User login validation method, device and system
A login verification and user technology, applied in the Internet field, can solve problems such as user account security and business pressure threats, and achieve the effect of improving user time efficiency, reducing operations, and balancing security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example
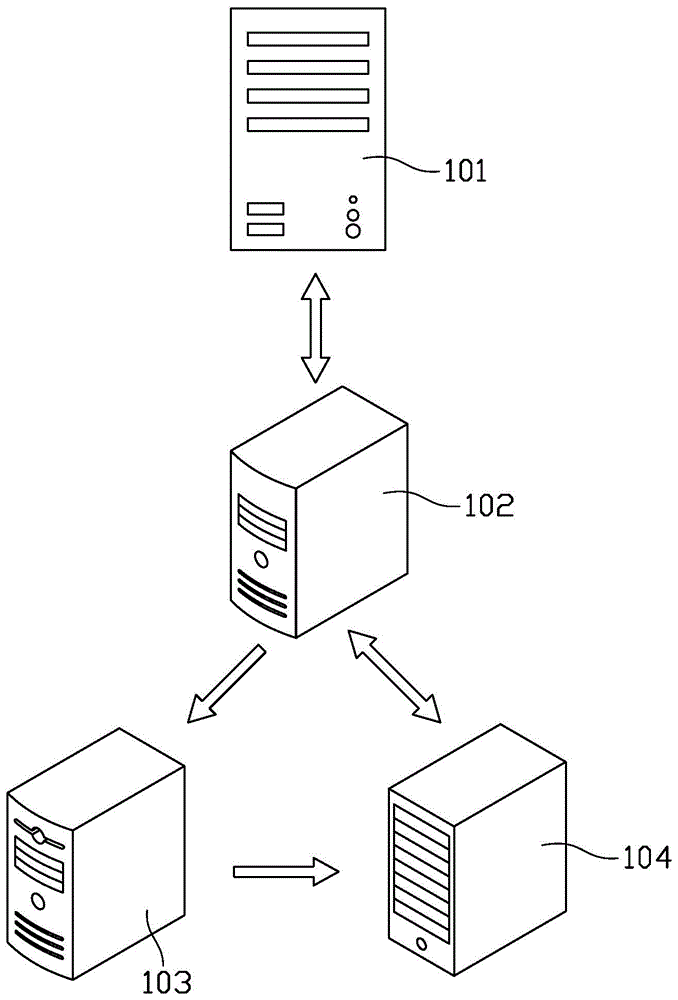
[0040] refer to figure 1 , which is a schematic diagram of the user login verification system provided by the first embodiment of the present invention. Such as figure 1 As shown, the above system includes: an access server 101 , an application server 102 , a data management server 103 and a verification policy server 104 .
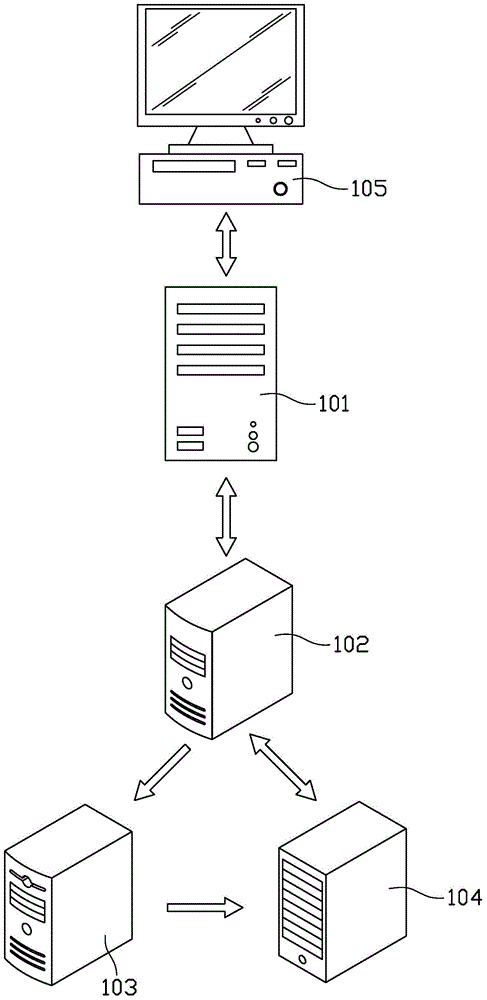
[0041] Among them, see image 3 , the access server 101 is connected to the client 105 ( figure 2 ) and the application server 102, receive the login request information from the client 105, and transmit the login request information from the client 105 to the application server 102, and then return the result returned by the application server 102 to the client 105.
