Two-dimension code generating method, terminal and server and two-dimension code reading method, terminal and server
A server and two-dimensional code technology, applied in the field of information processing, can solve the problems of increasing the cost of reading two-dimensional codes, not being able to guarantee the security of private information, and unfavorable application of two-dimensional codes, so as to reduce generation and reading costs and ensure safety , the effect of expanding the scope of application
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
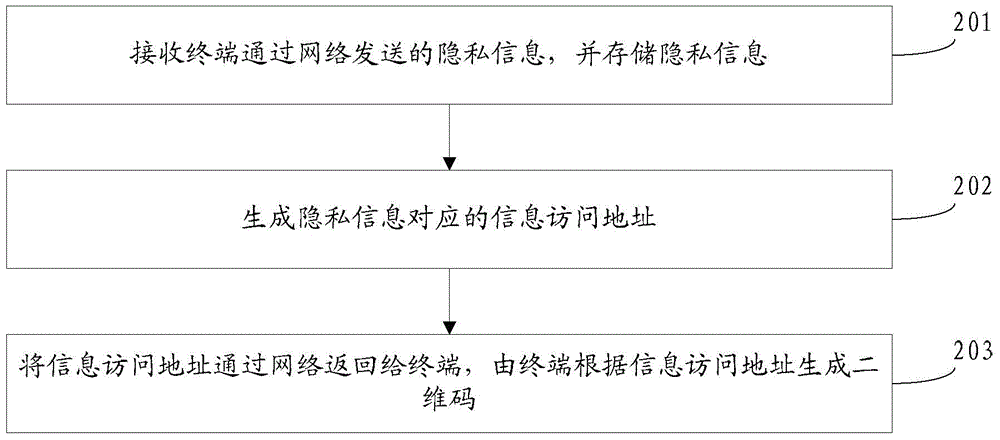
[0070] For private information, an embodiment of the present invention provides a method for generating a two-dimensional code, the method is applicable to a system for generating a two-dimensional code, the system includes a terminal and a server, and both the terminal and the server are in a network environment. Taking the perspective of the terminal executing the method provided by the embodiment of the present invention as an example, see figure 1 , the method flow includes:
[0071] 101: Obtain the private information input by the user, and send the obtained private information to the server through the network, and the server stores the private information, and generates an information access address corresponding to the private information;
[0072] 102: receiving the information access address returned by the server through the network;
[0073] As an optional embodiment, receiving the information access address returned by the server through the network includes:
...
Embodiment 2
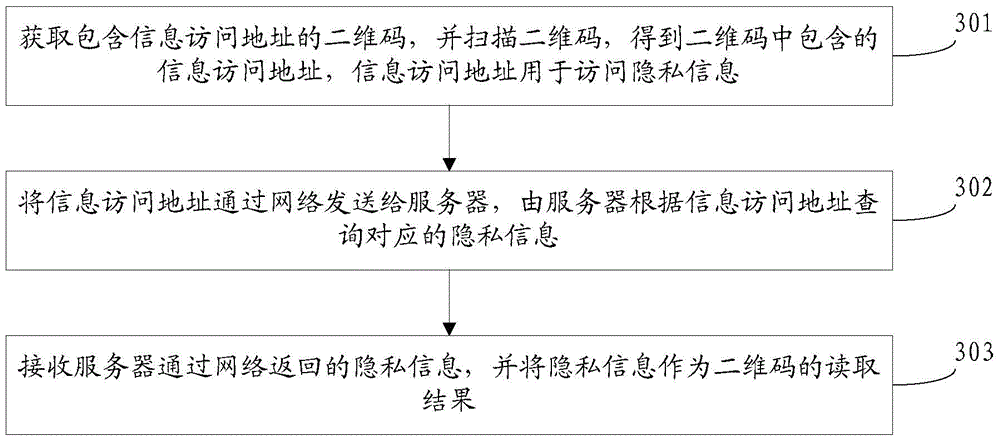
[0091] Regarding the method for generating a two-dimensional code provided in the first embodiment above, the embodiment of the present invention provides a method for reading a two-dimensional code, which is suitable for a two-dimensional code reading system, the system includes a terminal and a server, and Both the terminal and the server are in the network environment. Taking the perspective of the terminal executing the method provided by the embodiment of the present invention as an example, see image 3 , the method flow includes:
[0092] 301: Obtain a two-dimensional code containing an information access address, and scan the two-dimensional code to obtain the information access address contained in the two-dimensional code, and the information access address is used to access private information;
[0093] 302: Send the information access address to the server through the network, and the server queries the corresponding private information according to the informatio...
Embodiment 3
[0114] An embodiment of the present invention provides a method for generating a two-dimensional code. The method provided by the embodiment of the present invention is explained in detail in combination with the content of the first embodiment above. see Figure 5 , the method flow includes:
[0115] 501: The terminal obtains the private information input by the user, and sends the obtained private information to the server through the network;
[0116] This embodiment does not specifically limit the manner of obtaining the private information input by the user. During specific implementation, it includes but is not limited to providing an information input interface, which also provides a submit button; obtaining the information input by the user through the information input interface, and when it is detected that the user clicks the submit button, the information input by the user through the information input interface The information is used as the obtained private inf...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com