Credible execution method for privacy policy in cloud environment
A privacy policy and execution method technology, applied in the field of cloud computing security, can solve the problems that users are difficult to identify cloud service providers, lack of distributed policy-driven access control mechanisms, etc., to ensure credibility and integrity, and ensure privacy security performance, ensuring credible implementation
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
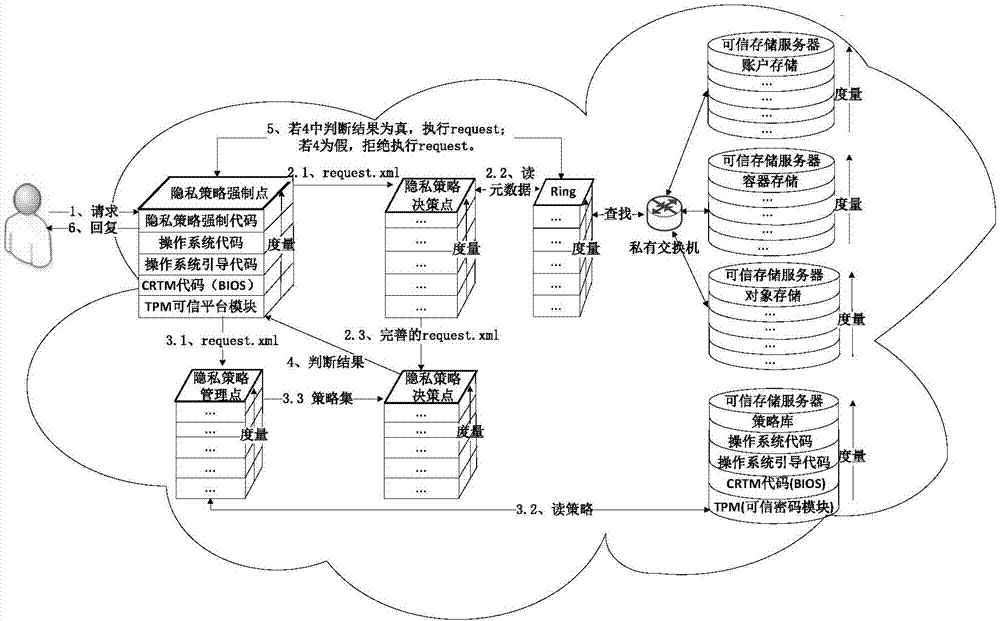
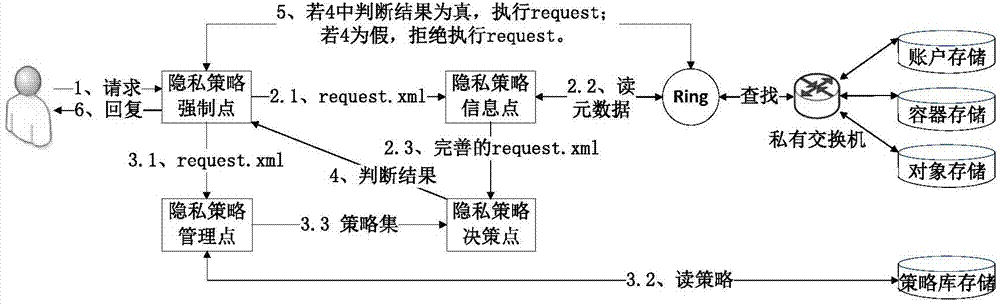
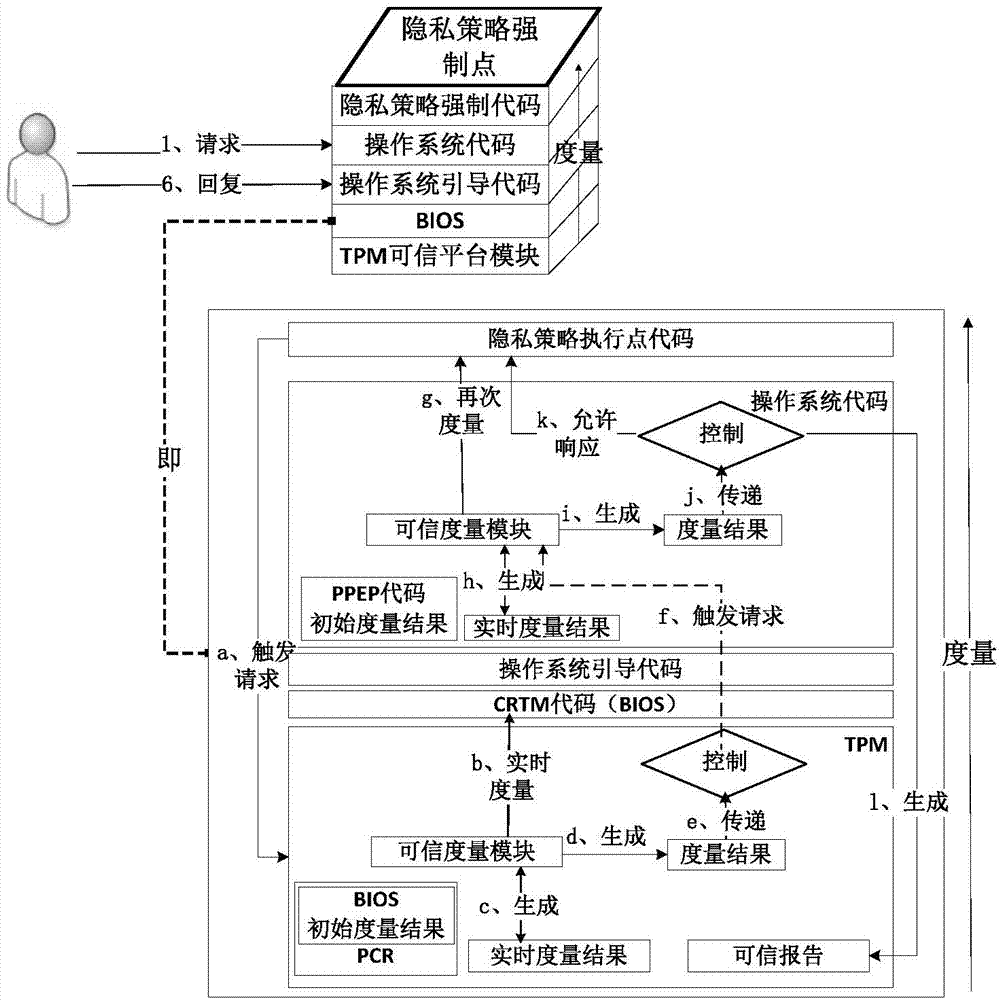
[0032] The operating environment of the present invention is composed of two parts, a remote access client program and a cloud platform. Among them, the remote access client program is developed based on Myeclipse10.0, which is implemented in J2SDK1.6 version java language, installed on the Windows7 system configured as Intel Core Duo.i5-4200H1.7GHz, and used to send user requests and receive services Response; the cloud platform is developed based on the Swift1.7 cloud storage architecture. The platform is composed of 9 Intel Xeon E5-2650 2.0GHz Linux system servers configured with a trusted root TPM. Each module in the privacy policy distributed execution method is independent It is configured on each server, and based on the trusted root TPM in each server, the implementation of privacy policy can be guaranteed, and the third-party Sunxacml development kit is used to analyze, complete and complete user requests, subject and object metadata, and privacy policies. match calcu...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com