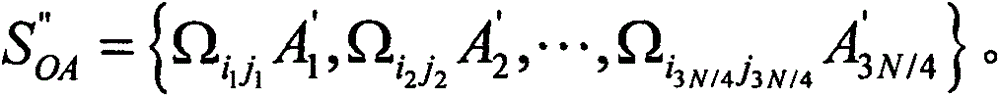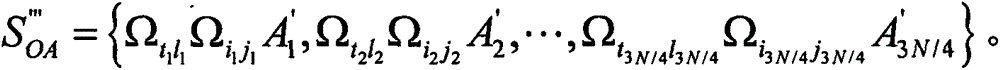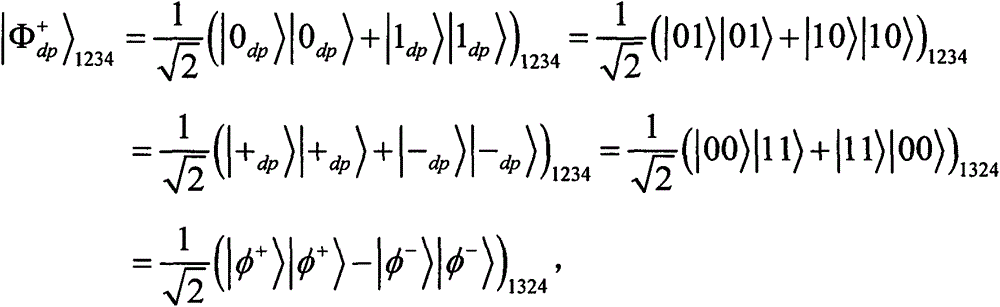Quantum dialogue protocol with collective-dephasing noise resisting authentication based on logic Bell states
A technology of phase noise and quantum dialogue, applied in user identity/authority verification, electrical components, transmission systems, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
[0114] 1. Application example of AQD protocol
[0115] Suppose (i 1 , j 1 ) and (t 1 , l 1 ) are (0, 1) and (1, 0) respectively. Moreover, suppose (A' 1 , B' 1 ) is prepared at Apply Ω to Alice and Bob respectively 01 and Ω 10 After encoding, (A' 1 , B' 1 ) is transformed into Bob can then easily read (i 1 , j 1 ) is (0, 1). After Bob sends him to After sending the measurement results of , Alice can easily deduce that (t 1 , l 1 ) is (1, 0). After decoding m' A ||h(m A )', Bob calculates h(m' A ) and h(m′ A ) and h(m A )' to authenticate Alice's m A . Similarly, after decoding m' B ||h(m B )', Alice calculates h(m' B ) and h(m′ B ) and h(m B )' to authenticate Bob's m B .
[0116] 2. Discussion
[0117] The information leakage problem means that anyone else can extract some classic information from public announcements without any active attack. Since every two adjacent information logic Bell states (A 2n-1 , B 2n-1 ) and (A 2n , B 2n ) ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com