detail below in conjunction with the accompanying drawings and embodiments.
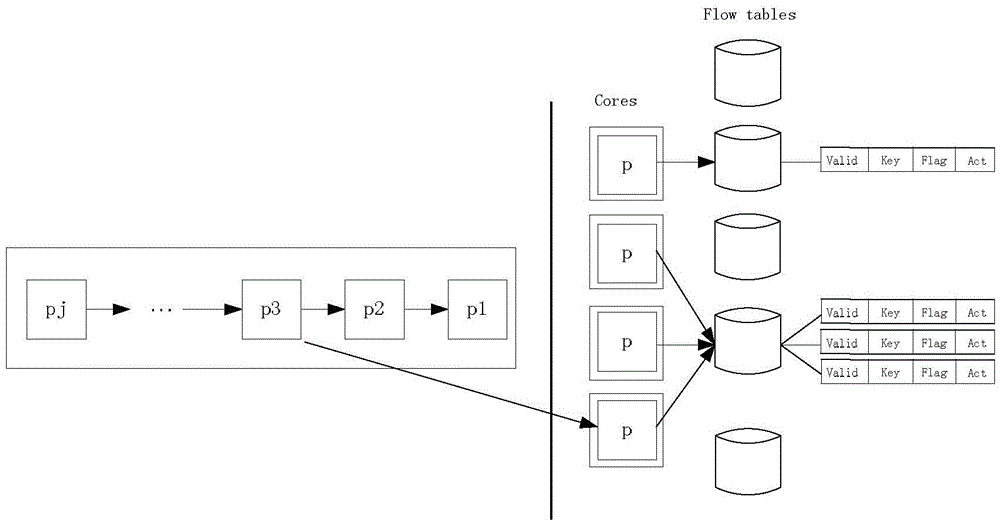
[0028] see figure 1 As shown, a parallel large-capacity access control list search method is implemented based on multi-core processors, including:
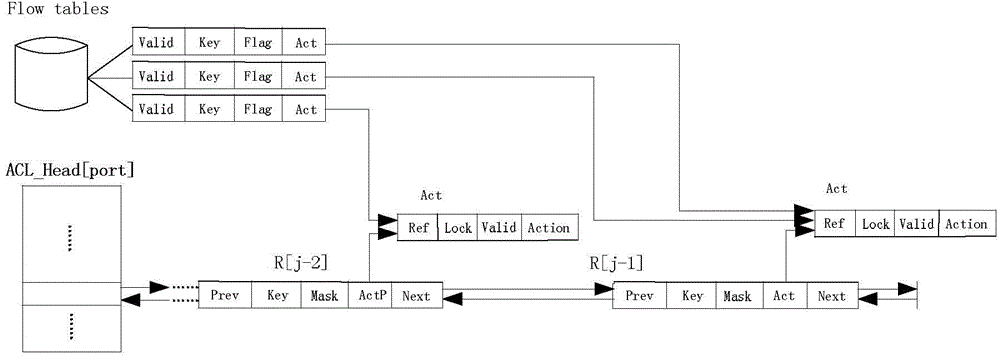
[0029] The linked list storage structure of the access control list is set as a two-way linked list, and the structural relationship between the entries in the access control list is established. Wherein, the linked list storage structure of the access control list can also be designed as a tree structure or a graph structure.
[0030] Multi-core processors (Cores) divide the first incoming data streams (P1, P2...Pj), establish flow tables (Flow tables), and search for appropriate access control list entries at the same time, and establish flow tables and access control list tables The association of items; wherein, the multi-core processor distributes the data packets (P) in the received data ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com