Network intrusion identification method based on anomaly flow and black-white list library of IP terminal
An abnormal traffic, black and white list technology, applied in the transmission system, electrical components, etc., can solve the problems of increasing network burden, complex network traffic of data mining technology operating system, and increased false negative rate, so as to avoid the effect of system crash
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0016] The present invention will be described in further detail in conjunction with the accompanying drawings and specific embodiments.
[0017] Network intrusion will generate a lot of flooded message data, which will lead to a surge in network traffic data. At the same time, the propagation and attacks of these messages will directly cause the CPU usage of routers and switches on the path to continue to rise, seriously affecting normal routing. and forwarding efficiency, and even cause downtime and complete network paralysis, and the attacked servers and business data centers cannot operate normally. Therefore, how to detect network intrusions in a timely manner has become crucial for power companies.
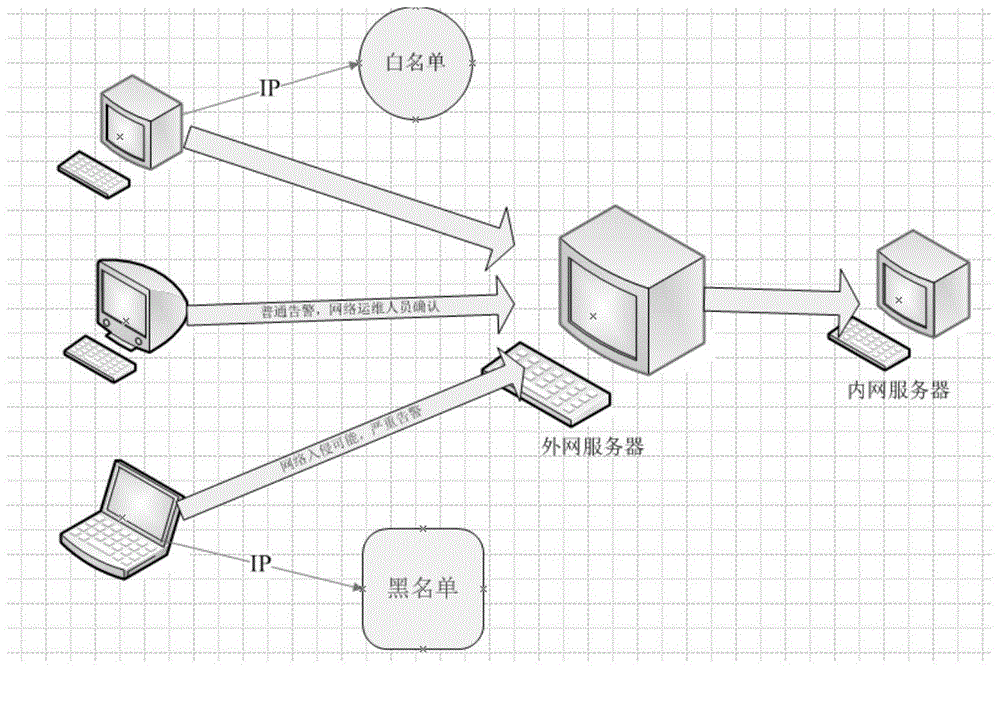
[0018] In the present invention, first set up such as figure 1 The IP terminal analysis behavior platform shown includes an external network server, an internal network server and a client, wherein the client communicates with the external network server, and the external ne...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com