[0042] The application server 102 receives the login request information sent by the access server 101, and forwards the received login request information to the verification policy server 104 to obtain the verification policy. The verification strategy mentioned above refers to the w...
no. 2 example
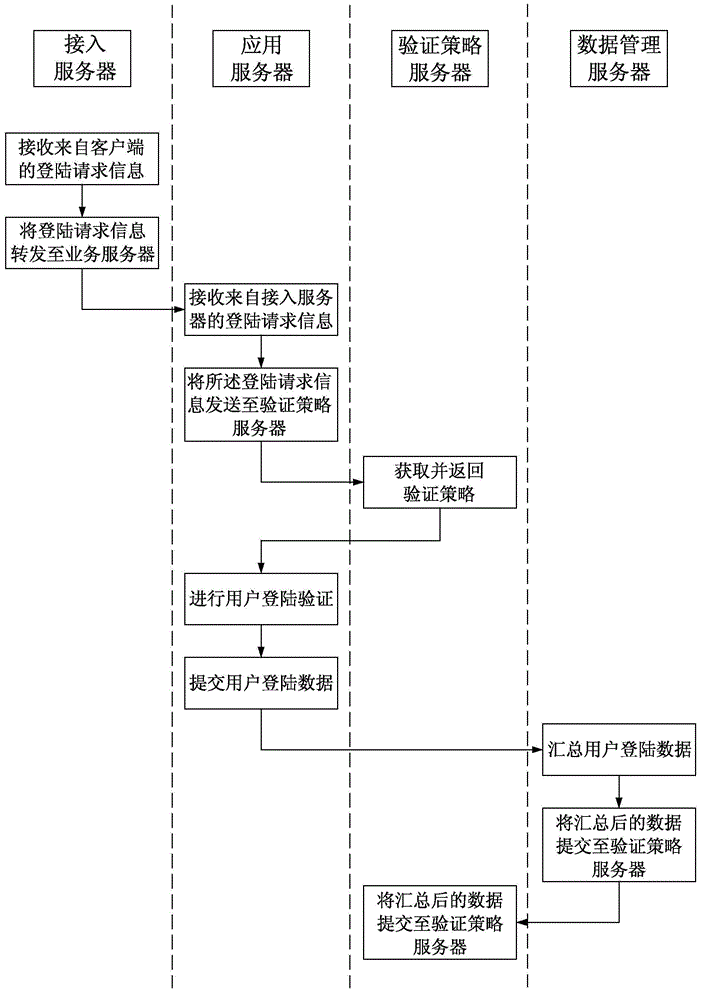
[0067] This embodiment provides a user login verification method, which can be used for figure 1 The user shown is logged into the authentication system. refer to Figure 6 , the method of this embodiment includes the following steps:
[0068] Step 210, receiving login request information from the user. see also figure 2 and image 3 , the verification policy server 104 receives the login request information forwarded by the application server 102 . The login request information may include user name, password and other information used for user login verification.
[0069] Step 220: Parse the login request information to obtain a user ID, and obtain the user's historical login records according to the user ID; and parse the historical login records to obtain multiple login feature information of the user.
[0070] The above-mentioned historical login records are submitted by the data management server 103 to the verification policy server 104 . Multiple login feature ...
no. 3 example
[0080] This embodiment provides a user login verification method, which can be used for figure 1 The user shown is logged into the authentication system. refer to Figure 7 The method of this embodiment is similar to the method of the second embodiment, the difference is that it further includes: Step 310, acquiring the source application program of the login request information.
[0081] It can be understood that the above-mentioned application program refers to a collection of program modules distinguished by functions, products or requirements. Different applications should provide different functions and features. For example, an online forum and a shopping website may be different applications. Generally speaking, the URL / domain name of the web application can be used to distinguish the application. The same web application generally has part of the same domain name / URL.
[0082] In the application server 102, the source application program of the login request infor...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com