Safety method for accessing mobile phone terminal to visit cloud storage server
A cloud storage server and mobile terminal technology, applied in electrical components, transmission systems, etc., can solve the problem of unable to meet the security authentication and key negotiation requirements of mobile terminals and cloud servers, saving communication overhead, improving computing performance, guaranteeing safety effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0043] The present invention will be described in further detail below in conjunction with the accompanying drawings and embodiments.
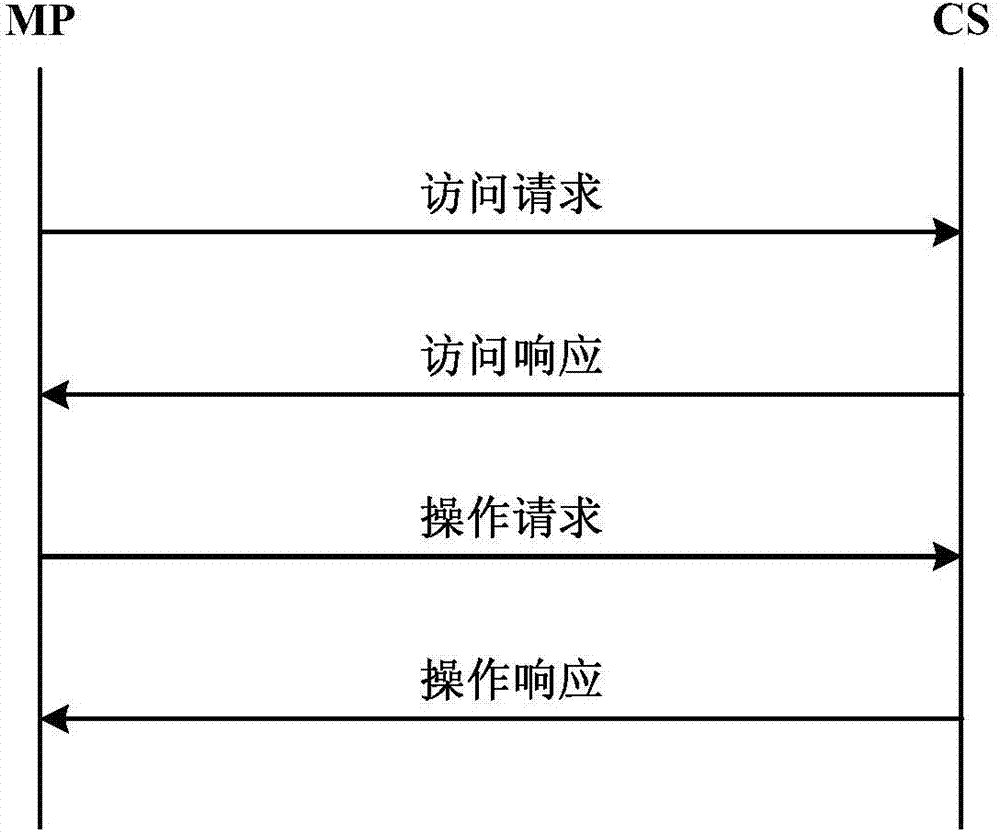
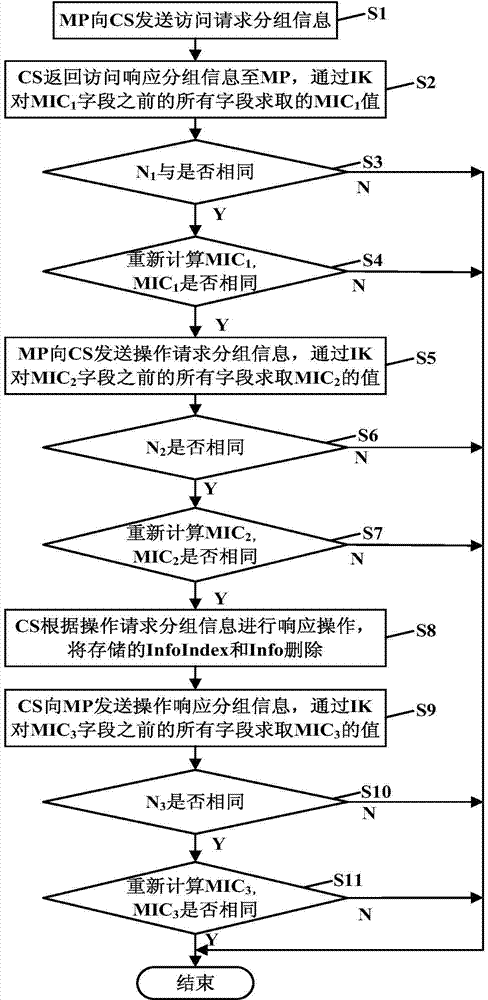
[0044] see figure 1 and figure 2 As shown, the security method for the mobile terminal to access the cloud storage server in the embodiment of the present invention comprises the following steps:
[0045] S1: When the MP (smart phone terminal) needs to access the CS (cloud storage server), the MP sends access request packet information to the CS. The request packet information includes MPID (identity information of MP) and N 1 (the first random number selected by the MP), go to step S2.
[0046] S2: CS returns the access response packet information to MP, and the access response packet information includes N 1 , N 2 (random number selected by CS), CHelp (ciphertext auxiliary information) of K (session key) selected by CS for communication with MP. CS uses K to derive IK (integrity verification key), and CS uses IK to MIC 1 (First Integ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com