A wireless terminal authentication method, wireless router and system
A wireless router and wireless terminal technology, applied in the transmission system, wireless communication, digital transmission system, etc., can solve the problems of being easily forged, reducing the security of the wireless local area network, and the security of the wireless terminal authentication process is not high, so as to reduce the risk of forgery Possibility, effect of improving safety
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
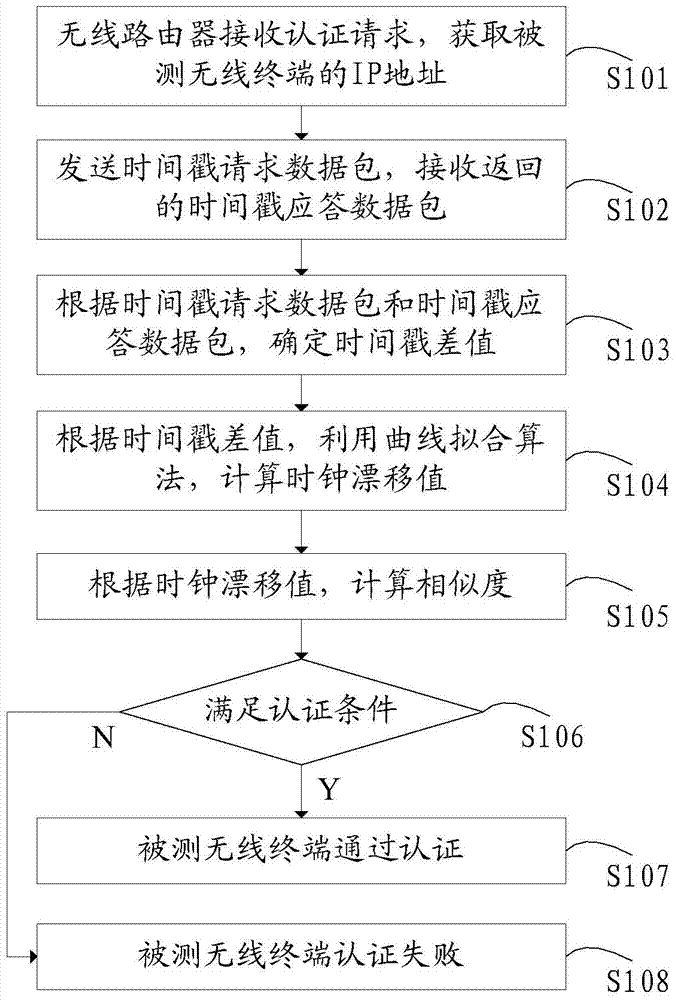
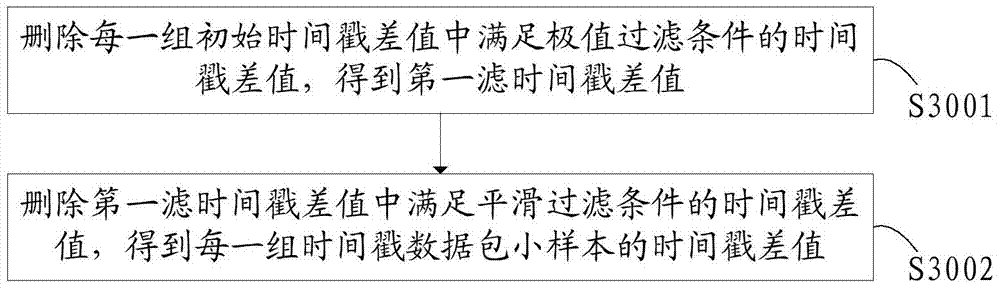
[0123]In the wireless terminal authentication method disclosed in Embodiment 1, after the wireless router receives the time stamp response data packet returned by the wireless terminal under test, it will sample and group all the finally obtained time stamp data packets, thereby reducing the authentication process. In addition, before calculating the clock drift value, the wireless router will perform offset deletion processing on the initial timestamp difference, which improves the accuracy and stability of the subsequent clock drift value to be calculated.
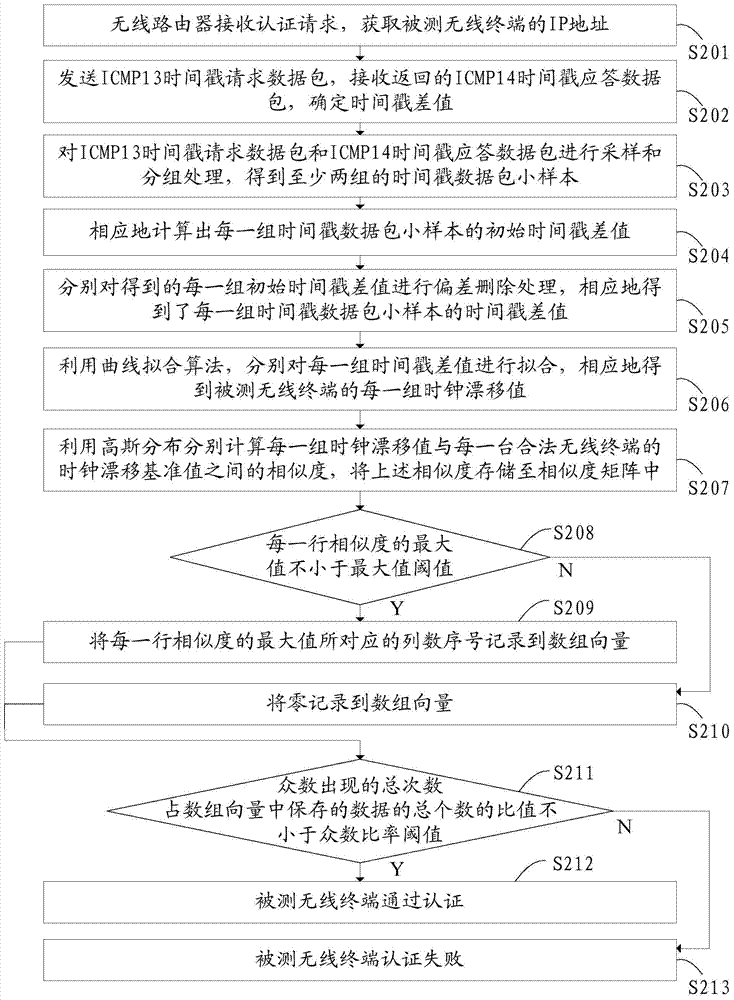
[0124] In order to further simplify the authentication process of the wireless terminal, the process of the wireless router judging whether the wireless terminal under test satisfies the authentication condition in the first embodiment is optimized below to obtain the second and third embodiments.
Embodiment 2
[0125] In Embodiment 2, the process of the wireless router judging whether the tested wireless terminal satisfies the authentication conditions is as follows:
[0126] The wireless router separately calculates the median of the similarity of each column in the similarity matrix, and judges whether the maximum value of the above median is greater than or equal to the threshold of the median, if yes, the wireless terminal under test passes the authentication, if not, then The wireless terminal under test fails to authenticate.
[0127] The preferred median threshold is 68.26%.
[0128] In the similarity matrix shown in Table 1, the median of the similarity between the first column and the third column is approximately equal to 0, the median of the similarity of the fourth column is 94.263%, and the median of the similarity of the fifth column is 5.7569%, so the maximum value of the above-mentioned median is 94.263%, which is greater than 68.26%, so it is determined that the tes...
Embodiment 3
[0130] In the third embodiment, the process of the wireless router judging whether the wireless terminal under test satisfies the authentication conditions is as follows:
[0131] The wireless router separately calculates the average value of the similarity of each column in the similarity matrix, and judges whether the maximum value of the above average value is greater than or equal to the average threshold value. If yes, the tested wireless terminal has passed the authentication; if not, the tested wireless terminal Terminal authentication failed.
[0132] The preferred mean threshold is 68.26%.
[0133] In the similarity matrix shown in Table 1, the average value of the similarity from the first column to the third column is approximately equal to 0, the average value of the similarity in the fourth column is 85.32%, and the average value of the similarity in the fifth column is 7.77% , so the maximum value of the above average value is 85.32%, which is greater than 68.26...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com